python 供应链
ZDNet published this interesting post 2 days ago titled “Two malicious Python libraries caught stealing SSH and GPG keys” which sets stage to what is coming in 2020 and onward.
网易科技发布这个有趣的帖子3天前标题为“ 这两种恶意Python库捕盗SSH和GPG密钥 ”这台阶段什么是在2020年及以后的到来。
And if you think your are safe (as you recently procured a well marketed commercial open source dependency scanner) is when you are most in danger as all such tools lack intelligence to track such advanced infiltration patterns.
而且,如果您认为自己是安全的(最近购买的是市售的商业开源依赖扫描仪) ,那么您处于最大危险之中,因为所有此类工具都缺乏跟踪此类高级渗透模式的情报。
The phrase “Think like an Attacker” is often abused in cyber security to encourage people and organizations to get inside the head of the groups which are targeting them.
网络安全中经常滥用 “ 像攻击者一样思考 ”一词,以鼓励人们和组织进入针对他们的组织的领导层。
Here’s what’s wrong with think like an attacker: most people have no clue how to do it. They don’t know what matters to an attacker. They don’t know how an attacker spends their day. They don’t know how an attacker approaches a problem.
这就是像攻击者那样思考的地方出了问题 :大多数人都不知道如何做。 他们不知道什么对攻击者重要。 他们不知道攻击者如何度过他们的一天。 他们不知道攻击者如何解决问题。
Lately, I’ve been challenging people to think like a professional chef. Most people have no idea how a chef spends their days, or how they approach a problem. They have no idea how to plan a menu, or how to cook a hundred or more dinners in an hour.
最近,我一直在挑战人们像专业厨师那样思考。 大多数人不知道厨师如何度过他们的一天,或如何解决问题。 他们不知道如何计划菜单,或者如何在一个小时内烹饪一百个或更多的晚餐。
~ Adam Shostack
〜 亚当·肖斯塔克
I’d strongly encourage everyone to pause and watch this entire presentation by Haroon Meer titled Learning the wrong lessons from Offense. Haroon’s presentations are often vendor-agnostic, honest, informative and downright fabulous.
我强烈鼓励大家暂停观看由Haroon Meer撰写的整个演讲,题目为“ 从进攻中学习错误的教训” 。 Haroon的演讲通常与供应商无关,诚实,信息丰富且彻头彻尾。
Key takeaways : You cannot teach a defender to think like an attacker. As Haroon wisely states (quoting from Richard Feynman’s Caro Cult Science), we as defenders follow everything that we see the attacker do, then model detection in isolation (honeypots, adversarial modeling, situational awareness) and not grasp the point bearing context.
关键要点 :您不能教会防御者像攻击者那样思考。 正如Haroon明智地指出的那样 (引自Richard Feynman的Caro Cult Science ),我们作为防御者会遵循攻击者所做的所有事情,然后孤立地进行模型检测(蜜罐,对抗性建模,态势感知),而不是掌握关键点上下文。
Let’s now revert back to this incident and speculatively understand how an infiltrator organized her/his actions.
现在让我们回到该事件,并推测性地了解一个渗透者如何组织她/他的行动。
基本原理思考-渗透者思维模式建模 (First principles thinking — Modeling the Infiltrators mindset)
行动1:猎物选择 (Act 1: Prey Selection)
Identify the most popular libraries imported/used in the PyPI — Python Package Index via https://hugovk.github.io/top-pypi-packages/.
通过https://hugovk.github.io/top-pypi-packages/识别在PyPI中引入/使用的最受欢迎的库-Python软件包索引。
Why pick these two?
为什么选择这两个?
It’s imperative that python-dateutil (7MM downloads) and jellyfish (387K downloads) are fairly popular and ranked on the fortnight index https://hugovk.github.io/top-pypi-packages/top-pypi-packages-30-days.json
至关重要的是, python-dateutil (7 毫米下载)和水母 (38.7万下载)相当受欢迎,并在两周的索引上排名https://hugovk.github.io/top-pypi-packages/top-pypi-packages-30天.json
第二幕:模仿和伪装 (Act 2: Mimicry and Camouflage)
Ambush predators are types of carnivores that usually distinguish themselves by an approach to hunting which relies on stealth or strategy as opposed to speed or strength. Hallmarks of this behavior is mimicry and camouflage which are ways to deceive prey into believing predator activity is something else.
伏击食肉动物是食肉动物的一种,通常通过一种依靠隐身或策略而不是速度或力量的狩猎方法来区分自己。 这种行为的标志是模仿和伪装 ,这是欺骗猎物以相信捕食者活动的另一种方式。
Applied to cyber security, this can be rationalized to typosquatting packages and domains.
应用于网络安全,这可以合理化为域名抢注包和域名。
In this case, the actor created two new packages in the package index PyPI: python3-dateutil and jelLyfish.
在这种情况下, 参与者在包索引PyPI中创建了两个新包: python3-dateutil和jelLyfish 。
If you haven’t noticed, pause for moment and pay attention to the naming convention.
如果您没有注意到,请暂停片刻并注意命名约定。
python3-dateutil mimics python-dateutil with a version number prefix and jelLyfish mimics jellyfish with a typo that can often go unnoticed.
python3-dateutil 模仿带有版本号前缀的python-dateutil ,而jelLyfish 模仿带错别字的水母 ,这种错别字经常会被忽略。
Applying the art of smart mimicry, the actor pretends to serve the community by porting dateutil to python version 3+ and thereby calling it python3-dateutil. The actor then camouflages jelLyfish as a transitive dependency of python3-dateutil that contains the seeded trojan pattern (encode-download-decode-exfiltrate-send).
通过运用智能模仿的技巧 ,演员通过将dateutil移植到python 3+版本并因此将其称为python3-dateutil来假装为社区服务。 然后,演员将jelLyfish伪装成python3-dateutil的传递依赖项 ,其中包含种子木马模式( encode-download-decode-exfiltrate-send )。
第三幕:播种意识 (Act 3: Seeding awareness)
Merely seeding a trojan package amongst a plethora of packages is insufficient. Majority of the developers make choices and decisions using a package-index service in combination with a search engine query (google, bing, etc) and of course stackoverflow.
仅在大量软件包中播种特洛伊木马程序包是不够的。 大多数开发人员通过使用包索引服务结合搜索引擎查询(谷歌,必应等)以及当然stackoverflow来做出选择和决策。
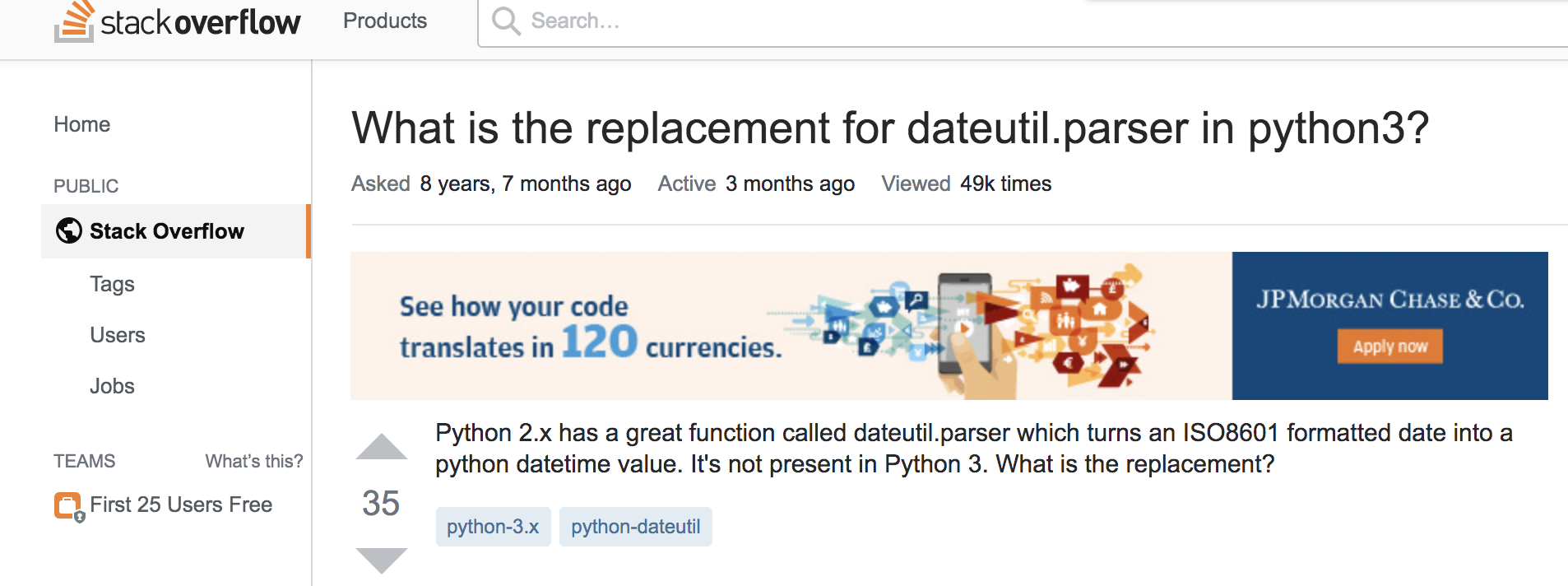
[Speculative account] The actor now pivots to stackoverflow and creates an anonymous identity. Concealed behind this identity the actor can pose a simple question.
[ 投机帐户 ]现在,actor转而使用stackoverflow并创建一个匿名身份。 隐藏在这种身份背后的演员可以提出一个简单的问题。
What is the replacement for dateutil.parser in python3?
python3中dateutil.parser的替代品是什么?
Thereafter he/she creates additional identities and answers to this question with a hyperlink to the malicious python3-dateutil. The poser now scores answers with the this hyperlink.
此后,他(她)将创建其他身份并通过指向恶意python3-dateutil的超链接来回答此问题。 姿势者现在使用此超链接为答案评分。
Based on a ranking algorithm, any search engine would begin to index/score this question and any subsequent searches for “dateutil for python 3” would yield this stackoverflow link.
基于排名算法,任何搜索引擎都将开始为该问题建立索引/评分,并且随后对“ dateutil for python 3 ”的任何搜索都将产生此stackoverflow链接。
第4幕:躺在等待 (Act 4: Lie in Wait)
Now the actor waits insidiously until the appropriate moment where a prey (data scientist/programmer/developer) incorporates the library into his/her software supply chain.
现在,演员会阴险地等待,直到适当的时刻,猎物(数据科学家/程序员/开发人员)将图书馆合并到他/她的软件供应链中。
第五幕:反捕食者的适应 (Act 5: Anti Predator Adaptions)
This is not a new attack technique.
这不是新的攻击技术。
In 2016, Nikolai Philipp Tschacher documented and proved this technique as a part of his bachelor thesis.
在2016年,尼古拉·菲利普·查查(Nikolai Philipp Tschacher) 记录并证明了该技术是其学士论文的一部分。
Why haven’t commercial security vendors assessed and incorporated his research to improve detection techniques?
商业安全厂商为什么不评估并结合他的研究以改进检测技术?
Some statistical numbers from Nikolai’s thesis for the uploaded packages and their installations:
来自Nikolai论文的一些统计数字,用于上传的软件包及其安装:
214 total different uploaded typo packages on three different package repositories
在三个不同的软件包存储库中总共有214个不同的上载错别字软件包
- 92 average installations per package 每个软件包平均安装92次
- The standard derivation of installations per package is 433 and thus relatively high 每个软件包的安装标准推导为433,因此相对较高
The most installed package (urllib2) received 3929 unique installations in almost 2 weeks (284 average installations per day)
安装最多的软件包(urllib2)在近两周内获得了3929次唯一安装 (每天平均安装284次)
The most installed package per day was
bs4with 366 unique daily installations on average每天最多安装的软件包是
bs4,平均每天有366次独特的安装- The least installed package had only one installation (Probably by a mirror or crawler) 安装最少的软件包只有一个安装(可能是通过镜像或搜寻器安装的)
外卖 (Takeaways)
For engineers — Be informed and pay more attention prior to depending on any library. Use your own judgement and assess all transitive dependencies as well.
对于工程师 -在依赖任何库之前,请先获知并给予更多关注。 使用您自己的判断并评估所有传递依存关系。
For engineers — Incorporate a formal verification process as a part of your code reviews and CI pipeline to ensure that such libraries are not imported.
对于工程师 -将正式的验证过程纳入代码检查和CI管道的一部分,以确保不导入此类库。
For engineers — Identify all trigger functions in your application’s call path to assess attack surface exposure.
对于工程师 —确定应用程序的调用路径中的所有触发功能,以评估被攻击面的暴露程度。
For vendors — Stop spending dollars in messaging your product and start paying attention to improving detection techniques. An obvious one is to simply check string edit distance of packages being installed. If you see ‘pip install xyz’, compare ‘xyz’ to the top 500 PyPI packages, and see if it’s close, but not the same, as an existing package — bonus points if the difference is in a lookalike character such as 0/O, l/L/I, etc.
对于供应商 —停止在产品信息上花钱,开始关注改进检测技术。 一个明显的方法是简单地检查正在安装的软件包的字符串编辑距离。 如果您看到“ pip install xyz ”,则将“ xyz ”与前500个PyPI软件包进行比较,看看它与现有软件包是否接近但不相同-如果区别在于相似字符(例如0 / O,l / L / I等
For publishers/vendors — Avoid selling FUD and provide insights / solutions that a customer can incorporate to solve for these emerging threats.
对于发布者/供应商-避免出售FUD,并提供客户可以用来解决这些新出现的威胁的见解/解决方案。
For customers — Ask vendors hard questions to ensure that such detection is provable.
对于客户 -向供应商提出难题,以确保可以进行这种检测。
更新: (Update:)
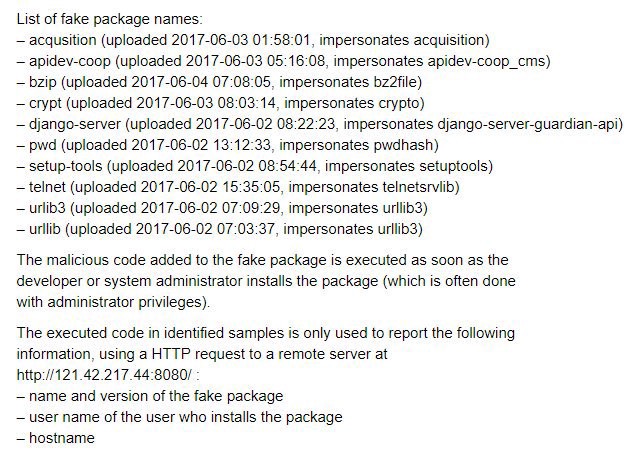
List of other packages in ecosystem with traits of mimicry and camouflage since 2017
自2017年以来具有拟态和伪装特性的生态系统中其他软件包的列表
翻译自: https://medium.com/analytics-vidhya/infiltrating-pythons-software-supply-chain-bcb4cef3afdf
python 供应链




















 1160
1160











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








