Our analysis and further investigation on proxyOverflow (CVE-2018–10376) and batchOverflow (CVE-2018–10299) vulnerabilities. Verichains Lab has performed a scan on all Ethereum smart contracts with above 100 tx and confirmed that the bugs affected quite a number of smart contracts.
Integer overflow
This section is just definitions, can be skipped for people already know about it.
In computer programming, an integer overflow occurs when an arithmeticoperation attempts to create a numeric value that is outside of the range that can be represented with a given number of bits — either larger than the maximum or lower than the minimum representable value. - wikipedia.org
In computer, normal integer operations work well if nothing is out of bound, 1 + 1 = 2, 2 + 2 = 4, 4 + 4 = 8, …, 64 + 64 = 128, …
wait, that simple addition does not work with computer, if the last addition operation is performed using 8-bit signed integer arithmetics, the result is -128!
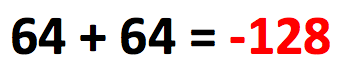
This seems wrong but actually it’s the way integers work in computer. All operations of fixed width integers are truncated. If a number is stored as 8 bit signed integer, its value must be within the range -128 to 127, inclusively, else the value will be truncated into that range, or in another way, only lowest bits are kept for the operation results.
Binary expression of 8 bit signed integers for values from 0 to 127 are:
0: 00000000 | 1: 00000001 | 2: 00000010 | 3: 00000011 ... 124: 01111100 | 125: 01111101 | 126: 01111110 | 127: 01111111
Negative numbers are expressed using two’s complement. Values from -128 to -1 are:
-128: 10000000 | -127: 10000001 | -126: 10000010 | -125: 10000011 ... -4: 11111100 | -3: 11111101 | -2: 11111110 | -1: 11111111
The number 64 is encoded as 01000000 in base 2, 64 + 64 is 0100000 + 01000000 = 10000000, it’s actually 128 but it’s out of the range above encoding can cover, so it’s truncated and mapped to-128 as in the above table!
Furthermore, in 8-bit unsigned arithmetics, 128 + 128 = 0. More formally let’s say we store result ofa + b into variable r which encoded using n-bit unsigned integer, only the following equation holds:
a + b ≡ r mod 2^n
CVE-2018–10376: proxyOverflow
An integer overflow in the transferProxy function of a smart contract implementation for SmartMesh (aka SMT), an Ethereum ERC20 token, allows attackers to accomplish an unauthorized increase of digital assets via crafted _fee and _value parameters, as exploited in the wild in April 2018, aka the “proxyOverflow” issue.
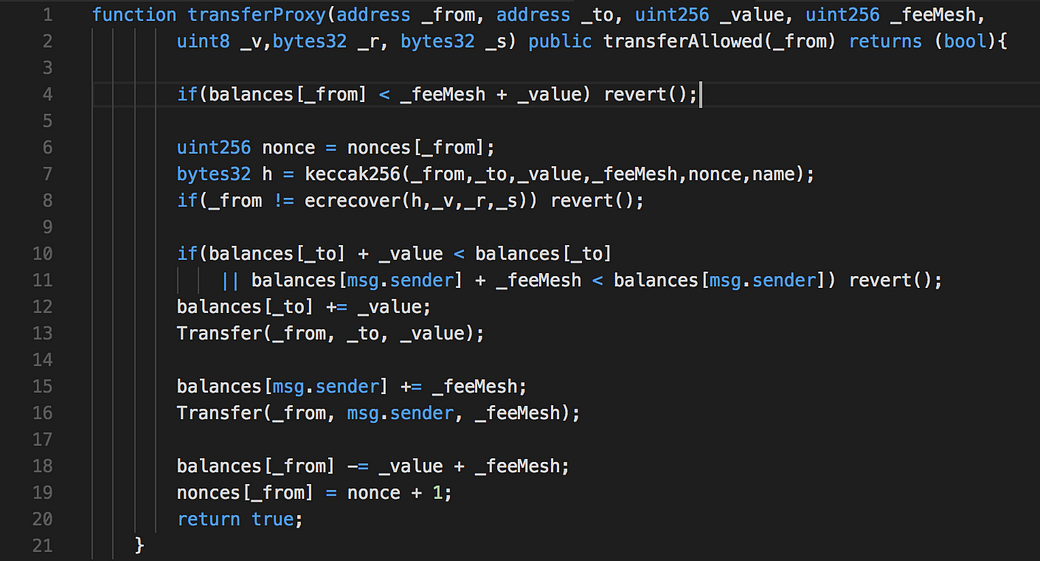
This method already have integer overflow in mind (coded at line 10 and line 11 to detect overflow on post-update balance check) but the pre-update balance check at line 4 did not handle addition-overflow of _feeMesh + _value, both these 2 variables are directly controlled by user-input as parameters. With integer overflow each of these variables can be large enough and their sum (truncated with integer overflow) become small enough to satisfy the check, which has been used to exploit the contract at block 5497602:
Function: transferProxy(address _from, address _to, uint256 _value, uint256 _fee, uint8 _v, bytes32 _r, bytes32 _s)
MethodID: 0xeb502d45 [0]: 00000000000000000000000024e62761adad4e64be580efa6180282004bae866 [1]: 00000000000000000000000024e62761adad4e64be580efa6180282004bae866 [2]: 8fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff [3]: 7000000000000000000000000000000000000000000000000000000000000001 [4]: 000000000000000000000000000000000000000000000000000000000000001b [5]: aebbb9bbb393b69eabc44fea38860cf7fbf274d179b37a1d6444569b734f17f3 [6]: 16565f08cb904fe6c00ff33618acc13ca6bd269150353648851525beb9d048ec
With the above input, _value is 8fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff, _feeis 7000000000000000000000000000000000000000000000000000000000000001, which sums up to 0 in 256 bit unsigned integer.
CVE-2018–10299: batchOverflow
An integer overflow in the batchTransfer function of a smart contract implementation for Beauty Ecosystem Coin (BEC), the Ethereum ERC20 token used in the Beauty Chain economic system, allows attackers to accomplish an unauthorized increase of digital assets by providing two _receivers arguments in conjunction with a large _value argument, as exploited in the wild in April 2018, aka the “batchOverflow” issue.
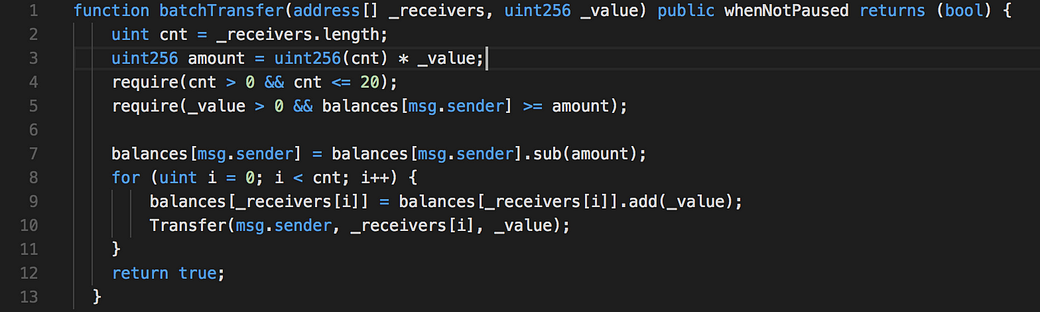
This time the overflow is caused by multiplication on line 3, with large enough _value and cnt, we can generate small enough amount and exploit the contract, like in block 5512547:
Function: batchTransfer(address[] _receivers, uint256 _value)
MethodID: 0x83f12fec [0]: 0000000000000000000000000000000000000000000000000000000000000040 [1]: 8000000000000000000000000000000000000000000000000000000000000000 [2]: 0000000000000000000000000000000000000000000000000000000000000002 [3]: 0000000000000000000000004473c6396eba3d737f953a8849b0f4296be8c3e7 [4]: 00000000000000000000000066f471fd1c471bb3ee15d81a3cea4a7f21282355
The above input sent _value as 8000000000000000000000000000000000000000000000000000000000000000 and the _receivers as array of length 2, which result in amount = 8000000000000000000000000000000000000000000000000000000000000000 * 2 = 0.
Affected contracts
Using our internal tool, Verichains Lab has performed a scan on all Ethereum smart contracts with above 100 tx and found that the bugs affected quite a number of smart contracts.
batchTransfer
UPCToken (UPCT), UPCToken (UPC), MTC (MTC), BeautyChain (BEC)
transferProxy
MeshBox (MESH), M2C Mesh Network (MTC), M2C Mesh Network (mesh), SmartMesh (SMT), UG Token (UGT)
We also found a contract with similar vulnerability but luckily the method can only be called by admin.





 本文深入分析了两个智能合约漏洞:proxyOverflow (CVE-2018–10376) 和 batchOverflow (CVE-2018–10299),详细解释了整数溢出的概念及其实现方式,并通过实际案例展示了攻击者如何利用这些漏洞非法增加数字资产。
本文深入分析了两个智能合约漏洞:proxyOverflow (CVE-2018–10376) 和 batchOverflow (CVE-2018–10299),详细解释了整数溢出的概念及其实现方式,并通过实际案例展示了攻击者如何利用这些漏洞非法增加数字资产。
















 1017
1017

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








