google fuzzer-test-suite 数据集每个程序的编译细节
- 编译程序
- 每个程序编译的细节。
- boringssl-2016-02-12
- c-ares-CVE-2016-5180
- freetype2-2017
- guetzli-2017-3-30
- harfbuzz-1.3.2
- json-2017-02-12
- lcms-2017-03-21
- libarchive-2017-01-04
- libjpeg-turbo-07-2017
- libpng-1.2.56
- libssh-2017-1272
- libxml2-v2.9.2
- llvm-libcxxabi-2017-01-27
- openssl-1.0.1f
- openssl-1.0.2d
- openssl-1.1.0c
- openthread-2018-02-27
- pcre2-10.00
- proj4-2017-08-14
- re2-2014-12-09
- sqlite-2016-11-14
- vorbis-2017-12-11
- woff2-2016-05-06
- wpantund-2018-02-27
- 用coverage模式编译:
编译程序
在custom-build.sh以及common.sh中把FUZZER_ENGINE改成afl。并且把AFL、libfuzzer等的目录位置填好,其他地方不改。

大部分程序在该程序目录下执行以下命令就可以得到目标程序,有的需要安装一些依赖。目标程序为 程序名称-afl。如果找不到这个程序就crtl+H显示隐藏文件,以-afl结尾的就是目标程序。
mkdir build
cd build
../build.sh asan
每个程序编译的细节。
boringssl-2016-02-12
在boringssl-2016-02-12目录下执行:
sudo apt-get update
sudo apt-get install -y build-essential
sudo apt-get install cmake
sudo add-apt-repository ppa:longsleep/golang-backports
sudo apt-get update
sudo apt-get install golang-go
mkdir build
cd build
../build.sh asan
编译结束后,build目录中以-afl为结尾的就是可执行程序(可能是boringssl-2016-02-12也有可能是…-afl,按ctrl+H显示隐藏文件就能找到)。
运行:
用提供的crash文件测试,可以输出AddressSanitizer信息:
./boringssl-2016-02-12-afl ../crash-ffb22c3101db1e53e38fdf630efd3dfd19cbeb84
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./boringssl-2016-02-12-afl < INPUT_FILE
or
./boringssl-2016-02-12-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./boringssl-2016-02-12-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 41 bytes from ../crash-ffb22c3101db1e53e38fdf630efd3dfd19cbeb84
=================================================================
==3656864==ERROR: AddressSanitizer: heap-use-after-free on address 0x603000000258 at pc 0x00000056a84d bp 0x7fffffffd920 sp 0x7fffffffd918
READ of size 8 at 0x603000000258 thread T0
#0 0x56a84c in ASN1_STRING_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/asn1_lib.c:459:12
#1 0x5766ed in ASN1_primitive_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_fre.c:241:9
#2 0x576618 in ASN1_primitive_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_fre.c:236:9
#3 0x575978 in ASN1_item_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_fre.c:69:5
#4 0x4e70bc in sk_pop_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/stack/stack.c:142:7
#5 0x4ce147 in dsa_priv_decode /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/p_dsa_asn1.c:288:3
#6 0x4dd325 in EVP_PKCS82PKEY /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/pkcs8/pkcs8.c:616:10
#7 0x4caacb in d2i_AutoPrivateKey /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/evp_asn1.c:151:11
#8 0x4c7f51 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/fuzz/privkey.cc:5:17
#9 0x63e798 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#10 0x63e798 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#11 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#12 0x41d6ed in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/boringssl-2016-02-12-afl+0x41d6ed)
0x603000000258 is located 8 bytes inside of 24-byte region [0x603000000250,0x603000000268)
freed by thread T0 here:
#0 0x495bad in free (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/boringssl-2016-02-12-afl+0x495bad)
#1 0x4ce13a in dsa_priv_decode /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/p_dsa_asn1.c:287:3
#2 0x4dd325 in EVP_PKCS82PKEY /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/pkcs8/pkcs8.c:616:10
#3 0x4caacb in d2i_AutoPrivateKey /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/evp_asn1.c:151:11
#4 0x4c7f51 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/fuzz/privkey.cc:5:17
#5 0x63e798 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#6 0x63e798 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#7 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x495e2d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/boringssl-2016-02-12-afl+0x495e2d)
#1 0x56a94d in ASN1_STRING_type_new /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/asn1_lib.c:443:26
#2 0x562793 in c2i_ASN1_INTEGER /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/a_int.c:193:20
#3 0x57129d in asn1_ex_c2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:905:14
#4 0x56fc6b in asn1_d2i_ex_primitive /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:829:10
#5 0x56d08b in ASN1_item_ex_d2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:207:16
#6 0x571f7e in asn1_template_noexp_d2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:661:18
#7 0x56ea80 in asn1_template_ex_d2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:579:16
#8 0x56cbc0 in ASN1_item_ex_d2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:204:20
#9 0x56c84e in ASN1_item_d2i /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/tasn_dec.c:145:9
#10 0x4cdb94 in dsa_priv_decode /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/p_dsa_asn1.c:198:12
#11 0x4dd325 in EVP_PKCS82PKEY /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/pkcs8/pkcs8.c:616:10
#12 0x4caacb in d2i_AutoPrivateKey /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/evp/evp_asn1.c:151:11
#13 0x4c7f51 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/fuzz/privkey.cc:5:17
#14 0x63e798 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#15 0x63e798 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#16 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-use-after-free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/boringssl-2016-02-12/build/BUILD/crypto/asn1/asn1_lib.c:459:12 in ASN1_STRING_free
Shadow bytes around the buggy address:
0x0c067fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c067fff8000: fa fa fd fd fd fd fa fa fd fd fd fa fa fa fd fd
0x0c067fff8010: fd fa fa fa fd fd fd fa fa fa fd fd fd fa fa fa
0x0c067fff8020: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff8030: fa fa 00 00 02 fa fa fa 00 00 00 fa fa fa 00 00
=>0x0c067fff8040: 00 00 fa fa fd fd fd fa fa fa fd[fd]fd fa fa fa
0x0c067fff8050: 00 00 00 00 fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3656864==ABORTING
用AFL执行:
afl-fuzz -i ./seeds/ -o ./out/ -m none -d ./boringssl-2016-02-12-afl @@`
AFL -d模式运行五个多小时没有crash,代码覆盖率前两分钟从1.66%上升到1.70,之后没有上升。

c-ares-CVE-2016-5180
在c-ares-CVE-2016-5180目录下执行:
mkdir build
cd build
../build.sh asan
运行c-ares-CVE-2016-5180-afl:
用AFL测试,不到1分钟测试出1个crash:
运行这个crash文件:./c-ares-CVE-2016-5180-afl out/crashes/id\:000000\,sig\:06\,src\:000020+000017\,op\:splice\,rep\:8 ======================= INFO ========================= This binary is built for AFL-fuzz. To run the target function on individual input(s) execute this: ./c-ares-CVE-2016-5180-afl < INPUT_FILE or ./c-ares-CVE-2016-5180-afl INPUT_FILE1 [INPUT_FILE2 ... ] To fuzz with afl-fuzz execute this: afl-fuzz [afl-flags] ./c-ares-CVE-2016-5180-afl [-N] afl-fuzz will run N iterations before re-spawning the process (default: 1000) ====================================================== Reading 6 bytes from out/crashes/id:000000,sig:06,src:000020+000017,op:splice,rep:8 ================================================================= ==2044204==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x603000000025 at pc 0x0000004c7c99 bp 0x7fffffffdd70 sp 0x7fffffffdd68 WRITE of size 1 at 0x603000000025 thread T0 #0 0x4c7c98 in ares_create_query (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/test/c-ares-CVE-2016-5180-afl+0x4c7c98) #1 0x4c70e4 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/../target.cc:14:3 #2 0x4c8938 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5 #3 0x4c8938 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12 #4 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16 #5 0x41c5cd in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/test/c-ares-CVE-2016-5180-afl+0x41c5cd) 0x603000000025 is located 0 bytes to the right of 21-byte region [0x603000000010,0x603000000025) allocated by thread T0 here: #0 0x494d0d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/test/c-ares-CVE-2016-5180-afl+0x494d0d) #1 0x4c75ca in ares_create_query (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/test/c-ares-CVE-2016-5180-afl+0x4c75ca) #2 0x4c70e4 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/../target.cc:14:3 #3 0x4c8938 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5 #4 0x4c8938 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12 #5 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16 SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/c-ares-CVE-2016-5180/build/test/c-ares-CVE-2016-5180-afl+0x4c7c98) in ares_create_query Shadow bytes around the buggy address: 0x0c067fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0c067fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0c067fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0c067fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0c067fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 =>0x0c067fff8000: fa fa 00 00[05]fa fa fa fa fa fa fa fa fa fa fa 0x0c067fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa 0x0c067fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa 0x0c067fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa 0x0c067fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa 0x0c067fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa Shadow byte legend (one shadow byte represents 8 application bytes): Addressable: 00 Partially addressable: 01 02 03 04 05 06 07 Heap left redzone: fa Freed heap region: fd Stack left redzone: f1 Stack mid redzone: f2 Stack right redzone: f3 Stack after return: f5 Stack use after scope: f8 Global redzone: f9 Global init order: f6 Poisoned by user: f7 Container overflow: fc Array cookie: ac Intra object redzone: bb ASan internal: fe Left alloca redzone: ca Right alloca redzone: cb Shadow gap: cc ==2044204==ABORTING
freetype2-2017
在freetype2-2017目录下运行:
sudo apt-get install libarchive-dev
mkdir build
cd build
../build.sh asan
运行程序:
用AFL测试,这个程序主要用于代码覆盖率的获取。
guetzli-2017-3-30
在guetzli-2017-3-30目录下运行
mkdir build
cd build
../build.sh asan
运行编好的程序:
运行提供的crash,触发这个assertion failure:
用AFL运行半个小时有1个crash,这个crash触发了这个assertion failure。
harfbuzz-1.3.2
在 sudo apt install ragel目录下执行以下命令:
sudo apt install ragel
mkdir build
cd build
../build.sh asan
运行:
运行提供的crash,触发断言错误:
用AFL -d模式运行1个半小时,无crash,代码覆盖率一直在增长。
json-2017-02-12
运行编译好的程序:
用提供的crash测试,触发这个断言错误:
用AFL测试,15分钟内出现两个crash。
crash
执行发现的crash,二者都触发了断言错误:
lcms-2017-03-21
在lcms-2017-03-21此目录下执行
mkdir build
cd build
../build.sh asan
得到程序lcms-2017-03-21-afl。(如果没有就 ctrl+H 显示隐藏文件 “…-afl”即为编译好的程序)一下是编译好后build文件夹
运行lcms-2017-03-21-afl:
用提供的crash文件运行这个程序,会输出addressSanitizer的输出:$ ./lcms-2017-03-21-afl ../crash-6a7f7b35fc6de5b19080b1c32588c727caf5d396 ======================= INFO ========================= This binary is built for AFL-fuzz. To run the target function on individual input(s) execute this: ./lcms-2017-03-21-afl < INPUT_FILE or ./lcms-2017-03-21-afl INPUT_FILE1 [INPUT_FILE2 ... ] To fuzz with afl-fuzz execute this: afl-fuzz [afl-flags] ./lcms-2017-03-21-afl [-N] afl-fuzz will run N iterations before re-spawning the process (default: 1000) ====================================================== Reading 4096 bytes from ../crash->6a7f7b35fc6de5b19080b1c32588c727caf5d396 ================================================================= ==1744598==ERROR: AddressSanitizer: heap-buffer-overflow on address >0x60800000098c at pc 0x00000055c8d3 bp 0x7fffffffd550 sp 0x7fffffffd548 READ of size 4 at 0x60800000098c thread T0 #0 0x55c8d2 in TetrahedralInterpFloat /home/yiru/fuzzer-test-suite/fuzzer->test-suite/lcms-2017-03-21/build/BUILD/src/cmsintrp.c:642:22 #1 0x57d257 in _LUTeval16 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmslut.c:1330:14 #2 0x4f9108 in CachedXFORM /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:525:17 #3 0x4eff23 in cmsDoTransform /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:189:5 #4 0x4c7613 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/../cms_transform_fuzzer.c #5 0x5861d8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5 #6 0x5861d8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12 #7 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16 #8 0x41c6bd in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/lcms-2017-03-21-afl+0x41c6bd) 0x60800000098c is located 12 bytes to the right of 96-byte region [0x608000000920,0x608000000980) allocated by thread T0 here: #0 0x494dfd in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/lcms-2017-03-21-afl+0x494dfd) #1 0x5440f2 in _cmsMalloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmserr.c:267:12 #2 0x5440f2 in _cmsDupDefaultFn /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmserr.c:171:11 #3 0x574c98 in CLUTElemDup /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmslut.c:503:56 #4 0x57fa82 in cmsStageDup /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmslut.c:1257:25 #5 0x57fa82 in cmsPipelineCat /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmslut.c:1617:56 #6 0x53e155 in DefaultICCintents /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmscnvrt.c:628:14 #7 0x4f1414 in cmsCreateExtendedTransform /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:1059:11 #8 0x4f4be0 in cmsCreateMultiprofileTransformTHR /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:1175:12 #9 0x4f4be0 in cmsCreateTransformTHR /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:1216:12 #10 0x4f4be0 in cmsCreateTransform /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsxform.c:1226:12 #11 0x4c6f89 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/../cms_transform_fuzzer.c:31:30 #12 0x5861d8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5 #13 0x5861d8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12 #14 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16 SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/lcms-2017-03-21/build/BUILD/src/cmsintrp.c:642:22 in TetrahedralInterpFloat Shadow bytes around the buggy address: 0x0c107fff80e0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00 0x0c107fff80f0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00 0x0c107fff8100: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00 0x0c107fff8110: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00 0x0c107fff8120: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00 =>0x0c107fff8130: fa [fa] fa fa 00 00 00 00 00 00 00 00 00 00 00 00 0x0c107fff8140: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd 0x0c107fff8150: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fa 0x0c107fff8160: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd 0x0c107fff8170: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa 0x0c107fff8180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa Shadow byte legend (one shadow byte represents 8 application bytes): Addressable: 00 Partially addressable: 01 02 03 04 05 06 07 Heap left redzone: fa Freed heap region: fd Stack left redzone: f1 Stack mid redzone: f2 Stack right redzone: f3 Stack after return: f5 Stack use after scope: f8 Global redzone: f9 Global init order: f6 Poisoned by user: f7 Container overflow: fc Array cookie: ac Intra object redzone: bb ASan internal: fe Left alloca redzone: ca Right alloca redzone: cb Shadow gap: cc ==1744598==ABORTING执行AFL:
afl-fuzz -i ./seeds/ -o ./out -m none -d ./lcms-2017-03-21-afl @@
用AFL运行一个半小时,没有crash,代码覆盖率保持持续增长。
libarchive-2017-01-04
编译出现问题,暂时未解决。

libjpeg-turbo-07-2017
- 在fuzzer-test-suite根目录下执行
libjpeg-turbo-07-2017/build.sh asan- 生成的程序是:
- 运行这个程序:
./libjpeg-turbo-07-2017-afl
- 用AFL测试这个程序,这个程序主要用于代码覆盖率的比较。
bash afl-fuzz -i ./seeds/ -o ./out/ -m none ./libjpeg-turbo-07-2017-afl @@
libpng-1.2.56
运行程序:
运行提供的crash,输出如下,只报了一个read_error。
root@prodsec-HP-Z440-Workstation:/home/yiru/fuzzer-test-suite/program/libpng# ./libpng-1.2.56-afl oom-63efa8b5a2adf76dc225d62939db3337ff6774f1
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./libpng-1.2.56-afl < INPUT_FILE
or
./libpng-1.2.56-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./libpng-1.2.56-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 51 bytes from oom-63efa8b5a2adf76dc225d62939db3337ff6774f1
libpng error: read error
Execution successful
libssh-2017-1272
执行build.sh可能会报无法git到。手动git到本地
pip install abimap
apt-get install libkrb5-dev
pip install gssapi
apt-get install doxygen
mkdir build
cd build
git clone https://git.libssh.org/projects/libssh.git SRC
../build.sh asan
libxml2-v2.9.2

用提供的crash测试:
- crash-50b12d37d6968a2cd9eb3665d158d9a2fb1f6e28
./libxml2-v2.9.2-afl ../crash-50b12d37d6968a2cd9eb3665d158d9a2fb1f6e28
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./libxml2-v2.9.2-afl < INPUT_FILE
or
./libxml2-v2.9.2-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./libxml2-v2.9.2-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 60 bytes from ../crash-50b12d37d6968a2cd9eb3665d158d9a2fb1f6e28
=================================================================
==2750611==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x621000002500 at pc 0x000000524432 bp 0x7fffffffdd60 sp 0x7fffffffdd58
READ of size 1 at 0x621000002500 thread T0
#0 0x524431 in xmlParseXMLDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10666:2
#1 0x525dc9 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10771:2
#2 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#3 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#4 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#5 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#6 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41d83d in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x41d83d)
0x621000002500 is located 0 bytes to the right of 4096-byte region [0x621000001500,0x621000002500)
allocated by thread T0 here:
#0 0x495f7d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x495f7d)
#1 0x698be3 in xmlBufCreate /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/buf.c:136:32
#2 0x792c66 in xmlSwitchInputEncodingInt /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parserInternals.c:1196:34
#3 0x792ff2 in xmlSwitchToEncodingInt /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parserInternals.c:1272:12
#4 0x792ff2 in xmlSwitchToEncoding /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parserInternals.c:1300:13
#5 0x508081 in xmlParseEncodingDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10462:3
#6 0x523e2e in xmlParseXMLDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10630:5
#7 0x525dc9 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10771:2
#8 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#9 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#10 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#11 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#12 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10666:2 in xmlParseXMLDecl
Shadow bytes around the buggy address:
0x0c427fff8450: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8460: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8470: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8480: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8490: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c427fff84a0:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2750611==ABORTING
- crash-d8960e21ca40ea5dc60ad655000842376d4178a1
./libxml2-v2.9.2-afl ../crash-d8960e21ca40ea5dc60ad655000842376d4178a1
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./libxml2-v2.9.2-afl < INPUT_FILE
or
./libxml2-v2.9.2-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./libxml2-v2.9.2-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 313 bytes from ../crash-d8960e21ca40ea5dc60ad655000842376d4178a1
=================================================================
==2791320==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61900000057b at pc 0x000000744d0b bp 0x7fffffffd0a0 sp 0x7fffffffd098
READ of size 1 at 0x61900000057b thread T0
#0 0x744d0a in xmlDictComputeFastQKey /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/dict.c:489:18
#1 0x742b7a in xmlDictQLookup /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/dict.c:1093:12
#2 0x751822 in xmlSAX2StartElementNs /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/SAX2.c:2238:17
#3 0x51ed78 in xmlParseStartTag2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:9707:6
#4 0x515e9c in xmlParseElement /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10069:16
#5 0x5151d9 in xmlParseContent /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:9982:6
#6 0x516a98 in xmlParseElement /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10155:5
#7 0x5151d9 in xmlParseContent /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:9982:6
#8 0x516a98 in xmlParseElement /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10155:5
#9 0x5264b0 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10841:2
#10 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#11 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#12 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#13 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#14 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x41d83d in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x41d83d)
0x61900000057b is located 5 bytes to the left of 1048-byte region [0x619000000580,0x619000000998)
allocated by thread T0 here:
#0 0x495f7d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x495f7d)
#1 0x73f1ab in xmlDictAddString /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/dict.c:270:29
#2 0x73f1ab in xmlDictLookup /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/dict.c:923:11
#3 0x509518 in xmlDetectSAX2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:1067:21
#4 0x524e89 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10725:5
#5 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#6 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#7 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/dict.c:489:18 in xmlDictComputeFastQKey
Shadow bytes around the buggy address:
0x0c327fff8050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c327fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c327fff80b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff80c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff80d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff80e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff80f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2791320==ABORTING
- leak-bdbb2857b7a086f003db1c418e1d124181341fb1
./libxml2-v2.9.2-afl ../leak-bdbb2857b7a086f003db1c418e1d124181341fb1
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./libxml2-v2.9.2-afl < INPUT_FILE
or
./libxml2-v2.9.2-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./libxml2-v2.9.2-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 64 bytes from ../leak-bdbb2857b7a086f003db1c418e1d124181341fb1
Execution successful
=================================================================
==2799042==ERROR: LeakSanitizer: detected memory leaks
Indirect leak of 48 byte(s) in 1 object(s) allocated from:
#0 0x495f7d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x495f7d)
#1 0x59a5e6 in xmlNewDocElementContent /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/valid.c:952:34
#2 0x4ff354 in xmlParseElementMixedContentDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c
#3 0x502365 in xmlParseElementContentDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6624:16
#4 0x502dca in xmlParseElementDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6691:12
#5 0x503e8e in xmlParseMarkupDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6934:4
#6 0x527547 in xmlParseInternalSubset /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:8401:6
#7 0x525cd6 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10809:6
#8 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#9 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#10 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#11 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#12 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
Indirect leak of 48 byte(s) in 1 object(s) allocated from:
#0 0x495f7d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/libxml2-v2.9.2-afl+0x495f7d)
#1 0x59a5e6 in xmlNewDocElementContent /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/valid.c:952:34
#2 0x4ff228 in xmlParseElementMixedContentDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6194:18
#3 0x502365 in xmlParseElementContentDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6624:16
#4 0x502dca in xmlParseElementDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6691:12
#5 0x503e8e in xmlParseMarkupDecl /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:6934:4
#6 0x527547 in xmlParseInternalSubset /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:8401:6
#7 0x525cd6 in xmlParseDocument /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:10809:6
#8 0x53fcbd in xmlDoRead /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/BUILD/parser.c:15298:5
#9 0x4c8057 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/libxml2-v2.9.2/build/../target.cc:14:18
#10 0x87cdd8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#11 0x87cdd8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#12 0x7ffff7a440b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: 96 byte(s) leaked in 2 allocation(s).
llvm-libcxxabi-2017-01-27
这个网址已经无了,GitHub上应该已经合并到llvm-project下了。

尝试把llvm-project下的libcxxabi拷贝过来成为SRC,然后build.sh asan,
用提供的crash测试,发现没有crash。应该是已经修复了漏洞了。
openssl-1.0.1f
运行编译好的文件:
用提供的crash测试:
./openssl-1.0.1f-afl ../leak-268f0e85f4bc45cbaf4d257222b830eac18977f3
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./openssl-1.0.1f-afl < INPUT_FILE
or
./openssl-1.0.1f-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./openssl-1.0.1f-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 249 bytes from ../leak-268f0e85f4bc45cbaf4d257222b830eac18977f3
Execution successful
=================================================================
==3079777==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x495e2d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/openssl-1.0.1f-afl+0x495e2d)
#1 0x57678c in CRYPTO_malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/mem.c:308:8
#2 0x5cfe18 in sk_new /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/stack/stack.c:125:11
#3 0x5cfe18 in sk_new_null /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/stack/stack.c:117:9
#4 0x4dccab in ssl_parse_clienthello_use_srtp_ext /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/d1_srtp.c:345:7
#5 0x4cd5fe in ssl_parse_clienthello_tlsext /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/t1_lib.c:1419:7
#6 0x512bbd in ssl3_get_client_hello /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/s3_srvr.c:1180:8
#7 0x50dcfa in ssl3_accept /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/s3_srvr.c:357:9
#8 0x4c8062 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/../target.cc:34:3
#9 0x7f77a8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#10 0x7f77a8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#11 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
Indirect leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x495e2d in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/openssl-1.0.1f-afl+0x495e2d)
#1 0x57678c in CRYPTO_malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/mem.c:308:8
#2 0x5cfe38 in sk_new /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/stack/stack.c:127:17
#3 0x5cfe38 in sk_new_null /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/crypto/stack/stack.c:117:9
#4 0x4dccab in ssl_parse_clienthello_use_srtp_ext /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/d1_srtp.c:345:7
#5 0x4cd5fe in ssl_parse_clienthello_tlsext /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/t1_lib.c:1419:7
#6 0x512bbd in ssl3_get_client_hello /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/s3_srvr.c:1180:8
#7 0x50dcfa in ssl3_accept /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/BUILD/ssl/s3_srvr.c:357:9
#8 0x4c8062 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/openssl-1.0.1f/build/../target.cc:34:3
#9 0x7f77a8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#10 0x7f77a8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#11 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: 64 byte(s) leaked in 2 allocation(s).
openssl-1.0.2d
运行编好的程序:
用提供的crash测试触发断言错误:
openssl-1.1.0c
openthread-2018-02-27
需要安装2.68以上的Autoconf。
pcre2-10.00
同样的方法获得pcre2-10.00-afl
用AFL测试在我的环境下跑了近一个小时找到两个crash。
用程序运行crash,获得AddressSanitizer的输出:
./pcre2-10.00-afl out/crashes/id\:000000\,sig\:06\,src\:006518\,op\:havoc\,rep\:2 ======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./pcre2-10.00-afl < INPUT_FILE
or
./pcre2-10.00-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./pcre2-10.00-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 17 bytes from out/crashes/id:000000,sig:06,src:006518,op:havoc,rep:2
=================================================================
==24==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300000003f at pc 0x000000559e5d bp 0x7fff48498650 sp 0x7fff48498648
READ of size 1 at 0x60300000003f thread T0
==24==WARNING: invalid path to external symbolizer!
==24==WARNING: Failed to use and restart external symbolizer!
#0 0x559e5c (/home/program/pcre2/pcre2-10.00-afl+0x559e5c)
#1 0x517199 (/home/program/pcre2/pcre2-10.00-afl+0x517199)
#2 0x576990 (/home/program/pcre2/pcre2-10.00-afl+0x576990)
#3 0x4c73af (/home/program/pcre2/pcre2-10.00-afl+0x4c73af)
#4 0x5776b8 (/home/program/pcre2/pcre2-10.00-afl+0x5776b8)
#5 0x7f909fdfc83f (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#6 0x41c5fd (/home/program/pcre2/pcre2-10.00-afl+0x41c5fd)
0x60300000003f is located 1 bytes to the left of 18-byte region [0x603000000040,0x603000000052)
allocated by thread T0 here:
#0 0x4c44ad (/home/program/pcre2/pcre2-10.00-afl+0x4c44ad)
#1 0x4c6f61 (/home/program/pcre2/pcre2-10.00-afl+0x4c6f61)
#2 0x5776b8 (/home/program/pcre2/pcre2-10.00-afl+0x5776b8)
#3 0x7f909fdfc83f (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/program/pcre2/pcre2-10.00-afl+0x559e5c)
Shadow bytes around the buggy address:
0x0c067fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c067fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c067fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c067fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c067fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c067fff8000: fa fa 00 00 01 fa fa[fa]00 00 02 fa fa fa 00 00
0x0c067fff8010: 02 fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==24==ABORTING
用AFL -d模式运行一个半小时能够发现两个crash。
proj4-2017-08-14
运行编译好的程序:
用提供的crash测试:leak-7c19589a27e15f3432d245c7685bd518693e70d3
./proj4-2017-08-14-afl ../leak-7c19589a27e15f3432d245c7685bd518693e70d3
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./proj4-2017-08-14-afl < INPUT_FILE
or
./proj4-2017-08-14-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./proj4-2017-08-14-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 157 bytes from ../leak-7c19589a27e15f3432d245c7685bd518693e70d3
Execution successful
=================================================================
==101559==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 640 byte(s) in 1 object(s) allocated from:
#0 0x495ead in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/proj4-2017-08-14-afl+0x495ead)
#1 0x4cda86 in pj_malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_malloc.c:57:21
#2 0x4cda86 in pj_calloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_malloc.c:80:17
#3 0x563a9e in pj_urm5 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/PJ_urm5.c:39:5
#4 0x4c9cc7 in pj_init_ctx /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_init.c:502:17
#5 0x4c9198 in pj_init_plus_ctx /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_init.c:409:14
#6 0x4c8168 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/test/fuzzers/standard_fuzzer.cpp:89:21
#7 0x571fc8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x571fc8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
Indirect leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x495ead in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/proj4-2017-08-14-afl+0x495ead)
#1 0x4cda86 in pj_malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_malloc.c:57:21
#2 0x4cda86 in pj_calloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_malloc.c:80:17
#3 0x563b3c in pj_projection_specific_setup_urm5 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/PJ_urm5.c:41:27
#4 0x4cb7ed in pj_init_ctx /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_init.c:726:21
#5 0x4c9198 in pj_init_plus_ctx /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/src/pj_init.c:409:14
#6 0x4c8168 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/proj4-2017-08-14/build/BUILD/test/fuzzers/standard_fuzzer.cpp:89:21
#7 0x571fc8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x571fc8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: 672 byte(s) leaked in 2 allocation(s).
用AFL -d模式运行五个多小时,没有crash。

re2-2014-12-09
运行编译好的程序:
 execute this:
./re2-2014-12-09-afl < INPUT_FILE
or
./re2-2014-12-09-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./re2-2014-12-09-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 17 bytes from ../crash-a23ed2a04358b9c070c603a5af6ae2b34598664a
re2/dfa.cc:474: DFA out of memory: prog size 17145 mem 2727402
=================================================================
==3887751==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000128 at pc 0x0000005327bb bp 0x7fffffffa1d0 sp 0x7fffffffa1c8
WRITE of size 8 at 0x602000000128 thread T0
#0 0x5327ba in re2::NFA::Search(re2::StringPiece const&, re2::StringPiece const&, bool, bool, re2::StringPiece*, int) /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:532:31
#1 0x535208 in re2::Prog::SearchNFA(re2::StringPiece const&, re2::StringPiece const&, re2::Prog::Anchor, re2::Prog::MatchKind, re2::StringPiece*, int) /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:701:12
#2 0x4d55cd in re2::RE2::Match(re2::StringPiece const&, int, int, re2::RE2::Anchor, re2::StringPiece*, int) const /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/re2.cc:768:19
#3 0x4d01ac in re2::RE2::DoMatch(re2::StringPiece const&, re2::RE2::Anchor, int*, re2::RE2::Arg const* const*, int) const /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/re2.cc:817:8
#4 0x4c87c5 in operator() /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/variadic_function.h:15:12
#5 0x4c87c5 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/../target.cc:27:5
#6 0x5607d8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#7 0x5607d8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#8 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#9 0x41d83d in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/re2-2014-12-09-afl+0x41d83d)
0x602000000128 is located 8 bytes to the left of 16-byte region [0x602000000130,0x602000000140)
allocated by thread T0 here:
#0 0x4c56ed in operator new(unsigned long) (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/re2-2014-12-09-afl+0x4c56ed)
#1 0x52fb1d in AllocThread /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:167:9
#2 0x52fb1d in re2::NFA::AddToThreadq(re2::SparseArray<re2::NFA::Thread*>*, int, int, char const*, char const**) /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:234:11
#3 0x531894 in re2::NFA::Search(re2::StringPiece const&, re2::StringPiece const&, bool, bool, re2::StringPiece*, int) /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:585:7
#4 0x535208 in re2::Prog::SearchNFA(re2::StringPiece const&, re2::StringPiece const&, re2::Prog::Anchor, re2::Prog::MatchKind, re2::StringPiece*, int) /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:701:12
#5 0x4d55cd in re2::RE2::Match(re2::StringPiece const&, int, int, re2::RE2::Anchor, re2::StringPiece*, int) const /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/re2.cc:768:19
#6 0x4d01ac in re2::RE2::DoMatch(re2::StringPiece const&, re2::RE2::Anchor, int*, re2::RE2::Arg const* const*, int) const /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/re2.cc:817:8
#7 0x4c87c5 in operator() /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/variadic_function.h:15:12
#8 0x4c87c5 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/../target.cc:27:5
#9 0x5607d8 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#10 0x5607d8 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#11 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/re2-2014-12-09/build/BUILD/re2/nfa.cc:532:31 in re2::NFA::Search(re2::StringPiece const&, re2::StringPiece const&, bool, bool, re2::StringPiece*, int)
Shadow bytes around the buggy address:
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa fd fd fa fa fd fd fa fa 00 00 fa fa fd fd
0x0c047fff8010: fa fa fd fd fa fa fd fd fa fa 01 fa fa fa fd fa
=>0x0c047fff8020: fa fa 00 00 fa[fa]00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8030: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8040: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8050: fa fa 00 00 fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3887751==ABORTING
用AFL -d模式运行一个半小时,没有crash,代码覆盖率持续增长。
sqlite-2016-11-14
运行编译好的程序
运行提供的crash:
- crash-0adc497ccfcc1a4d5e031b735c599df0cae3f4eb
/sqlite-2016-11-14-afl ../crash-0adc497ccfcc1a4d5e031b735c599df0cae3f4eb
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./sqlite-2016-11-14-afl < INPUT_FILE
or
./sqlite-2016-11-14-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./sqlite-2016-11-14-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 88 bytes from ../crash-0adc497ccfcc1a4d5e031b735c599df0cae3f4eb
=================================================================
==3326656==ERROR: AddressSanitizer: heap-use-after-free on address 0x6190000028f8 at pc 0x00000084443c bp 0x7fffffffbf70 sp 0x7fffffffbf68
READ of size 8 at 0x6190000028f8 thread T0
#0 0x84443b in exprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127734:22
#1 0x7dfc16 in sqlite3WhereExprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127858:5
#2 0x7dfc16 in sqlite3WhereBegin /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:132407:3
#3 0x6d0a03 in sqlite3Select /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:119628:14
#4 0x6672b5 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135421:3
#5 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#6 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#7 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#8 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#9 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#10 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#11 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#12 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#13 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#14 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x41d67d in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x41d67d)
0x6190000028f8 is located 120 bytes inside of 1032-byte region [0x619000002880,0x619000002c88)
freed by thread T0 here:
#0 0x495b3d in free (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495b3d)
#1 0x4cc2a1 in sqlite3_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24358:5
#2 0x4cc2a1 in sqlite3DbFree /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24401:3
#3 0x839233 in whereClauseInsert /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:126538:7
#4 0x841222 in exprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127686:16
#5 0x7dfc16 in sqlite3WhereExprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127858:5
#6 0x7dfc16 in sqlite3WhereBegin /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:132407:3
#7 0x6d0a03 in sqlite3Select /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:119628:14
#8 0x6672b5 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135421:3
#9 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#10 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#11 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#12 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#13 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#14 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#15 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#16 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#17 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#18 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x495dbd in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495dbd)
#1 0x8d38c3 in sqlite3MemMalloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:20478:7
#2 0x4ceefd in mallocWithAlarm /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24147:7
#3 0x4ceefd in sqlite3Malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24178:5
#4 0x541ca5 in dbMallocRawFinish /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24504:7
#5 0x8391c3 in sqlite3DbMallocRawNN /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24572:10
#6 0x8391c3 in whereClauseInsert /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:126528:14
#7 0x841222 in exprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127686:16
#8 0x7dfc16 in sqlite3WhereExprAnalyze /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127858:5
#9 0x7dfc16 in sqlite3WhereBegin /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:132407:3
#10 0x6d0a03 in sqlite3Select /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:119628:14
#11 0x6672b5 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135421:3
#12 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#13 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#14 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#15 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#16 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#17 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#18 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#19 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#20 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#21 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-use-after-free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:127734:22 in exprAnalyze
Shadow bytes around the buggy address:
0x0c327fff84c0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff84d0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff84e0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fa
0x0c327fff84f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8500: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c327fff8510: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd[fd]
0x0c327fff8520: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff8530: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff8540: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff8550: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fff8560: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3326656==ABORTING
- crash-1066e42866aad3a04e6851dc494ad54bc31b9f78
./sqlite-2016-11-14-afl ../crash-1066e42866aad3a04e6851dc494ad54bc31b9f78
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./sqlite-2016-11-14-afl < INPUT_FILE
or
./sqlite-2016-11-14-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./sqlite-2016-11-14-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 64 bytes from ../crash-1066e42866aad3a04e6851dc494ad54bc31b9f78
=================================================================
==3414715==ERROR: AddressSanitizer: heap-use-after-free on address 0x60d0000004b3 at pc 0x00000049520a bp 0x7fffffffcdf0 sp 0x7fffffffc5b8
READ of size 1 at 0x60d0000004b3 thread T0
#0 0x495209 in __asan_memcpy (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495209)
#1 0x4d27ea in sqlite3VXPrintf /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c
#2 0x512ceb in sqlite3VMPrintf /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25667:3
#3 0x512ceb in sqlite3ErrorMsg /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:27516:10
#4 0x5238ca in yy_syntax_error /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136445:3
#5 0x5238ca in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136605:7
#6 0x5238ca in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#7 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#8 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#9 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#10 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#11 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#12 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#13 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#14 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x41d67d in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x41d67d)
0x60d0000004b3 is located 99 bytes inside of 136-byte region [0x60d000000450,0x60d0000004d8)
freed by thread T0 here:
#0 0x495b3d in free (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495b3d)
#1 0x4cc2a1 in sqlite3_free /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24358:5
#2 0x4cc2a1 in sqlite3DbFree /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24401:3
#3 0x7b1876 in sqlite3NestedParse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:98638:3
#4 0x6bd079 in sqlite3CreateIndex /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:101731:5
#5 0x6691c3 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135304:2
#6 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#7 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#8 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#9 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#10 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#11 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#12 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#13 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#14 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#15 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x495dbd in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495dbd)
#1 0x8d38c3 in sqlite3MemMalloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:20478:7
#2 0x4ceefd in mallocWithAlarm /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24147:7
#3 0x4ceefd in sqlite3Malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24178:5
#4 0x541ca5 in dbMallocRawFinish /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24504:7
#5 0x54113a in sqlite3DbMallocRawNN /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24572:10
#6 0x54113a in sqlite3DbRealloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24584:21
#7 0x54113a in sqlite3StrAccumEnlarge /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25523:14
#8 0x5408c9 in enlargeAndAppend /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25563:7
#9 0x4d5dbc in sqlite3StrAccumAppend /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25581:5
#10 0x4d5dbc in sqlite3VXPrintf /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25476:5
#11 0x7b1501 in sqlite3VMPrintf /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:25667:3
#12 0x7b1501 in sqlite3NestedParse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:98628:10
#13 0x6bd079 in sqlite3CreateIndex /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:101731:5
#14 0x6691c3 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135304:2
#15 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#16 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#17 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#18 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#19 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#20 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#21 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#22 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#23 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#24 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-use-after-free (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495209) in __asan_memcpy
Shadow bytes around the buggy address:
0x0c1a7fff8040: 00 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa
0x0c1a7fff8050: fa fa fa fa fa fa 00 00 00 00 00 00 00 00 00 00
0x0c1a7fff8060: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c1a7fff8070: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1a7fff8080: fd fa fa fa fa fa fa fa fa fa fd fd fd fd fd fd
=>0x0c1a7fff8090: fd fd fd fd fd fd[fd]fd fd fd fd fa fa fa fa fa
0x0c1a7fff80a0: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1a7fff80b0: fd fd fd fd fd fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1a7fff80e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3414715==ABORTING
- leak-b0276985af5aa23c98d9abf33856ce069ef600e2
./sqlite-2016-11-14-afl ../leak-b0276985af5aa23c98d9abf33856ce069ef600e2
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./sqlite-2016-11-14-afl < INPUT_FILE
or
./sqlite-2016-11-14-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./sqlite-2016-11-14-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 2716 bytes from ../leak-b0276985af5aa23c98d9abf33856ce069ef600e2
Execution successful
=================================================================
==3495696==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x495dbd in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/sqlite-2016-11-14-afl+0x495dbd)
#1 0x8d38c3 in sqlite3MemMalloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:20478:7
#2 0x4ceefd in mallocWithAlarm /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24147:7
#3 0x4ceefd in sqlite3Malloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24178:5
#4 0x541ca5 in dbMallocRawFinish /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24504:7
#5 0x733862 in sqlite3DbMallocRawNN /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:24572:10
#6 0x733862 in sqlite3ExprAlloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:90536:10
#7 0x6665f5 in yy_reduce /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:135791:28
#8 0x52376c in sqlite3Parser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:136530:7
#9 0x52376c in sqlite3RunParser /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:137477:7
#10 0x65de77 in sqlite3Prepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114208:5
#11 0x51e7ed in sqlite3LockAndPrepare /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114299:8
#12 0x51abbf in sqlite3_prepare_v2 /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:114375:8
#13 0x51abbf in sqlite3_exec /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../sqlite3.c:109705:10
#14 0x8dcaa0 in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/sqlite-2016-11-14/build/../ossfuzz.c:78:3
#15 0x8dd778 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#16 0x8dd778 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#17 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: 80 byte(s) leaked in 1 allocation(s).
用AFL -d模式运行一个半小时没有crash,代码覆盖率从第4分钟之后就没有增加了。
vorbis-2017-12-11
运行编译好的程序
运行提供的crash:
- crash-8c5dea6410b0fb0b21ff968a9966a0bd7956405f
./vorbis-2017-12-11-afl ../crash-8c5dea6410b0fb0b21ff968a9966a0bd7956405f
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./vorbis-2017-12-11-afl < INPUT_FILE
or
./vorbis-2017-12-11-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./vorbis-2017-12-11-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 4096 bytes from ../crash-8c5dea6410b0fb0b21ff968a9966a0bd7956405f
=================================================================
==3088035==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61d000006280 at pc 0x000000511bd0 bp 0x7fffffffbf80 sp 0x7fffffffbf78
READ of size 16 at 0x61d000006280 thread T0
#0 0x511bcf in vorbis_book_decodev_add /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/codebook.c:407:17
#1 0x54e37a in _01inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:693:20
#2 0x552044 in res1_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:757:12
#3 0x559b9a in mapping0_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/mapping0.c:748:5
#4 0x4d13ca in _fetch_and_process_packet /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:705:15
#5 0x4d32b7 in ov_read_filter /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:1976:15
#6 0x4d3f45 in ov_read /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:2096:10
#7 0x4c71ed in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/SRC/oss-fuzz/projects/vorbis/decode_fuzzer.cc:41:19
#8 0x4c7d18 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#9 0x4c7d18 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#10 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x41c6ad in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/vorbis-2017-12-11-afl+0x41c6ad)
0x61d000006280 is located 0 bytes to the right of 2048-byte region [0x61d000005a80,0x61d000006280)
allocated by thread T0 here:
#0 0x494ded in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/vorbis-2017-12-11-afl+0x494ded)
#1 0x4dd666 in _vorbis_block_alloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/block.c:115:20
#2 0x4f1d6e in vorbis_synthesis /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/synthesis.c:82:16
#3 0x4d13ca in _fetch_and_process_packet /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:705:15
#4 0x4d32b7 in ov_read_filter /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:1976:15
#5 0x4d3f45 in ov_read /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:2096:10
#6 0x4c71ed in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/SRC/oss-fuzz/projects/vorbis/decode_fuzzer.cc:41:19
#7 0x4c7d18 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x4c7d18 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/codebook.c:407:17 in vorbis_book_decodev_add
Shadow bytes around the buggy address:
0x0c3a7fff8c00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8c10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8c20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8c30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8c40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c3a7fff8c50:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8c60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8c70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8c80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8c90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8ca0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3088035==ABORTING
- crash-23c2d78e497bf4aebe5859e3092657cb0af4c299
./vorbis-2017-12-11-afl ../crash-23c2d78e497bf4aebe5859e3092657cb0af4c299
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./vorbis-2017-12-11-afl < INPUT_FILE
or
./vorbis-2017-12-11-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./vorbis-2017-12-11-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 3990 bytes from ../crash-23c2d78e497bf4aebe5859e3092657cb0af4c299
AddressSanitizer:DEADLYSIGNAL
=================================================================
==3088224==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x00000054e25f bp 0x7fffffffbff0 sp 0x7fffffffbe40 T0)
==3088224==The signal is caused by a READ memory access.
==3088224==Hint: this fault was caused by a dereference of a high value address (see register values below). Dissassemble the provided pc to learn which register was used.
#0 0x54e25f in _01inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:690:35
#1 0x552044 in res1_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:757:12
#2 0x559b9a in mapping0_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/mapping0.c:748:5
#3 0x4d13ca in _fetch_and_process_packet /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:705:15
#4 0x4d32b7 in ov_read_filter /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:1976:15
#5 0x4d3f45 in ov_read /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:2096:10
#6 0x4c71ed in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/SRC/oss-fuzz/projects/vorbis/decode_fuzzer.cc:41:19
#7 0x4c7d18 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x4c7d18 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#10 0x41c6ad in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/vorbis-2017-12-11-afl+0x41c6ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:690:35 in _01inverse
==3088224==ABORTING
- crash-e86e0482b8d66f924e50e62f5d7cc36a0acb03a7
/vorbis-2017-12-11-afl ../crash-e86e0482b8d66f924e50e62f5d7cc36a0acb03a7
======================= INFO =========================
This binary is built for AFL-fuzz.
To run the target function on individual input(s) execute this:
./vorbis-2017-12-11-afl < INPUT_FILE
or
./vorbis-2017-12-11-afl INPUT_FILE1 [INPUT_FILE2 ... ]
To fuzz with afl-fuzz execute this:
afl-fuzz [afl-flags] ./vorbis-2017-12-11-afl [-N]
afl-fuzz will run N iterations before re-spawning the process (default: 1000)
======================================================
Reading 321 bytes from ../crash-e86e0482b8d66f924e50e62f5d7cc36a0acb03a7
=================================================================
==3088301==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x619000000980 at pc 0x00000051261e bp 0x7fffffffbd90 sp 0x7fffffffbd88
READ of size 4 at 0x619000000980 thread T0
#0 0x51261d in vorbis_book_decodevv_add /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/codebook.c:479:24
#1 0x554464 in res2_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/res0.c:843:18
#2 0x559b9a in mapping0_inverse /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/mapping0.c:748:5
#3 0x4d13ca in _fetch_and_process_packet /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:705:15
#4 0x4d32b7 in ov_read_filter /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:1976:15
#5 0x4d3f45 in ov_read /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:2096:10
#6 0x4c71ed in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/SRC/oss-fuzz/projects/vorbis/decode_fuzzer.cc:41:19
#7 0x4c7d18 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x4c7d18 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#10 0x41c6ad in _start (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/vorbis-2017-12-11-afl+0x41c6ad)
0x619000000980 is located 0 bytes to the right of 1024-byte region [0x619000000580,0x619000000980)
allocated by thread T0 here:
#0 0x494ded in malloc (/home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/vorbis-2017-12-11-afl+0x494ded)
#1 0x4dd666 in _vorbis_block_alloc /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/block.c:115:20
#2 0x4f1d6e in vorbis_synthesis /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/synthesis.c:82:16
#3 0x4d13ca in _fetch_and_process_packet /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:705:15
#4 0x4d32b7 in ov_read_filter /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:1976:15
#5 0x4d3f45 in ov_read /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/vorbisfile.c:2096:10
#6 0x4c71ed in LLVMFuzzerTestOneInput /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/SRC/oss-fuzz/projects/vorbis/decode_fuzzer.cc:41:19
#7 0x4c7d18 in ExecuteFilesOnyByOne /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:216:5
#8 0x4c7d18 in main /home/yiru/fuzzer-test-suite/libfuzzer/libfuzzer-workshop/libFuzzer/Fuzzer/afl/afl_driver.cpp:253:12
#9 0x7ffff7a600b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yiru/fuzzer-test-suite/fuzzer-test-suite/vorbis-2017-12-11/build/BUILD/vorbis/lib/codebook.c:479:24 in vorbis_book_decodevv_add
Shadow bytes around the buggy address:
0x0c327fff80e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff80f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8100: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c327fff8130:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff8150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8160: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3088301==ABORTING
用AFL -d模式测试,运行6个小时,没有crash。
woff2-2016-05-06
运行编译好的程序:
测试提供的crash,有AddressSanitizer输出,提供的oom那个文件执行后没有报错。
用AFL运行一个半小时,没有crash,代码覆盖率也很低。
wpantund-2018-02-27
用coverage模式编译:
用c-ares这个程序测试,因为它能很快出现crash。初始测试用例为空文件时,afl版本的程序1分钟内能够发现crash。
-
尝试:custom-build.sh中FUZZING_ENGINE为afl, common.sh中FUZZING_ENGINE为coverage,build.sh asan
编译结果运行:

用AFL跑出来的crash测试,有AddressSanitizer信息输出。
用AFL测试,使用-Q模式会报forkserver超时。不适用-Q模式会报没有插桩。使用-n模式可以跑。跑半个小时出现了crash。运行跑出来的crash有AddressSanitizer信息输出。

-
尝试:common.sh中FUZZING_ENGINE为coverage,build.sh
此时不加asan这个选项,不会执行custom-build.sh中的逻辑,
编译结果运行同上。用AFL跑出来的crash测试,没有crash输出。用AFL测试,使用-Q模式可以跑。但是跑了两个小时没有crash。 -
尝试:custom-build.sh中FUZZING_ENGINE为libfuzzer, common.sh中FUZZING_ENGINE为coverage,build.sh asan。用AFL跑出来的crash测试,有AddressSanitizer信息输出。用AFL测试,使用-Q模式会报forkserver超时。不适用-Q模式会报没有插桩。使用-n模式可以跑。跑了两个小时没有crash。








 文章记录了使用AFL编译和测试Google Fuzzer数据集中多个程序的过程,包括编译细节、AddressSanitizer检测出的内存错误及运行AFL进行模糊测试的实例。
文章记录了使用AFL编译和测试Google Fuzzer数据集中多个程序的过程,包括编译细节、AddressSanitizer检测出的内存错误及运行AFL进行模糊测试的实例。









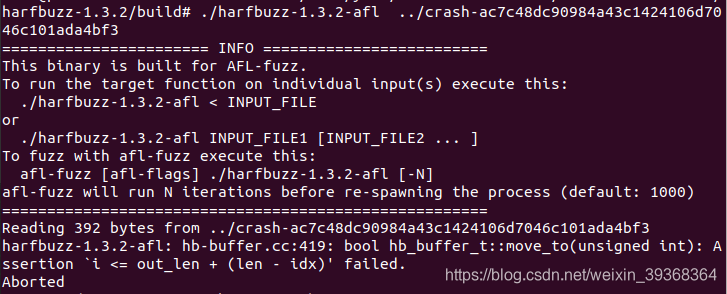







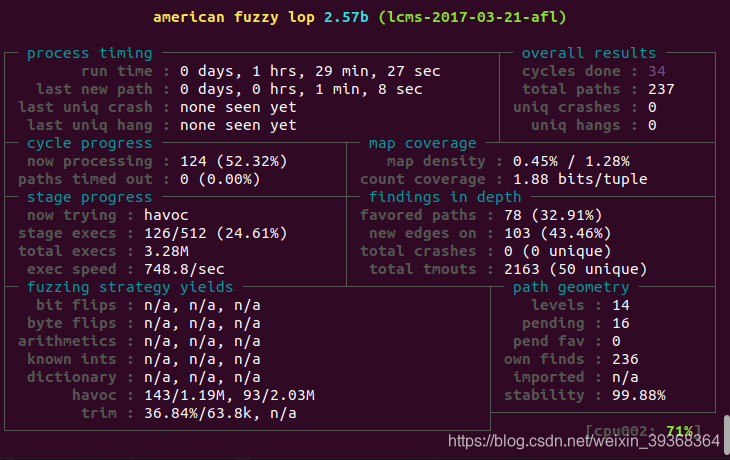






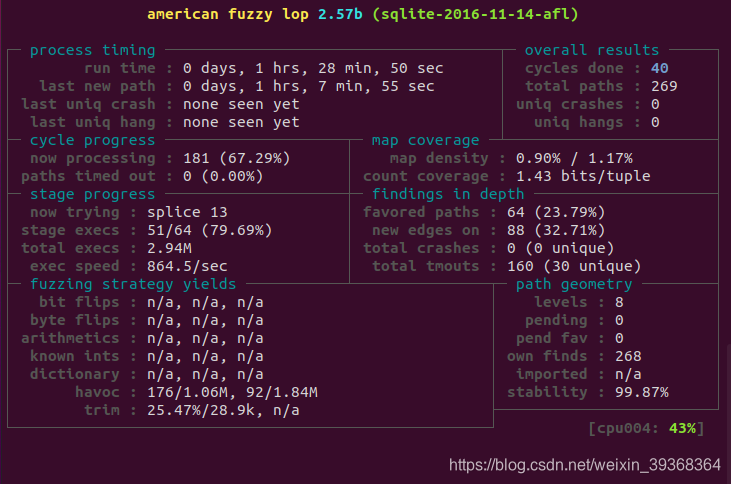





















 673
673

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








