一、实验背景
一个组织最近发现了数据泄露事件。执法部门已发现黑客攻击嫌疑人“Greg Schardt”并查获了一台旧的戴尔CPi笔记本电脑,该笔记本电脑可能怀疑。您的团队的任务是对笔记本进行取证调查计算机。您的合作伙伴已使用专业映像获取了硬盘驱动器磁盘映像工具以及写阻止程序。磁盘映像“WinLabImage.E01”已传递给您视窗取证分析。您还收到了图像的 MD5 哈希值,如下所示“AEE4fcd9301c03b3b054623ca261959a”。
- 实验目的
1. 在Autopsy中创建新案例。
2. 使用Autopsy的取证模块扫描 Windows 磁盘映像。(警告:耗时的过程)
3. 分析Windows文件系统,注册表和各种工件。
4. 提取数字证据并回答问题。
三、实验准备
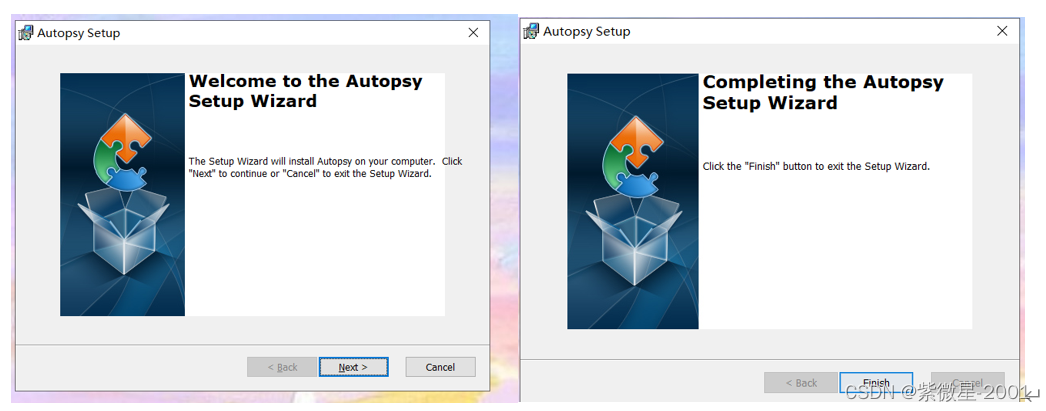
(1)安装Autopsy
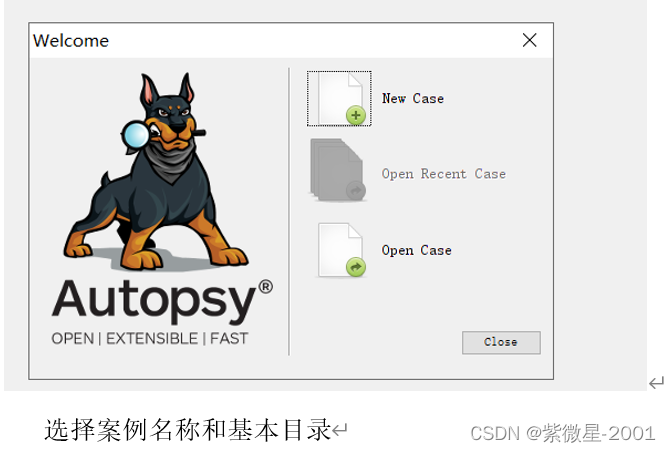
(2)在Autopsy中创建一个新案例
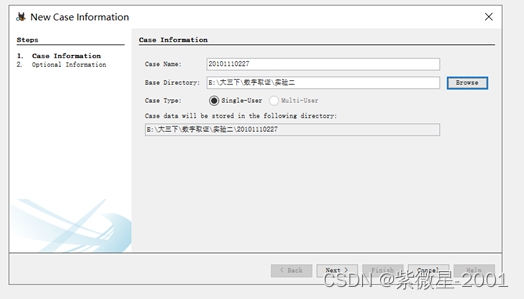

(保护隐私哈哈哈)
 (3)将磁盘映像“WinLabImage.E01”添加为数据源 (.E02文件自动加载)并选择所有收录模块
(3)将磁盘映像“WinLabImage.E01”添加为数据源 (.E02文件自动加载)并选择所有收录模块








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 1041
1041











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










