11. Privacy
There are many ways to collect information: spyware, cookies, biometrics, DNA testing, face recognition, search engines and web surfing, data mining via AI systems, and social networking.
Privacy includes bodily privacy like protection of physical space, territorial privacy, communications privacy like protection of mail/telephone conversations and emails, and privacy for information like protection of personal data.
We need to balance privacy rights with other needs such as national security and business efficiency where information needs to be collected.
Privacy Laws is a general concept which mentioned in many specific regulations such as constitutional rights, tort law, property rights, criminal law, information law which includes Data Protection Laws, and Law of Evidence.
Technologies are threatening privacy when surveilling and collecting information, especially using databases which collect, store, exchange and process information about individuals like profiling, and using ecommerce where more collection and utilization of information occur.
Online information is collected via cookies, webbugs, spyware, targeted advertising, DRM technologies(Digital Right Management), bots, crawlers, or spiders.
Dark side of information collection and processing like abuse of census data, data errors, nuisance information collection like spam where customers’ email addresses are either sold to companies for unsolicited commercial emailing or mined. Spam is a threat cause information is traded without personal consent, resulting in control loses and privacy invades.
Privacy laws do not prevent government and ecommerce collection, control and use of information, which is for national security, public interest like reporting news, and regulating employers by snooping on existing or potential employee. Such actions should be fair and reasonable to ensure that information is not abused and accurate.
There are many approaches to protect personal data, including comprehensive laws like EU General Data Protection Regulation, sectoral laws like China pre-2021, self regulation which is favored in US in ecommerce relations, and using technologies such as encryptions and proxy servers(gateway between users and the Internet to prevent cyber attacks).
For data protection laws, they are used to strike a balance between individual privacy rights and business purposes, to establish trust like framework to oversee collection and use, or to give individuals control on over collection and use of information, accuracy of information held or protection from abuse.
Different countries or regions have distinct legal frameworks especially those for online information like in ecommerce context.
USA and China use sectoral protection on data, each law protect particular circumstances. Whereas EU has omnibus laws which overcast set of rules designed to protect personal data in all circumstances(GDPR).
12. EU Data Protection Law GDPR
Two key principles:
1. Europe Convention on Human Rights(ECHR) ACL 8, Rights to respect for private and family life.
2. Support free flow of information throughout the EU to promote the growth of the Single Market economy, which gives powers to internal markets.
EU Charter of Fundamental Rights: All EU countries are also members of the CoE (Council of Europe)
ACL 7: Everyone has the right to respect for his or her private and family life, home and communications.
ACL 8: Protection of personal data:

EU General Data Protection Regulation
Recital 1: fundamental rights and freedoms of natural persons to protection of personal data
Recital 4: Data protection in Balance with Other Fundamental Rights: the right is not absolute, it must be considered in relation to its function in society and be balanced against other fundamental rights.
Recital 5: Cooperation Between Member States to Exchange Personal Data: to serve the economic and social integration from the internal market, the exchange of public and private actors’ personal information, and the duties of national authorities.
Recital 6: Ensuring a high level of data protection despite the increased exchange of data: since technology developments challenge personal data protection, the scale of data collection and sharing increased, companies and public authorities use personal data in large scale, personal information could easily be accessed. So technology facilitates free flow of personal data within the union and third parties’ transfer, inquiring a higher level of protection.
Recital 7: The framework is based on control and certainty: trust is needed for digital economy in the internal market by applying a more strong and coherent data protection framework. So natural person should have control over their personal data and legal and practical certainty should be enhanced.( Legal certainty is the principle that a legal system be predictable and transparent. It is considered a protection that guarantees that the law will not be used in an arbitrary way.)
Recital 8: Adoption into National Law: incorporation GDPR into national law
Recital 9: Different Standards of Protection by the Directive->Recital 10: Harmonized Level of Data Protection Despite National Scope->Recital 11: Harmonization of the Powers and Sanctions->Recital 12: Authorization Transparency of the European Parliament and the Council->
Recital 13: Legal certainty and transparency for economic operations including micro, small and medium-sized enterprises. Take account specific needs of them.
Recital 14: The protection afforded by this Regulation should apply to natural persons
Recital 15: Technology Neutrality: the protection of natural person should be technologically neutral. Protection through automated means or manual processing.
Recital 24: Applicable to Controllers/Processors Not Established in the Union if Data Subjects Within the Union are Profiled. Proves should be established if natural person are tracked on the internet for analyzing or predicting personal preferences, behaviors and attitudes.
Recital 25: Applicable to Controllers Due to International Law.比如领事馆, where an EU MS’s laws apply outside the EU
Recital 38: Special Protection of Children’s Personal Data: in activities such as marketing or creating personality or user profiles, and child direct services.
ACL 4: Definitions
Data Subject:
an identified or identifiable natural person who can be identified directly or indirectly. They have specific rights under EU DP law who are not limited to EU residents or citizens but any ‘subject’ of personal data within scope of EU DP Law. Identifiable means all ways in which the data could be reasonably be used.
Personal Data:
any information relating to a data subject, the information is unlimited in nature including name, an identification number, location data, an online identifier, which are physical, physiological, genetic, mental, economic, cultural or social identity.
Personal data can be protected via obligations on controllers by compliance with data principles, rights accorded to data subjects including access, correction, deletion or redress, and subject to enforcement by member states and overseen by EU regulator.
Sensitive Data:
Recital 51: Protecting Sensitive Personal Date: personal data revealing racial or ethnic origin and biometric data.
These data are with enhanced obligations and narrower exceptions because processing presents greater risk of harm to data subject because of its nature, which includes(Acl 9):


ACL 9 also gives exceptions on sensitive data protection if there’s explicit consent[JX1] unless MS/EU law does not allow consent, and the exceptions are narrow.
Processing:
any operation or set of operations, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction;
processing exceptions: ART 2 Material Scope:
Activities which fall outside scope of EU law;
Prevention/detection/prosecution/punishment of crimes;
Recital 16: Processing for reasons of national security;
and follows the common foreign and security policy of the Union;
Recital 18: purely personal or household activity like correspondence and the holding of addresses, or social networking and online activity but GDPR still applies to controllers or processors which provide the means for processing personal data for such personal or household activities;
Recital 27: Not Applicable to Data of Deceased Persons, MS should create and apply their own rules;
ART 11: no processing on identification-free data, or to say fully anonymized data;[JX2]
Statistical / historic /scientific research.
Controller:
natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data, which are determined by EU/MS law.
ART 3: Territorial scope:
controller established in the EU regardless of the data processing place;
controller not in the EU but offering of goods or services to data subjects based in EU or monitoring subjects behavior within EU;
the place not in the EU but MA law appliers.
Obligations of Controllers:
Not to collect or process personal data unless legitimate basis;
Compliance with processing principles;
Ensure confidentiality and security of personal data: Use of “appropriate technical and organizational measures”, privacy by design, notification of any breach;
Keep adequate records of processing;
Not transfer data to 3rd country unless ‘adequate’ protection;
Co-operation with supervisory authority including breach notification;
Conduct Impact Assessments where necessary;
Follow approved relevant industry codes of conduct where applicable.
Data Processor
One who processes data on behalf of the controller, according to the instructions of a controller.
Processors must meet EU Law’s security requirements, must have contract with controller, Must process according to controller’s instructions.
Controller is responsible for compliance, sometimes both processer and controller should comply if data are used further beyond controller’s instructions.
Legitimate Basis for Data Processing:
Consent-ART 4: any freely given, specific, informed and unambiguous indication of the data subject’s wishes by which he or she, by a statement or by a clear affirmative action, signifies agreement to the processing of personal data relating to him or her.
Recital 32: Conditions for consent: Consent such as by a written statement, including by electronic means, or an oral statement, could include ticking a box when visiting an internet website, choosing technical settings for information society services or another statement or conduct which clearly indicates in this context the data subject’s acceptance. Silence, pre-ticked boxes or inactivity should not therefore constitute consent.(opt-out is insufficient). If the data subject’s consent is to be given following a request by electronic means, the request must be clear, concise and not unnecessarily disruptive to the use of the service for which it is provided.(correlation with fair)
Necessary-ART 6: to comply with obligation to which the controller is subject or for the performance of a contract related to data subject; To protect vital interests of data subject; for the performance of a task carried out in the public interest or in the exercise of official authority vested in the controller; To protect legitimate interests of controller or 3rd party to whom data disclosed unless fundamental rights override.
For processing of sensitive data, explicit consent is required and never implied consent.
Necessary to more limited circumstances when:
Carry out obligations and specific rights of the controller authorized under national employment law that provides for adequate safeguards;
Protect the vital interests of the data subject or another person where data subject legally or physically incapable of giving consent like data subject is experiencing very serious health or safety threats;
Legitimate activities by a foundation, association or any other non-profit-seeking body with a political, philosophical, religious or trade union aim and with sufficient protections;
To the establishment, exercise or defense of a legal claim.
GDPR ART 21: Data subjects Rights to object to process personal data where:
Processing in the public interest or exercise of lawful authority;
Necessary for the purposes of legitimate interests of a third party;
Controller can only continue to process where can demonstrate an overriding case (test of proportionality).
Data subject to be informed of this right “at the latest” at time of firm communication with data subject.
Consent: Children
ART 8: In relation to the offer of information society services directly to a child the processing of the personal data of a child shall be lawful where the child is at least 16 years old, child below the age of 16 years, consent should be given or authorized by the holder of parental responsibility over the child, MS could minus the age but not under 13.
not affect the general contract law of Member States such as the rules on the validity, formation or effect of a contract in relation to a child.
Compliance with Principles
ART 5: Principle relating to processing of personal data:
(‘lawfulness, fairness and transparency’):processed lawfully, fairly and in a transparent manner in relation to the data subject
Lawfully: corresponds to legitimate processing and consent should be natural, which means ‘freely given, specific and informed’, clear ‘opt in’ and explicit with no ambiguous.
Lawfully Processed: for processing obligation for sensitive data, they could only on explicit consent or more compelling alternative grounds like matter of life and death; provide the data subject prior to that further processing with information on that other purpose and other necessary information; where the personal data are obtained from another source, within a reasonable period; unless data subject already has this information.

(‘accountability’);The controller shall be responsible for, and be able to demonstrate compliance
(‘purpose limitation’)collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall, in accordance with Article 89(1), not be considered to be incompatible with the initial purposes;
Processing without consent: safeguards: controllers must take into account:

Further Data Subject Rights
ACL 15: rights of access, ACL 16: rights to rectification, ACL 17: to be forgotten, ACL 18: rights to restriction of processing, ACL 19: Notification obligation regarding rectification or erasure of personal data or restriction of processing, ACL 20: Right to data portability(receive and transmit), ACL 21&22: automated decision making, ACL 23: Restrictions on these rights.
(‘storage limitation’)

Other duties: supervisory authority under GDPR:

Data Transfer
Within EU: subject to GDPR
Outside EU:

5.26
13.1 Transfer of Data Outside the EU
Background:
1.Data transfer within EU:
EU has very high standards of Data Protection, there are limits on controllers and processers in collection and use of data, transfer of information to other parties within EU so that security is established. Also, there are rights for data subjects who can access, correct and delete their personal data for proper reasons.
2. Data transfer outside EU:
In increasingly international commerce, transfers of huge quantities of PD covers from customers to employees, and between and among units of the same corporate enterprises located in different countries such as several MNCs headquartered in the US, make multiple transfers as well. This represent a globalization trend of trade that overseas’ PD processing is a good way of balancing cost and efficiency.
For data transfer outside EU, adequate protection of PD is required:
1) GDPR ART 45: before transfer PD to a third party, the EU commission has ensures they have adequate level of protection, in that case no specific authorization for transfer required.
Or 2) ART 46: an alternative rule to adequacy is the controller or the processer must provide appropriate safeguards, and on condition that enforceable data subject rights and effective legal remedies for data subjects are available.
Derogation of adequate protection: ART 49:
1) Data subjects have explicitly consent data transfer as long as he/sha has been informed possible risks in the condition that there’s no appropriate safeguards or adequate protection
Or 2) The transfer is necessary or legally required on important public interest grounds, or for establishment, exercise or defense of legal claims, or to protect the vital interests the data subjects, or the transfer is made from a register who is intended to provide information to the public, available to general public or any person who can demonstrate a legitimate interest, or for the performance of contract between the controller and data subject.
All of the above, the necessity criteria is applied strictly.
13.2 Compliance with Adequacy Requirement
General Adequacy Criteria: Making sure that EU citizens PD have same protection outside EU:
Commission adequacy decisions should be reviewed periodically.
Factors to consider for the Commission:

And supervisory authorities who can ensure protections are enforced; third country committed any legal binding international rules on protecting PD; nature of the data especially sensitive data and the risk extend of data transfer.
For data controller: consider the purposes of data transfer and be accountable for actions of processors in third countries.
For data exporters: they should ensure that processing time in the third country is kept to a minimum and data is deleted by the data importer as soon as it is no longer required for the intended purpose.
Counties whose national laws have adequate protection are limited.
For other areas, alternative means are needed, such as derogations, other more ideal ways are for regular business, namely appropriate safeguards:
>appropriate safeguards do not require approval by supervisory authority:
Legally binding and enforceable instruments between public bodies / authorities (Treaties):
 ,
,
Binding Corporate Rules (GDPR ART47: four roles: controllers, processors, data subjects and supervisory authorities):
This is to facilitate Transborder Data Flow(TBDF) within particular corporate groups. GDPR A47 states that Code of Conduct drafted by enterprises should contain privacy policy, covering each entity included in the enterprise subscribes, and this could enables data subjects to enforce code against the enterprise. Supervisory Authorities/National DPAs are to ensure consistency of pre-GDPR approvals and post ones.
European Commission’s standard contractual clauses,
Standard Contractual Clauses adopted by national DPA(Data Processing Arrangement) and approved by Commission:
SCCs comes from EU Commission or National DPA. Business can use these standard clauses without approval or come up with their own and seek Commission/DPA approval.
Three sets of adopted SCCs by EU categorized into two kinds: EU controller to non-EU or EEA controller, and EU controller to non-EU or EEA processor which was revised in 2010, allowing the outsourcing processing activities by the data processors to other sub-processors.
Approved Code of Conduct (A40):
Codes not themselves binding law though help to obey the law, and code can provide appropriate safeguards on binding contract on thrid parties. Accredited body can give day to day monitoring of approved codes.
Approved certification mechanism (A42):
 .
.
>appropriate safeguards require approval by supervisory authority:
Contractual arrangements between parties in EU (Controller or Processor) and party in third country(controller/processor/recipient) or international organization,
Provisions(条款) inserted in administrative arrangements between public authorities or bodies which include enforceable and effective data subject rights.
EU-US established Privacy Shield from 2016 to 2020, after limited success of EU0US Safe Harbor Agreement 2000-2015.
Privacy Shield Principles include notice, choice, accountability for Onward Transfers, Security, Data Integrity and Purpose Limitation, Access, Recourse( the egal right to demand compensation or payment)/Enforcement/ and Liability.
Key implications of the Privacy Shield:

But for the US cloud service, Standard Contractual Clauses are not enough. So here’s third attempt:

14-15: Privacy and Online Data Collection
Online Service Providers: Internet Service Providers(ISPs):
deal with Internet Access only, provide personal data and log the date, time, duration, IP address, and other personal data.
ISPs provide services to individuals and companies on the web. They own or hire a permanent TCP/IP connection, use servers permanently connected to the Internet. And those servers equipped with protocols which gather personal data. Some of the http servers create logbooks and logfiles systematically, may containing all or some data present in the http request header and the IP address, which are not always defined as PD.
ISPs collect PD from users/customers through contract implementation, registration, or service usage when they sell or advertise their goods or services online.
Third parties: get to know existing users of ISPs by IP addresses, cookies or data mining.
Collection of information online:
Visible collection which has users’ explicit consent, Invisible collection which often have users’ implied consent.
Privacy risks raised by invisible collection:
TCP/IP: route, DNS Server, Ping command:

HTTP, invisible hyperlinks: browser chattering: besides IP address/name, other information is also transmitted, which includes OS version, software version, users’ language and geographical location.
Cookies:
Set cookies are placed in invisible hyperlinks, where cybermarketing companies could know all the key words user searched and other surfing information. Furthermore, collected raw data can linked to more new and more private data. Set cookies can be deleted by setting browsers.
Flash cookies collect information on how the user navigate those websites.
Traffic data:
Can be used to picture a user by identifying via communication transmissions, such as e-mail, mobile phone calls.
Clickstream data: clickstream is route that a visitor chooses when clicking or navigating through a site.
Online Services: users provide data to online retailers, in charge of using free services or cloud computes, when using some platforms, and AI used to scrape data on social media. With customers’ consent, online services use them for commercial purposes, while most of the consents are implied cause privacy policies are lengthy and non-negotiable.
Online Profiling:
By combine visible and invisible collection of PD online, online profiling is useful for direct marketing and targeted sales activities.
Direct marketing:
Direct marketing companies and common websites both perform direct marketing. The latter put invisible hyperlinks to make connections with cybermarketing companies, after which all data are collected, advertisements are targeted, pools of personal data are created for the convenience of third party access.
Possible protections are anonymization where personal data is collected but identity is disguised, or pseudonymization which identities are often traceable.
However, by using data analysis, data mining and other techniques, anonymized data may targeted to an individual at which point they become personal data.
Furthermore, by pay for the information, companies do not need to track identities, whose actions are predatory or manipulative marketing(targeted advertising) and are not restricted by DPLs.
Impact of Search Engines
Identify users, collect and store search behaviors. However, personal data can be retraced from anonymized data.
Working as aggregators, search engines help content providers publicly known across the world. However, cache can retrieving and grouping all the information of a data subject to create a new picture of him or her.
Privacy & Online Data Collection:
Privacy in eCommunications:
ePrivacy Directive:
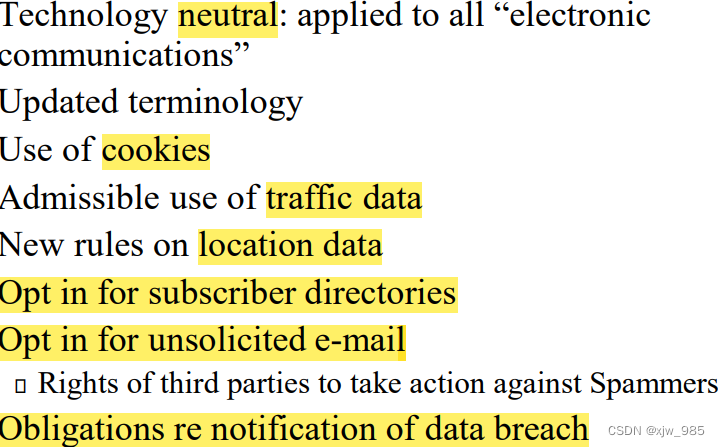
Rules for cookies from 2011:
‘notice and opt in”, user given his or her consent after having been provided with clear and comprehensive information.

Spyware etc: inform users invisible tracking devices and their purpose.
Traffic data: restrictions on retention of data and erasing or anonymized them once data reservation period is met.
Direct marketing & Spam Email
Spam is unsolicited e-mails.
Definition of emails.
According to ePrivacy Directive, unsolicited e-mails are prohibited unless opts-in or prior consent is given. Consent is freely given, specific and informed indication of wishes by any appropriate method in GDPR. GDPR also states that consent must includes asking, purposes, obtained from applicable place, data controller identity provided. Implied consent is not allowed.
Prior consent means opt in, it’s purposes to be specified, it’s consent to pass on the PI to third parties to be asked where applicable, and at time of collection those information could identify data controllers. GDPR adds that data subject has the right to object data processing for marketing purpose at any time.
However, there are limited exceptions that merchants can use email addresses if they are collected in the course of a sale to market similar products/services to those customers. While customers can also opy-out.(soft opt-out).
Direct Marketing: Any form of sales promotion, including fund raising by charities and political organizations.
Email Harvesting: Automatic collection of PI on public internet places is unlawful. GDPR ART22 says that data subjects has the right to reject solely automated processing which produces legal effects, while certain exemptions can be added by nations.
Electronic Direct Marketing:
UK Information Commission guidelines are of ittle help to bulk spam sent outside of UK/EU. Users need to speak to ISPs or use SPAM filters. While, within EU, one could talk to the emailer and let UK ICO investigating and asking SPAM to stop.
Regulations of Search Engines.
EU Working Party notes that unless absolute certainty that the users’ data is not identifiable, ISPs must treat all IP information as PD protect them.
Search engines situated outside the EU:
For Working Party Opinion, EU DP law should also be applied on them, and they are those search engines which use data centers in EU ot equipment based in EU.
For GDPR ART3: GDPR protects data subject in the EU whose search engines process activities offered relate to good or services, or monitor behavior (keyword-based advertising?) where that takes place in the EU (keyword-based advertising?) where that takes place in the EU (using computer to access web from the EU?).
IP Address
Is IP address personal data? Identifiability should be tested.

Other general rules:
Processing of IP Addresses: GDPR ART10: data processing relating to criminal convictions and offences should be carried out under the control of official authority…, ART 6: processing is necessary where legitimate interests of a third party.
The right to be forgotten
Data Portability

1. Introduction
Cybersecurity includes three main elements, information security, privacy and data protection, and cybercrime.
Information Security protects information assets both in hard copy and digital form.
We use data protections to enforce data privacy.
Information privacy is individual rights to control the use and disclosure of their own personal information, which is processed by information security.
Cybercrime use information and communication technology to target to some system and facilitate a crime. It carries characters such as no physical or geographic boundaries, conduct with less effort, greater ease, and at greater speed and scale than traditional crime.
Cybersecurity Law: Information security obligations, privacy and data protection laws, cybercrime substantive and procedural laws.
There are technical challenges such as growing number of devices, software vulnerabilities, and virtualized information technology infrastructure; legal challenges such as increasing number, scope and complexity of legal obligations, and different legal systems between countries.
The trend is advent of new technologies, new cyber attacks.
Drivers of cybersecurity is legal, regulatory and commercial.
Information Security:
We need processes, procedures and infrastructure to preserve confidentiality, integrity, and availability(CIA) of information.
Confidentiality means only people with the right permission can access and use information. We can use encryption and access controls to ensure confidentiality. Sometimes we need to compromise confidentiality but this may result in bad effects.
Integrity means information systems and their data are accurate, no data change is allowed without appropriate permission.
Authentication is specific to integrity and confidentiality considerations, ensuring that a machine(digital signature) or person is which they purport to be, like creator/sender/signature of record, or person who seeks access to it.
Availability is to ensure the information system is reliable: data is accessible, permitted individuals use system dependently, have recovery plans and backup systems.
2. Information Security Key concept
Vulnerabilities are weakness or flaw in the information system that can be exploited. They are generated in construction or design mistake, or by flaws of internal safeguards, or no safeguards. We need to avoid flaws in four categories:
People, whose duties are separated into two or more parts especially on the critical task functions;
process, where flaws of organization procedures occur. Steps could be missed in a checklist or there’s no checklist, and appliance of hardware and software patches could fail;
Facility flaws in physical infrastructure like in fences, locks, or CCTV cameras;
And technology design flaws, which includes unpatched applications, improperly configured equipment.
An example of vulnerability is that a company do not have sufficient controls to protect an employee from deleting critical files.
Threats is successful exploits of vulnerabilities, such as the action of deleting critical files. The source of threats comes from:
Human, either internal or external, meaning well-meaning employees and external attackers;
Natural uncontrollable events like fire and floods;
Technological and operational threats that operate inside information systems, such as malicious code, hardware and software failures;
Physical and environmental threats due to lack of physical security which are either accidental or intentional, come from internal or external attackers.
Trends of threads in the recent decade are the number of threats to information, networks, systems have increased, due to more devices and greater attack surface complex networks, and more device with IoT. All these trends make end points of corporate networks no longer in enterprise control and more smart devices are not in authentication systems. Another trend is attacks have grown more sophisticated, meaning there are longer preparation periods and more of them are undetected like ransomware.
Influences of threats can be the compromise of availability.
Risks are likelihoods that a threat will exploit a vulnerability and cause harm, where the harm is the impact to organization. In this case, risk is vulnerability plus threat.
Risks can occur at:
Physical hardware or device layer; software layer; network layer; and user layer.
Risk management is used to justify information security laws, it’s the process of listing the risks that an organization faces and taking steps to control them.
Risk analysis and management to classify and respond to risks. We need to classify the probability that a threat will exploit a vulnerability as high, medium, or low. We also need to identify the impact, which includes information security impact in the loss confidentiality, integrity and availability, and other impacts such as loss of life, productivity or profit, property and reputation. Subsequently, we need to assess impact and then address risks that have large impact on information security.
Types of responses listed as risk avoidance, risk mitigation, risk transfer, and risk acceptance.
Safeguards is to reduce the harm posed by information security vulnerabilities or threats. There are three kinds of safeguards:
Administrative, which are actions and rules implemented to protect information;
Technical safeguards by using logical rules that state how systems will operate, forming as least privilege rule;
Physical safeguards which take actions to protect actual physical resources.
Safeguards can be put in place at all layers of the system:

There’s no single definition of information security and thus no single information security law. However, liability have established by different potential sources, including statutes, regulations, contracts, organizational governance, voluntary organizations, and private law tort.
Moreover, different kinds of information often sought to be protected, which includes personal data defined under data protection laws, corporate financial information, health information, and credit card information.
We need to meet the legal requirements so that there’s reasonable, appropriate, and adequate security.
Sources of obligations are laws, rules, regulations, and standards:
Laws:
Common law is body of law that developed through legal tradition and court cases, which has impact on tort, contract, and property laws:
A tort, in common law jurisdictions, is a civil wrong that unfairly causes someone else to suffer loss or harm resulting in legal liability for the person who commits the tortious act. When establishing a tort prosecution, one need to figure out the plaintiff’s duty, prove a duty breach, classify the causation, and find out harm elements.
A contract is an agreement, giving rise to obligations, which are enforced or recognized by law.
Statutory laws are laws adopted by the governments and often address broader issues, such as privacy and telecommunications security.:

Statutory laws (e.g. US Sarbanes Oxley Act) also ensures corporate financial reporting integrity and transparency by enforcing Financial transparency and securities market reporting and audit obligations to ensure continuing provision of government services.
Statutory laws are applicable in other areas such as consumer protection, and electronic records retention.
Governments delegate power to agencies to create rules, enforce rules, and review rules.
Regulations:
Regulatory authorities have the power to create and enforce regulations.
Sector regulators are increasingly auditing companies for their information security management and also issuing ‘regulatory guidance’ or ‘best practice advisories’ on information security.
These legal obligations specify a duty as providing adequate or reasonable or appropriate security but no specific guidance. The general guidance in GDPR is ‘ensure a level of security appropriate to the risks represented by the processing and the nature of the data to be protected, which requires cost/risk analysis to qualify an appropriate level of security.
While emerging guidance is in form of ‘standards’ which determine how to comply with a legal duty or self-imposed obligation for adequate/reasonable/appropriate information security, by standards bodies or international organizations.
Standards and Interoperability (cellular technology standards)/ Accessibility( disabled people accessibility)/ Law ( a way for entities to show their reasonable care)
3. EU Obligations
Cyber includes any device that has the ability to communicate. Cybersecurity refers to the systems, contracts and policies we put in place to manage risk with regards to Cyberspace.
Cyber threats are anywhere and everywhere:


And the impact of cyber threats are of various kinds and extends.
For EU, there are directives and regulations for information security for different areas:
EU General Data Protection Regulation (GDPR) for privacy:










EU Electronic Communications Privacy Directives (ePrivacy Directive) for electronic communications services/ networks:
Network and Information Systems Directive (NIS Directive) for critical infrastructure:
NIS addresses risks to critical national infrastructure (CNI) from under-investment in cybersecurity and insufficient information-sharing.
CNI providers include operators of essential services (OES) which are directly responsible for CNI, and digital service providers(DSPs) which provide services upon which others are reliant.(OES rely on DSP)
NIS scope: OES sectors: energy, transport, banking, financial markets, health, drinking water, and digital infrastructure. OES operate on such a scale that they are essential for the maintenance of critical societal and economic activities.
Digital service is a subset of information society services which is any service provided for remuneration at a distance by electronic means and at the individual request of a recipient of services.
DSPs are: online marketplace, online search engine, or cloud computing services.
NIS has the same information security obligation as GDPR which are safeguarding obligations and information obligations, and the respective obligations of them are also similar.




4. Information Security-US Obligations
Statues: (for different purposes)
A sectoral law approach for privacy and data protection:
1) HIPPA: US Health Insurance Portability and Accountability Act (health information privacy):
a) Scope: Apply to covered entities and determine how they may create, store, use or disclose protected health information (PHI). HIPPA applies information security principles established in other industries.
Covered entities are those that handle PHI in a certain way, which include health plans, health care providers, health insurance companies, etc.
HIPPA also applies to business associates of covered entities.
PHI is any individually identifiable information about the health of the person, including past, present or future mental or physical health information.
b) Security Rules:
Covered Entity must implement policies and procedures to prevent, detect, contain and correct security violations, which means using security safeguards that protect CIA of electronic PHI(EPHI) from reasonably anticipated threats.
c) Security Rules Standards:
Security rules contain instructions on the way to use information security safeguards and standards to be met.
d) Implementation Specifications(IS):
This is detailed instructions for meeting the standards.
There are required specifications which is compulsory, and addressable specifications which need covered entities to decide whether it is reasonable and appropriate to the particular environment and the cost to implement these specifications.
Covered entities can either implement IS as published, Implement some alternative (and document why), and Not implement the IS at all (and document why).
e) Safeguards:

2) COPPA: Children's Online Privacy Protection Rule:
This is sectoral approach which derived partly from federal statute, but also from state law, case law and increasingly from the decisions and guidance of the Federal Trade Commission (FTC)
a) Scope:

3) CCPA: California Consumer Privacy Act
a) Scope:
CCPA came into effect in January 2020, which is the most comprehensive privacy legislation to-date.
CCPA applies to any business that collects or processes Personal Identifiable Information(PII) from California residents, and that captures most apps or free-to-play games.
PII includes any information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household (under the CCPA).
Telecommunications security: US Telecommunication security Act
Breach notification laws:
47 states require private or governmental entities to notify consumers when personal information may have been compromised, lost, or stolen.
a) subjects who must comply with the law (businesses, data/ information brokers, government entities);
b) definitions of ‘personal information’ (name combined with SSN, drivers license or state ID, account numbers);
c) what constitutes a breach (unauthorized acquisition of data);
d) requirements for notice (timing or method of notice, who must be notified)
Corporate Governance Laws: US Sarbanes Oxley Act (SOX)
Consumer protection Regulations: Federal Trade Commission Act(FTC)
State consumer protection laws create fiduciary duties that are breached when data is lost or stolen.
FTC forbids unfair and deceptive trade practices in Section 5.
a) Scope:
Unfair means causes or likely to cause substantial harm/injury to consumer, consumer cannot reasonably avoid the harm, or there’s not a benefit to the practice that outweighs the harm.
Deceptive means representation or omission likely to mislead the consumer, not reasonable from the perspective of the consumer, or affects consumer’s decision, harm, or likely another decision.
b) New approach to cybersecurity in FTC enforces a reasonableness standard at a minimum.
c) Priorities:

d) Limitations:
FTC didn’t create a robust cybersecurity framework or an agency empowered to enforce it. For the time being, it fills the void in USA cybersecurity ecosystem.
Electronic records retention obligations:
US Federal Rules of Evidence 901(a)
Tort Law
Information security lawsuits commonly claim for negligence, breach of fiduciary duty or breach of contract individually or together.
1) Negligence is generally defined as a breach of the duty not to impose an unreasonable risk on society. To establish the claim, plaintiff must prove:

a) Foreseeability:
A person can be held liable only when they should reasonably have foreseen that their negligence act would imperil others.
2) Special Relationships:

To establish the claim, plaintiff must prove:

3) Statues: Fair Credit Reporting Act
Impose a duty of care for how entities use or limit access to personal information in the normal course of business, otherwise civil liability may exists.
4) Harm
For actual harm case, there are Concrete and particularized injury that is actual or imminent, not conjectural or hypothetical.
For data breach case, we could find future harm that establishes a threat of future identity theft.
Contract Law


Conclusions:

5.
I) Information Security Obligation in China
PRC Cybersecurity Law 2017 is the first national-level law to address cybersecurity and data privacy protection.
1) Privacy Law
Decision has the same legal effect as law, while Guidelines and PIS Specifications are references to best practice.
a) The Decision on Strengthening Online Information Protection 2012
This is to protect online information security, safeguard the lawful rights and interests of citizens, legal entities or other organizations, and ensure national security and public interests.
b) National Standard of Information Security Technology – Guideline for Personal Information Protection within Information System for Public and Commercial Services 2013
c) PRC Cybersecurity Law
Provides supervisory jurisdiction over cyberspace, defines security obligations for network operators, and enhances the protection over personal information.
It also establishes a regulatory regime in respect of critical information infrastructure and imposes data localization requirements for certain industries.:
Operators of Critical Information Infrastructure:
Network operators must adopt technological measures and other necessary measures to ensure the security of personal information they gather, and prevent personal information from being leaked, destroyed or lost:

Data localization:
Drafted Personal Information Protection Law requires that PI that have reached or exceeded the PI processing threshold shall e stored inside China or undergo risk assessments when cross-border data transfer is required.
d) National Standard of Information Security Technology – Personal Information Security Specification (PIS Specification) 2018:
A standard to determine whether companies are following their legal obligations, to assist organizations in complying with the data protection obligations imposed under the PRC Cybersecurity Law.
Businesses that collect or process personal information in China should check their current practices against this Specification to identify and minimize their potential risks.
They should check the definition of personal and sensitive information, data controller, data collection, data retention, use of data, third-Party Processors sharing and transferring data, and data breach incidents.
e) Cybersecurity multi-level protection system 2.0 (three National Standards) 2019
f) PRC Civil Code 2021:

Civil Code stipulates that the rights pertaining to PI are personal rights of the personal information subjects.
But the ownership of PI is disputed.
2) Telecommunications/ ISPs law: The Provisions on Telecommunication and Internet User Personal Information Protection 2013
Telecommunications and Internet service providers have duty to keep information in proper custody, mitigate harms from actual or suspected disclosure, and have breach (actual or suspected) notification obligation.

3) Breach notification law
PRC Cybersecurity Law:
Where personal information is leaked, lost or distorted (or if there is a potential for such incidents), organizations must promptly take relevant measures to mitigate any damage and notify relevant data subjects and report to relevant government agencies in a timely manner in accordance with relevant provisions.
4) Consumer protection law: The PRC Consumer Rights Protection Law:
Data protection obligations to all types of businesses:

5) E-commerce law
Aims to gain greater control over the online consumer markets.

6) Private and tort law

II) Information Security Standards:
1) Sources
2) Scope of Obligations: duty to provide adequate or reasonable or appropriate security
3) Issue: the duties are not further specified in the statues, and there’s no specific guidance on how to implement, only GDPR states that “give reasonable appropriate security after cost/risk analysis”.
4) Emerging Guidance:
GDPR: requires an “adequate” level of data protection
HIPPA Security Rule for healthcare, and Safeguards Rule for financial services
Federal Trade Commission(FTC): considers the collection of personal information without providing reasonable security to be an unfair practice.
5) Standards
Frameworks include International Organization for Standardization (ISO) 27001, Payment Card Industry Data Security Standard (PCI DSS), and National Institute of Standards and Technology (NIST).
a) Definition of ISO
a standard is a document, established by consensus and approved by a recognized body, that provides, for common and repeated use, rules, guidelines or characteristics for activities or their results, aimed at the achievement of the optimum degree of order in a given context.
b) Types
Informal/formal, achieved dominant position/ standard contractual terms, social, technical, commercial
c) Benefits
joint and complete control of problems, reduces uncertainties and no need to test further, makes operations smoother, advances progress where there’s anticipated further developments, avoid conflicts.
d) Conformity with Standards:
Through certification process which is audited by third parties. Mark of conformity means quality certification and market entry permission.
f) National Standards Bodies
National Standards of Health and Safety industries are compulsory.
g) International Standards Bodies
non-treaty bodies: ISO, International Electrotechnical Commission (IEC):
treaty bodies: International Telecommunication Union (ITU)
6) OECD 2002 Information Security Guidelines
Guidelines = non-binding, represents political will of members, great ‘moral force’.
OECD 2002 has standards setting role
7) De Jure Standards
They are legal requirement for appropriate level of information security process:
a) HIPPA:

b) PCI/DSS (The Payment Card Industry Data Security Standards)


6.1 Criminal Law and Basic Principles
Criminal law can be so damaged to society that loss of liberty or life is possible.
Two types of criminal laws: substantive offences(PRC Criminal Law), and Procedure Rules(PRC Criminal Procedure Law). They are to define and deter criminal acts and ensure a fair and just trial.
Substantive Offences are laws that create and define socially acceptable conduct, and crimes and punishments. There are general provisions and specific provisions.
Procedure Rules are laws that govern the investigation, arrest, and trial of the accused. They can protect the constitutional rights of the accused.
General Principles:
1)no punishment without the law;
2)Innocent until proven guilty; guilty has to be proved beyond reasonable doubt, If there is reasonable doubt, the person charged of the offence must be acquitted;
3)Guilty to be proven beyond reasonable doubt: (ARL 46 PRC CL) the defendant may be found guilty and sentenced to a criminal punishment if evidence is sufficient and reliable;
4)and an act cannot be made a crime retroactively which means an act must be a crime at the time it is committed.
5)Burden of proof: one should state prosecutes, to prove guilt beyond reasonable doubt and defendant rarely has to establish their innocence.
6)Right to remain silent: In many counties, the accused has the right to remain silent about the details of the crime with which charged, while China accused has no right to remain silent, but cannot be convicted on confession alone.
7)Double jeopardy
8)Limitations: If offence is ‘minor’ there is no prosecution; Usually, time period for prosecuting offences, outside time period, crime cannot be prosecuted.
9) Parties to a crime:
Principal or joint principal, secondary participants (adding and abetting)/inciting
10) An inchoate crime is a crime that might not be completed. Inchoate crime is also punishable.
Inchoate Offences implemented by:
a) incitement (the defendant must have tried to persuade another to commit a crime);
b) conspiracy (at least two defendants must have agreed to commit a crime)
c) attempt:
The defendant must have tried to commit the offence and have got relatively close to achieving this objective.
Article 22 Preparation for a crime refers to the preparation of the instruments or the creation of the conditions for a crime.
ART 23 PRC CL: A criminal attempt refers to a case where an offender has already started to commit a crime but is prevented from completing it for reasons independent of his will.
11) Defenses
Insanity, automatism, mistake, intoxication, duress by threat, acting in self-defense, “entrapment”.
Elements of a Crime: a voluntary act or omission Actus Reus + a certain state of mind Mens Rea
1)Actus Reus (guilty act): prohibited conduct either requiring course of conduct (act or omission) (such as rape), or consequences or results (such as death in ‘murder’, injury, damage to property).
2)Mens Rea (guilty mind): Some offences require a specific intention to cause the result or a result close to one that occurs.
State of mind: intention/ knowledge/will; recklessness/ negligence
Criminal Intents: purposely/intentionally->knowingly->recklessly->negligently.
a) Knowledge
can be inferred from both act and surrounding circumstances. Circumstantial evidence may be allowed. Post-crime conduct may be recognized if demonstrates consciousness of guilt.
b) Intention
Direct: Consequence is desired, accused decides to bring it about or tries his best to
Oblique: Accused sees the consequence as certain or virtually certain
c) Negligence
Falling below the standard of the ordinary reasonable man, doing something he would do or doing something he would not do. We can use objective test(Objective tests are questions whose answers are either correct or incorrect. They tend to be better at testing 'low order' thinking skills, such as memory, basic comprehension and perhaps application (of numerical procedures for example) and are often (though not necessarily always) best used for diagnostic assessment) to determine whether or not him or her is hypothetical reasonable person.
d) Strict Liability
an offence which law states requires no mens rea.
Some offences are classed as strict liability because it would be near impossible to prove mens rea in some offences and without it, people would easily escape conviction.
For other offences, the consequences of particular acts or omissions are considered to be so serious that criminal sanctions must be imposed as a matter of social policy.
3) Coincidence of actus reus and mens rea
A criminal offence requires both the actus reus and the mens rea to occur (except strict liability) at the same time or very closely to each other for criminal liability to be established
Motivation

Evidence of a defendant’s motive may be introduced at trial to convince a judge that she is guilty, but motive is not perceived as a legal component of guilt.
6.2 Cybercrime Law
I)PRC Criminal Law
Article 2 The aim of the Criminal Law of the People's Republic of China is to use criminal punishments to fight against all criminal acts in order to safeguard security of the State.
ART 13 Criminal act/Crime is any act endangering society and subject to punishment. Additionally, where circumstances are ‘minor’ and harm is not ‘serious’: the act is not a criminal act but an ‘unlawful’ act. However, if the act is serious or especially serious, there can be fixed-term sentences.
ART 3 No crime without the law.
The PRC's legislature, the National People's Congress (NPC), or its Standing Committee determines the threshold separating a criminal act from an unlawful act by specifying the extent of seriousness of the consequences and circumstances to which an act warrants a criminal penalty. Threshold can be determined by a trigger amount.
Minor offenses and administrative penalties: The police punish minor offenses that are not regarded as having breached the criminal law. Those punishments are referred to as administrative because the police make the decisions.
Prosecution of a crime: complaint -> investigation by the police-> court trial between prosecutors and defense lawyers.
The police is the most powerful institution in China's criminal process: who have wide power to investigate and is in charge of evidence gathering.
The procuracy(检察院):
performs multiple functions as an investigative, prosecutorial, supervisory, and judicial body.
Institutes public prosecution against all crimes in court.
After the investigators conclude their investigations, they transfer the case to the procuracy for public prosecution.

Court Trial
Prosecution provides a Bill of Prosecution and a list of evidence to be produced in court.
The court will decide to try the case if there is prima facie(at first sight) evidence of criminal wrongdoing.
Prosecution bears the burden of proof
Defense can cross-examine(to ask detailed questions about sb.) the prosecution evidence and produce its own evidence to challenge the allegation. They are making strong arguments on behalf of the accused.
Judges
Judges are neutral and passive arbitrators, evaluating evidence and arguments presented before the court. Judges are possible to make ‘not-guilty’ verdicts.
The principle of territoriality
ART 6: … anyone who commits a crime within the territory…; … who commits a crime on board a ship or aircraft of PRC …; … a crime act or its consequence takes place within the territory of PRC …
ART 7: Chinese citizens committing a crime abroad is punished more than 3Y, may be tried in China the periods can be shorter.
ART 8: Foreigner committing a crime abroad against a Chinese citizen, PRC CL may apply.
Computer Crime provisions
ART 285-287
II) PRC Constitution: Safeguards
ART 37: Freedom of the person of citizens of the People's Republic of China is inviolable. No citizen may be arrested except with the approval or by decision of a people's procuratorate or by decision of a people's court, and arrests must be made by a public security organ. Unlawful detention or deprivation or restriction of citizens' freedom of the person by other means is prohibited, and unlawful search of the person of citizens is prohibited.
III) PRC Criminal Procedure Law
The procedural law governs the investigation and trial of a case
The purpose of this law is to ensure that PRC CL is correctly applied, innocent people are protected from criminal prosecution, safeguards citizens’ personal/ property/democratic rights.
It provides rules for arrest, evidence, jurisdiction, confiscating illegal gains, and sentencing.
7. Introduce to Cybercrime
I) Definition
Cybercrime is an act that violates the law, which is perpetrated using information and communication technology.
Other definition:
Any activity in which computers or computer networks are a tool, a target or a place of criminal activity.
Different from traditional crime, cybercrime knows no physical or geographic boundaries and can be conducted with less effort, greater ease, and at greater speed.
II) Characteristics
Easy to learn how to commit, require few resources, can be committed without being physically present, not clearly illegal. Plus, cybercrime can be global, while investigation and prosecution is territorial along territories and by jurisdictions.
III) Classification
1) Computers as the target of the offence
And the consequence is the compromise of confidence, integrity, and availability of data, applications, and networks.
Typical crimes: hacking, cracking, malicious code, vandalism(website defacement), and denial of service and DDoS attacks.
2) Computers as tools
Which means ICT (information communication technology) is part of the modus operandi(a particular way of doing sth.) to commit traditional crimes, such as fraud, child pornography, conspiracy, and theft.
Or activities aiming to damage or modify other computerized systems (usually prosecuted using computer crime legislation). Such as extortion, cyberstalking…
3) Computers being incidental to a crime
Although computers being incidental to a crime, they have significant importance to law enforcement, especially for evidentiary purposes. Imagine in the following scenario:
• Blackmailer uses computer to write blackmail letters
• Drug dealer stores records on computer
• Computer used to research murder methods
IV) Goals and objectives of cybercrime law
Goals: Prevention, investigation, and law enforcement against cybercrimes.

Objectives: Virtually all modern services depend on the use of ICT, with computer technology integrated into products and services
V) Challenges
Potential to harm society, emerging new threats from use of AI and ML techniques.->Deterrence is critical.
Cybercrime has global reach.
VI) Jurisdiction
Traditionally, courts has the ability to only ‘hear’ cases that or disputes that are within their jurisdiction, and jurisdiction describes the authority a particular court has to hear a case such as subject matter jurisdiction(family. Federal court) or personal jurisdiction which refers to the court’s ability to exercise power over the defendant. However, cybercrime as geographical boundaries to not limit computer networks.
In addition, the perpetrators reside in a jurisdiction other than that of their victims in most cases. Thus, evidence must be obtained from multiple jurisdictions in order to investigate. However, International cooperation across national borders to solve and prosecute crimes is complex and slow.
Cybercrime laws in different countries:
UK:

US:

China:
ART 285-287
VII) The Convention on Cybercrime
This is the first multinational treaty on cybercrime issues, dealing particularly with infringements of copyright, computer-related fraud, child pornography and violations of network security.
This is an important international benchmark cybercrime legislation in both industrialized and developing countries.
Its main objective is to pursue a common criminal policy aimed at the protection of society against cybercrime, especially by adopting appropriate legislation and fostering international co-operation.
VIII) Structure and content

8. Substantive Criminal Law
I) Illegal Access: ‘threshold offence’
1) Definition:
Intentional access without right to the whole or part of any computer system(this affect the integrity of the computer system itself):
The Convention on Cybercrime:

Access is about attacks on stored data.(this affects the integrity and confidentiality of the data)
The Convention on Cybercrime ART 2:

Includes all means of entering another computer system, including Internet attacks, as well as illegal access to wireless networks.
More examples:

2) Motives
‘Hackers’ showing off, hacktivism, to commit further crimes
3) Differences between laws

This need to be considered especially on outsiders and insiders questions.
II) Illegal Interception
1) Definition
The Convention of Cybercrime

The provision only applies to the interception of transmissions – access to stored information is not considered as an interception of a transmission.
III) Data Interference
1) Definition
The Convention of Cybercrime ART 4
… when committed intentionally, the damaging, deletion, deterioration, alteration or suppression of computer data without right.->Manipulation or destruction of information.
IV) System Interference
1) Definition
The Convention of Cybercrime ART 5
… when committed intentionally, the serious hindering without right of the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data.
V) Misuse of Devices
1) Definition
The Convention of Cybercrime ART 6


VI) Preventive Measures
9. Cybercrime and International Cooperation
I) Background
Cross-border Crimes are frequent; It is critical to have cybercrime deterrence. However, there are challenges in:
Technical:
(Cybercriminals are not hampered by territorial borders, Difficulty in identifying and locating cybercriminal and the computer involved, Difficulty of locating evidence of crime stored at remote location, Cybercriminals can hide their identities through anonymous software, Availability of hacking tools and techniques on the internet, Difficulty for real-time tracing of transmission when the architecture of the internet does not support it, strong encryption used by criminals, wireless and satellite communications, the cooperation from the private sector/ industry, international cooperation),
Legal:
Absence of cyber criminal law, inconsistent substantive criminal laws in different parts of the world, law lags behind technology and social change, lack of a universal legal framework at international level.

Legal challenges in Jurisdiction:
Jurisdictional borders makes it difficult to commit crime in cyberspace.
Challenges are to identify the location of cybercrime and decide which law apply to that conduct.
Substantive & procedural laws of countries may conflict.
International cooperations are slow.
Extradition(A principle of sovereignty is that every state has legal authority over the people within its borders.)needs to secure: The consensus in international law is that a state does not have any obligation to surrender an alleged criminal to a foreign state.
We have to deal with dual criminality: The act under investigation must be criminalized under both countries’ laws and punishable by a minimum term in prison.
We can apply Mutual Legal Assistance Treaties (MLATs) which is a voluntary cooperation between governments.
Operational:

And cooperation from the industry is not enough.
II) Legal response of cybercrime
1) Substantive Law 2) Procedure Law
III) Legal response of harmonization
1) International Legislative Approaches
United States, Countries in Europe, Japan, G8, OECD, Council of Europe are Global Leaders in Advancing Harmonization
a) Council of Europe (CoE) Convention on Cybercrime
This is the most extensive convention on cybercrime.
It creates a minimum list of cybercrime offenses and attempts to harmonize the elements of those offenses, thereby reducing many conflict-of-law and dual criminality issues
four different types of offences:
• Offences against the confidentiality, integrity and availability of computer
data and systems;
• Computer-related offences;
• Content-related offences; and
• Copyright-related offences
b) The Oxford Process on International Law Protections in Cyberspace
c) Paris Call For trust and security in cyberspace:
o Protect individuals and infrastructure
o Protect the Internet
o Defend electoral processes
o Defend intellectual property
o Non-proliferation o Lifecycle security
o Cyber hygiene
o No private hack back
o International norms
d) Tech Accord
The initiative promotes a safer online world by fostering collaboration among global technology companies committed to protecting their customers and users and helping them defend against malicious threats
IV) Summary

16. Chinese Information Privacy
Root of information privacy in China: ART 40 PRC Constitution, the freedom and privacy of correspondence of citizens of PRC are protected.
Related laws affect data protection:

Prior to PIPL:
2012: Decision on strengthening online information protection
2013: National Standard of Information Security Technology Guideline for Personal Information Protection within Information Systems for Public and Commercial Services
I) Personal Information Protection Law 2021(PIPL)
This is data protection under Chinese law, whose aim is to protect Chinese Citizens, stimulate eCommerce, and balance public interests such as privacy, cybersecurity, or national security.
This is China’s first omnibus information privacy law.
1) Things introduced to Chinese Law
Comprehensive protection approach. Expansion of newer concepts such as sensitive personal information. Extra-territorial reach. Clarification of role of information handlers/ processors & enhanced data security obligations. Enhanced rules on consent and data subjects rights. Cross-border rules transfer rules enhanced & clarified.
2) Effect on business
Business should operate with the law and avoid reputational damage.:
Penalties:
ART 66 states correction and confiscation of unlawful income.
ART 67 states a ‘name and shame’ approach
ART 69 deals with circumstances where cannot prove lack of liability for infringements, including requirements to compensate loss which based on loss to individual and/or unjust enrichment.
ART 70 states the potential prosecution for breach.
a) Collection of personal information must be: legal, necessary and honest; only collect information for intended use; show clarity for data subject.
b) Obligations: to ensure data integrity and security; treatment and use should in line with the law.
3) Oversight Bodies
Oversight Bodies are at national or regional level.
State Cybersecurity & Information Department are at top level.
They are responsible for guidance on law and compliance, enforcement, dealing with complaints from individuals, creation of clear rules and standards for applying the PIPL, support for R&D and adoption of privacy protection technologies, and support for industry certification schemes.
4) Scope
a) ART 3:
Within PRC borders +
outside PRC borders where purpose is to provide products or service into China, or analysis/ assessment of Chinese citizens’ activities within PRC such as market research and targeted advertising. +
“natural persons” who are living currently. For deceased’s information, there’re special arrangements for sensitive handling.
b) ART 4:
Personal information, which are all kinds of information recorded by electronic or other means, and are related to identified or identifiable natural persons (Identifying from the information or Identifying from the information plus other information).
c) Exceptions:
>not including information after anonymization handling, which includes de-identification (processing personal information to make it impossible to identify specific natural persons in the absence of the support of additional information.) and anonymization (processing personal information to make it impossible to identify specific natural persons and impossible to restore.)
>If the profiling problem is in doubt, profiles should be treated as personal information.
d) Sensitive personal information: ART 28
>definition: once leaked or illegally used, may easily cause harm, such as personal dignity/ privacy, personal or property security.
>examples: Biometrics, religious belief, health records, finances, location tracking…; Personal information of minors under 14 years of age; Non-exhaustive list (a list that doesn't show every single thing that would otherwise belong on that list).
>Sensitive personal information need additional safeguards and pay attention to necessity.
5) Subjects that have responsibilities
a) public & private sector application
b) personal information handlers who are organizations/ individuals that “autonomously decide handling processes” and play roles as data controllers. They are also responsible for activities of processors. Any business collecting & using personal information is affected by this law.
6) Consent
a) A13-18
Consent is required for collection and use of individual data.
Data subjects must be informed to consent.
Consent should be voluntary and explicit.
Consent only applies to purposes for specified which information collected, which include entrusting information to sub-contractors.
Consent may be withdrawn.
If data subject declined, service may only be refused if information is necessary.
Exceptions: police investigation…
b) Compliance of consent
One can compliant to consent by management and design such as website design where clear privacy policy with ‘tick box’ type requirement to progress, or recorded message as a telephone sign-up.
Collecting consent should use clear and easily understood language, and key information must be provided which includes name and details of information collector, purpose and duration of collection and use, and information about exercise of data subject rights.
ART 31 states special requirement of children consent.
Consent requires careful management which means not to exceed clear purpose for which collected, and not to be kept longer than needed for that purpose(time limitation).
Consent can be withdrawn, so data collectors need to provide clear information on process such as account settings on website, dedicated email address, and telephone number. So the beast practice is do regular checks.
7) Necessity
This is an alternative to consent.
a) legal compliance
For example tax laws, criminal investigations, or to fulfil contracts which need to disclose payment details and address for distance selling.
b) Emergencies
For example health emergency, and employee collapse at work(工伤).
c) Public interest
For example news reporting.
8) Further Obligations for Personal Information Handlers
a) ART 22: When facing mergers, sale, company dissolution, bankruptcy, the processor shall inform the individuals of the name and contact information of the recipient of the transferred personal information. The recipient shall continue to perform the obligations of the said personal information processor.
b) ART 23: Handlers could transfer personal information to another only with full, informed and voluntary consent.
c) ART 24: Automated decision making must be transparent and fair. Unreasonable differential treatment of individuals in trading conditions is forbidden. Automated decision making must be convenient method to refuse targeted advertising or offers. Individuals have a right to challenge and refuse automated decision making.
Additional rights for individuals:



d) ART 50:
Establish mechanisms and processes to deal with individual requests about data rights.
Provide explanation if refuse a request.
e) ART 51-53 Data Security Requirements
Handlers should give clear information about how information is stored, what are the potential risks, and how they protect information.

Data Security Requirements work closely with Data Security Law 2021.
f) ART 54-56
Regular review and audits of pi handling & compliance, including security provisions.
Provide impact assessment before information collected, when relates to sensitive pi, automated decision making, using subcontractor, sending pi outside China, or otherwise “major impact” on data subject.
g) ART 57 Response to data leak
There should have immediate remedial measures based on existing processes.
They have notification requirements to government departments dealing with PI protection. The notification must include information category, cause, potential harm; measures to mitigate harm; and contract details. There’s no need to notify individuals if handlers can ensure harm avoidance. Otherwise, if the handler believe harm may have been caused, they must notify affected individuals.
h) ART 58 Providers of “important internet platform services”
To those have a large number of users and their business models are complex such as social media, and any other companies who have scale or quantity of personal information, the law has additional requirements:
Oversight bodies should composed mainly by outside members; They should provide public social responsibility reports.
i) Working with other companies (co-handlers, sub-contractors, cross-border transfers)
ART 59: If PI is processed by third party contractors, they must ensure data security.
ART 20: If there are more than one PI hander working together, they shall reach clear agreement on division of rights and responsibilities, and individuals can still demand action about their rights from any one PI handler.
>Subcontractors:
ART 21:
Only after the consent of data subject can subcontractors enter the process.
There must be an agreement setting out key issues like time limitation, handling method, types of PI to be collected, protection measures, and rights and duty of each side.
Subcontractors are achievable by contractual agreement or binding corporate rules.
Subcontractors have legal responsibility for oversight remains with (To continue to be a member of a group, team, organization, company, etc.) the PI handler.
>cross-border operations that transfer data out of China for processing and use elsewhere:
ART 38:
Data exportations are only allowed if it’s truly necessary.(data localization)
Before cross-transfer, the operation must fulfill one of the following assessment or certification:

If data export to company in country where China recognizes its law, it is also allowed.
Exporters are liable to ensure compliance with law by applying strategies like training their staffs, shoulder oversight legal responsibilities like giving advice, forming contract like get everything in writing, and pay close attention to Cybersecurity & Information Department security advice.
ART 39: Consent of the data subject is required. While asking for consent, PI handlers should fully inform them and apply all standard consent requirements and all details must be provided to permit full exercise of data subject rights.
ART 40: Critical information infrastructure operators and PI handlers [who meet set data quotas] must store information within PRC. They are overseen by C&I Dept and specifically take security assessments unless they have a standard arrangement in place with destination country.
ART 41: National security issues
Personal information stored in PRC may only be provided to foreign judicial or LEAs where PRC authorities have granted permission.
ART 42: Blacklist Provision
If foreign organizations or individuals violate PRC law on information protection or harm national security, State C&I Dept can add to list requiring their access to Chinese PI be limited or prohibited.
9) PIPL & International Transfers

10) Key practical advice for compliance
a) For profiling questions especially those online are in doubt, treat them as PI.
b) Informed consent is king. One should invest in ensuring consent is properly acquired, by web design, training of telephone staff, clearly explaining privacy policies with appropriate attention drawn, recording for telephone or a script. Consent trumps necessity.
c) sensitive personal data are easier to avoid where it is possible. They should have extra care and only process where it’s strictly necessary.
d) If children are target market or among it: Parental consent requirements, age verification by checking citizenship number, credit card…, extra flagging is needed while designing website and making telephone procedures.
e) Consent is an ongoing process which can be withdrawn. Thus PI handlers need to have regular dialogue with users just as cooking warnings and regular reminders.
f) PI handlers should facilitate user rights by ensuring key contact details available, arranging specialist staffs at where appropriate(酌情), establishing proper internal organizations and processes, paying attention to website design and access, and considering procedure in place for posthumous dealing with data, deletion whenever appropriate.
g) Ensuring data security by complying with all guidance per regulatory authorities, ensuring encryption, firewalls et cetera are kept up to date, procedures in place for handling a data leak should one arise, prevention is better than cure.
h) Work with others by setting individual consent, creating clear liability rules and find trusted partners who bear oversight responsibilities. For transfer of PI outside China, exporters should ensure compliance with data localization rules, follow the necessary rules, get informed consent, and have clear contractual agreements which may help with liability questions even where law recognized by PRC.
i) Keep clear records on information sent to customers, security procedures, actions in event of breach, audit requirements, dealing with individuals, showing followed all the rules, which are all acting as evidence.
II) Communications Privacy in China 2012
This is decision of the Standing Committee of the National People’s Congress on Strengthening Online Information Protection
1) Collection of digital personal data by network service providers and other enterprises and public institutions without consent of data subject is forbidden.
2) Collection may only be done with consent plus disclosure of objective, scope and method of collection.
3) Security obligations
4) Obligation to publish their rules on data collection and use
5) Citizens entitled to request deletion of information collected in infringement of rules or privacy and other remedies, such as fines, confiscation(taking it away as punishment) of profits, or websites shut down.
6) ART 7: Measures for Security Protection Administration of the International Networking of Computer Information Networks in the PRC:
Users' freedom of communication and communications secrecy are protected by law. No unit or individual shall use the international networking to infringe on users’ freedom of communication and communications secrecy in violation of the provisions of law.
7) ART 18: Implementation Rules for Provisional Regulations of the Administration of International Networking of Computer Information in the People’s Republic of China:
It is prohibited to infringe on the privacy of others by accessing computer systems without authorization, tampering(to touch or make changes to something that you should not, usually without enough knowledge of how it works or when you are trying to damage it)with the information of others or sending information in the name of others.
8) Measures for the administration of Internet e-mail services 2006:
a) Obligations on e-mail providers should:
>keep confidential the users personal registered information and Internet e-mail addresses;
>not illegally use any users personal registered information or Internet e-mail;
>not divulge(make known private or sensitive information) the uses personal registered information or Internet e-mail address without consent of the user;
>Confidentiality requirements: ‘national security’ provisions in EU law & elsewhere
>Email services must comply with technical specifications established by the MII;
>Anonymous email forwarding must be prevented by disabling open-relays(accept mail from any sender and deliver it to any recipient. );
>Security management is required, and remedial measures must be immediately undertaken when network security flaws are discovered;
>Service providers must maintain copies of all emails sent and received, as well as the email addresses and IP addresses of senders/receivers for at least 60 days;(just as EU ePrivacy Directive states: provisions on retention of Traffic Data)
>Penalties for breach
>Reporting obligations: report to compliant and handling center for email abuse
> Anti-spam provisions:
>>Labeling obligation which means advertising emails must be clearly labelled ‘AD’ in subject line;
>>Opt-in consent to receiving advertising email, and unsolicited advertising emails are forbidden.
>>Prohibited Activities, which include sending of email from someone else’s computer without authorization, email harvesting(collecting a large number of email addresses following some illegal methods), selling, sharing or distributing harvested emails, and creating anonymous/ mislabeled emails.
>>Content restrictions: state secrets, hate speech, defamation, obscenity, pornography, gambling, violence, incitement to criminal activity.
>> Prohibitions on hacking, theft of others’ information on a network, spreading viruses, attacks on network security.
III) Personal Information Protection Guidelines 2013
This is guidelines for Personal Information Protection within Public and Commercial Services Information Systems.
1) This law has similar definition of PI to IISP(Internet Information Service Provider) Provisions
2) Information obligations include: why, what, how collecting, and how long will be held; Contact information for collector; how to register a complaint
3) When transferring to third parties, there should state why and what to be transferred, the reason for transfer, and the details of third parties.
4) Sensitive PI requires express consent, general PI only need tacit consent(understood or implied without being stated) which could be assumed in absence of objection.
5) Minimum collection requirement
6) PI must be deleted once the purpose for which collected is completed.
7) This is only a non-mandatory guidance.
IV) Chinese Laws which protect Information Privacy in Specific Sectors
1) Postal Law-protection of communications privacy
ART 4: Freedom and privacy of correspondence shall be protected by law. No organization or individual shall infringe the freedom and privacy of correspondence of other persons for any reason, except when the inspection of correspondence in accordance with legal procedures by the public security organ, the State security organ or the procuratorial organ is necessary for the State's safety or the investigation of a criminal offence.
2) Criminal Law- Protection of personal information
a) ART 252: [t]hose infringing upon the citizen's right of communication freedom by hiding, destroying, or illegally opening others' letters, if the case is serious, are to be sentenced to one year or less in prison or put under criminal detention.
b) Article 284: Whoever unlawfully uses any special equipment or devices for eavesdropping or secret photographing, if the consequences are serious, shall be sentenced to fixed-term imprisonment of not more than two years, criminal detention or public surveillance.
c) 2009 amendments: penalize sale and other illegal transfers of personal information by employees of government agencies and other institutions have up to 3 years’ imprisonment. ( but the definition of “unlawful provision” or “personal data”, and assessment criteria of “severe” violation are not clear)
d) ART 253(A):
where any staff member in violation of the state provisions, sells or illegally provides personal information on citizens, which is obtained during the organ’s or entity’s performance of duties or provision of services, to others shall, if the circumstances are serious, be sentenced or criminal detention, and/or be fined.
Whoever illegally obtains the aforesaid information by stealing or any other means shall, if the circumstances are serious, be punished.
where any entity commits crimes it shall be fined, and the direct liable person in charge and other directly liable persons shall be punished.
3) Communication Privacy in China
4) PRC Supreme People’s Court Guidance-
Provisions of the Supreme People’s Court on Several Issues Concerning the Application of the Rules regarding Cases of the Infringement of Personal Rights over Information Networks
Contents include:
1) whether an ISP was “aware” of infringement
2) Liability for reprinting, unauthorized modification or deletion
3) Procedures for legal action
4) Scope of information protected
5) Disclosure online is permissible if:
a) there’s consent in writing
b) Disclosure is necessary in the public interest
c) Educational or scientific entity makes disclosure in public interest, academic research, or statistical analysis, which is with consent in writing to publication and publication will not identify individuals.
d) Information is already made public, online or otherwise.
e) personal information is legitimately obtained.
V) Data Privacy and Online Services; Inc. Consumer Protection
1) IISPs & Personal Information
In 2012, there were several provisions on regulating the market order for internet information services.
(a) Those regulations came from ministry of industry & information technology(MIIT).
(b) The range of those provisions includes anti-competition, consumer protection (such as Inc. and users rights, pop-up advertisements, data protection, and information security), and new penalties.
(c) These regulations apply to website operators.
(d) ART 11:
>User’s personal data is:
Data related to a user which can identify a user if the data is used independently or in conjunction with other information
>User consent is required for:
Collection of personal data, disclosure to third party, but these activities are subject to exceptions provided for by law/ administrative regulation.
>Once consent obtained, IISPs should send clear information to user on how data will be collected/ processed and what personal data have been collected.
>Limitation of collection is IISPs can only collect data which are necessary to provide services, and they also should follow use restrictions.
(e) ART 12:
>Website operators have duty to protect information
>data leakage must be reported to local telecommunications authorities is may cause serious consequences.
(f) ART 13:
>Users have rights to use/ modify/ delete information they uploaded
>Operators may not modify or delete information without legitimate reason
>Operators may not disclose or transfer without user consent
>User consent must be genuine where no deception, coercion or misleading.
(g) ART 14:
For complaints procedures, one should have clear contact information for operator on website and wait for a 15 day response period.
(h) ART 15-18:
Penalties are monetary, and telecommunication authorities are empowered to make public announcement of wrongdoing.
2) Provisions on Telecommunication & Internet User Personal Information Protection 2013
ART 2: This applies to both IISPs and telecommunications business providers.
Along with 2012 Regulations and 2013 Guidelines, a fairly comprehensive set of DP rules for the internet have been established.
There are focused as well as binding regulation.
a) ART 4:
Personal information is information relating to individuals, collected by telecommunication companies and IISPs in course of service provision, including name, DOB, ID no, address, phone, account info, passwords and other info that can be used separately or with other information to identify an individual. PI also includes log details.
b) EU-style Fair Information Practice Principles
>ART 5: collection must be legal, proportionate and necessary, and other law requires retention for security purposes.
>ART 9: for consent requirement, although there’s no mention of opt-in/out, 2013 Guidelines suggest opt in for sensitive PI. And there should have throughout transparency by forming informed consent.
>Requirement to ensure data security:
Requirement to have internal allocation of administration of security;
Management systems and security protocols to be in place for collection of personal information;
Third party processors to be supervised and managed;
Technological protection should be put in place such as firewalls, antivirus, encryption, etc.;
There should also have protocols dealing with data breach;
ART 17: MIIT(China’s Ministry of Industry and Information Technology) officials can inspect to ensure compliance.
> Data breach
Response to reports of data breach should within 15 days;
Requirement to report a security breach to MIIT where possibility of serious consequences;
Duty to take remedial action to minimize effect of breach
>Enforcement
Penalties for non-compliance if
there’s failure to publish protocols for collection of personal data or failure to report misuse of personal data;
or collection of personal data without consent, misusing personal data, or failing to protect personal data properly(ART 22).
VI) Banking & Financial Services: Outsourcing
1) Guidelines for the supervision of IT Outsourcing risks of Banking Financial Institutions (2014)
a) ART 2: this apply to all banks and finance institutions established in PRC
b) ART 3: design to regulate outsourcing:
>The term outsourcing refers to the banking financial institutions’ entrustment of service providers with some of their own business for continuous handling.
> Service providers shall include independent third parties and the subsidiary companies, affiliated companies or related companies established inside and outside China by the parent companies of banking financial institutions or the groups to which they are subordinate.
>Bank financial institutions(BFI) duties include:
ART 15: guarantee confidentiality of client information; notify clients that outsourcing is happening;
ART 16: Company to which outsourced must protect client information otherwise BFI can terminate outsourcing contract at Any time;
ART 19: Where dealing with overseas partner, must ensure protection of information and partner signs up to Chinese protection standards;
ART 23: in the event of data breach, must notify banking authorities;
ART 24: Carry out inspections of outsourcing facilities to ensure standards.
VII) Consumer Protection Law

1) Chinese Consumer Protection Law
a) Aim
ART 1: to enhance consumer protection and to promote development of the socialist market economy.
b) Scope
ART 3: consumer transactions where proprietors producing or selling goods to provide to consumers.
c) mix of obligations for sellers and rights for consumers
ART 14: consumers have their rights to protect their personal information.
2) Consumer Protection Measures 2015
- Measures for the Punishment of Conduct Infringing the Rights and Interests of Consumers
(a) ART 11:
List of forbidden actions re infringement of consumer privacy in personal information;
Consumer personal information is information collected by an enterprise operator during the sale of products or provision of services, that can, singly, or in combination with other information, identify a consumer;
Examples of Consumer personal information are “name, gender, occupation, birth date, identification card number, residential address, contact information, income and financial status, health status, and consumer status.
(b) Forbidden activities
ART 29: Collection & use without consent; Disclosure, sale, or illegal transfer to third parties; Commercial communications (SPAM) where either no consent or clear indication not wanted.
(c) Obligations
ART 29: Lawfulness, rationality, necessity; Expressly state purpose, method, scope of collection & use; Consent; Security (and duty to act if breach); Publicize Privacy Policy; Observe additional laws and/or contractual obligations.
(d) Penalties
ART 56: warning; confiscation of illegal gains; fine; closure of business for remediation or revocation (the official cancellation of a decree, decision, or promise) of business license.
(e) potential civil liabilities

(VIII) National Security & Cybersecurity Laws
(1) National Security Law 2015
This law is to protect people’s fundamental interests.
Internet infrastructure is important for China, and we need to apply law over it.
Key internet and information systems need to be secure and controllable.
This law reflects the global trend of government concern about online threats to national security.
(2) PRC Cybersecurity Law
(a) Key aim
Combat fraudulent online use of personal information and protect against internet security risks.
(b) new obligations:
>Transfer of personal information outside of China;
>Network operators’ obligations:
They should give data privacy notifications, perform technical protection for data security, and notify immediately in event of breach to authorities and sometimes to users;
When collecting PD, network operators should be lawful, necessary, not excessive, have consent, no illegal collection actions, and exempt truly anonymized data.
>data subjects have right to correct any inaccuracies in personal data held by network operators, and request deletion of data in evet of a breach.
>’Real identity’ rules(Mandatory registration on social networking sites with real identities) should apply to network operators while handling network access and domain registration services.
(c) new PRC commerce Law has wider context than PRC Cybersecurity Law
(3) Protection of Minors
(a)2017 PRC Cybersecurity Law includes new rules requiring providers of networks and online services to protect minors.
(b) Provisions on Cyber-protection of Personal Information of Children (2019):
>Protect children under 14, have parental consent, and must have consent withhold option.
>principle-based approach:

>informed consent required content:

>network operators:
Follow user agreements and codes of conduct for specific protections for children;
Follow minimum authorization rules for access to under 14 data;
Requests of contractual rules for third-party processors;
Parental entitlement to access, correct, delete data;
Parents must be notified of data breaches of their children’s.
(4) National Cyberspace Security Strategy
Key goals for China’s information security: highlight Chinese Internet Sovereignty:
Establish rights to police internet within China and;
Establish safeguards of key information infrastructure operators:
Information facilities that have an immediate bearing on national security, the national economy or people's livelihoods such that, in the event of a data leakage, damage, or loss of functionality, national security and public interest would be jeopardized.
(5) Personal Data Security Specification 2020
(a) In this specification, personal data definition goes beyond the cybersecurity law and explicitly include biological identity data, behavioral data, and geographical location data.
Personal data also includes:

(b) personal sensitive data
(c) key requirements for data controllers
> risk management:
>>assign staff/ department for data security management if business has over 200 employees and collects personal data
>>If processes more than 500,000 people’s personal data, data security department must be dedicated.
>>Perform regular risk assessments
>>adopt appropriate security measures such as encryption
>>have data security audits
>>make public disclosure
>emergence disposal and reporting:
>>Set out strategic plan to follow in the event of a breach
>>Keep proper records of details of any breach
>>notify authorities or individuals if they are affected
>specific guidelines on collection/storage/processing of data
>>Meet the requirements of consent either passively or explicitly
>>Collect and retain only what is necessary for as long as necessary
>>data subject has right to access, correct, and call for deletion, while controllers can refuse if there’s reasons to suspect malicious intent or abuse.
>privacy by design requirement:
>>considering the factors in trialing or testing new products
>training data protection officers
>data processing records:
>>Controllers must maintain and update records of processing of data by keeping track of collection and use.
>specific requirements on transfer and disclosure of personal data:
>>Prior consent is required for transfer or disclosure
>>perform risk assessment before transfer or disclosure
>>data controller must ensure that transferee at least meets data controller’s standards of data security
>outside transfer only if controller comply with all relevant Chinese regulations and standards
(6) Measures for the Security Review of Network Products and Services
(a) Scope: Network services which might affect national security will be subject to security review
(b) Key issue: products or services must be secure and controllable, which shall be determined by analyzing following factors:

(7) Measures for the Security Assessment of Outbound Transmission of Personal Information and Critical Data
(a)This guideline state obligations for network operators, who should:
>Have prior consent from data subject.
Exceptions are for emergencies where life or property of data subject is in danger.
Consent can be implied by an affirmative act.( positive steps taken to increase the representation of women and minorities in areas of employment, education, and culture from which they have been historically excluded.)
>Must conduct a security assessment of all cross-border transfers of personal data
Large-scale transfers(involves pd of over 500,000 individuals) AND/OR transfers involving relatively sensitive information must be overseen by a regulatory authority
(8) Other Guidelines
(a) Draft Guidelines on Multi-Level Protection Scheme for Information Systems
(b) Draft National Standard of Information Security Technology – Guidelines for Personal Information Security Impact Assessment
(c) Draft National Standard of Information Security Technology – Guidelines on Data Security Capability Maturity Model
(d) Draft Guideline for Internet Personal Information Security Protection
(e) The People's Bank of China's Circular on Further Intensifying Management of Credit Information Security:
This guideline states obligations to strengthen credit information security in relation to access to database for financial credit information
(f) PBOC(People’s Bank of China) PFI(Private Financial Initiative) Specification
PFI: to encourage private sector businesses to tender to local and central government authorities for the provision of public infrastructure and services. private sector finances, builds and operates infrastructure and provides long term services and facilities management through long term contractual arrangements
This specification gives additional privacy and cybersecurity requirements for PFI and applies to Finance Industry.
(g) Ministry of Industry and Information Technology
It gives guidance on areas for industry improvement
(9) Data Security Law 2021
This covers security requirements for personal information, especially cross-border transfer and data trading.
(a) ART 31: Penalties for company officers in charge of compliance if violate security requirements

(IX) China’s Ecommerce Law
(a) Scope: This law applies to all ecommerce taking place in China.
(b) Definition:
Ecommerce is business activities of sales of goods or provision of services through the Internet and other information networks. While the followings are excluded:

(c) ART 24: Ecommerce businesses must clearly state methods or procedures to facilitate individuals to:
Make enquiries about what information is held about them, correct wrong information, delete user information where requested, and de-register user-accounts as long as no unreasonable conditions are to be applied.
(d) ART 25: Provide information to relevant authorities on request for criminal investigation etc.
- [JX1]‘consent’ of the data subject means any freely given, specific, informed and unambiguous indication of the data subject’s wishes by which he or she, by a statement or by a clear affirmative action, signifies agreement to the processing of personal data relating to him or her;
- [JX2]‘pseudonymisation’ means the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information, provided that such additional information is kept separately and is subject to technical and organisational measures to ensure that the personal data are not attributed to an identified or identifiable natural person;
Different from fully anonymized data




















 723
723











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








