目录
一、部署
官网:https://kubernetes.github.io/ingress-nginx/deploy/#bare-metal-clusters
下载部署文件
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.8.2/deploy/static/provider/baremetal/deploy.yaml
上传镜像到harbor
docker pull dyrnq/ingress-nginx-controller:v1.8.2
docker pull dyrnq/kube-webhook-certgen:v20230407
docker tag dyrnq/kube-webhook-certgen:v20230407 reg.westos.org/ingress-nginx/kube-webhook-certgen:v20230407
docker tag dyrnq/ingress-nginx-controller:v1.8.2 reg.westos.org/ingress-nginx/ingress-nginx-controller:v1.8.2
docker push reg.westos.org/ingress-nginx/ingress-nginx-controller:v1.8.2
docker push reg.westos.org/ingress-nginx/kube-webhook-certgen:v20230407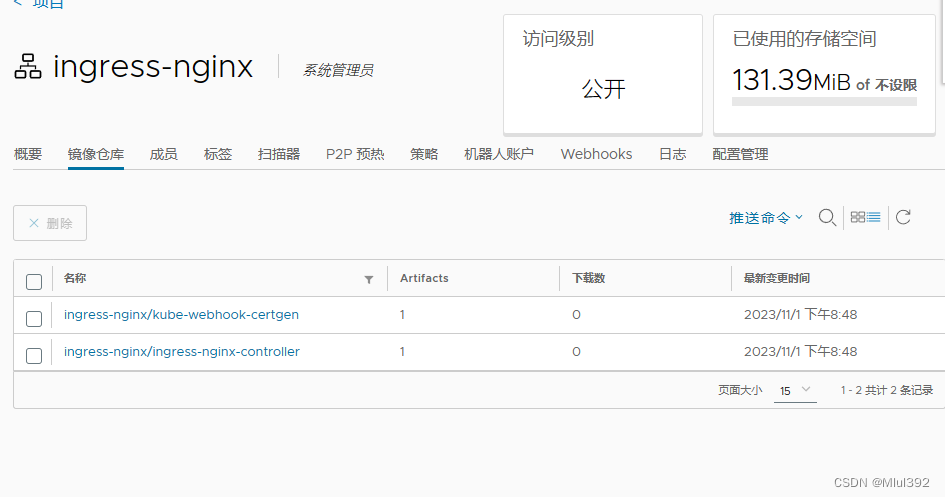
修改3个镜像路径
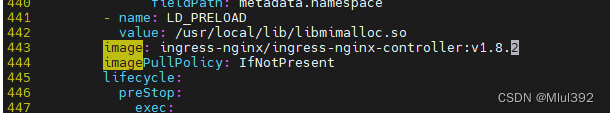
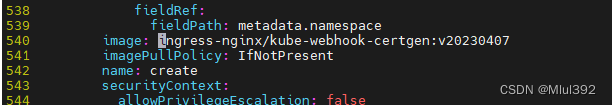
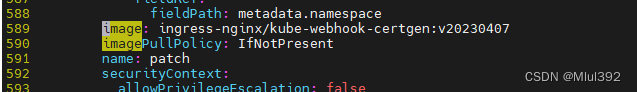
kubectl apply -f deploy.yaml
kubectl -n ingress-nginx get pod
kubectl -n ingress-nginx get svc
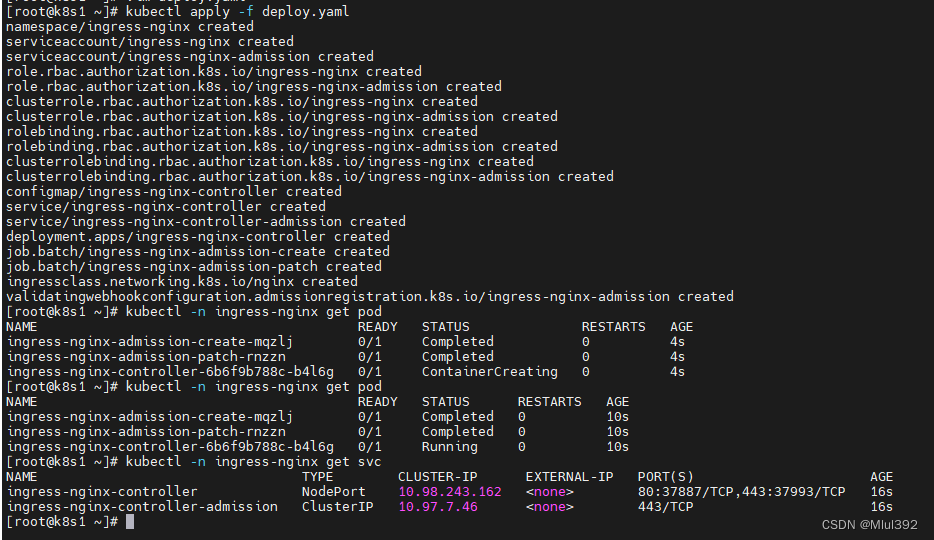
修改为LoadBalancer方式
kubectl -n ingress-nginx edit svc ingress-nginx-controller
kubectl -n ingress-nginx get svc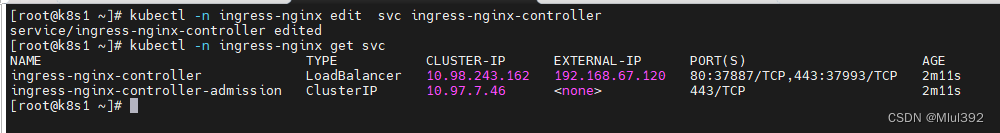
创建ingress策略
vim ingress.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: minimal-ingress
spec:
ingressClassName: nginx
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp
port:
number: 80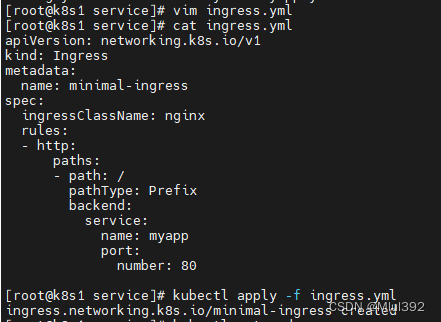
ingress必须和输出的service资源处于同一namespace
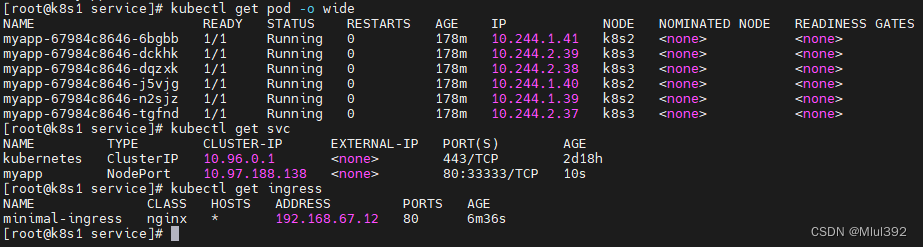
测试:
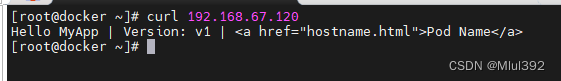
二、访问
1.基于路径访问
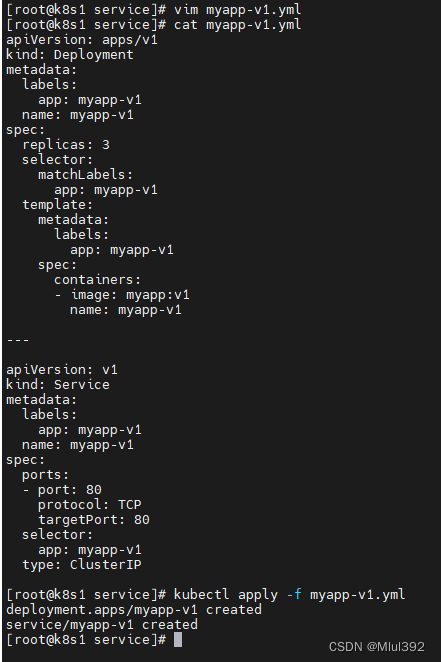
创建svc
vim myapp-v1.yml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: myapp-v1
name: myapp-v1
spec:
replicas: 3
selector:
matchLabels:
app: myapp-v1
template:
metadata:
labels:
app: myapp-v1
spec:
containers:
- image: myapp:v1
name: myapp-v1
---
apiVersion: v1
kind: Service
metadata:
labels:
app: myapp-v1
name: myapp-v1
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
app: myapp-v1
type: ClusterIP
vim myapp-v2.yml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: myapp-v2
name: myapp-v2
spec:
replicas: 3
selector:
matchLabels:
app: myapp-v2
template:
metadata:
labels:
app: myapp-v2
spec:
containers:
- image: myapp:v2
name: myapp-v2
---
apiVersion: v1
kind: Service
metadata:
labels:
app: myapp-v2
name: myapp-v2
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
app: myapp-v2
type: ClusterIP
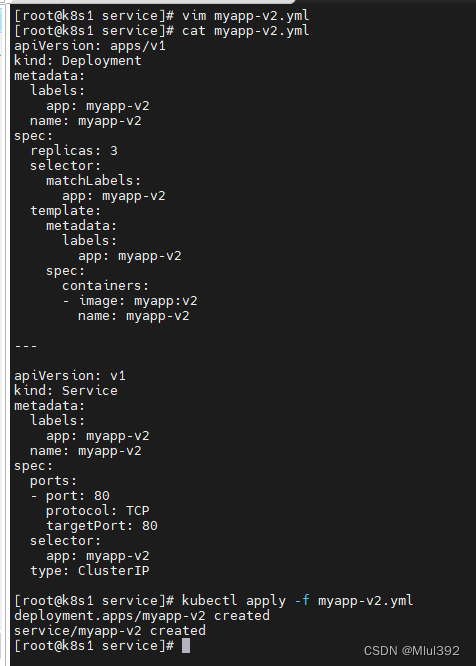
kubectl get svc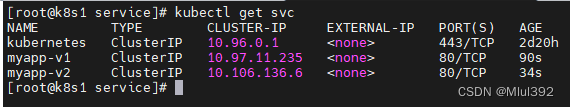
创建ingress
vim ingress1.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: minimal-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /v1
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
- path: /v2
pathType: Prefix
backend:
service:
name: myapp-v2
port:
number: 80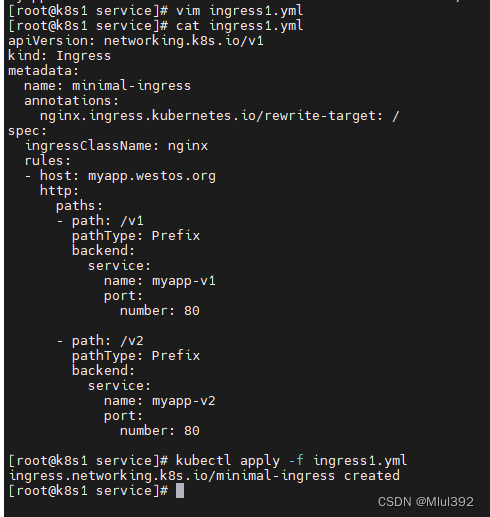
kubectl describe ingress minimal-ingress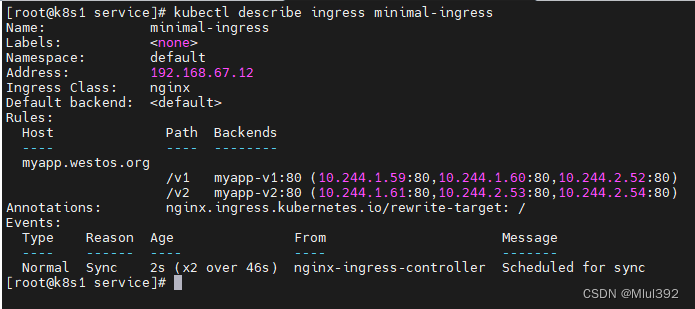
测试
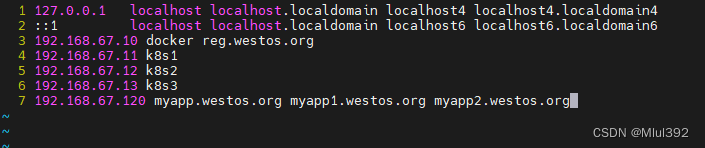
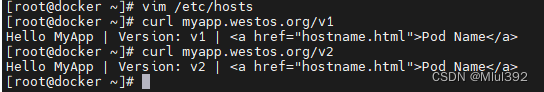
记得回收资源哦
2.基于域名访问
vim ingress2.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: minimal-ingress
spec:
ingressClassName: nginx
rules:
- host: myapp1.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
- host: myapp2.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v2
port:
number: 80
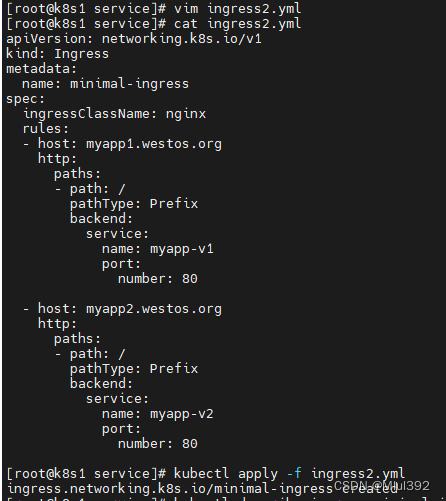
kubectl describe ingress minimal-ingress
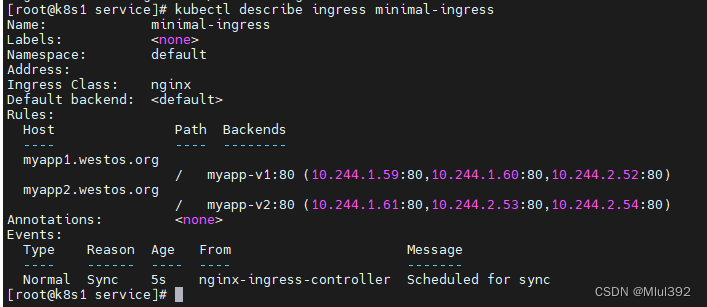
测试:
三、加密与认证
1.TLS加密
创建证书
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc"
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
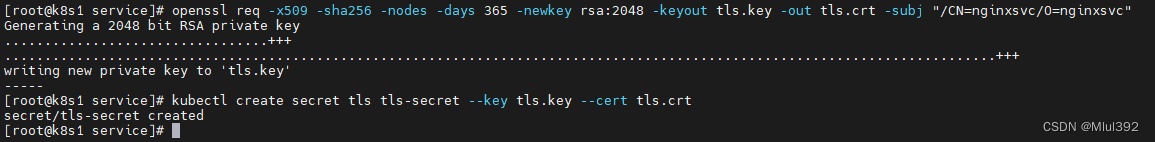
vim ingress3.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-tls
spec:
tls:
- hosts:
- myapp.westos.org
secretName: tls-secret
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
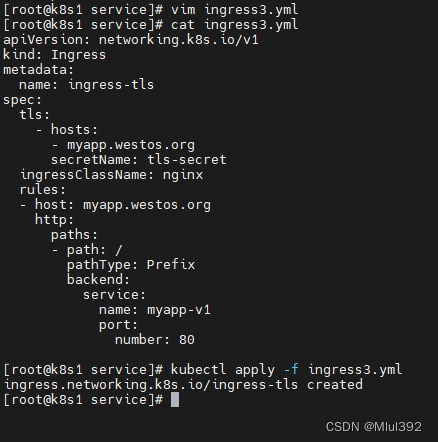
kubectl describe ingress ingress-tls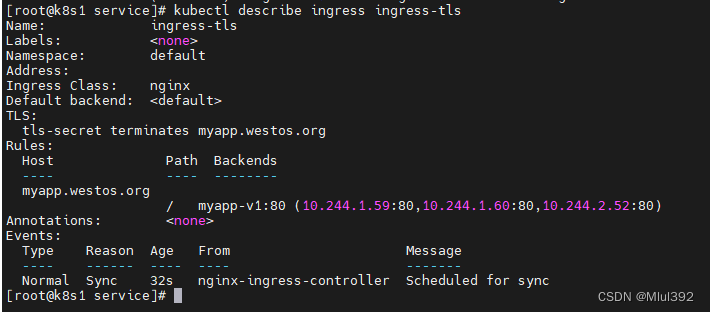
测试:
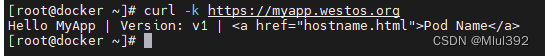
2.auth认证
创建认证文件
yum install -y httpd-tools
htpasswd -c auth yyl
cat auth
kubectl create secret generic basic-auth --from-file=auth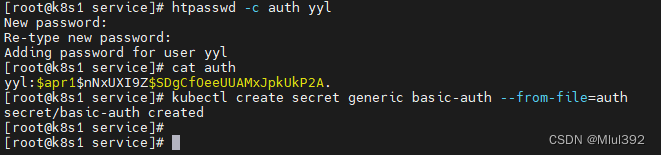
vim ingress3.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-tls
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - yyl'
spec:
tls:
- hosts:
- myapp.westos.org
secretName: tls-secret
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80 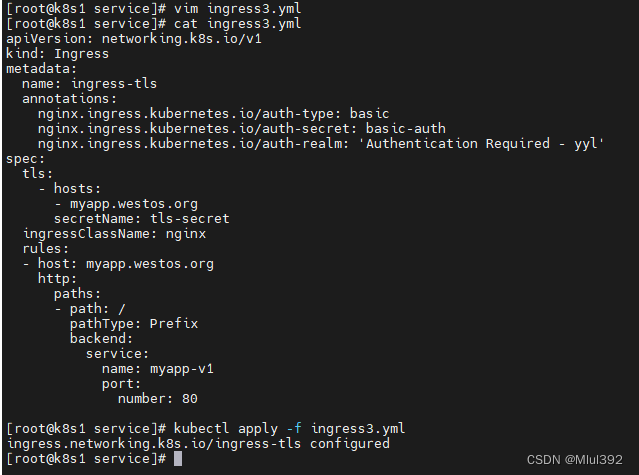
kubectl describe ingress ingress-tls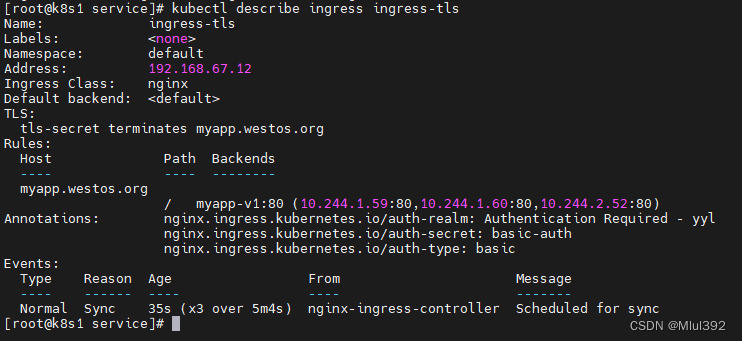
测试:
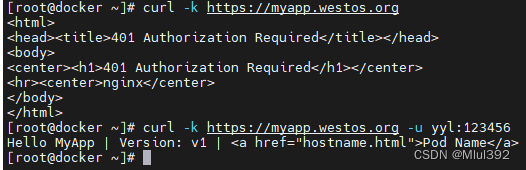
四、rewrite重定向
示例一:
vim ingress3.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-tls
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - yyl'
nginx.ingress.kubernetes.io/app-root: /hostname.html
spec:
tls:
- hosts:
- myapp.westos.org
secretName: tls-secret
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
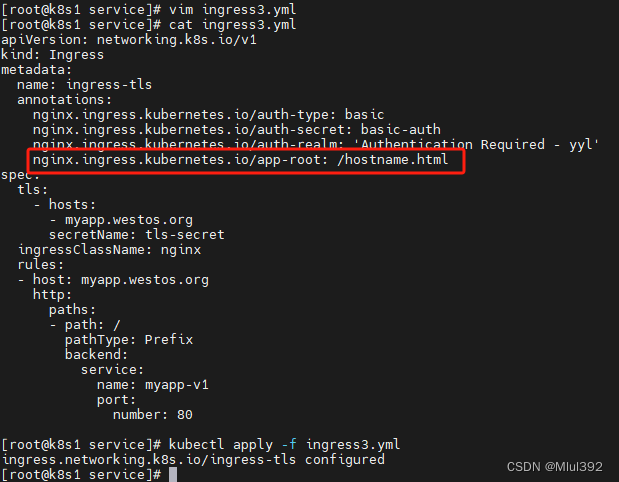
kubectl describe ingress ingress-tls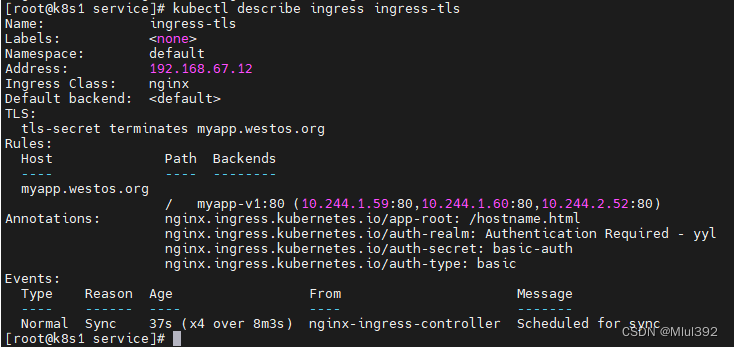
测试:
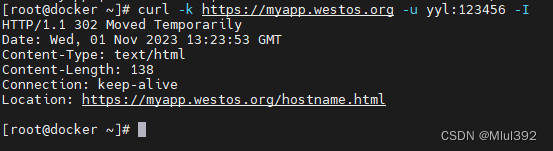
示例二:
vim ingress3.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-tls
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - yyl'
#nginx.ingress.kubernetes.io/app-root: /hostname.html
nginx.ingress.kubernetes.io/use-regex: "true"
nginx.ingress.kubernetes.io/rewrite-target: /$2
spec:
tls:
- hosts:
- myapp.westos.org
secretName: tls-secret
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
- path: /westos(/|$)(.*)
pathType: ImplementationSpecific
backend:
service:
name: myapp-v1
port:
number: 80
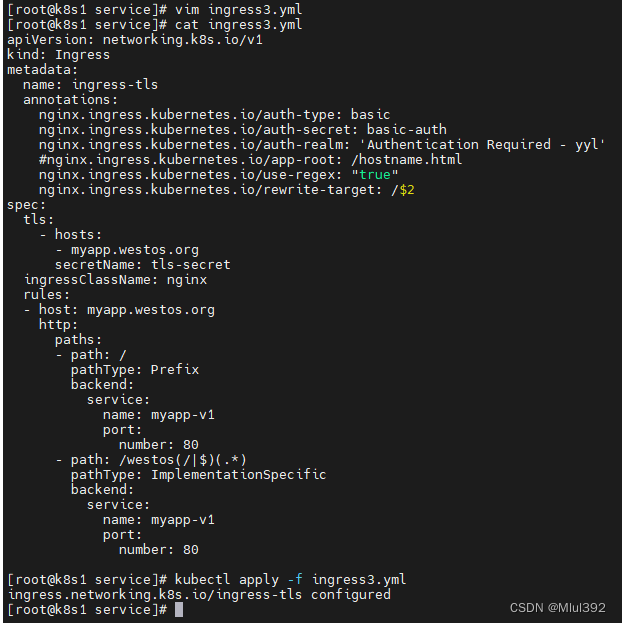
kubectl describe ingress ingress-tls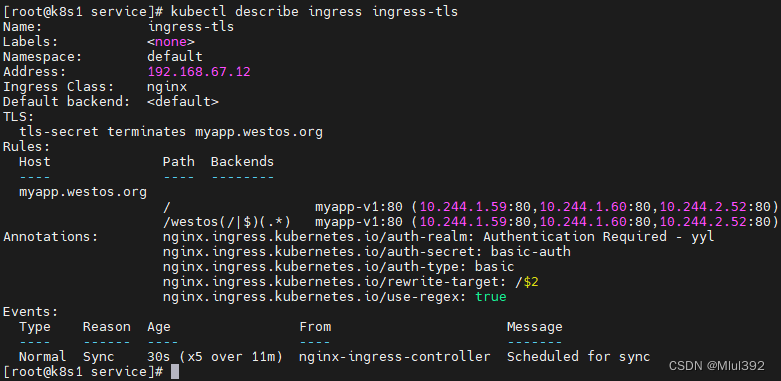
测试:
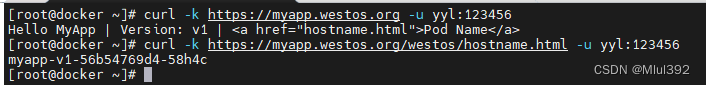
记得回收资源哦
五、canary金丝雀发布
1.基于header灰度
Canary发布是一种渐进式发布技术,可以将新版本的应用程序逐步推送给一小部分用户,以便在生产环境中测试其稳定性和性能。基于header的灰度是其中一种实现方式,即通过在HTTP请求的头部添加特定标记,然后在应用程序中处理该标记,以区分是否将请求路由到新版本或旧版本的应用程序中。通过这种方式,可以以逐渐增加的百分比向用户推送新版本,并在推送完成后逐步停止旧版本的支持。这种方法允许应用程序在不影响所有用户的情况下进行测试和升级,并且可以帮助识别和解决潜在问题。
vim ingress4.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: myapp-v1-ingress
spec:
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: myapp-v1
port:
number: 80
kubectl apply -f ingress4.yml
kubectl get ingress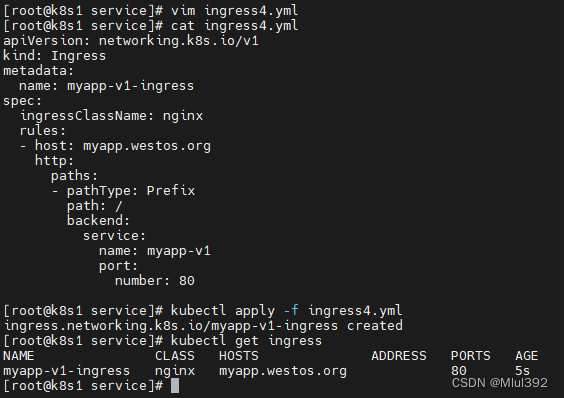
vim ingress5.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/canary: "true"
nginx.ingress.kubernetes.io/canary-by-header: stage
nginx.ingress.kubernetes.io/canary-by-header-value: gray
name: myapp-v2-ingress
spec:
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: myapp-v2
port:
number: 80
kubectl apply -f ingress5.yml
kubectl describe ingress myapp-v2-ingress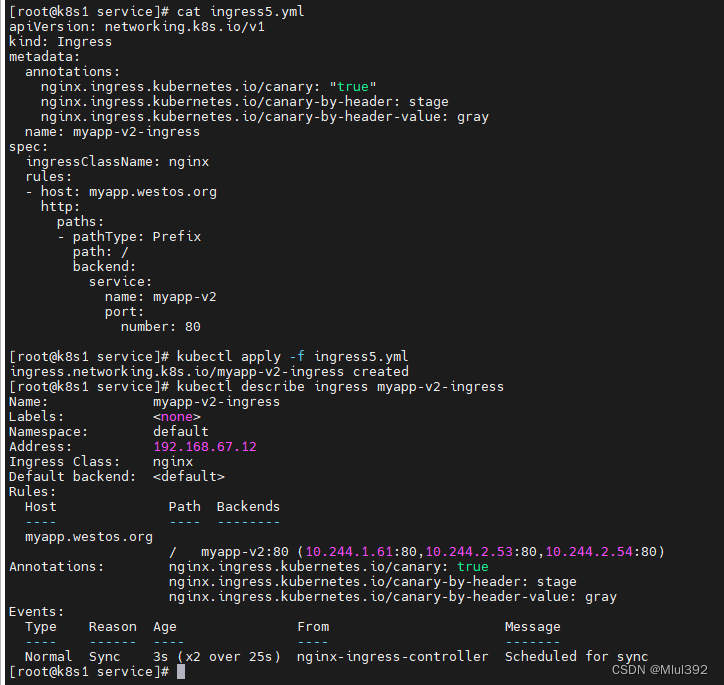
测试:
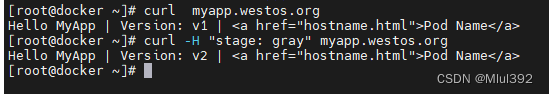
2.基于权重灰度
Canary发布是一种逐步部署新代码版本的方法,其中新代码版本仅在一小部分用户中运行,以测试其稳定性和性能。基于权重的灰度发布是Canary发布的一种变体,其中不同用户组被分配不同的权重,以控制他们接收新代码版本的比例。例如,较新和更有经验的用户可以分配较高的权重,以测试新功能和修复问题,而较少用到的或新购买的用户可以分配较低的权重,以减少潜在的影响。灰度发布的目的是最大限度地减少对生产环境的影响,同时仍然有助于确认发布的正确性。
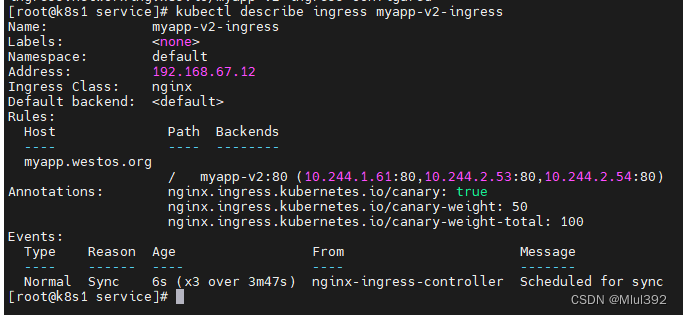
vim ingress5.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/canary: "true"
#nginx.ingress.kubernetes.io/canary-by-header: stage
#nginx.ingress.kubernetes.io/canary-by-header-value: gray
nginx.ingress.kubernetes.io/canary-weight: "50"
nginx.ingress.kubernetes.io/canary-weight-total: "100"
name: myapp-v2-ingress
spec:
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: myapp-v2
port:
number: 80
kubectl apply -f ingress5.yml
kubectl describe ingress myapp-v2-ingress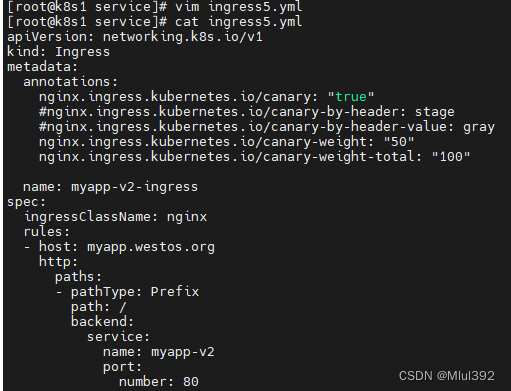
测试:
vim ingress.sh
#!/bin/bash
v1=0
v2=0
for (( i=0; i<100; i++))
do
response=`curl -s myapp.westos.org |grep -c v1`
v1=`expr $v1 + $response`
v2=`expr $v2 + 1 - $response`
done
echo "v1:$v1, v2:$v2"
sh ingress.sh

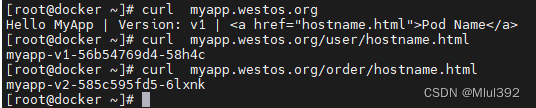
3.业务域拆分
vim ingress6.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /$1
name: rewrite-ingress
spec:
ingressClassName: nginx
rules:
- host: myapp.westos.org
http:
paths:
- path: /user/(.*)
pathType: Prefix
backend:
service:
name: myapp-v1
port:
number: 80
- path: /order/(.*)
pathType: Prefix
backend:
service:
name: myapp-v2
port:
number: 80
kubectl apply -f ingress6.yml
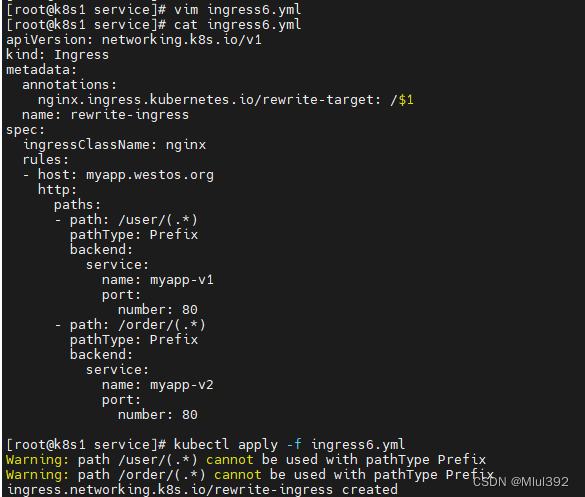
kubectl describe ingress rewrite-ingress
测试:
回收资源哦





















 425
425











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








