实验开始前
1.准备好两台虚拟机(下载好镜像文件的)
2.实验步骤
公钥验证:(免密登陆验证方式)
(1)生成非对称秘钥
[root@client ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:i8wSE5j8P2yxx8tsfkgkG+VBCDBfuW4Y5UdDpMq9cd4 root@client
The key's randomart image is:
+---[RSA 3072]----+
| o....*+ |
| . = .+.= |
| + oo.= o |
| o.+= + |
| *++*S |
| .B+X.o |
| ..@.=.E |
| o =o.. |
| o=. |
+----[SHA256]-----+
(2) 公钥发送到服务器/root/.ssh/authorized_keys
[root@client ~]# ssh-copy-id -i root@192.168.10.129
(3) 等待客户端请求内部通过非对称验证
[root@client ~]# ssh root@192.168.10.129
以上是实验步骤,下面是具体操作:
可以在VMware里面操作,也可以用Xshell,我这里用的是MobaXterm
1. 我这里先将虚拟机名字改了(方便看是否连接上)
这里客户端IP为192.168.168.129
服务器的IP为192.168.168.128
2. 生成非对称秘钥
ssh-keygen -t rsa
3. 公钥发送到服务器/root/.ssh/authorized_keys
[root@client ~]# ssh-copy-id 192.168.10.129
4. 等待客户端请求内部通过非对称验证
[root@client ~]# ssh 192.168.10.129
[root@client ~]# #先改名虚拟机名字,方便查看是否连接上(必须永久保存名字,不然没用)
[root@client ~]# hostnamectl set-hostname client
[root@client ~]# #再生成非对称密钥
[root@client ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
/root/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:NHG9KayVObJloLgIlK+urlFYJkYzTUJ7BcBd1rs1lhw root@client
The key's randomart image is:
+---[RSA 3072]----+
|oB*oo+. . .. |
|.+=oo ..E . |
|oo+. . .=ooo o |
|o=... .o.BX o |
|..o. . SB.o |
| o. . .o |
|o |
| o |
|*. |
+----[SHA256]-----+
然后再将公钥发送给服务器(IP地址):
注意这里输完:[root@client ~]# ssh-copy-id 192.168.10.129这个命令后,会让你输入yes还是no
[root@client ~]# #然后再将公钥发送给另外一个虚拟机(服务器)
[root@client ~]# ssh-copy-id 192.168.168.128
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.168.12 (192.168.168.12)' can't be established.
ED25519 key fingerprint is SHA256:t9VyyGfB3e3ltZhQPNA27vzQt4OVzyYielt8R9SI8Ho.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.168.128's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.168.128'"
and check to make sure that only the key(s) you wanted were added.
然后服务器配置也是一样的操作:
[root@server ~]# hostnamectl set-hostname server
[root@server ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:t7DsCVsPfihjwFagBdeqWxLXIXUp+pzwMAWs+muSnzI root@server
The key's randomart image is:
+---[RSA 3072]----+
| .oo+. .. |
| .= =.. |
| + B o |
| + B o |
| . = O .S . |
|. o = =. + . |
| o = .. =.. |
|E +. +*.+. |
| *+. ..o+.. |
+----[SHA256]-----+
[root@server ~]# ssh-copy-id 192.168.168.129
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.168.129 (192.168.168.129)' can't be established.
ED25519 key fingerprint is SHA256:t9VyyGfB3e3ltZhQPNA27vzQt4OVzyYielt8R9SI8Ho.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.168.129's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.168.129'"
and check to make sure that only the key(s) you wanted were added.
最后验证:
直接输入ssh + IP地址
客户端到服务器:
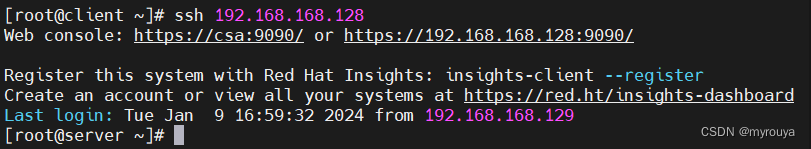
服务器到客户端:
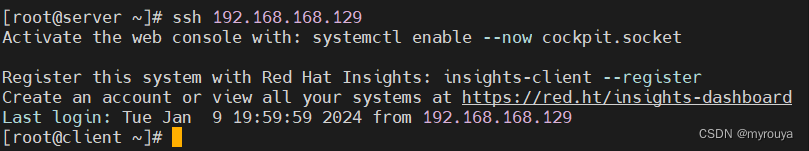
可以看到输完ssh后,直接登录进去了,免密登录,实验就完成了




















 2741
2741











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








