公司最近Android 12 GMS认证所有问题已经解决完了,感觉是时候写一篇博客记录下一些技术方案.
1,什么是GMS认证
这些在网上已经有太多的介绍,截取其中关键部分.
Google GMS 认证( Google Mobile Services Test Certification )是谷歌公司为
了确保全世界的硬件厂商设计和生产的安卓为基础的各种智能硬件产品的兼容性、稳定性,
以及这些硬件与安卓各种自带的各种软件 APP 产品和服务的兼容性、稳定性方面的测试和
认证,包括各种安卓 (ANDROID) 智能手机、安卓智能平板、安卓手表、安卓智能汽车、谷歌眼镜、谷歌人工智能、谷歌 VR ,以及如何确保这些硬件产品与谷歌的 APP 软件通过 GMS 认证的产品,将获得谷歌的服务授权,同时产品的型号将列出在谷歌相关的网站中。
说白了,就是要求你在的架构要求内办事,即使是开源的,如果想卖到国外去,就必须这么做,当然啦,你自己做的系统,不能只兼容你的应用,服务,市场上还有广大的应用呢,所以这种认证,即使是不卖到国外,也有必须测试下.
2.认证流程

网上找的一个流程图,是不是一目了然,估计英语不好的人会有一些懵逼,再总结下哈
芯片厂商发布初始版本-->
ODM厂商根据需求定制开发-->
跑所有的GMS报告(CTS/GTS等)-->
送3PL 测试拿到认证-->
量产
//重点来了哈,下面是认证failed 是如何解决思路
3,GMS 测试那些东西
,简单说下哈,经典图片来了

简单来说Hal 以上由CTS 测试API,和apk 是否符合兼容规则
Hal 以下由VTS 测试 不同硬件的兼容
1,CTS
当电子产品开发出来。并定制了自己的Android系统后,必需要通过最新的CTS检測。。从而基于 Android 的应用程序能在基于同一个 api 版本的设备上面运行,即上图Application和Framework的兼容.
源码路径在源码根目录 cts/ 下面
调试方式:CTS 源码加上自己的log,找到对应的Module name,例如CtsAppSecurityHostTestCases ,mm CtsAppSecurityHostTestCases ,生成apk或者jar,替换测试工具的文件,重新跑测试即可抓到想要的log
| arm64-v8a CtsAppSecurityHostTestCases | ||
| Test | Result | Details |
| android.appsecurity.cts.ApexSignatureVerificationTest#testApexPubKeyIsNotWellKnownKey | fail | MultipleFailureException, There were 2 errors: |
解法:需要生成ODM 厂商自己的签名文件,上传即可,签名方式
# create an rsa key pair
openssl genrsa -out foo.pem 4096
# extract the public key from the key pair
avbtool extract_public_key --key foo.pem --output foo.avbpubkey
foo 替换成需要签名的apex 文件名,需要签名的apex log 里面会有
| armeabi-v7a CtsBiometricsTestCases | ||
| Test | Result | Details |
| android.server.biometrics.BiometricSimpleTests#testWhenCredentialNotEnrolled | fail | Argument(s) are different! Wanted: |
解法:GMS 认证版本不支持气压计,移除相关feature 即可
| arm64-v8a CtsContentCaptureServiceTestCases | ||
| Test | Result | Details |
| android.contentcaptureservice.cts.ResizingEditActivityTest#testInsetsChangedOnImeAction | fail | java.lang.IllegalStateException: There Can Be Only One! |
解法:系统只允许有一个发短信的应用,GMS 版本包含了GMS包的和Android 原生的,只需要在编译GMS 包Messages mk 文件加 LOCAL_OVERRIDES_PACKAGES := messaging Mms 覆盖原生的即可
| armeabi-v7a CtsKeystoreTestCases |
| arm64-v8a CtsDevicePolicyManagerTestCases |
| arm64-v8a CtsKeystoreTestCases | ||
| Test | Result | Details |
| android.keystore.cts.KeyAttestationTest#testAttestationKmVersionMatchesFeatureVersion | fail | java.lang.AssertionError: Values should be different. Actual: 0 |
解法:android s 要求Android 12 以上,keymaster 版本要求4.1 以上,
高通:修改 keymaster_vendor_proprietary_product.mk
#ifeq ($(call is-platform-sdk-version-at-least,31),true)
PRODUCT_COPY_FILES += vendor/qcom/proprietary/securemsm/keymaster_utils/android.hardware.hardware_keystore.xml:$(TARGET_COPY_OUT_VENDOR)/etc/permissions/android.hardware.hardware_keystore.xml
#endif
MTK:
修改ProjectConfig.mk KEYMASTER_VERSION = 4.1
keymaster 相关,一般只要只要按照imei imed sn号,然后写入keymaster ,就可以正常pass,对于该模块比较多,会有单独文章介绍
| arm64-v8a CtsNfcTestCases | ||
| Test | Result | Details |
| android.nfc.cts.NfcPreferredPaymentTest#testGetSelectionModeForCategoryPayment | fail | java.lang.AssertionError: Unexpected Exception java.lang.SecurityException: Settings key: <nfc_payment_default_component> is not readable. From S+, settings keys annotated with @hide are restricted to system_server and system apps only, unless they are annotated with @Readable. |
解法:Setting 属性不可读,加上可读注解即可
+ @Readable
@UnsupportedAppUsage(maxTargetSdk = Build.VERSION_CODES.R, trackingBug = 170729553)
public static final String NFC_PAYMENT_DEFAULT_COMPONENT = "nfc_payment_default_component";
| arm64-v8a CtsPermissionTestCases | ||
| Test | Result | Details |
| android.permission.cts.ProviderPermissionTest#testManageDocuments | fail | junit.framework.AssertionFailedError: Exactly one package (must be com.google.android.documentsui) can request the MANAGE_DOCUMENTS permission; found package com.android.contacts which must be revoked for security reasons |
解法:和上面的CtsContentCaptureServiceTestCases 解法一致,GMS编译的时候,覆盖原生Contact
| arm64-v8a CtsViewTestCases | ||
| Test | Result | Details |
| android.view.cts.KeyEventTest#testKeyCodeFromString | fail | java.lang.AssertionError: expected:<0> but was:<289> |
解法:android 不允许odm 厂商加key和修改key code,最大只能288,所以只能规避
frameworks/base / core/java/android/view/KeyEvent.java
private static boolean keyCodeIsValid(int keyCode) {
Exception e = new Exception();
StackTraceElement[] trace = e.getStackTrace();
String classname = trace[2].getClassName();
if(("android.view.cts.KeyEventTest").equals(classname)) {
return keyCode >= KEYCODE_UNKNOWN && keyCode <= KEYCODE_PROFILE_SWITCH;
} else {
return keyCode >= KEYCODE_UNKNOWN && keyCode <= LAST_KEYCODE;
}
}| arm64-v8a CtsWindowManagerDeviceTestCases | ||
| Test | Result | Details |
| android.server.wm.AppConfigurationTests#testSplitscreenLandscapeAppOrientationRequests | fail | java.lang.AssertionError: Split-screen apps shouldn't influence device orientation expected:<1> but was:<0> |
解法:申请google patch 后,pass
diff --git a/services/core/java/com/android/server/wm/TaskDisplayArea.java b/services/core/java/com/android/server/wm/TaskDisplayArea.java
index 89db2ff..8f2bb88 100755
--- a/services/core/java/com/android/server/wm/TaskDisplayArea.java
+++ b/services/core/java/com/android/server/wm/TaskDisplayArea.java
@@ -802,10 +802,12 @@
}
return SCREEN_ORIENTATION_UNSPECIFIED;
} else {
- // Apps and their containers are not allowed to specify an orientation of full screen
- // tasks created by organizer. The organizer handles the orientation instead.
- final Task task = getTopRootTaskInWindowingMode(WINDOWING_MODE_FULLSCREEN);
- if (task != null && task.isVisible() && task.mCreatedByOrganizer) {
+ // Apps and their containers are not allowed to specify an orientation of non floating
+ // visible tasks created by organizer. The organizer handles the orientation instead.
+ final Task nonFloatingTopTask =
+ getRootTask(t -> !t.getWindowConfiguration().tasksAreFloating());
+ if (nonFloatingTopTask != null && nonFloatingTopTask.mCreatedByOrganizer
+ && nonFloatingTopTask.isVisible()) {
return SCREEN_ORIENTATION_UNSPECIFIED;
}
}GtsPermissionTestCases
com.google.android.permission.gts.DefaultPermissionGrantPolicyTest#testDefaultGrantsWithRemoteExceptions
com.google.android.permission.gts.DefaultPermissionGrantPolicyTest#testPreGrantsWithRemoteExceptions
解法:未知原因,直接规避
/frameworks/base / core/java/android/app/ApplicationPackageManager.java
@Override
public boolean hasSystemFeature(String name) {
//
if("cn.google.services".equals(name)){
Exception e = new Exception();
boolean isSpecialGtsTest = false;
if(e != null){
StackTraceElement[] trace = e.getStackTrace();
if(trace != null ){
for (int i = 0; i < trace.length; i++) {
StackTraceElement stackTraceElement=trace[i];
if(stackTraceElement != null){
String className=stackTraceElement.getClassName();
String methodName=stackTraceElement.getMethodName();
if(className != null && methodName != null){
if(className.contains("DefaultPermissionGrantPolicyTest")
&&methodName.contains("addDefaultSystemHandlerPermissions")){
isSpecialGtsTest = true;
}
}
}
}
}
}
if(isSpecialGtsTest){
Log.d(TAG,"hasSystemFeature "+name +" isSpecialGtsTest "+isSpecialGtsTest);
}
if(isSpecialGtsTest) return true;
}
//
return hasSystemFeature(name, 0);
}
2,GTS
Google 全家桶的应用,也要兼容系统,也是醉了,人家屋檐下,不得不低头,没办法
特别说明,这个没有源码,只能看log 盲解,不过网上找到反编译apk 的软件还是挺好用的,可以参考下哈
https://www.jianshu.com/p/dbe579f6cc84
| arm64-v8a GtsIntelligenceTestCases | ||
| Test | Result | Details |
| com.google.android.gts.intelligence.IntelligenceRolesTest#testIntelligenceRolesAllowed | fail | java.lang.RuntimeException: expected to be empty |
解法:删除ASI,Google 在Android T 上有要求,android s 不做要求,删除gms.mk 中下面内容即可,如果有EEA 版本,那么eea_common.mk 也需要删除相关的
#PRODUCT_PACKAGES += GmsConfigOverlayASI
| arm64-v8a GtsFeaturesTestCases | ||
| Test | Result | Details |
| com.google.android.features.gts.GoogleFeaturesTest#testFeatureAiai | fail | expected to be true |
解法:和上面问题是一样的,Android S 没有Aiai feature 要求,删除即可
etc/sysconfig/google.xml 中删除 <feature name="com.google.android.feature.ASI" />
gms.mk 和 eea_common.mk 删除 AndroidSystemIntelligence_Features
| arm64-v8a GtsJniUncompressHostTestCases | ||
| Test | Result | Details |
| com.google.android.gts.jniuncompress.GtsJniUncompressHostTest#testJniLibsUncompressed | fail | java.lang.RuntimeException: [GMS-13.3.5-001] For PRODUCTs that launch with or upgrade to Android11 or higher, if a preloaded APK file targets API level 30 or higher, it MUST be signed and verifiable with the APK Signature scheme v2 or higher. Any native libraries embedded in it MUST be uncompressed and page aligned before signing. |
解法:Android 12 target sdk 31以上最新要求,如果apk存在.so/.dex压缩,则必须使用:LOCAL_REPLACE_PREBUILT_APK_INSTALLED 编译apk,不要使用copy命令!
| arm64-v8a GtsPlacementTestCases | ||
| Test | Result | Details |
| com.google.android.placement.gts.HomescreenPlacementTest#testAppPlacement | fail | java.lang.RuntimeException: Test failed for cases: [2] |
解法:GMS 版本要求,Google chrome 和 Play store ,google chrome widget 必须位于首页桌面或者底部快捷方式,修改方式Launch app位置修改_xss534890437的博客-CSDN博客
| arm64-v8a GtsWellbeingTestCases | ||
| Test | Result | Details |
| com.google.android.wellbeing.gts.WellbeingTest#testQuickSettingsAutoAddContainWindDownTile | fail | List of Quick Settings tiles that can be added automatically doesn't contain Bedtime Mode tile. |
| com.google.android.wellbeing.gts.WellbeingTest#testQuickSettingsAutoAddContainFocusModeTile | fail | List of Quick Settings tiles that can be added automatically doesn't contain Focus Mode tile. |
解法:quick setting 加下面内容,至于为啥要加,我也不知道,Google 要求的,咱就加
<string-array name="config_quickSettingsAutoAdd" translatable="false">
<item>accessibility_display_inversion_enabled:inversion</item>
<item>focus_mode_first_time_setup:custom(com.google.android.apps.wellbeing/com.google.android.apps.wellbeing.focusmode.quicksettings.FocusModeTileService)</item>
<item>wind_down_first_time_setup:custom(com.google.android.apps.wellbeing/com.google.android.apps.wellbeing.screen.ui.GrayscaleTileService)</item>
</string-array>
| arm64-v8a GtsRegulationComplianceTestCases | ||
| Test | Result | Details |
| com.google.android.regulationcompliance.gts.EEAComplianceTest#testEEAv2Compliance | fail | java.lang.RuntimeException: This build does not meet all of the EEA requirements for EEA devices. |
解法:使用EEA 账号登录后一般可以pass,不过他也有测试要求
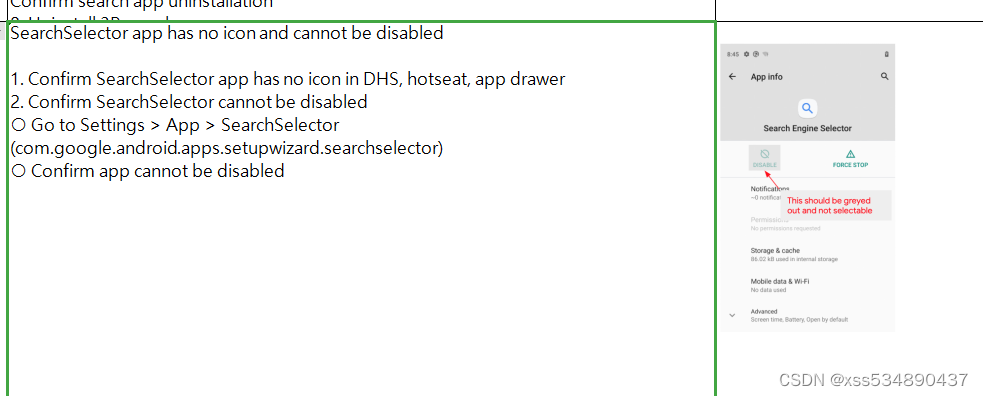
1,search engine selector 不能有图标
2,在设置里面不能被禁用
我遇到情况,是可以被禁用,导致测试失败
修改方法:Settings / src/com/android/settings/applications/ApplicationFeatureProviderImpl.java
@Override
public Set<String> getKeepEnabledPackages() {
...........
+ keepEnabledPackages.add("com.google.android.apps.setupwizard.searchselector");
return keepEnabledPackages;
}google 文件夹中的Google TV 消失
apps/GmsSampleIntegration/res_dhs_full/xml/partner_default_layout.xml
修改: <favorite packageName="com.google.android.videos" className="com.google.android.youtube.videos.EntryPoint"/>
改为
<favorite packageName="com.google.android.videos" className="com.google.android.videos.GoogleTvEntryPoint"/>
GtsPermissionTestCases com.google.android.permission.gts.ActivityRecognitionPermissionTest#activityRecognitionPermissionNotGrantedForPostPUpgrade
解法:google patch
https://android.googlesource.com/platform/frameworks/base/+/0873a30210d6425ffb28021000ef3fe40a8da711
3,STS
Android Security Test Suite (STS). 是谷歌关于android安全补丁安装情况的一个测试套件.STS和security patch相关的,是CTS测试新增加一项安全测试套件。STS是201808才开始测试的。由vendor 负责定时更新三个月以内的Security patch.STS会测试这些patch 是否merge,同时测试对系统的兼容.
STS 一般出问题 ,都是因为补丁少合入了,举一个栗子
| arm64-v8a CtsSecurityBulletinHostTestCases | |||
| Test | Result | Details | |
| android.security.cts.CVE_2021_39702#testPocCVE_2021_39702 | fail | java.lang.AssertionError: on-device tests failed: | pass |
我们在https://source.android.com/ 搜索 CVE-2021-39702 注意下划线变成中线

随便点一个进去,ctrl+F 再次搜索关键字39702 找到对应的patch 点进去,就是patch

只需要查看是否merge 即可,如果没有merge ,那就merge 在测试,如果已经merge 了,那就需要log 分析原因了,具体问题具体分析.
ps:对于MTK 项目需要注意的是overlay(MTK 就喜欢单独搞一套,无语) ,MTK Setting Launcher SystemUI 等都覆盖原生的了,如果有这类相关patch ,还是fail ,就需要看看vendor 下面这些app 是否已经合并相关patch 了
补充下新版本 sts 的测试命令
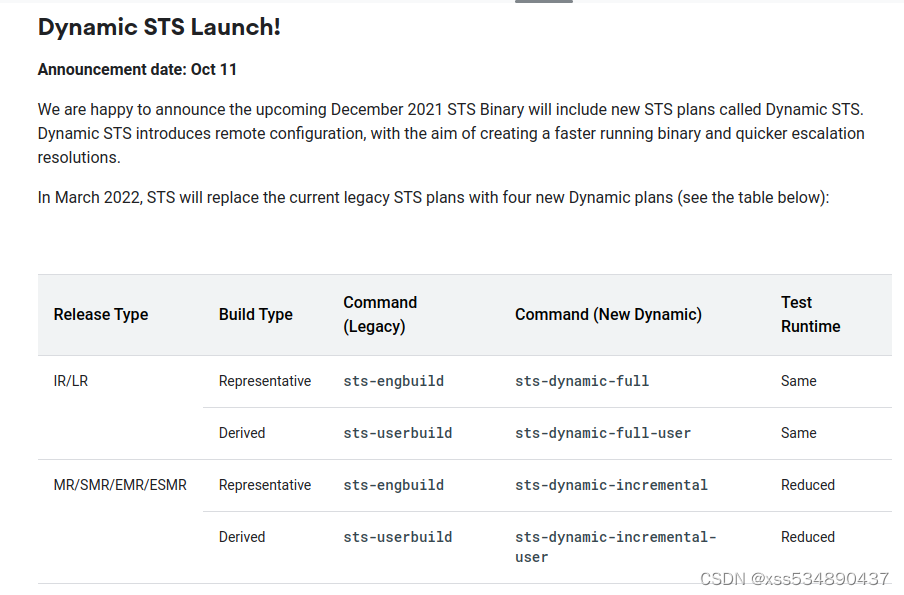
IR/LR 可以理解为第一个版本认证阶段,获取Google 认证的测试命令
MR..... 认证过后后续 迭代升级的测试命令
| arm64-v8a StsHostTestCases | ||
| Test | Result | Details |
|---|---|---|
| android.security.sts.KernelLtsTest#testRequiredKernelLts_WARN | fail | java.lang.AssertionError: This device does not meet the current or upcoming LTS update requirements. This test is a warning that is autowaived in APA and no waiver request is necessary. Optionally, to override the warning, add this argument: --test-arg com.android.compatibility.common.tradefed.testtype.JarHostTest:set-option:android.security.sts.KernelLtsTest:acknowledge_kernel_update_requirement_warning_failure:true |
解法:根据log
com.android.compatibility.common.tradefed.testtype.JarHostTest:set-option:android.security.sts.KernelLtsTest:acknowledge_kernel_update_requirement_warning_failure:true
Caused by: java.lang.AssertionError: WARNING, this kernel (5.4.210) must be (5.4.233+) by the upcoming kernel LTS update requirement for SPL (2023-11-05). https://support.google.com/androidpartners_security/answer/11616490
Expected: a value equal to or greater than <5.4.233>
but: <5.4.210> was less than <5.4.233>
修改kernel 版本为5.4.233 即可(kernel/msm-5.4)
diff --git a/Makefile b/Makefile
index 3efd51fc..6091652 100644
--- a/Makefile
+++ b/Makefile
@@ -1,7 +1,7 @@
# SPDX-License-Identifier: GPL-2.0
VERSION = 5
PATCHLEVEL = 4
-SUBLEVEL = 210
+SUBLEVEL = 233
EXTRAVERSION =
4,VTS
VTS 全称Android Vendor Test Suite (VTS). VTS 类似 CTS,通过对 Vendor Interface 进行测试,确保同一个版本的 Android Framework 可以运行在不同 HAL(HardWare Abstraction Layer) 上,或不同 Android Framework 可以运行在 同一个 HAL 上。
通过这样的 Framework / HAL 分离设计和接口一致性保证,也使得 8.0 版本之后的 Android 系统在进行升级时,可以直接对 Framework 进行升级而不用考虑 HAL 层的改动,从而缩短了用户手上设备得到系统升级 OTA 推送的时间。
废话补多少,我们看下VTS问题如何解决,其实VTS 和CTS 的原理都是一样,编译module ,可以单测
源码路径:
源码更目录下 test/vts 和 test/vts-testcase
典型的错误
| arm64-v8a vts_treble_vintf_vendor_test | ||
| Test | Result | Details |
| DeviceManifest/SingleManifestTest#HalsAreServed/0 | fail | Getting: android.hardware.audio@7.0::IDevicesFactory/default |
| DeviceManifest/SingleManifestTest#InterfacesAreReleased/0 | fail | Getting: android.hardware.audio@7.0::IDevicesFactory/default |
解法:相关server 被调用,没有在矩阵张注册,或者注册了没有使用,只需要在manifest 删除即可
| armeabi-v7a vts_libsnapshot_test | ||
| Test | Result | Details |
| ImageManagerTest/ImageManagerTest#CreateImageEnoughAvailSpace/8 | fail | system/core/fs_mgr/libsnapshot/snapshot_test.cpp:2271: Failure |
解法:userdata 分区大小不够,我加了一个G pass userdata,EXT4,4296704,,EMMC_USER,,N,Y,userdata.img,N,N,Y,,Y,,AUTO,8388608,
VtsTrebleVendorVintfTest测试时可能会遭遇以下两种情况报hash的错误:
ModuleListener.testStarted(VtsTrebleVendorVintfTest#DeviceManifest/SingleManifestTest.InterfacesAreReleased/0_32bit)
vendor.sw.swfingerprint@1.0::xxxx has an empty hash. This is because it was compiled without being frozen in a corresponding current.txt file.
解法:我们只需要找到对应的HIDL.使用以下命令,生成hash 值.添加到对应的current.txt 中即可
hidl-gen -L hash -r vendor.nxp.nxpnfclegacy:hardware/nxp/nfc/extns/intf/nxpnfclegacy -r android.hardware:hardware/interfaces -r android.hidl:system/libhidl/transport vendor.nxp.nxpnfclegacy@1.0::INxpNfcLegacy
例子中的加粗部分, 需要替换成自己的.
5.CTS-V
Android 兼容性测试套件验证程序( cts-verifier )是对兼容性测试套件 (CTS) 的补充 。CTS 可以对具备测试自动化功能 API 和功能进行测试,而 CTS 验证程序则可以针对一些必须依赖于手动操作才能在固定设备上进行测试的 API 和功能(例如蓝牙,音频质量、触摸屏、加速度计、相机等)提供测试。
6,checklist 问题
google 额外提出一些测试要求
1,长按Home 键弹出Google assistent
实体按键按照要求修改参数为2即可
<!-- Control the behavior when the user long presses the home button.
0 - Nothing
1 - Launch all apps intent
2 - Launch assist intent
3 - Launch notification panel
This needs to match the constants in
policy/src/com/android/internal/policy/impl/PhoneWindowManager.java
-->
<integer name="config_longPressOnHomeBehavior">2</integer>
虚拟导航栏按键修改 SystemUI 中 NavigationBar.java
@VisibleForTesting
boolean onHomeLongClick(View v) {
mMetricsLogger.action(MetricsEvent.ACTION_ASSIST_LONG_PRESS);
mUiEventLogger.log(NavBarActionEvent.NAVBAR_ASSIST_LONGPRESS);
Bundle args = new Bundle();
args.putInt(
AssistManager.INVOCATION_TYPE_KEY,
AssistManager.INVOCATION_TYPE_HOME_BUTTON_LONG_PRESS);
mAssistManagerLazy.get().startAssist(args);
mStatusBarLazy.get().awakenDreams();
mNavigationBarView.abortCurrentGesture();
return true;
}
2,安装controls.apk 系统quick setting 需要加上device control
当时不知道原因,解决办法是监听apk 安装后,添加quick setting ,然后刷新,满足需求,后面发现安装control.apk 这种可能会有一个广播,不过没有验证是否OK
SystemUI 中 QSTileHost
@Inject
public QSTileHost(Context context,
StatusBarIconController iconController,
QSFactory defaultFactory,
@Main Handler mainHandler,
@Background Looper bgLooper,
PluginManager pluginManager,
TunerService tunerService,
Provider<AutoTileManager> autoTiles,
DumpManager dumpManager,
BroadcastDispatcher broadcastDispatcher,
Optional<StatusBar> statusBarOptional,
QSLogger qsLogger,
UiEventLogger uiEventLogger,
UserTracker userTracker,
SecureSettings secureSettings,
CustomTileStatePersister customTileStatePersister
) {
//监听安装包
IntentFilter packageChangedFilter = new IntentFilter(Intent.ACTION_PACKAGE_ADDED);
packageChangedFilter.addDataScheme("package");
mContext.registerReceiver(new BroadcastReceiver() {
@Override
public void onReceive(Context context, Intent intent) {
String packageName = intent.getData().getSchemeSpecificPart();
if(packageName.equals("controls.mock")){
String qstitles = Settings.Secure.getString(context.getContentResolver(), "sysui_qs_tiles");
if(!qstitles.contains("controls")){
String allTitles = qstitles +",controls";
Settings.Secure.putString(context.getContentResolver(), "sysui_qs_tiles", allTitles);
Log.d(TAG, "QSObserver");
onTuningChanged(TILES_SETTING, allTitles);
}
}
}
}, packageChangedFilter);
}SystemUI 中有这个广播应该和controls 是相关的,在这里加应该也是可以,没有尝试,有兴趣的可以自己试试
<receiver android:name=".controls.management.ControlsRequestReceiver"
android:exported="true">
<intent-filter>
<action android:name="android.service.controls.action.ADD_CONTROL" />
</intent-filter>
</receiver>
如何规避
对于odm 厂商来说,改的东西很多,有些是必须改动,但是又不符合google 的要求,那样的话通过规避的方式,来来通过测试也是一种途径,嘿嘿,如何规避呢?
查看测试源码,我们发现XTS 测试,都是通过assert 断言来判断结果是否符合预期,所以那就好办了,我这边主要使用下面两种规避方式
1,通过callstack 判断如果是特定测试项调用 ,则直接返回预期值,通过测试
Exception e = new Exception();
StackTraceElement[] trace = e.getStackTrace();
String classname = trace[x].getClassName();
for(StackTraceElement e:trace){
if(e.getClassName().equals("xxx.xxx.xxx")){/xxx.xxx.xxx 测试项的包名+类名
//返回预期数据
}
}2,通过测试应用是否安装,若安装则直接返回预期值,通过测试
final PackageManager packageManager = context.getPackageManager();
// 获取所有已安装程序的包信息
List<PackageInfo> info = packageManager.getInstalledPackages(0);
for ( int i = 0; i < info.size(); i++ ) {
if(pkgName.equals(info.get(i).packageName)) {
// 返回预期结果
}
}或者
PackageManager pm = mContext.getPackageManager();
try {
ApplicationInfo info = pm.getApplicationInfo(packageName, 0);
if(info != null){
//返回预期结果
}
} catch (PackageManager.NameNotFoundException e) {
return false;
}两段代码不知道那个效率高一些,有兴趣的可以研究下哈























 450
450

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








