This series of articles are the study notes of "An Introduction to Programming the Internet of Things", by Prof. Harris, Department of Computer Science, University of California, Irvine. This article is week 1, lessen 1: Definition of the Internet of Things (IoT). This article is the notes of Lesson3: The Importance of the Internet of Things (IoT) in Society.
3. Lesson 3 The Importance of the Internetof Things (IoT) in Society
3.1 Lecture 3.1 Societal Benefits of IoT
3.1.1 IoT makes life easier
- What food do I need?
- Are my accounts balanced?
3.1.2 Independence from people
- IoT devices handle things you needed humans for
- Fewer doctor visits; no trips to the super market
3.2 Lecture 3.2 Risks, Privacy, andSecurity
3.2.1 IoT Risks
Social isolation
Dependence on technology and infrastructure
Another big problem with IoT is that you're now more dependent on technology, and all the infrastructure that comes along with it. So, if things go down, like for instance my email. And this is noteven really an Internet of Things issue. But, email, I use it on a standard computeror my iphone too, if I want to. But if email goes down, it's a seriousimpediment to me. When you're using it through IoT, through the internet, and through your devices, when your device goes down, or when the network itself goes down, it's a big problem for you. So, power outages in general are a big problem because all your devices are going down.
3.2.2 Privacy and Security
So another property of these IoT devices isthey are, they're recording information. They are observing us. Now, presumably for our benefit. But they are observing us a lot and they are pervasive, so everywhere.
Observation by IoT devices is pervasive
- Location: cell phone
- Health: health monitor
- Media watching habits: TV/ media system
- Purchasing habits: credit card, cellphone
- Driving habits: car incident recording
Data may be used to market to you
- Health problem? Drugs may be marketed to you
Purchasing an IoT device may give the manufacturerpermission to use or sell your data
- Consumer agreement contracts can be cryptic
Often you give permission to the person you purchase the device from, you give them permission to use that data in those long agreements that you click Okay to. So when you buy a device, buy a phone, or put an application on your phone and it says do you accept the agreement terms? And you don't read that, but you click Okay.
Data my be used by insurance agencies
This type of information is very useful to different agencies in different ways. And you should be aware that while these IoT devices are beneficial to you, they are storing data and that data may or may not be in your control.
- Were you speeding at the time of the accident?
- Do you have any undignosed health problem?
Security: data maynot be held in a secure way
- Cloud is attacked with your data inside
- Even encrypted data is decrypted in use
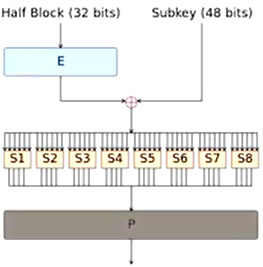
Security's another thing. Often this datais held in the cloud somewhere. So say FitBit, it tracks your data, it sends it to some cloud servers. Now, this is medical information and you would like it to remain private. And they maybe try to keep it private, but there are hackers. There are people who steal data, and you must have heard about this inthe news. The data can be attacked at the cloud server, and it's out of your control. So if that data isn't maintained in a secure way. So, what we're showing over here is basically a rough picture of an encryption algorithm. But the idea is that data would need to be encrypted.


























 4399
4399

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








