指采用IPSEC协议来实现远程接入的一种XXX技术,IPSec全称为Internet Protocol Security,是由Internet Engineering Task Force (IETF) 定义的安全标准框架,在公网上为两个私有网络提供安全通信通道,通过加密通道保证连接的安全——在两个公共网关间提供私密数据封包服务,
配置采用IKE协商方式建立IPSec隧道的基本步骤如下:
(1)配置接口的IP地址和到对端的静态路由,保证两端路由可达。
(2)配置ACL,以定义需要IPSec保护的数据流。
(3)配置IPSec安全提议,定义IPSec的保护方法。
(4)配置IKE对等体,确定对等体间IKE协商时的参数。
(5)配置安全策略,并引用ACL、 IPSec安全提议和IKE对等体,确定对每种数据流采取的保护方法。
(6)在接口上应用安全策略组,使接口具有IPSec的保护功能。
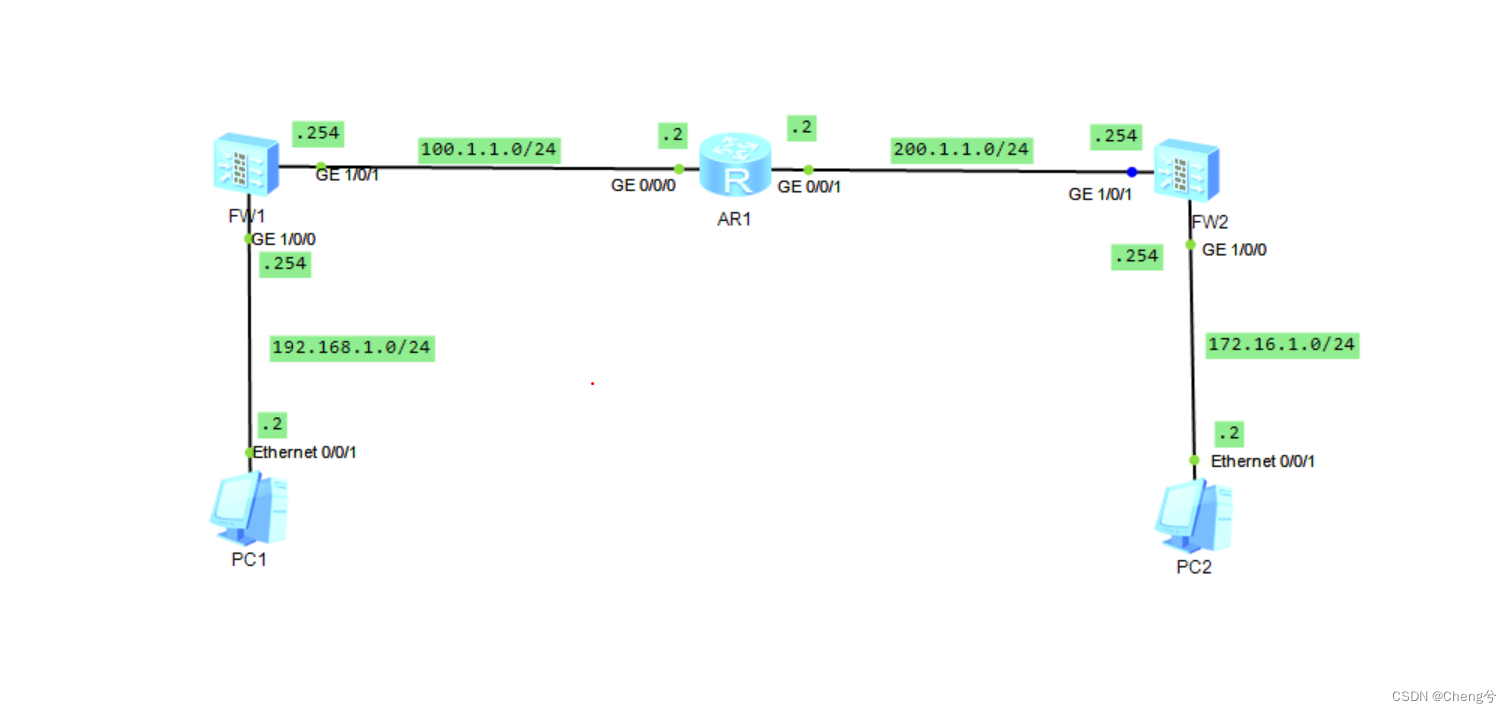
要求:PC1和PC2通过IPSCE XXX加密通道实现通信
AR1
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]int g0/0/0
[Huawei-GigabitEthernet0/0/0]ip address 100.1.1.2 24
[Huawei-GigabitEthernet0/0/0]q
[Huawei]int g0/0/1
[Huawei-GigabitEthernet0/0/1]
[Huawei-GigabitEthernet0/0/1]ip address 200.1.1.2 24
[Huawei-GigabitEthernet0/0/1]q
[Huawei]PC1
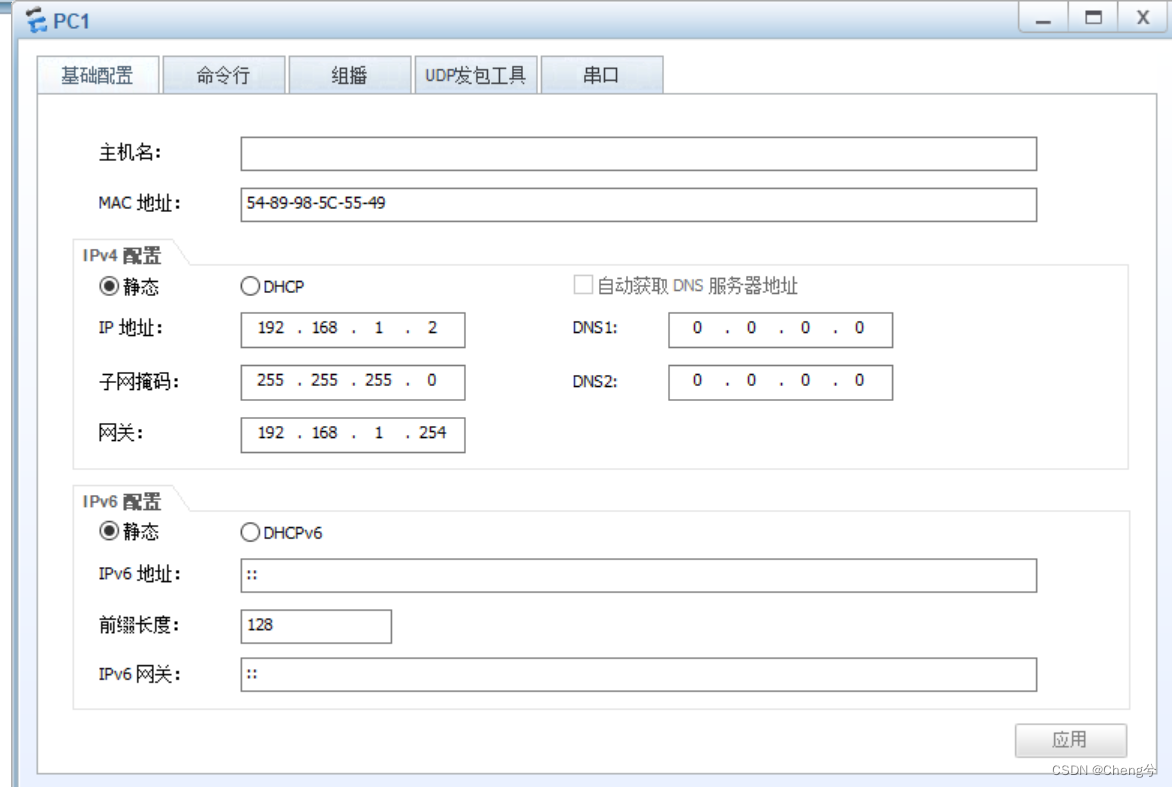
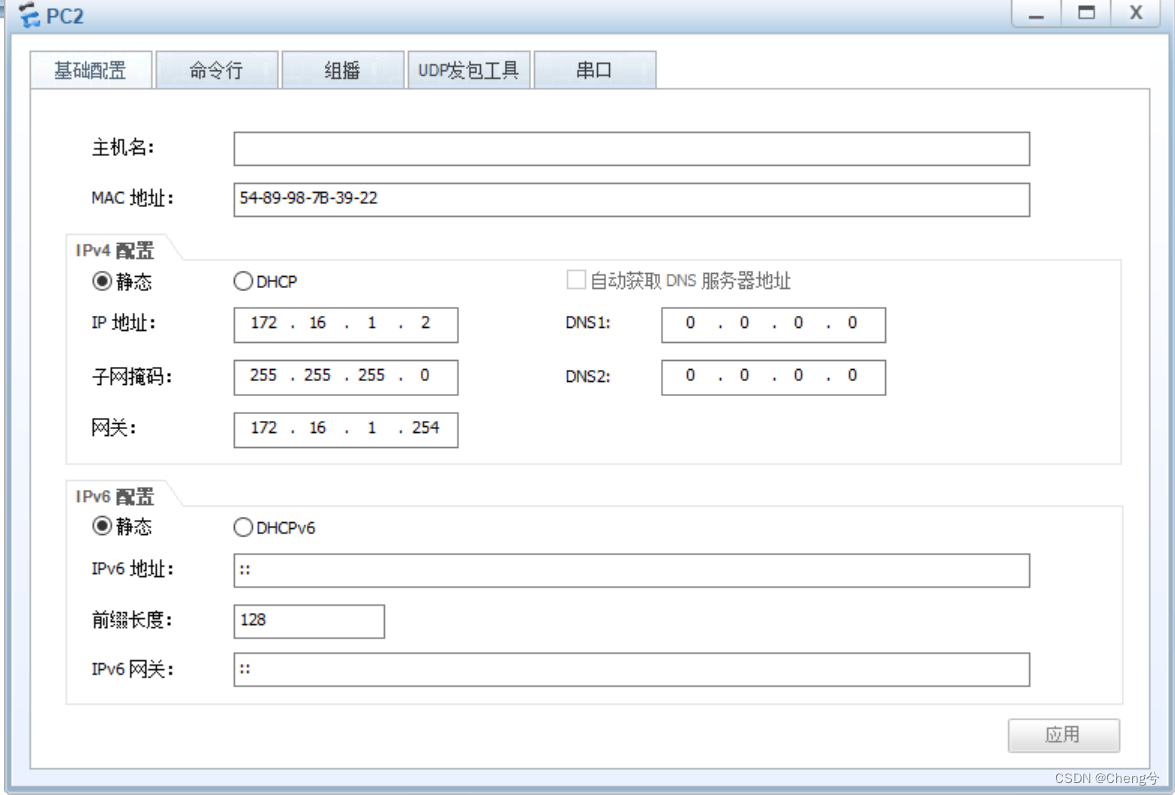
PC2
FW1
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info-center enable #清除广告
Info: Saving log files...
Info: Information center is disabled.
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]undo shutdown #打开接口
[USG6000V1-GigabitEthernet1/0/0]ip address 192.168.1.254 24 #配IP地址
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]service-manage ping permit
[USG6000V1-GigabitEthernet1/0/0]q
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip address 100.1.1.254 24
[USG6000V1-GigabitEthernet1/0/1]undo shutdown
[USG6000V1-GigabitEthernet1/0/1]service-manage ping permit
[USG6000V1-GigabitEthernet1/0/1]q
[USG6000V1]firewall zone trust #设置安全区域
[USG6000V1-zone-trust]add interface g1/0/0 #把接口添加到接口
[USG6000V1-zone-trust]q
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add interface g1/0/1
[USG6000V1-zone-untrust]q
[USG6000V1]
[USG6000V1]ip route-static 0.0.0.0 0 100.1.1.2 #配置缺省路由
[USG6000V1]se
[USG6000V1]security-policy #配置安全策略
[USG6000V1-policy-security]rule name trust_untrust #信任区到非信任区
[USG6000V1-policy-security-rule-trust_untrust]source-zone trust
[USG6000V1-policy-security-rule-trust_untrust]source-address 192.168.1.0 24
[USG6000V1-policy-security-rule-trust_untrust]destination-zone untrust
[USG6000V1-policy-security-rule-trust_untrust]action permit
[USG6000V1-policy-security-rule-trust_untrust]q
[USG6000V1-policy-security]rule name untrust_trust #非信任区到信任区
[USG6000V1-policy-security-rule-untrust_trust]source-zone untrust
[USG6000V1-policy-security-rule-untrust_trust]source-address 172.16.1.0 24
[USG6000V1-policy-security-rule-untrust_trust]destination-zone trust
[USG6000V1-policy-security-rule-untrust_trust]action permit
[USG6000V1-policy-security-rule-untrust_trust]q
[USG6000V1-policy-security]rule name local_untrust #本地到非信任区
[USG6000V1-policy-security-rule-local_untrust]source-zone local
[USG6000V1-policy-security-rule-local_untrust]destination-zone untrust
[USG6000V1-policy-security-rule-local_untrust]destination-address 200.1.1.254 32
[USG6000V1-policy-security-rule-local_untrust]source-address 100.1.1.254 32
[USG6000V1-policy-security-rule-local_untrust]action permit
[USG6000V1-policy-security-rule-local_untrust]q
[USG6000V1-policy-security]rule name untrust_local #非信任区到本地
[USG6000V1-policy-security-rule-untrust_local]source-zone untrust
[USG6000V1-policy-security-rule-untrust_local]source-address 200.1.1.254 32
[USG6000V1-policy-security-rule-untrust_local]destination-zone local
[USG6000V1-policy-security-rule-untrust_local]destination-address 100.1.1.254 32
[USG6000V1-policy-security-rule-untrust_local]action permit
[USG6000V1]nat-policy #配置NAT-easy-ip
[USG6000V1-policy-nat]rule name nopat
[USG6000V1-policy-nat-rule-nopat]source-zone trust
[USG6000V1-policy-nat-rule-nopat]egress-interface g1/0/1
[USG6000V1-policy-nat-rule-nopat]source-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-nopat]destination-zone untrust
[USG6000V1-policy-nat-rule-nopat]destination-address 172.16.1.0 24
[USG6000V1-policy-nat-rule-nopat]action no-nat
[USG6000V1-policy-nat-rule-nopat]q
[USG6000V1-policy-nat]rule name nat
[USG6000V1-policy-nat-rule-nat]source-zone trust
[USG6000V1-policy-nat-rule-nat]source-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-nat]destination-zone untrust
[USG6000V1-policy-nat-rule-nat]egress-interface g1/0/1
[USG6000V1-policy-nat-rule-nat]action source-nat easy-ip
[USG6000V1-policy-nat-rule-nat]q
[USG6000V1]ike proposal 10 #创建IKE提议,编号为10
[USG6000V1-ike-proposal-10]authentication-method pre-share #认证模式为预共享
[USG6000V1-ike-proposal-10]authentication-algorithm sha2-256 #认证算法为sha2-256
[USG6000V1-ike-proposal-10]encryption-algorithm aes-256 #加密算法为aes-256
[USG6000V1-ike-proposal-10]dh group14 #配置DH算法参数
[USG6000V1-ike-proposal-10]q
[USG6000V1]ike peer huawei #创建IKE对等体
[USG6000V1-ike-peer-huawei]ike-proposal 10 #引用ike安全提议
[USG6000V1-ike-peer-huawei]pre-shared-key abc-123 #预共享密钥
[USG6000V1-ike-peer-huawei]remote-address 200.1.1.254 #远端地址
[USG6000V1-ike-peer-huawei]q
[USG6000V1]ipsec proposal huawei-set #配置ipsec安全提议名为huawei-set
[USG6000V1-ipsec-proposal-huawei-set]encapsulation-mode tunnel #配置报文的IPSec封装模式为隧道模式
[USG6000V1-ipsec-proposal-huawei-set]transform esp #传输协议设置为esp默认也是esp
[USG6000V1-ipsec-proposal-huawei-set]esp encryption-algorithm aes-256
[USG6000V1-ipsec-proposal-huawei-set]esp authentication-algorithm sha2-256
[USG6000V1-ipsec-proposal-huawei-set]q
[USG6000V1]acl 3000 #配置感兴趣流
[USG6000V1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination
172.16.1.0 0.0.0.255
[USG6000V1-acl-adv-3000]q
[USG6000V1]ipsec policy huawei-map 10 isakmp #配置IKE动态协商方式安全策略
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]ike-peer huawei #引入ike对等体
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]proposal huawei-set #引入ipsec安全提议
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]security acl 3000 #引入感兴趣流
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]q
[USG6000V1]int g1/0/1 #接口上应用安全策略组
[USG6000V1-GigabitEthernet1/0/1]ipsec policy huawei-map
[USG6000V1-GigabitEthernet1/0/1]q
[USG6000V1]FW2 (与FW1大致相同)
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info-center enable
Info: Saving log files...
Info: Information center is disabled.
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]undo shutdown
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]ip address 172.16.1.254 24
[USG6000V1-GigabitEthernet1/0/0]service-manage ping permit
[USG6000V1-GigabitEthernet1/0/0]q
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]undo shutdown
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[USG6000V1-GigabitEthernet1/0/1]ip address 200.1.1.254 24
[USG6000V1-GigabitEthernet1/0/1]service-manage ping permit
[USG6000V1-GigabitEthernet1/0/1]q
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface g1/0/0
[USG6000V1-zone-trust]q
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add interface g1/0/1
[USG6000V1-zone-untrust]q
[USG6000V1]IP route-static 0.0.0.0 0 200.1.1.2
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name trust_untrust
[USG6000V1-policy-security-rule-trust_untrust]source-zone trust
[USG6000V1-policy-security-rule-trust_untrust]source-address 172.16.1.0 24
[USG6000V1-policy-security-rule-trust_untrust]destination-zone untrust
[USG6000V1-policy-security-rule-trust_untrust]access-authentication
[USG6000V1-policy-security-rule-trust_untrust]action permit
[USG6000V1-policy-security-rule-trust_untrust]q
[USG6000V1-policy-security]rule name untrust_trust
[USG6000V1-policy-security-rule-untrust_trust]source-zone untrust
[USG6000V1-policy-security-rule-untrust_trust]destination-zone trust
[USG6000V1-policy-security-rule-untrust_trust]destination-address 172.16.1.0 24
[USG6000V1-policy-security-rule-untrust_trust]source-address 192.168.1.0 24
[USG6000V1-policy-security-rule-untrust_trust]action permit
[USG6000V1-policy-security-rule-untrust_trust]q
[USG6000V1-policy-security]rule name local_untrust
[USG6000V1-policy-security-rule-local_untrust]source-zone local
[USG6000V1-policy-security-rule-local_untrust]source-address 200.1.1.254 32
[USG6000V1-policy-security-rule-local_untrust]destination-zone untrust
[USG6000V1-policy-security-rule-local_untrust]destination-address 100.1.1.254 32
[USG6000V1-policy-security-rule-local_untrust]action permit
[USG6000V1-policy-security-rule-local_untrust]q
[USG6000V1-policy-security]rule name untrust_local
[USG6000V1-policy-security-rule-untrust_local]source-zone untrust
[USG6000V1-policy-security-rule-untrust_local]source-address 100.1.1.254 32
[USG6000V1-policy-security-rule-untrust_local]destination-zone local
[USG6000V1-policy-security-rule-untrust_local]destination-address 200.1.1.254 32
[USG6000V1-policy-security-rule-untrust_local]action permit
[USG6000V1-policy-security-rule-untrust_local]q
[USG6000V1-policy-security]q
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name nopat
[USG6000V1-policy-nat-rule-nopat]source-zone trust
[USG6000V1-policy-nat-rule-nopat]source-address 172.16.1.0 24
[USG6000V1-policy-nat-rule-nopat]destination-zone untrust
[USG6000V1-policy-nat-rule-nopat]destination-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-nopat]egress-interface g1/0/1
[USG6000V1-policy-nat-rule-nopat]action no-nat
[USG6000V1-policy-nat-rule-nopat]q
[USG6000V1-policy-nat]rule name nat
[USG6000V1-policy-nat-rule-nat]source-zone trust
[USG6000V1-policy-nat-rule-nat]source-address 172.16.1.0 24
[USG6000V1-policy-nat-rule-nat]destination-zone untrust
[USG6000V1-policy-nat-rule-nat]egress-interface g1/0/1
[USG6000V1-policy-nat-rule-nat]action source-nat easy-ip
[USG6000V1-policy-nat-rule-nat]q
[USG6000V1-policy-nat]q
[USG6000V1]ike proposal 10
[USG6000V1-ike-proposal-10]authentication-method pre-share
[USG6000V1-ike-proposal-10]authentication-algorithm sha2-256
[USG6000V1-ike-proposal-10]encryption-algorithm aes-256
[USG6000V1-ike-proposal-10]dh group14
[USG6000V1-ike-proposal-10]q
[USG6000V1-ike-peer-huawei]ike-proposal 10
[USG6000V1-ike-peer-huawei]pre-shared-key abc-123
[USG6000V1-ike-peer-huawei]remote-address 100.1.1.254
[USG6000V1-ike-peer-huawei]q
[USG6000V1]ipsec proposal huawei-set
[USG6000V1-ipsec-proposal-huawei-set]transform esp
[USG6000V1-ipsec-proposal-huawei-set]encapsulation-mode tunnel
[USG6000V1-ipsec-proposal-huawei-set]esp authentication-algorithm sha2-256
[USG6000V1-ipsec-proposal-huawei-set]esp encryption-algorithm aes-256
[USG6000V1-ipsec-proposal-huawei-set]q
[USG6000V1]acl 3000
[USG6000V1-acl-adv-3000]rule permit ip source 172.16.1.0 0.0.0.255 destination 1
92.168.1.0 0.0.0.255
[USG6000V1-acl-adv-3000]q
[USG6000V1]ipsec policy huawei-map 10 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.[USG6000V1-ipsec-policy-isakmp-huawei-map-10]ike-peer huawei
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]proposal huawei-set
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]security acl 3000
[USG6000V1-ipsec-policy-isakmp-huawei-map-10]q
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ipsec policy huawei-map
[USG6000V1-GigabitEthernet1/0/1]q
验证
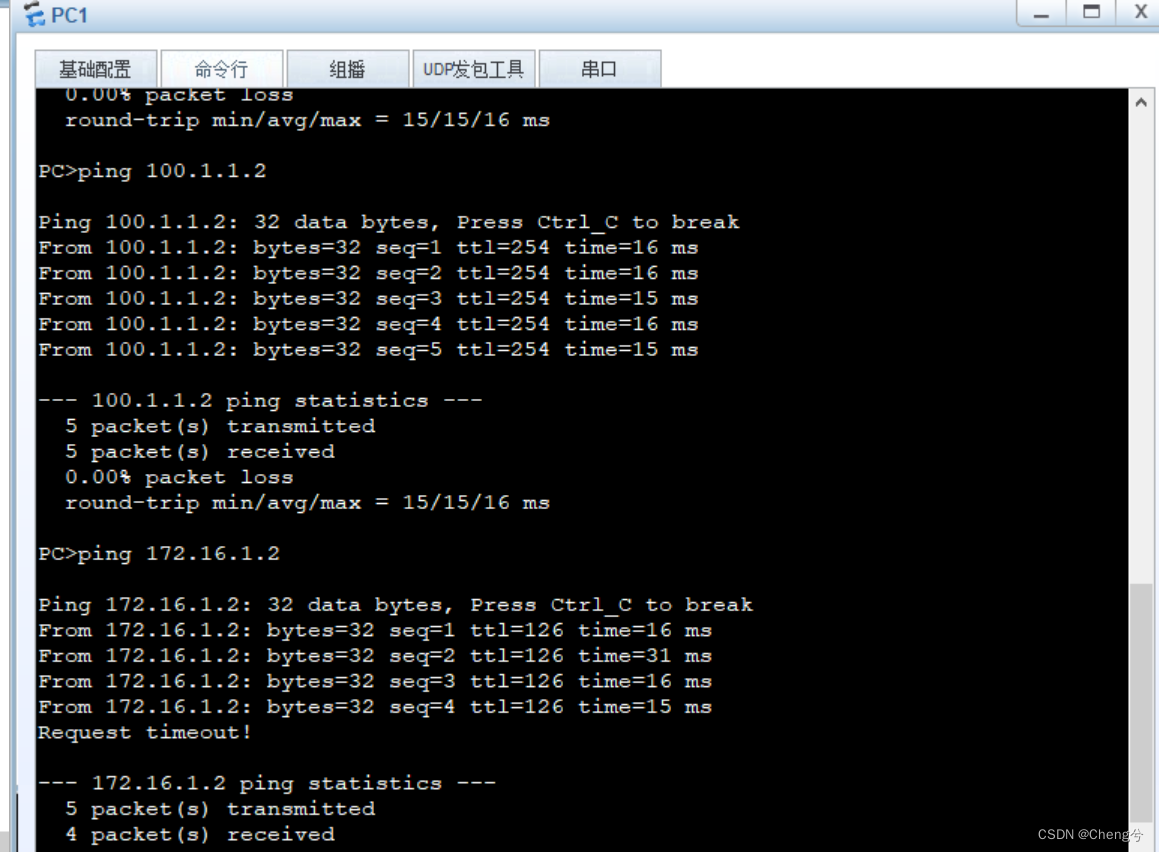
FW2的G1/0/1处转包
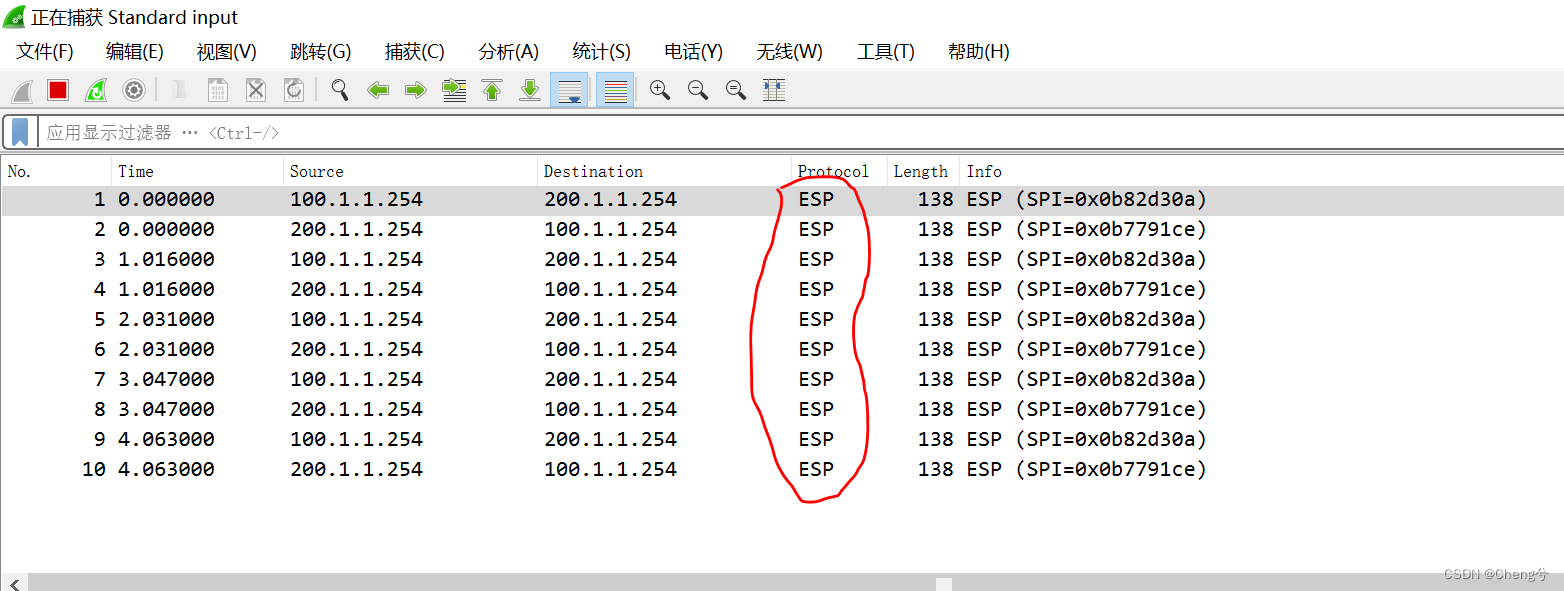
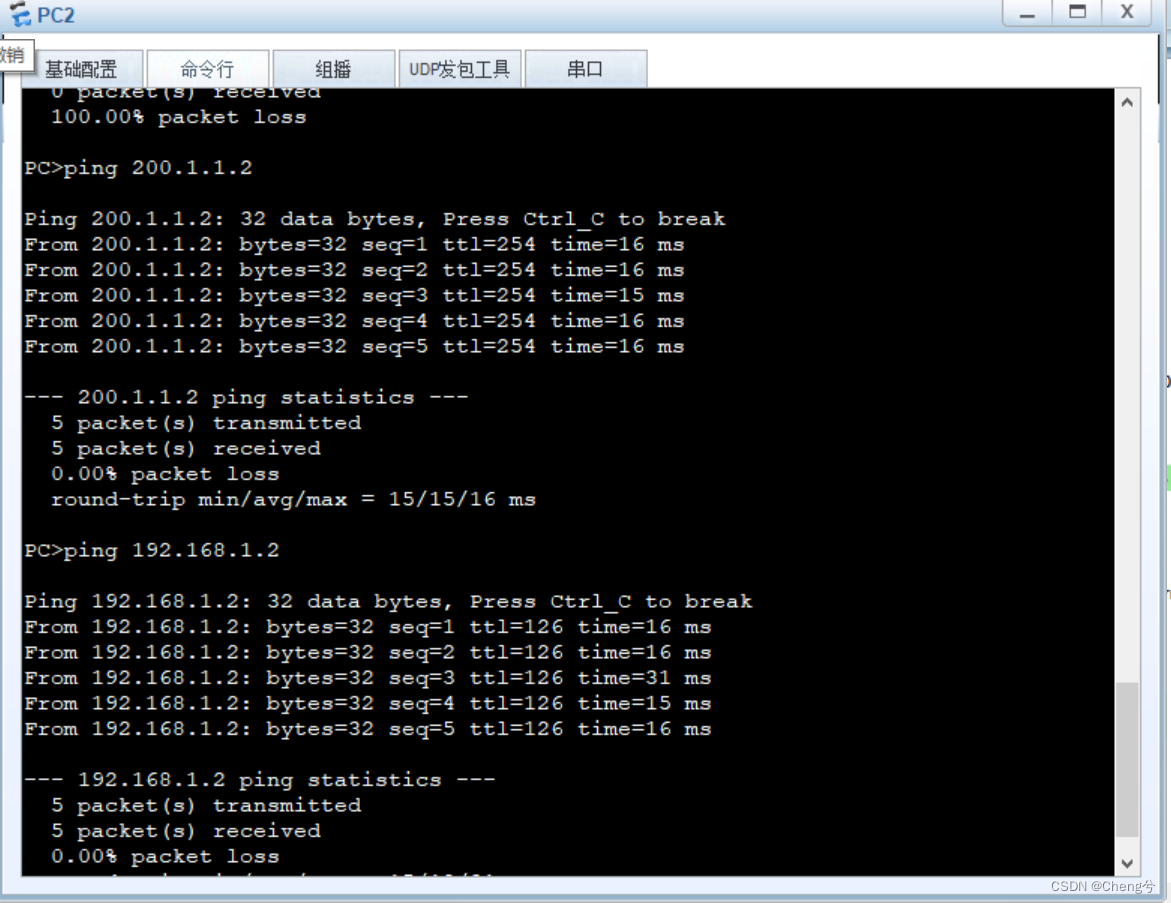
FW2
























 2988
2988











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








