北邮国院大三电商在读,随课程进行整理知识点。仅整理PPT中相对重要的知识点,内容驳杂并不做期末突击复习用。个人认为相对不重要的细小的知识点不列在其中。如有错误请指出。转载请注明出处,祝您学习愉快。
编辑软件为Effie,如需要pdf/docx/effiesheet/markdown格式的文件请私信联系或微信联系
Week2
How is criminal law different from civil law?
Some behaviour is considered so damaging (such as murder, rape, theft, terrorism, …) to society that it must be ‘criminalized’, i.e., the accused will be punished with loss of liberty, or even with death, if found guilty
有些行为被认为对社会具有极大的破坏性(如谋杀、强奸、盗窃、恐怖主义……),因此必须将其“定为犯罪”,即被告如果被判有罪,将被判处丧失自由,甚至死刑
Civil Law: no loss of liberty or life
民法:不得丧失自由或生命
2 Types of Criminal Laws
- Substantive Offences 实质性的犯罪
- PRC Criminal Law (PRC CL)
- Procedural Rules 程序法规则
- PRC Criminal Procedure Law (PRC CPL)
The Aim of both types of Criminal Laws
To define and deter ‘criminal’ acts
定义和阻止“犯罪”行为
To ensure a fair and just trial for the accused, in accordance with the law
确保依法公正审判被告人
- Constitutional Guarantee: life and liberty 宪法保障:生命和自由
Substantive Offences 实质性的犯罪
Laws that create and define socially acceptable conduct
创造和定义社会可接受行为的法律
Create and define crimes and punishment
创建和定义犯罪和惩罚
E.g. Article 120 PRC CL: "Those organizing or leading a terrorist organization shall be sentenced to ten or more years imprisonment or life imprisonment, and their property confiscated…”
例:中华人民共和国刑法第一百二十条:“组织、领导恐怖组织的,处十年以上有期徒刑或者无期徒刑,没收财产……”
Procedural Rules 程序法规则
Laws that govern the investigation, arrest, and trial of the accused
管理调查、逮捕和审判被告的法律
Protect the constitutional rights of the accused
保护被告的宪法权利
E.g.
- Article 71 PRC CPL: When making an arrest, a public security organ must produce an arrest warrant. 第七十一条中华人民共和国刑法典:公安机关实施逮捕,必须出示逮捕证。
- Within 24 hours after an arrest, the family of the arrested person or the unit to which he belongs shall be notified of the reasons for arrest and the place of custody…… 逮捕后24小时内,应将逮捕理由和拘留地点通知被逮捕人的家属或其所在单位…
Criminal Law: General Principles
- Nulla poena sine lege
法无明文规定者不罚
- No punishment without the law
- Article 3 PRC CL : For acts that are explicitly defined as criminal acts in law, the offenders shall be convicted and punished in accordance with law; otherwise, they shall not be convicted or punished. 第三条中华人民共和国刑法:法律明文规定为犯罪行为的,依法定罪处罚;否则,不得定罪或处罚。
- Nullum crimen, nulla poena sine praevia lege poenali
法无明文规定不为罪
- An act cannot be made a crime retroactively (an act must be a crime at the time it is committed)
- innocent until proven guilty 无罪推定
- Person charged with offence, but innocent till found guilty 被指控犯罪的人,但在被判有罪之前是无辜的人
- Article 12 PRC CL: No person shall be found guilty without being judged as such by a People’s Court according to law. 中华人民共和国刑法第十二条:未经人民法院依法判决,任何人不得被判有罪。
- Guilt has to be proved beyond reasonable doubt 必须排除合理疑问才能证明有罪
- Article 46 PRC CPL:In the decision of all cases, stress shall be laid on evidence, investigation and study ……. the defendant may be found guilty and sentenced to a criminal punishment if evidence is sufficient and reliable… 第四十六条中华人民共和国民事诉讼法:一切案件的判决,都应当注重证据、调查研究…如果证据充分可靠,被告可能被判有罪并处以刑事处罚。
- If there is reasonable doubt, the person charged of the offence must be acquitted 如果有合理的疑问,被控犯罪的人必须被无罪释放
- burden of proof 举证责任
- State ‘prosecutes’ (also ‘private’ prosecution in limited cases) 国家“起诉”(在有限的情况下也称为“私人”起诉)
- Prosecution’s task: to prove guilt beyond reasonable doubt 控方的任务是:排除合理怀疑证明有罪
- Defendant: rarely has to establish their innocence 被告:很少需要证明自己的清白
- right to remain silent 沉默权
- Generally, in many countries, the accused has a right to remain silent about the details of the crime with which charged 一般来说,在许多国家,被告有权对被控罪行的细节保持沉默
- China: Accused has no right to remain silent, but cannot be convicted on confession alone 中国:被告无权保持沉默,但不能仅凭供词定罪
- double jeopardy 一罪不受两次审理原则
- No person should be punished more than once for the same offence 任何人不得因同一罪行被罚一次以上
- No person should be placed twice at risk (in jeopardy) of being convicted 任何人都不应被置于两次被定罪的危险之中
- If a person is charged, tried and acquitted: CANNOT be charged for the same offence 如果一个人被指控,审判和无罪释放:不能因同一罪行被指控
- Limitations 局限性
- If offence is ‘minor’ there is no prosecution (China) 如果罪行“轻微”,就不会被起诉(中国)
- Time: Usually, time period for prosecuting offences, outside time period, crime cannot be prosecuted 时间:通常为起诉犯罪的时间,超出时间,犯罪不能被起诉
- 相关法律:Art.15 PRC CL
- In any of the following circumstances, no criminal responsibility shall be investigated; if investigation has already been undertaken, the case shall be dismissed, or prosecution shall not be initiated, or the handling shall be terminated, or innocence shall be declared: 有下列情形之一的,不追究刑事责任;已经侦查的,应当撤销案件,或者不起诉,或者终止处理,或者宣告无罪:
- (1) if an act is obviously minor, causing no serious harm, and is therefore not deemed a crime; 情节明显轻微,危害不大,不构成犯罪的;
- (2) if the limitation period for criminal prosecution has expired; 超过刑事追诉时效期间的;
-
Accused has a right to be represented by a lawyer / lawyers 被告有权由律师代表
-
No one is above the law (Art.4) 没有人可以凌驾于法律之上
-
Punishment must fit the crime (Art 5) 惩罚必须与罪行相称
-
Parties to a Crime 犯罪当事人
- Principal or Joint Principals 委托人或共同委托人
- Secondary Participants 次要的参与者
- Aiding and Abetting 协助与教唆
- Inciting 煽动
- Inchoate Offences 早期犯罪 (Also punishable)
An inchoate crime is a crime that might not be completed
早期犯罪是指可能尚未完成的犯罪
- Incitement 煽动
- Conspiracy 阴谋
- Attempt 尝试
With incitement the defendant must have tried to persuade another to commit a crime
在煽动罪中,被告肯定曾试图说服他人犯罪
With conspiracy at least two defendants must have agreed to commit a crime
共谋罪必须至少有两名被告同意犯罪
- 举个例子:
- Article 156 PRC CL: Whoever conspires with criminals of smuggling and provides them with loans, funds, account numbers, invoices or certificates or with such conveniences as transportation, storage and mailing shall be deemed an accomplice in the crime of smuggling and punished as such. 与走私犯罪分子合谋,为其提供贷款、资金、账号、发票、证件或者运输、保管、邮寄等便利的,以走私罪的共犯论处。
With attempt the defendant must have tried to commit the offence and have got relatively close to achieving this objective
有了企图,被告必须已经试图实施犯罪,并且已经相对接近实现这一目标
- 注意几个术语:Preparation for a Crime(犯罪预备), Criminal Attempt(犯罪未遂) and Discontinuation of a Crime(犯罪中止)
- Article 22 Preparation for a crime refers to the preparation of the instruments or the creation of the conditions for a crime 犯罪准备,是指准备犯罪工具或者创造犯罪条件
- Article 23 A criminal attempt refers to a case where an offender has already started to commit a crime but is prevented from completing it for reasons independent of his will. 犯罪未遂是指犯罪人已经开始犯罪,但由于非本人自愿的原因而无法完成犯罪的情况。
- Defences
↑这个词相当不好翻译,也没找到什么合适的翻译,在我的理解里是“免罪/减罪条件”的意思,下面的elements of a crime里也提到了no defense才算是crime
- Insanity 精神错乱
- Automatism 无意识行为
- Mistake 过失
- Intoxication 中毒、醉酒
- Duress by threat 威胁胁迫
- Acting in self-defence 自卫行为
- “Entrapment” 圈套
The only real questions at trial are
庭审中唯一真正的问题是
(1) did the defendant commit the illegal act and 被告是否有违法行为
(2) did she have the necessary mental state. 她有必要的精神状态吗。
- The defendant’s mental state is relevant only to determine if she acted with mens rea—did she act purposefully, knowingly, recklessly, et cetera. 被告的精神状态只与判定她的行为是否出于善意有关她的行为是否有目的,是否故意,是否鲁莽等等。
Evidence of a defendant’s motive may be introduced at trial to convince a judge that she is guilty, but motive is not perceived as a legal component of guilt.
被告动机的证据可能在审判中被引入,以说服法官她有罪,但动机不被视为有罪的法律组成部分。
Elements of a Crime
Most criminal conduct requires both a voluntary act or omission Actus Reus and a certain state of mind Mens Rea
大多数犯罪行为既需要有自愿作为或不作为的事实依据,也需要有一定的心理状态的事实依据
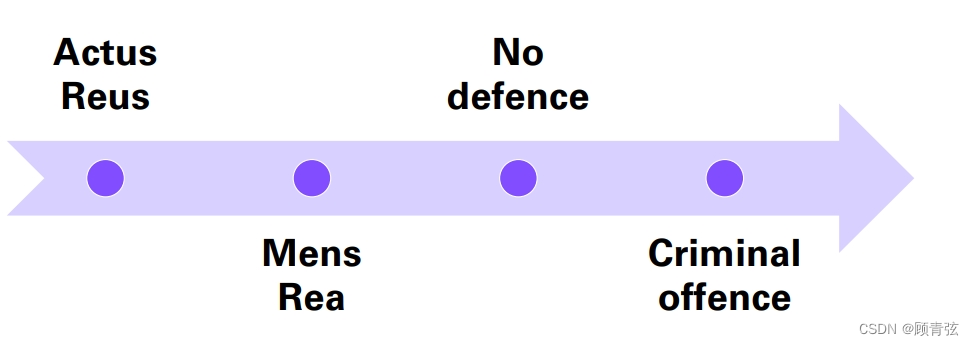
Actus Reus (guilty act) 犯罪行为
Prohibited conduct, either requiring 被禁止的行为,或是要求的
- Course of conduct (act or omission) (such as rape) 行为过程(作为或不作为)(如强奸)
- Consequences or results (such as death in ‘murder’, injury, damage to property) 后果或结果(如“谋杀”死亡、受伤、财产损失)
Usually, an act or positive action is required by the accused:
通常,被告被要求采取行动或积极行动:
- E.g. Article 170 PRC CL: Whoever counterfeits currencies shall be sentenced to fixed-term imprisonment 《中华人民共和国刑法》第一百七十条:伪造货币的,处有期徒刑
Mens Rea (guilty mind) 犯罪意图
Some offences require a specific intention to cause the result or a result close to one that occurs
有些违法行为需要有特定的意图来导致结果或与所发生的结果相近的结果
- For example, murder requires the accused intended to kill or inflict really serious harm 例如,谋杀要求被告有意杀人或造成真正严重的伤害
State of mind 心理状态
- Intention / Knowledge / Will 意图/知识/意志
- Purposely: Intends to bring about a result 故意的:有意产生结果的
- Knowingly: Parctically certain the result will occur 明知地:几乎肯定结果会发生
- Recklessness, negligence 鲁莽,疏忽
- Recklessly: Consciously disregards a substantial or unjustifiable risk 不顾后果的:有意识地忽视实质性的或不合理的风险
- Negligently: Should be aware of a substantial or unjustifiable risk, but is not. 疏忽大意:本应意识到存在重大或不合理的风险,但事实并非如此。
- Falling below the standard of the ordinary reasonable man, doing something he would do or doing something he would not do 低于普通理性人的标准,做他会做的事或做他不会做的事
几个关于Mens Rea的例子
- Article 232 PRC CL: Whoever intentionally commits homicide shall be sentenced to death, life imprisonment or fixed-term imprisonment of not less than 10 years; 《中华人民共和国刑法》第二百三十二条故意杀人的,处死刑、无期徒刑或者十年以上有期徒刑;
- Homicide: causing death of another human being 杀人罪:造成他人死亡
- Article 233 PRC CL: Whoever negligently causes death to another person shall be sentenced to fixed-term imprisonment of not less than three years but not more than seven years 中华人民共和国刑法第二百三十三条过失致人死亡的,处三年以上七年以下有期徒刑
关于Knowledge(knowingly)
- Cannot always be proven but may be inferred from both the act and surrounding circumstances. 不能总是被证明,但可以从行为和周围环境中推断出来。
- Circumstantial evidence may be allowed if it sheds light on the defendant’s state of mind. 如果能说明被告的精神状态,间接证据可以被允许。
- Post-crime conduct, such as flight, may be recognized if it demonstrates consciousness of guilt 犯罪后的行为,如逃跑,如果表现出有罪意识,可能会被承认
- 例子:
- Article 171 PRC CL: Whoever sells or buys counterfeit currencies or knowingly transports such currencies shall, if the amount involved is relatively large, be sentenced to fixed-term imprisonment of not more than three years 中华人民共和国刑法第一百七十一条买卖假币或者明知是假币而运输的,数额较大的,处三年以下有期徒刑
Intention分为两种:
- Direct 直接的
- Consequence is desired, accused decides to bring it about or tries his best to 结果是期望实现的,被告决定实现它或尽其所能
- Oblique 间接的
- Accused sees the consequence as certain or virtually certain 被告知道后果是确定的或几乎确定的
Strict Liability Offences
Strict Liability: An offence which law states requires no mens rea
严格责任:法律规定没有犯罪意图的一种罪行
Law must make it very clear that it an act is meant to be a strict liability offence
法律必须明确规定,如果一项行为意味着构成严格责任犯罪
Some offences are classed as strict liability because it would be near impossible to prove mens rea in some offences and without it, people would easily escape conviction
有些违法行为被归为严格责任,因为几乎不可能证明某些违法行为的真实,如果不证明,人们很容易逃脱定罪
For other offences, the consequences of particular acts or omissions are considered to be so serious that criminal sanctions must be imposed as a matter of social policy. For example, selling food unfit for human consumption
对于其他罪行,某些行为或不行为的后果被认为非常严重,必须作为一项社会政策予以刑事制裁。例如,出售不适合人类食用的食品
Coincidence of actus reus and mens rea
A criminal offence requires both the actus reus and the mens rea to occur (except strict liability) at the same time or very closely to each other for criminal liability to be established
刑事犯罪要求犯罪行为和犯罪目的(严格责任除外)同时发生或彼此非常接近,才能成立刑事责任
Chinese criminal law defines crime as
Any act endangering society and subject to punishment –‘criminal’ act
任何危害社会并受到惩罚的行为——“犯罪”行为
Where circumstances are *‘minor’ *and harm is not ‘serious’: the act is not a criminal act but an ‘unlawful’ act
如果情况“轻微”,而损害并不“严重”,该行为不是刑事行为,而是“非法”行为
Article 13 A crime refers to an act that endangers the sovereignty, territorial integrity and security of the State, splits the State, subverts the State power of the people’s democratic dictatorship and overthrows the socialist system, undermines public and economic order, violates State-owned property, property collectively owned by the working people, or property privately owned by citizens, infringes on the citizens’ rights of the person, their democratic or other rights, and any other act that endangers society and is subject to punishment according to law. However, if the circumstances are obviously minor and the harm done is not serious, the act shall not be considered a crime
危害国家主权、领土完整和安全,分裂国家,颠覆人民民主专政的国家政权,推翻社会主义制度,破坏公共秩序和经济秩序,侵犯国有财产、劳动人民集体所有的财产、公民私人所有的财产,侵犯公民的人身权利、民主权利和其他权利的行为。其他危害社会的行为,应当依法受到处罚。情节明显轻微,危害不大的,不构成犯罪
The PRC’s legislature 中华人民共和国立法机关
the National People’s Congress (NPC), or its Standing Committee
全国人民代表大会(NPC)或其常务委员会
- determines the threshold separating a criminal act from an unlawful act 确定区分犯罪行为和非法行为的界限
- by specifying the extent of seriousness of the consequences and circumstances to which an act warrants a criminal penalty. 具体说明后果的严重程度和行为应受到刑事处罚的情节。
Prosecution of a crime 检控罪行(看看就行,了解一下流程)
- Complaint - 控告
- Investigation by the police 警方的调查
- Court trial – prosecutors and defence lawyers 法庭审判——检察官和辩护律师
The police is the most powerful institution in China’s criminal process
警察是中国刑事诉讼中最有权力的机构
- Investigate (wide powers to investigate) 调查(广泛的调查权力)
- Gather evidence 收集证据
The Procuracy 检察院
- Performs multiple functions as an investigative, prosecutorial, supervisory, and judicial body 作为调查、起诉、监督和司法机构,履行多种职能
- Institutes public prosecution against all crimes in court. 在法庭上对所有罪行提起公诉。
- After the investigators conclude their investigations, they transfer the case to the procuracy for public prosecution. 侦查人员侦查完毕后,将案件移送检察院提起公诉。
- Where the procuracy considers the facts to be clear, the evidence reliable and complete, and the offense serious enough to warrant criminal sanction, it shall initiate a public prosecution in a court with competent jurisdiction, unless the case is “obviously minor” or where other statutory conditions exist 检察院认为事实清楚,证据可靠、完整,犯罪情节严重,应当给予刑事处罚的,应当向有管辖权的法院提起公诉,但案件“情节明显轻微”或者存在其他法定条件的除外
Court Trial 法庭审判
- Prosecution provides a Bill of Prosecution and a list of evidence to be produced in court 控方提供一份检控书和一份将在法庭上出示的证据清单
- The court will decide to try the case if there is prima facie evidence of criminal wrongdoing 如果有犯罪行为的初步证据,法院将决定审理此案
Prosecution bears the burden of proof
控方负有举证责任
- Defence: can cross-examine the prosecution evidence and produce its own evidence to challenge the allegation. 辩方:可以交叉询问控方证据,并提出自己的证据来质疑指控。
- Make strong arguments on behalf of the accused 为被告辩护
Judges: neutral and passive arbitrators, evaluating evidence and arguments presented before the court
法官:中立和被动的仲裁员,评估在法庭上提出的证据和论点
- ‘Not-guilty’ verdicts possible “无罪”判决是可能的
The principle of territoriality
Article 6: This Law shall be applicable to anyone who commits a crime within the territory and territorial waters and space of the People’s republic of China, except as otherwise specifically provided by law.
第六条在中华人民共和国领土和领水空间内犯罪的,适用本法,法律另有规定的除外。
- This Law shall also be applicable to anyone who commits a crime on board a ship or aircraft of the People’s Republic of China. 在中华人民共和国船舶、航空器上犯罪的,也适用本法。
- If a criminal act or its consequence takes place within the territoryor territorial waters or space of the People’s Republic of China, the crime shall be deemed to have been committed within the territory and territorial waters and space of the People’s Republic of China. 犯罪行为及其后果在中华人民共和国领土、领水、空间内发生的,视为在中华人民共和国领土、领水、空间内实施。
- Article 7 : Chinese citizen committing a crime abroad, if punishment more than 3 years under the PRC CL: may be tried in China 第七条中国公民在国外犯罪,依照中华人民共和国刑法判处三年以上刑罚的,可以在中国境内审判
- Article 8: Foreigner committing a crime abroad against a Chinese citizen, PRC CL may apply 第八条外国人在国外对中国公民犯罪的,中华人民共和国刑事诉讼法可以提出申请
刑法这块看看就好了,要考应该也是和Cybercrime一起考,复习时间不够的话就背几个关键词就行了
The definition of cybercrime
Cybercrime is an act that violates the law, which is perpetrated using information and communication technology
网络犯罪是一种利用信息和通信技术实施的违法行为
- Any activity in which computers or computer networks are a tool, a target or a place of criminal activity 以计算机或计算机网络为工具、目标或犯罪活动场所的任何活动
- Cybercrime differs from traditional crime in that it “knows no physical or geographic boundaries” and can be conducted with less effort, greater ease, and at greater speed than traditional crime 网络犯罪与传统犯罪的不同之处在于,它“没有物理或地理界限”,与传统犯罪相比,它可以更容易、更省力、更快地实施
While cyber crime may be global, investigation and prosecution is territorial along territories and by jurisdictions
虽然网络犯罪可能是全球性的,但调查和起诉是根据领土和司法管辖区进行的
The classification of cybercrime
-
Cyber-dependent crimes = any crime that can only be committed using computers, computer networks or other forms of information communication technology 依赖网络的犯罪=任何只能通过计算机、计算机网络或其他形式的信息通信技术实施的犯罪
-
Cyber-enabled crimes = traditional crimes facilitated by the Internet and digital technologies 网络犯罪=利用互联网和数字技术进行的传统犯罪
-
Crime and computers can be linked in three ways 犯罪和计算机可以通过三种方式联系起来
-
Computers:
- Can be the target of an offense 成为违法行为的目标
- Can be the tool to commit a crime 成为犯罪的工具
- Can be incidental to a crime 是犯罪的附带事件
Computers as the target of the offence
Computers can be the target of an offense: when confidentiality, integrity, and availability of data, applications, networks is compromised
当数据、应用程序和网络的机密性、完整性和可用性受到损害时,计算机可能成为攻击的目标
- Hacking (trespass) 黑客(侵权)
- Cracking (burglary) 破解(盗窃)
- Malicious code (viruses, worms, Trojan horses) 恶意代码(病毒、蠕虫、特洛伊木马)
- Vandalism (web site defacement) 破坏公物(破坏网站)
- Denial of service and DDoS attacks 拒绝服务和DDoS攻击
Computers as tools
Computers can be the tool to commit a crime, includes fraud, child pornography, conspiracy
电脑可以成为犯罪的工具,包括诈骗、儿童色情、阴谋
In this scenario, the ICT is part of the modus operandi to commit traditional crimes, such as fraud or theft
在这种情况下,信息通信技术是实施传统犯罪(如欺诈或盗窃)的手法的一部分
It also includes activities aiming to damage or modify other computerised systems (usually prosecuted using computer crime legislation)
它还包括旨在破坏或修改其他计算机化系统的活动(通常使用计算机犯罪立法起诉)。
- Fraud 欺诈
- Theft 偷窃
- Extortion 敲诈勒索
- Cyberstalking 网络骚扰(跟踪或威胁)
- Child pornography 儿童色情
Computers being incidental to a crime
Computers can be incidental to a crime but have significant importance to law enforcement, especially for evidentiary purposes
计算机可能是犯罪的附带品,但对执法具有重要意义,特别是对于证据目的
- Blackmailer uses computer to write blackmail letters 勒索者用电脑写勒索信
- Drug dealer stores records on computer 毒贩在电脑上储存记录
- Computer used to research murder methods 用来研究谋杀方法的计算机
The goals and objectives of cybercrime laws
Prevention, investigation and law enforcement against cybercrimes
网络犯罪的预防、调查和执法
Virtually all modern services depend on the use of ICT, with computer technology integrated into products and services
几乎所有的现代服务都依赖于信息通信技术的使用,计算机技术被整合到产品和服务中
- Essential services such as water and electricity supply 基本服务,如水和电力供应
- Transportation infrastructure, military services and logistics 交通基础设施、军事服务和后勤
- Cars, traffic control, elevators, air conditioning and telephones 汽车、交通管制、电梯、空调和电话
Challenges
Growing danger from crimes committed against computers or against information on computers
针对计算机或计算机信息的犯罪日益增加的危险
Attacks against information infrastructure and Internet services now have the potential to harm society in new and critical ways
对信息基础设施和互联网服务的攻击现在有可能以新的和关键的方式危害社会
Emerging new threats from nation-states, private sector offensive actors, use of AI and ML techniques
来自民族国家、私营部门攻击行为者、人工智能和机器学习技术使用的新威胁
- WSJ SolarWinds attack
- NSO Group (US litigation)
Deterrence is critical 威慑至关重要
Global reach of cybercrime
- Cybercrime cannot be addressed by an individual nation or group of nations 网络犯罪不能由单个国家或国家集团来解决
- Cybercrime is important to national and economic security interests 网络犯罪关系到国家和经济安全利益
- Public safety 公共安全
Jurisdiction of Cybercrime law
Courts have the ability to only ‘hear’ cases that or disputes that are within their jurisdiction
法院有能力只“审理”在其管辖范围内的案件或争议
Jurisdiction describes the authority a particular court has to hear a case
管辖权是指某一法院审理案件的权力
- Subject matter jurisdiction (family court, federal court) 事项管辖权(家事法院、联邦法院)
- Personal jurisdiction 属人管辖权
Personal jurisdiction refers to the court’s ability to exercise power over the defendant
属人管辖权是指法院对被告行使权力的能力
Particularly challenging for cybercrime as geographical boundaries to not limit computer networks
网络犯罪尤其具有挑战性,因为地理边界不能限制计算机网络
In most cases, the perpetrators reside in a jurisdiction other than that of their victims
在大多数情况下,肇事者居住在受害人管辖地以外的司法管辖区
In order to investigate such a case, evidence must be obtained from multiple jurisdictions
为了调查这类案件,必须从多个司法管辖区获得证据
International cooperation across national borders to solve and prosecute crimes is complex and slow
跨越国界解决和起诉犯罪的国际合作是复杂而缓慢的
Convention on Cybercrime
First multinational treaty on cybercrime issues
第一个关于网络犯罪问题的多国条约
Global benchmark for cybercrime legislation in both industrialized and developing countries
工业化国家和发展中国家网络犯罪立法的全球基准
Important international benchmark
重要的国际基准
The Convention is today recognised as an important international instrument in the fight against Cybercrime and is supported by different international organisations
《公约》已被公认为打击网络罪行的重要国际文书,并得到不同国际组织的支持
access: “threshold offence” 访问:“门槛犯罪”
Different countries criminalize different aspects of access
不同的国家将不同方面的访问行为定为犯罪
Illegal Access
Intentional access without right to the whole or part of any computer system (the treaty does not contain the concept of a ‘protected’ computer)
故意访问,但无权访问全部或部分计算机系统(条约不包含“受保护”计算机的概念)
Access is about attacks on stored data
访问指的是对存储数据的攻击
The definition of ‘access’ is open-ended, open to further technical developments
“接入”的定义是开放式的,对进一步的技术发展是开放的
Includes all means of entering another computer system, including Internet attacks, as well as illegal access to wireless networks
包括所有进入另一个计算机系统的手段,包括互联网攻击,以及非法接入无线网络
Hacking
Unlawful access to a computer system, such as:
非法进入电脑系统,例如:
- Breaking the password of password-protected websites 破解密码保护网站的密码
- Circumventing password protection on a computer 规避计算机上的密码保护
Preparatory acts include:
准备行动包括:
- Use of faulty hardware or software implementation to illegally obtain a password to enter a computer system; 使用有缺陷的硬件或者软件实现,非法获取进入计算机系统的密码;
- Setting up ‘spoofing’ websites to make users disclose their passwords; 建立“欺骗”网站,让用户泄露密码;
- Installing hardware and software based keylogging methods (e.g. ‘keyloggers’) that record every keystroke and consequently any passwords used on the computer and/or device 安装基于键盘记录方法的硬件和软件(例如“键盘记录器”),记录每次击键,从而记录计算机和/或设备上使用的任何密码
illegal access的motives
- ‘Hackers’ showing off “黑客”的炫耀
- Hacktivism 泛指因政治或社团目的而产生的黑客行为,或者是入侵计算机系统。
- To commit further crimes: data espionage, DDoS, data manipulation 进一步犯罪: 数据间谍,DDoS攻击,数据操纵
Convention on Cybercrime
Article 2 – Illegal access
Each Party shall adopt such legislative and other measures as may be necessary to establish as criminal offences under its domestic law, when committed intentionally, the access to the whole or any part of a computer system without right.
A Party may require that the offence be committed by infringing security measures, with the intent of obtaining computer data or other dishonest intent, or in relation to a computer system that is connected to another computer system.
各缔约方应采取必要的立法和其他措施,根据其国内法,将故意使用计算机系统的全部或任何部分而没有权利的行为确定为刑事犯罪。
缔约方可以要求该犯罪行为是通过违反安全措施,以获取计算机数据或其他不诚实的意图,或与连接到另一计算机系统的计算机系统有关的方式实施的
Substantive Criminal Law
相关法律:
Article 285 PRC Criminal Law
Whoever violates state regulations and intrudes into computer systems with information concerning state affairs, construction of defense facilities, and sophisticated science and technology is be sentenced to not more than three years of fixed-term imprisonment or limited incarceration.
Whoever, in violation of the state provisions, intrudes into a computer information system other than that prescribed in the preceding paragraph or uses other technical means to obtain the data stored, processed or transmitted in the said computer information system or exercise illegal control over the said computer information system shall, if the circumstances are serious, be sentenced to fixed-term imprisonment not more than three years or limited incarceration, and/or be fined; or if the circumstances are extremely serious, shall be sentenced to fixed-term imprisonment not less than three years but not more than seven years, and be fined.
Whoever provides special programs or tools specially used for intruding into or illegally controlling computer information systems, or whoever knows that any other person is committing the criminal act of intruding into or illegally controlling a computer information system and still provides programs or tools for such a person shall, if the circumstances are serious, be punished under the preceding paragraph.
Where an entity commits any crime as provided for in the preceding three paragraphs, the entity shall be sentenced to a fine, and its directly responsible person in charge and other directly liable persons shall be punished according to the provisions of the applicable paragraph.
【非法侵入计算机信息系统罪】违反国家规定,侵入国家事务、国防建设、尖端科学技术领域的计算机信息系统的,处三年以下有期徒刑或者拘役。
【非法获取计算机信息系统数据、非法控制计算机信息系统罪】违反国家规定,侵入前款规定以外的计算机信息系统或者采用其他技术手段,获取该计算机信息系统中存储、处理或者传输的数据,或者对该计算机信息系统实施非法控制,情节严重的,处三年以下有期徒刑或者拘役,并处或者单处罚金;情节特别严重的,处三年以上七年以下有期徒刑,并处罚金。
【提供侵入、非法控制计算机信息系统程序、工具罪】提供专门用于侵入、非法控制计算机信息系统的程序、工具,或者明知他人实施侵入、非法控制计算机信息系统的违法犯罪行为而为其提供程序、工具,情节严重的,依照前款的规定处罚。
单位犯前三款罪的,对单位判处罚金,并对其直接负责的主管人员和其他直接责任人员,依照各该款的规定处罚。
Interception 拦截
Intentional interception, without right, made by technical means, of non-public transmissions of computer data.
未经许可,利用技术手段故意截取非公开传输的计算机数据。
Attacks on transmitted data
对传输数据的攻击
illegal interception
- Offenders can intercept communications between users 违法者可以拦截用户之间的通信
- such as e-mails;
- Intercept data transfers to record the information exchanged 拦截数据传输,记录交换的信息
- when users upload data onto web servers or access web-based external storage media; 当用户将数据上传到网络服务器或访问基于网络的外部存储媒体时;
- Offenders can target any communication infrastructure 罪犯可以攻击任何通信基础设施
- e.g., fixed lines or wireless and any Internet service o e.g. e-mail, chat or VoIP communications 例如,固定线路或无线和任何互联网服务,例如电子邮件、聊天或VoIP通信
- Offenders look for weak points in the system 罪犯会寻找系统的弱点
- particularly wireless networks 特别是无线网络
Convention on Cybercrime
Article 3 – Illegal interception
… when committed intentionally, the interception without right, made by technical means, of non-public transmissions of computer data to, from or within a computer system, including electromagnetic emissions from a computer system carrying such computer data.
A Party may require that the offence be committed with dishonest intent, or in relation to a computer system that is connected to another computer system.
故意实施时,通过技术手段,无权利拦截计算机数据向计算机系统、从计算机系统或在计算机系统内的非公开传输,包括从载有该计算机数据的计算机系统发出的电磁发射。
一方当事人可以要求该犯罪行为具有不诚实的意图,或者与连接到另一计算机系统的计算机系统有关。
- 具体有哪些Technical means?
- Listening to, monitoring or surveillance of the content of communications 监听、监视或监视通信内容的
- To the procuring of the content of data either directly, through access and use of the computer system, or 直接获取数据的内容,通过访问和使用计算机系统,或
- Indirectly, through the use of electronic eavesdropping or tapping devices. Interception may also involve recording. 间接地,通过使用电子窃听或窃听设备。拦截也可能涉及录音。
In general the provision only applies to the interception of transmissions – access to stored information is not considered as an interception of a transmission.
一般来说,该规定只适用于拦截传输——获取存储的信息不被视为拦截传输。
Data Interference 数据干扰
Intentional damage, deletion, deterioration, alteration, or suppression of computer data without right (parties can reserve the right to require that it causes serious harm)
在没有权利的情况下故意破坏、删除、恶化、篡改或压制计算机数据(当事人可以保留要求造成严重损害的权利)
Manipulation or destruction of information 操纵或破坏信息
methods of data interference
Offenders can violate the integrity of data and interfere with them by:
违法者可以通过以下方式侵犯数据的完整性并进行干扰:
- deleting data; and/or 删除数据
- suppressing data; and/or 隐瞒数据
- altering data; and/or 变更数据
- restricting access to them. 限制访问它们
Computer viruses 计算机病毒
Delete data, modify data
删除数据,修改数据
Can take remote control of the computer of the victim or
能远程控制受害者的电脑
Encrypt files so that victims are denied access to their own files, until they pay money to receive the key.
加密文件,让受害者无法访问自己的文件,直到他们付钱获得密钥。
Convention on Cybercrime
Article 4 – Data interference
(1) … when committed intentionally, the damaging, deletion, deterioration, alteration or suppression of computer data without right.
故意擅自破坏、删除、变质、篡改或者压制计算机数据的。
(2) A Party may reserve the right to require that the conduct described in paragraph 1 result in serious harm.
缔约方可保留要求第1款所述行为造成严重损害的权利。
System Interference 系统干扰
Intentional and serious hindering of the function of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering, or suppressing computer data
通过输入、传输、破坏、删除、恶化、更改或抑制计算机数据,故意并严重妨碍计算机系统功能的行为
methods of system interference
Offenders succeed in preventing computer systems from operating smoothly:
违法者成功阻止电脑系统正常运作:
- Computer worms; or 计算机蠕虫
- Denial-of-Service (DoS) attacks 阻断式服务攻击(DoS)
Convention on Cybercrime
Article 5 – System interference
… when committed intentionally, the serious hindering without right of the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data.
故意输入、传输、破坏、删除、变质、篡改、压制计算机数据,严重妨碍计算机系统正常运行的。
Misuse of devices 设备滥用
Intentional, without right, production, sale, import and distribution of devices to commit any of the computer crimes
故意,无正当理由,生产、销售、进口、分销设备实施计算机犯罪的
Possession of such devices, with intent to commit computer crimes
拥有此类设备,意图实施计算机犯罪
Serious issue: availability of software and hardware tools designed to commit crimes
严重的问题是:用于犯罪的软件和硬件工具的可用性
- Crimeware, malware, scareware … 犯罪软件,恶意软件,恐吓软件…
Sophisticated offences can be committed using specialist software tools
复杂的犯罪可以使用专门的软件工具来实施
- Software tools exist to:
- Carry out DoS attacks; 执行DoS攻击;
- Design computer viruses; 设计电脑病毒;
- Decrypt encrypted communication; and 解密加密通信
- Illegally access computer systems. 非法进入电脑系统
Convention on Cybercrime
The CoC criminalizes Production of ‘crimeware’ and Possession of ‘crimeware’ to commit crimes
《准则》将生产“犯罪软件”和拥有“犯罪软件”犯罪定为刑事犯罪
Article 6 – Misuse of Devices
(1) ….when committed intentionally and without right:
- (a) the production, sale, procurement for use, import, distribution or otherwise making available of: 生产、销售、采购使用、进口、分销或以其他方式提供:
- (i) a device, including a computer program, designed or adapted primarily for the purpose of committing any of the offences established in accordance with the above Articles 2 through 5; 主要为实施根据上述第2至第5条确立的任何犯罪而设计或改造的装置,包括计算机程序
- (ii) a computer password, access code, or similar data by which the whole or any part of a computer system is capable of being accessed, with intent that it be used for the purpose of committing any of the offences established in Articles 2 through 5; and 计算机密码、存取代码或类似数据,可借此存取计算机系统的全部或任何部分,而意图将该等数据用于犯下第2至第5条所定的任何罪行;和
- (b) the possession of an item referred to in paragraphs a) i or ii above, with intent that it be used for the purpose of committing any of the offences established in Articles 2 through 5.…. a number of such items be possessed before criminal liability attaches. 拥有上述a) i或ii款所述物品,意图将其用于犯下第2至第5条所定的任何罪行…在承担刑事责任之前,必须拥有一些这样的物品。
Preventative measures 预防措施
Beacons – imperceptible, remotely hosted graphics inserted into content to trigger a contact with a remote server that will reveal the IP address of a computer that is viewing such content
信标-插入内容的难以察觉的远程托管图形,以触发与远程服务器的联系,从而显示正在查看此类内容的计算机的IP地址
Honeypots – digital traps designed to trick cyber attackers into taking action against a synthetic network, thereby allowing an organisation to detect and counteract attempts to attach its network without causing any damage to the organisation’s real network or data
诱捕系统——旨在诱骗网络攻击者对合成网络采取行动的数字陷阱,从而允许组织检测并抵制连接其网络的企图,而不会对组织的真实网络或数据造成任何损害
Sinkholes – measures to re-direct malicious traffic away from an organisation’s own IP addresses and servers, commonly used to prevent DDoS attacks
天坑-将恶意流量从组织自己的IP地址和服务器重定向的措施,通常用于防止DDoS攻击
Legality of preventative measures 预防措施的合法性
The use of beacons may result in the collection and use of users’ personal information
信标的使用可能导致用户个人信息的收集和使用
Pursuant to Chinese Cybersecurity law, organisations shall notify users and obtain their consent before collecting information
根据中国网络安全法,组织在收集信息前应通知用户并征得其同意
Considering the difficulty of obtaining consent when collecting information through beacons, they are generally regarded as not complying with the basic requirements under Cybersecurity Law
考虑到通过信标收集信息时难以获得同意,它们通常被认为不符合《网络安全法》的基本要求
Relevant laws and regulations do not explicitly prohibit organisations from using honeypots and sinkholes to detect and deflect incidents in their own network
相关法律法规并未明确禁止组织使用诱捕系统和天坑来检测和转移自己网络中的事件
Key Challenges in fighting cybercrime
- Technical Challenges 技术挑战
- Legal Challenges 法律挑战
- Operational Challenges 操作挑战
Technical challenge
- Cybercriminals are not hampered by territorial borders 网络罪犯不受地域边界的限制
- Difficulty in identifying and locating cybercriminal and the computer involved 难以识别和定位网络罪犯和涉及的计算机
- Difficulty of locating evidence of crime stored at remote location 难以找到存放在偏远地点的犯罪证据
- Cybercriminals can hide their identities through anonymous software 网络罪犯可以通过匿名软件隐藏自己的身份
- Availability of hacking tools and techniques on the internet 网络上黑客工具和技术的可用性
- Difficulty for real-time tracing of transmission when the architecture of the internet does not support it 在互联网架构不支持的情况下,难以对传输进行实时跟踪
- Strong encryption used by criminals 罪犯使用的强加密
- Wireless and satellite communications 无线和卫星通信
- The problem of co-operation from the private sector/industry 私营部门/行业的合作问题
- International co-operation 国际合作
Lack of Co-operation From the Industry
Corporate victims’ reluctance to report cybercrime to the authorities
企业受害者不愿向当局报告网络犯罪
Difficulty in collecting information on cybercrime
网络犯罪信息收集困难
Lack of reliable and efficient procedures and communication channels and co-operation between public and private sector
公营和私营部门之间缺乏可靠和有效的程序和沟通渠道及合作
Legal Challenges
- Absence of cyber criminal law 网络刑法缺失
- Jurisdictional issue – inconsistent substantive criminal laws in different parts of the world 管辖权问题——世界不同地区实体刑法的不一致
- Law lags behind technology and social change 法律落后于技术和社会变革
- Lack of a universal legal framework at international level 在国际一级缺乏普遍的法律框架
Laws of most countries in the early days of the internet : no clear prohibition of cyber crimes
大多数国家在互联网早期的法律:没有明确禁止网络犯罪
Existing laws: do not always cover cybercrime
现有法律:并不总是涵盖网络犯罪
- e.g. May 2000 Love Bug virus, caused billions of dollars of damage worldwide, but the perpetrators could not be punished 2000年5月,爱虫病毒在世界范围内造成了数十亿美元的损失,但肇事者却得不到惩罚
Jurisdiction
这些关于jurisdiction的基本不用背,但是要看看,因为我觉得提到网络犯罪肯定要提到Jurisdiction的问题,这些可以当做答题素材用
Jurisdictional borders pose unique challenges to the investigation of crimes committed in cyberspace
司法管辖区的边界对调查网络空间犯罪构成了独特的挑战
Cyber criminals can defy the conventional jurisdictional realms of sovereign nations, originating an attack from almost any computer in the world, passing it across multiple national boundaries, or designing attacks that appear to be originating from foreign sources
网络犯罪分子可以无视主权国家的传统管辖范围,从世界上几乎任何一台计算机发起攻击,将其跨越多个国家边界,或者设计看似来自外国的攻击
Technically, legally complex to investigate and prosecute cyber crime
从技术上讲,调查和起诉网络犯罪在法律上是复杂的
In most cases, the perpetrators reside in a jurisdiction other than that of their victims
在大多数情况下,肇事者居住在受害人管辖地以外的司法管辖区
In order to investigate such a case, evidence must be obtained from multiple jurisdictions
为了调查这类案件,必须从多个司法管辖区获得证据
- e.g. ILoveYou: Started in the Philippines, caused damage worldwide, prosecution in the Philippines, but failed 例如:ILoveYou:在菲律宾开始,在世界范围内造成损害,在菲律宾被起诉,但失败了
International cooperation across national borders to solve and prosecute crimes is complex and slow
跨越国界解决和起诉犯罪的国际合作是复杂而缓慢的
Possible for cyber criminal to be physically located in one country, weave an attack through multiple countries & computers, and store evidence on servers in yet another country
网络犯罪分子可能在一个国家,通过多个国家和计算机组织攻击,并将证据存储在另一个国家的服务器上
Victims may be all over globe, jurisdiction may be questionable
受害者可能遍布全球,管辖权可能存在问题
Internet borderless but law enforcement must stop at borders
互联网无国界,但执法必须止于边界
Challenge – to identify the location of cybercrime and decide which law apply to that conduct
挑战-确定网络犯罪的地点,并决定适用于该行为的法律
Substantive & procedural laws of countries may conflict
各国的实体法和程序法可能有冲突
Letters rogatory & multilateral assistance treaties (MLATs) time consuming, inconsistent
文书和多边援助条约(mlat)耗时,不一致
- Mutual Legal Assistance Treaties (MLATs) - 司法互助协定
- The most common mechanism for obtaining international legal assistance is the voluntary cooperation between governments 获得国际法律援助的最常见机制是政府间的自愿合作
- MLAT worked well enough for 20th Century Crimes, but too slow for cybercrime MLAT在20世纪的犯罪中表现不错,但在网络犯罪中表现太慢
Dual criminality requirements very problematic
双重犯罪要求很成问题
- Dual criminality : e.g. ‘I love you’ virus!
- The act under investigation must be criminalized under both countries’ laws and punishable by a minimum term in prison, usually one year. 被调查的行为必须在这两个国家的法律中被定为犯罪,并受到最低刑期的惩罚,通常是一年。
- If the act being investigated does not meet that requirement, the country receiving the request to extradite does not have to fulfil it. 如果正在调查的行为不符合这一要求,则收到引渡请求的国家不必履行这一要求。
Needs to be way to secure extradition
必须有办法确保引渡
- Extradition: 引渡
- A principle of sovereignty is that every state has legal authority over the people within its borders. 主权原则是指每个国家对其境内的人民拥有合法权力
- The consensus in international law is that a state does not have any obligation to surrender an alleged criminal to a foreign state 国际法的共识是,一个国家没有义务将被指控的罪犯移交给外国
Example: the United States
- In addition to more than 87,000 local jurisdictions, there are more than 3,000 county jurisdictions, 50 state jurisdictions, and 94 federal jurisdictions in the United States 除了87,000多个地方司法管辖区外,美国还有3,000多个县司法管辖区,50个州司法管辖区和94个联邦司法管辖区
Law enforcement burdened with cumbersome mechanisms for international co-operation, which often derail or slow investigations
繁琐的国际合作机制给执法部门带来了负担,常常使调查偏离轨道或放慢速度
Investigative techniques are governed by national law
调查手段受国家法律管辖
Operational challenges
- Lack of understanding of the technology 缺乏对技术的理解
- Lack of expertise or skilled cyber investigators 缺乏专业知识或熟练的网络调查人员
- Lack of regular and frequent training in investigation and prosecution of computer crime cases 在调查及检控电脑罪案方面缺乏定期及经常的训练
- Lack of availability of computer forensic capabilities 缺乏可用的计算机取证能力
International Legislative Approaches 国际立法途径
这个有很多,自己去看看PPT,我们只简单介绍一个:Council of Europe (CoE) Convention on Cybercrime(欧洲委员会(CoE)网络犯罪公约)
CoE Convention on Cybercrime
The Convention on Cybercrime distinguishes between four different types of offences:
《网络犯罪公约》区分了四种不同类型的犯罪:
- Offences against the confidentiality, integrity and availability of computer data and systems; 违反计算机数据和系统的机密性、完整性和可用性的罪行;
- Computer-related offences; 计算机相关的犯罪;
- Content-related offences; and 内容相关的罪行
- Copyright-related offences 与著作权有关的罪行
























 1307
1307











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








