前注:
学习书籍
Identity and Access Management and Security on AWS
1. Authentication (认证)
Managing users and their access
Managing federated users and their access
2. Authorization (授权)
In AWS, authorization is mainly done using IAM policies.
An IAM policy is a piece of code written in JSON where you can define one or more permissions. These permissions define which resources and which actions or operations the IAM entity is allowed.
This policy can be attached to any IAM entity such as a user, group, or role.
You can attach any number of policies to an entity.
A policy can even be attached to multiple entities.
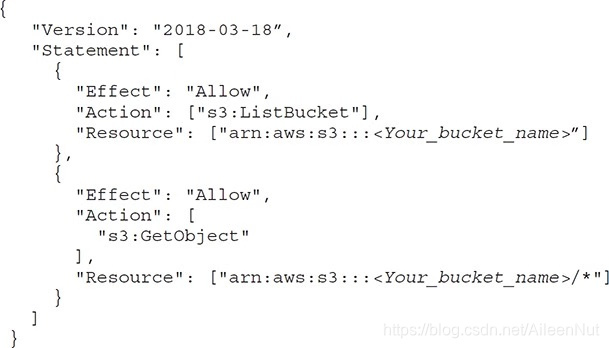 Policy Read-only access to S3
Policy Read-only access to S3
Using a policy, you can either allow or deny access to any resource for any IAM entity, but all permissions are implicitly denied by default.
3. Auditing (审核)
The AWS CloudTrail service records activity made on your account and delivers log files to your Amazon S3 bucket.
CloudTrail can log every API call and related event made.
CloudTrail records important information about each action, including:
· Who made the request?
· When was the request made?
· What was the request about?
· Which resources were acted upon in response to the request?
· Where was the request made from and made to?
4. Types of security credentials (安全凭证的类型)
(1) The security credentials often use:
· IAM username and password
Mainly used for accessing the AWS Management Console.
· E-mail address and password
Associate with your root account.
· Access keys
Often used with the CLI, APIs and SDKs.
· Key pair
Used with Amazon EC2 for logging in to the servers.
· Multifactor authentication (多重身份认证) (MFA)
An additional layer of security that can be used with the root account as well.
(2) Temporary Security Credentials
Temporary Security Credentials are short-term and should never be used for long-term purposes.
Use AWS Security Token Service (AWS STS) to create and provide the temporary security credentials to your set of trusted users to control some of the AWS resources.
The temporary security credentials won’t be stored with a user; rather, they will be dynamically generated whenever a user requests them.
5. Users
An IAM user is an entity that you create in AWS to uniquely represent a person or a service. This entity interacts with AWS to do day-to-day work with AWS.
Whenever an IAM user is created, the user does not have any permission to do anything unless explicit permissions are granted to the user by an administrator or via federation.
The first time you create an AWS account, you create the AWS root account, which has unrestricted access to all the resources within AWS. After that, you should create an IAM user with administrative access and should never log in using the root account.
You can create different IAM users with different privileges according to their job profile. They have their individual usernames and passwords to log in to the AWS console.
You can create access keys via IAM to let users make programmatic calls to AWS from the AWS CLI or SDKs or API calls for individual AWS services. The access key is accessible only at the time you create it. If it is lost, you must delete the access key for the associated user and create a new key.
6. Groups
Characteristics of IAM groups:
· A group consists of multiple roles and privileges, and you grant these permissions using IAM.
· Any user who is added to a group inherits the group’s roles and privileges.
· You can add multiple users in a group.
· A user can be part of multiple groups.
· You can’t add one group into another group. A group can contain only users and not other groups.
· No default group that automatically includes all users in the AWS account, but you can create one and assign it to each and every user.
7. Roles
Two types of AWS users:
IAM users: have a permanent identity
Federated users: don’t have a permanent identity
Since federated users don’t have permanent identities, the way to control their permission is by creating a role.
IAM user can also be associated with a role.
Using roles you can define a set of permissions to access the resources that a user or service needs, but the permissions are not attached to an IAM user or group.
An IAM role is similar to a user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS.
A role is intended to be assumable by anyone who needs it.
When a user is assigned a role or when an application assumes a role, the access keys or security credentials are created dynamically by AWS during runtime and are provided to the user or application.
Use cases of using roles:
· To delegate access to users, applications, or services that don’t normally have access to your AWS resources.
· When you don’t want to embed AWS keys within the app.
· When you want to grant AWS access to users who already have identities defined outside of AWS (for example, corporate directories).
· To grant access to your account to third parties (such as external auditors).
· So that applications can use other AWS services.
· To request temporary credentials for performing certain tasks.
Two policies:
Trust policy: govern who can assume the role (in other words, the principal)
Permission or Access policy: define what resources and action the principal or who is assuming the role is allowed access to.
8. IAM Hierarchy of Privileges
AWS root user or the account owner > AWS IAM user > Temporary security credentials
9. IAM Best Practices
(1) Use the IAM user
Create an IAM user for yourself and assign admin privileges, lock down the root user and never use the root user’s access key for any programmatic requests to AWS.
(2) Create a storing password policy
Set a strong password policy and make sure the password expires after 90 days.
(3) Rotate security credentials regularly
Use the Access Key Last Used to identify and deactivate credentials that have been unused in 90 or more days.
Use the Credential Report to audit credential rotation.
(4) Enable MFA
Enable MFA for root and critical accounts with superuser privileges.
MFA provides an additional layer of protection and using it will make sure your account is protected.
(5) Manage permission with groups
Instead of assigning permission to individual users, create groups that relate to job functions and attach policies to groups.
(6) Grant the least privileges
Always start with a minimum set of permissions and grant additional permissions only as necessary.
(7) Use IAM roles
You should always use IAM roles to delegate cross-account access, to delegate access within an account, and to provide access for federated users.
(8) Use IAM roles for Amazon EC2 instances
If you have an application that runs on an Amazon EC2 instance and it needs to access other AWS services, you need to assign the application credentials.
(9) Use IAM policy conditions for extra security
IAM policies allow access to a resource, but by using policy conditions, you can set up finer-grained conditions for the access.
(10) Enable AWS CloudTrail
You must ensure that AWS CloudTrail is enable in all regions and that the AWS CloudTrail log file validation is enabled. It is also important to make sure that the Amazon S3 bucket of CloudTrail logs is not publicly accessible.
10.AWS Compliance Program
By tying together governance-focused, audit-friendly service features with applicable compliance or audit standards, AWS Compliance features build on traditional programs, helping customers to establish and operate in an AWS security control environment. (通过将适用于监管的,易于审核的服务功能与适用的合规性或审核标准结合在一起,AWS Compliance功能可在传统程序的基础上构建,从而帮助客户在AWS安全控制环境中建立和运营。)
11.Shared Responsibility Model
AWS is responsible for securing the underlying infrastructure that supports the cloud, and you’re responsible for anything you put on the cloud or connect to the cloud.
The infrastructure consists of the hard ware, software, networking and data centers that run AWS services.
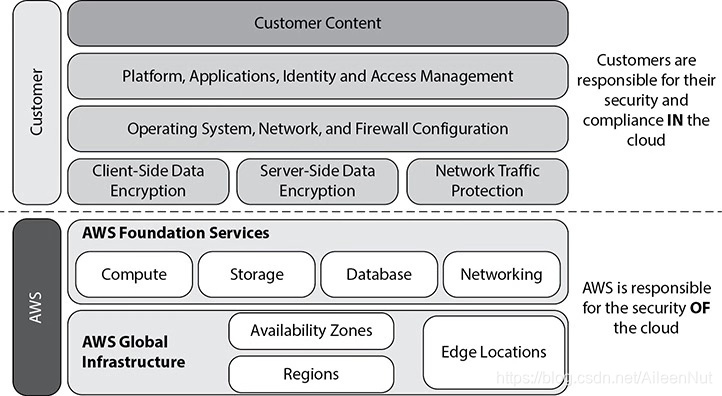
(1) AWS Responsibility
· Physical security of data center
· Amazon EC2 security
· Network security
· Configuration management
· Highly available data center
· Disk management
· Storage device decommissioning
(2) Customer’s Responsibility
The customer’s responsibility differs depending on the type of services being used from AWS.
Using AWS for IaaS, such as EC2, VPC, networking and so on.
· Operating system: Responsible for the management of the guest OS.
· Application
· Firewall
· Network configuration
· Service configuration
· Authentication and account management
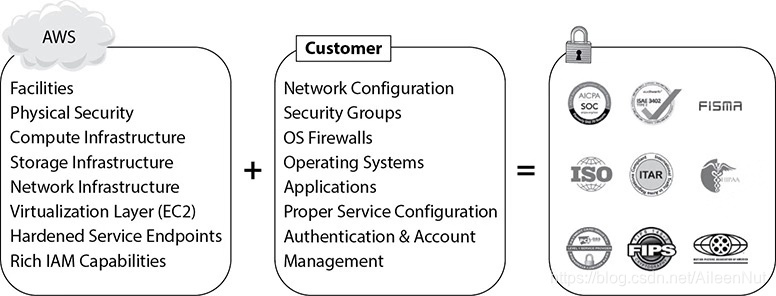
Using AWS for PaaS, which is also known as container services
You should protect your AWS account credentials and set up individual use accounts with Amazon IAM so that each of your users has their own credentials, and you can implement segregation of duties.

Using AWS for SaaS, or abstract services
A common example for using AWS as SaaS is S3. In this case, you just need to manage the data, and you are responsible for encrypting it.
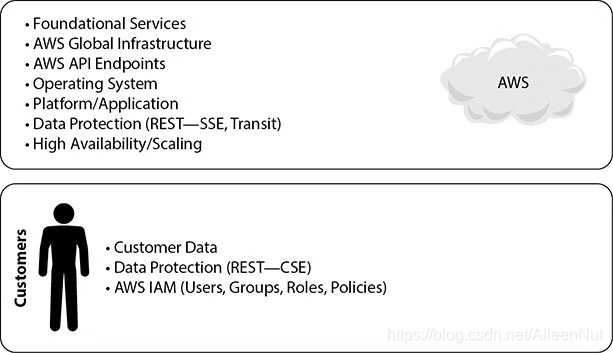
There are certain security features, such as individual user accounts and credentials, SSL/TLS for data transmissions, and user activity logging, that you should configure no matter which AWS service you use.





















 553
553











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








