调试器 (Debugger)
You might think that as long as you keep your password safe, you’re the only person who can access your online accounts. But
您可能会认为,只要确保密码安全,您就是唯一可以访问您的在线帐户的人。 但
Facebook, Facebook , Twitter, and the majority of tech companies build “user impersonation” tools into their software that allow their employees to peer inside of any account — and act as though they’ve logged into that account — without the owner ever knowing. These tools are generally accepted by engineers as common practice and rarely disclosed to users. Twitter和大多数科技公司在其软件中构建了“用户模拟”工具,这些工具使员工可以在任何帐户中进行窥探-就像他们已经登录该帐户一样-在所有者不知情的情况下进行操作。 这些工具通常被工程师接受为惯例,很少向用户公开。Often called “impersonate mode,” “ghost user,” or “proxy user,” they allow customer service representatives to see a service through a user’s account in order to diagnose errors and help engineers build better products by showing them how they work inside real users’ accounts.
通常被称为 “impersoñ吃模式”,“幻影用户”或“代理用户”,他们让客户服务代表看到一个服务,通过用户的帐户,以便诊断错误,并帮助工程师打造更好的产品向他们展示他们是如何工作的在真实用户的帐户中。
But this type of internal tool can be abused. Most famously, Uber employees used the app’s “God mode” to track the movements of everyone from politicians to ex-girlfriends. Lyft provided similar tools, which were also abused by employees. And Ring recently fired employees for watching customer videos, which they easily could have found using a user impersonation tool, though Ring did not disclose how the employees accessed videos.
但是这种内部工具可能会被滥用。 最著名的是,Uber员工使用该应用程序的“ 上帝模式 ”来跟踪从政客到前女友的每个人的活动。 Lyft提供了类似的工具 ,这些工具也被员工滥用。 而且,Ring 最近解雇了员工观看客户视频,他们很容易使用用户模拟工具找到他们,尽管Ring并未透露员工如何访问视频。
Part of the problem is how the programming tools that many developers use to build apps and services handle their user impersonation features.
问题的一部分是许多开发人员用来构建应用和服务的编程工具如何处理其用户模拟功能。
One of the most popular libraries for the programming language Ruby on Rails, ActiveAdmin, provides one such feature and has been installed over 7.9 million times. Laravel, a popular PHP-based language, offers a similar package called Spark as do many other development tools.
ActiveRuby是 Ruby on Rails编程语言中最受欢迎的库之一,它提供了一项这样的功能,已被安装了790万次 。 Laravel是一种流行的基于PHP的语言, 与 其他许多开发工具一样,它提供了一个称为Spark的类似软件包 。
Out-of-the-box user impersonation tools provided by these frameworks typically don’t ask for users’ permission or even notify users when their account has been accessed. For those with administrator access, popping into accounts is as easy as clicking around the app.
这些框架提供的开箱即用的用户模拟工具通常不会征求用户的许可,甚至不会在访问他们的帐户时通知用户。 对于具有管理员访问权限的用户来说,弹出帐户就像在应用程序周围单击一样容易。
A developer using Laravel Spark to build an app, for instance, manually “white lists” users with administrator access that would allow access to impersonator mode. Users of the application who are signed in with a white-listed email address then see features that regular users can’t access. In apps built with Spark, one of those features is an option to “impersonate” another user’s account.
例如,使用Laravel Spark来开发应用程序的开发人员,将具有管理员访问权限的用户手动“白名单”用户“白名单”,以允许其访问模拟者模式。 使用白名单中的电子邮件地址登录的应用程序用户将看到普通用户无法访问的功能。 在使用Spark构建的应用程序中,这些功能之一是“模拟”另一个用户帐户的选项。
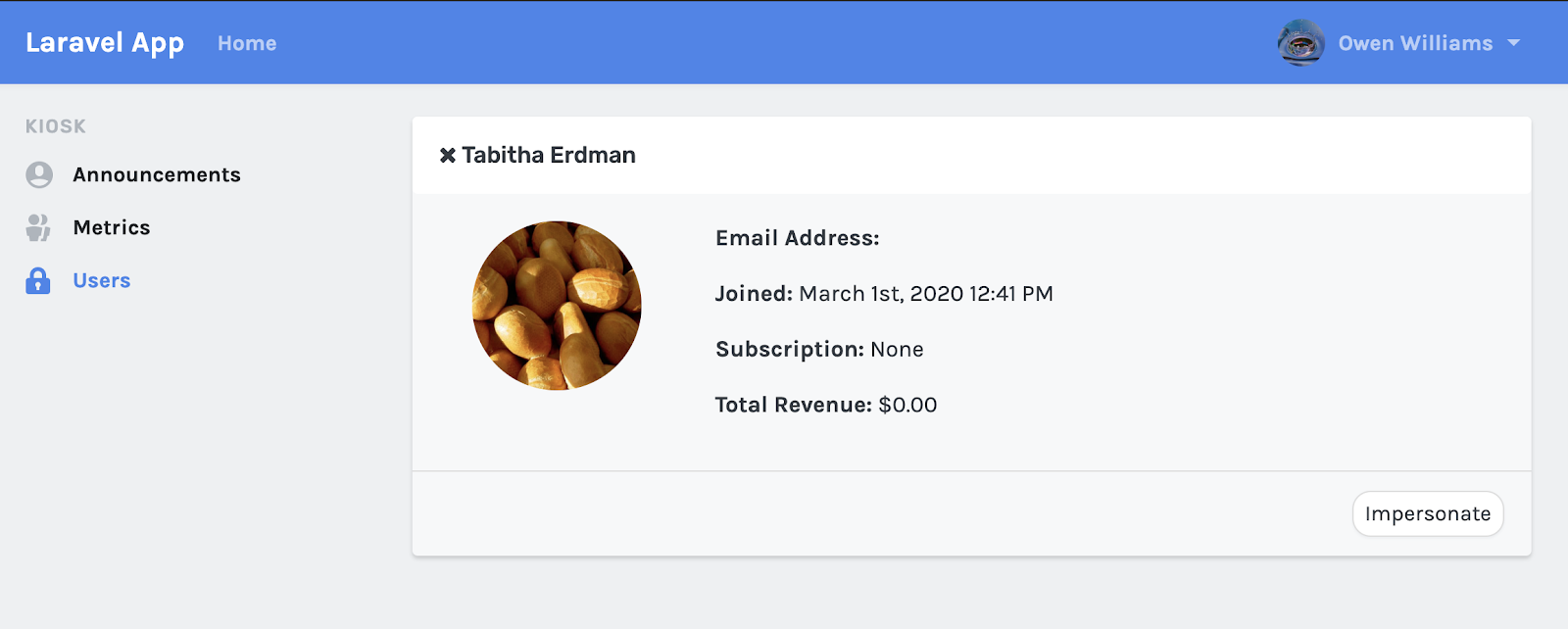
Those with administrator’s access can search for a specific user, click an “impersonate” button, and instantly view the app through that user’s account as if they had legitimately logged in with a password.
具有管理员访问权限的用户可以搜索特定用户,单击“模拟”按钮,然后立即通过该用户的帐户查看该应用程序,就好像他们已经使用密码合法登录一样。
Not only is the unsuspecting user not asked to consent to someone viewing their account, but they aren’t notified, and by default, the development framework doesn’t require the administrator to provide any sort of internal note or reason for accessing an account.
不仅不会要求毫无戒心的用户同意某人查看其帐户,而且不会通知他们,并且默认情况下,开发框架不需要管理员提供任何内部注释或访问帐户的原因。
Instead of creating a white list of users who can access user accounts, which Spark requires, some startups instead simply grant access based on the email address of an employee, which means that anyone who signs up for an account with a company email address can access user accounts. Because employees generally sign employment contracts that cover access to user data, it’s assumed they can be trusted with such access — but as companies grow, this becomes a bigger risk to take.
一些初创企业没有按照Spark要求创建可以访问用户帐户的用户白名单,而是仅根据员工的电子邮件地址授予访问权限,这意味着使用公司电子邮件地址注册帐户的任何人都可以访问用户帐户。 由于员工通常签署涵盖访问用户数据的雇佣合同,因此假定他们可以受到这种访问的信任-但是随着公司的发展,这将承担更大的风险。
And because impersonation tools provide little value to users, they can be the last tools to be improved or restricted as a growing company scrambles to keep customers happy. Though many companies do appropriately lock down access to user accounts as they grow, it’s not uncommon for impersonation tools to be left in their uncontrolled or companywide default for years until a security incident like Uber’s causes the company to change the way it’s implemented.
而且,由于模拟工具给用户带来的价值很小,因此它们可能是最后一个需要改进或限制的工具,因为成长中的公司争先恐后地使客户满意。 尽管许多公司确实会随着用户帐户的增长而适当地锁定其访问权限,但在Uber等安全事件导致公司更改其实施方式之前,假冒工具多年处于不受控制或全公司范围的默认设置中并不少见。
While large companies like Facebook have said they now have “rigorous administrative, physical, and technical controls in place to restrict employee access,” it’s telling that as a user of the service, there’s no way to actually know when someone internally accesses your account. While abusing such tools is the “easiest way to get fired” from the company, according to VentureBeat, such processes are invisible, and we must trust that Facebook actually audits this.
尽管像Facebook这样的大公司表示,他们现在已经“采取了严格的管理,物理和技术控制措施来限制员工的访问权限”,但它告诉我们,作为服务的用户,实际上无法知道有人何时在内部访问您的帐户。 据VentureBeat称 ,尽管滥用此类工具是公司“最容易被解雇的方法”,但这种过程是不可见的,我们必须相信Facebook确实对此进行了审核。
There are easy ways to make impersonation tools safer for customers. Some services require the user to specifically invite administrators in before they can access an account. Others, including Uber after the God mode scandal, require employees to make a request for access to security staff, with detailed notes, which is manually granted and logged internally.
有许多简便的方法可以使模拟工具对客户更安全。 某些服务要求用户特别邀请管理员进入,然后才能访问帐户。 其他措施,包括在“上帝”模式丑闻发生后的优步,要求员工要求访问安全人员,并提供详细的注释,这些注释由人工授予并在内部记录。
If development frameworks were to take a stance on this, it would change the way services are built from the very beginning. If Laravel or Ruby were to bake in a way for users of a service built with their frameworks to see when employees have accessed their accounts, it might become the standard for every service going forward.
如果开发框架对此采取立场,那么它将从一开始就改变构建服务的方式。 如果Laravel或Ruby要烘烤 一种使用其框架构建的服务的用户查看员工何时访问其帐户的方法,它可能成为以后每项服务的标准。
Developers should reconsider being intentional about how these features, which can be useful tools, are offered as they build their services from the beginning — before they’re abused by employees, not after.
开发人员应该重新考虑如何从一开始就在提供服务时(而不是在被员工滥用之前)提供这些功能,这些功能可能是有用的工具。
翻译自: https://onezero.medium.com/how-to-stop-god-mode-abuse-75d4c55fda7c




















 496
496











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








