
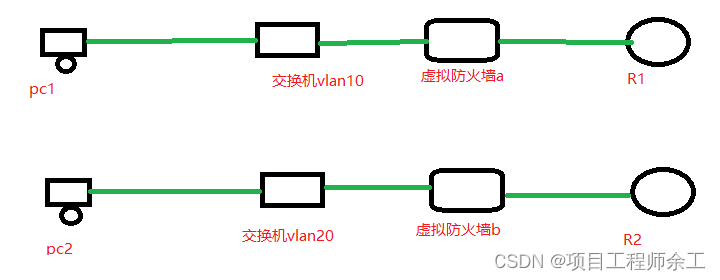
逻辑上简单看成下面这个图
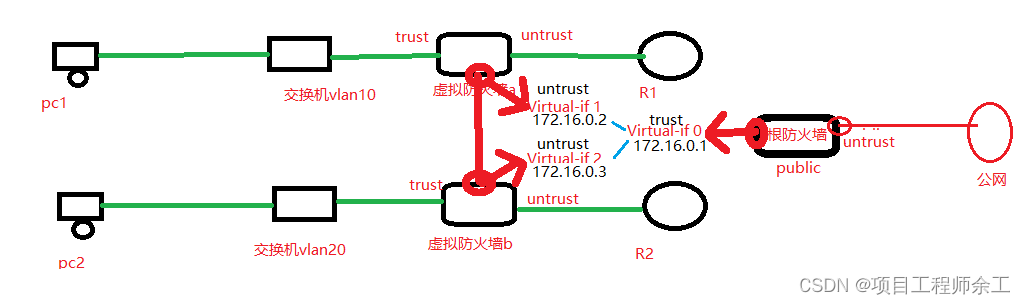
再具分析就可以看成下面逻辑图
fw配置
vsys enable
开虚拟功能
这两个虚拟口必须先创建
interface GigabitEthernet1/0/2.10
interface GigabitEthernet1/0/2.20
vsys name a 1
assign interface GigabitEthernet1/0/2.10
assign interface GigabitEthernet1/0/0
vsys name b 2
assign interface GigabitEthernet1/0/2.20
assign interface GigabitEthernet1/0/1
interface GigabitEthernet1/0/0
undo shutdown
ip binding vpn-instance a
ip address 1.1.1.254 255.255.255.0
interface GigabitEthernet1/0/1
undo shutdown
ip binding vpn-instance b
ip address 2.2.2.254 255.255.255.0
interface GigabitEthernet1/0/2.10
vlan-type dot1q 10
ip binding vpn-instance a
ip address 192.168.1.254 255.255.255.0
interface GigabitEthernet1/0/2.20
vlan-type dot1q 20
ip binding vpn-instance b
ip address 192.168.2.254 255.255.255.0
interface Virtual-if0
ip address 172.16.0.1 255.255.255.0
interface Virtual-if1
ip address 172.16.0.2 255.255.255.0
interface Virtual-if2
ip address 172.16.0.3 255.255.255.0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface Virtual-if0
用ospf协议把防火墙周边的虚拟防火墙各接口网段打通
ospf 1 router-id 1.1.1.254 vpn-instance a
area 0.0.0.0
network 1.1.1.254 0.0.0.0
network 192.168.1.254 0.0.0.0
ospf 2 router-id 2.2.2.254 vpn-instance b
area 0.0.0.0
network 2.2.2.254 0.0.0.0
network 192.168.2.254 0.0.0.0
实例a的网段去网段192.168.2.0并且目的网段在实例b
ip route-static vpn-instance a 192.168.2.0 255.255.255.0 vpn-instance b
ip route-static vpn-instance b 192.168.1.0 255.255.255.0 vpn-instance a
虚拟系统a 配置
switch vsys a 1
interface GigabitEthernet1/0/0
undo shutdown
ip binding vpn-instance a
ip address 1.1.1.254 255.255.255.0
interface GigabitEthernet1/0/2.10
vlan-type dot1q 10
ip binding vpn-instance a
ip address 192.168.1.254 255.255.255.0
interface Virtual-if1
ip address 172.16.0.2 255.255.255.0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/2.10
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Virtual-if1
security-policy
rule name trust-to-untrust
source-zone trust
destination-zone untrust
action permit
rule name untrust-to-trust //对端虚拟系统b访问过来放行
source-zone untrust
destination-zone trust
action permit
虚拟系统b配置
switch vsys b 2
interface GigabitEthernet1/0/1
undo shutdown
ip binding vpn-instance b
ip address 2.2.2.254 255.255.255.0
interface GigabitEthernet1/0/2.20
vlan-type dot1q 20
ip binding vpn-instance b
ip address 192.168.2.254 255.255.255.0
interface Virtual-if2
ip address 172.16.0.3 255.255.255.0
firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/2.20
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Virtual-if2
security-policy
rule name trust-to-untrust
source-zone trust
destination-zone untrust
action permit
rule name untrust-to-trust //对端a虚拟系统访问过来
source-zone untrust
destination-zone trust
action permit
交换机配置
vlan batch 10 20
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10 20
interface GigabitEthernet0/0/2
port link-type access
port default vlan 10
interface GigabitEthernet0/0/3
port link-type access
port default vlan 20
路由器R1配置
interface GigabitEthernet0/0/0
ip address 1.1.1.1 255.255.255.0
ospf 1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
路由器R2配置
interface GigabitEthernet0/0/0
ip address 2.2.2.2 255.255.255.0
ospf 1
area 0.0.0.0
network 2.2.2.2 0.0.0.0
最终实现pc1和pc2可以互通,并且可以各自己对端的路由器通
























 2073
2073











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










