setu
In order to fight Covid19, the Indian government released a mobile contact tracing application called Aarogya Setu. This application is available on the PlayStore and 90 million Indians already installed it.
为了对抗Covid19,印度政府发布了一个名为Aarogya Setu的移动联系人跟踪应用程序。 该应用程序在PlayStore上可用,已经有9000万印度人安装了该应用程序。
This application is currently getting a lot of attention in India. In Noida, if people doesn’t have the app installed on their phone, a person can be imprisoned up to 6 months or fined up to Rs 1000.
该应用程序目前在印度引起了很多关注。 在诺伊达,如果人们未在手机上安装该应用,则可能会被判处最高6个月的监禁或1000卢比的罚款。
访问应用内部文件 (Access to app internal files)
On April 3, 2 days after the launch of the app, I decided to give a look to the version 1.0.1 of the application. It was 11:54 pm and I spent less than 2 hours looking at it.
在启动应用程序两天后的4月3日,我决定看一下该应用程序的1.0.1版本。 当时是晚上11:54,我花了不到2个小时的时间在看它。
At 1:27 am, I found that an activity called WebViewActivity, was behaving weirdly. This activity is a webview and is, in theory, responsible of showing web page like the privacy policy for example.
凌晨1时27分,我发现一个名为WebViewActivity的活动行为异常。 该活动是一个webview,从理论上讲,它负责显示网页,例如隐私策略。

The issue is that WebViewActivity was capable of doing a little bit more than that.
问题在于,WebViewActivity的功能还不止于此。

As you can see, the onPageStarted method checked the value of the str parameter. If str:- is tel://[phone number]: it will ask Android to open the dialer and pre-dial the number- doesn’t contain http or https, it does nothing- else it is opening a webview with the specified URI.
如您所见,onPageStarted方法检查了str参数的值。 如果str:-是tel:// [电话号码]:它将要求Android打开拨号程序并预拨该号码-不包含http或https,则不执行任何操作-否则它将使用指定的名称打开Web视图URI。
As you can see there is no host validation at all. So, I tried to open an internal file of the application called FightCorona_prefs.xml by sending the following command
如您所见,根本没有主机验证 。 因此,我尝试通过发送以下命令来打开名为FightCorona_prefs.xml的应用程序的内部文件

As you can see in the following video, it worked fine!
正如您在以下视频中看到的那样,它运行良好!
Why it’s a problem? With only 1-click an attacker can open any app internal file, included the local database used by the app called fight-covid-db
为什么有问题呢? 只需单击一下鼠标,攻击者即可打开任何应用程序内部文件,包括该应用程序使用的名为fight-covid-db的本地数据库
知道印度任何地方谁生病的能力 (Ability to know who is sick anywhere in India)
On May 4, I decided to push my analyse a little bit further and I analysed the version v1.1.1 of the app which is the current version.
5月4日,我决定进一步分析,并分析了该应用程序的v1.1.1版本(当前版本)。
The first thing I noticed is the issue described previously had been fixed silently by the developpers. Indeed, the WebViewActivity is no more accessible from the outside, they removed the intent filters in the AndroidManifest.xml.
我注意到的第一件事是先前描述的问题已由开发人员静默修复。 实际上,WebViewActivity不再可以从外部访问,他们删除了AndroidManifest.xml中的意图过滤器。

To continue my analysis, I decided to use the app on a rooted device. When I tried, I directly received this message.
为了继续进行分析,我决定在有根设备上使用该应用程序。 尝试时,我直接收到此消息。

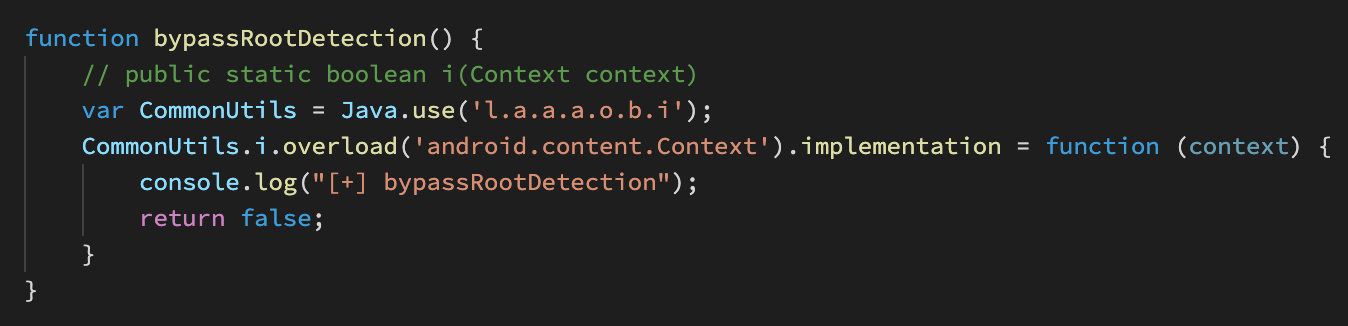
I decompiled the app and found where this root detection was implemented. In order to bypass it, I wrote a small function in my Frida script.
我对该应用程序进行了反编译,并发现在哪里实施了此根目录检测。 为了绕开它,我在Frida脚本中编写了一个小函数。
The next challenge was to be able to bypass the certificate pinning implemented in order to be able to monitor the network requests made by the app. Once I done that, I used the app and found an interesting feature
下一个挑战是能够绕过实现的证书固定,以便能够监视应用程序发出的网络请求。 完成此操作后,我使用了该应用程序,发现了一个有趣的功能

In the app, you have the ability to know how many people did a self assessment in your area. You can choose the radius of the area. It can be 500m, 1km, 2kms, 5kms or 10kms.
在应用程序中,您可以知道您所在地区有多少人进行了自我评估。 您可以选择区域的半径。 它可以是500m,1km,2kms,5kms或10kms。
When the user is clicking on one of the distance:- his location is sent: see the lat and lon parameters in the header- the radius choosen is sent: see the dist parameter in the url and the distance parameter in the header
当用户单击以下距离之一时:-发送其位置:请参见标头中的lat和lon参数-发送所选择的半径:请参见url中的dist参数和标头中的distance参数

The first thing I noticed is that this endpoint returns a lot of info:- Number of infected people- Number of unwell people- Number of people declared as bluetooth positive- Number of self assesment made around you- Number of people using the app around you
我注意到的第一件事是,此端点返回了很多信息:-受感染的人数-身体不适的人数-被宣布为蓝牙阳性的人数-围绕您进行自我评估的人数-使用您周围的应用程序的人数
Because I’m stupid, the 1st thing I tried was to modify the location to see if I was able to get information anywhere in India. The 2nd thing was to modify the radius to 100kms to see if I was able to get info with a radius which is not available in the app. As you can see in the previous screenshot, I set my location to Mumbai and set the radius to 100kms and it worked!
因为我很傻,所以我尝试的第一件事是修改位置,以查看我是否能够在印度的任何地方获取信息。 第二件事是将半径修改为100公里,以查看我是否能够获取应用程序中不可用的半径信息。 如您在上一个屏幕截图中所见,我将位置设置为孟买,并将半径设置为100kms,它确实起作用了!
What are the consequences?Thanks to this endpoint an attacker can know who is infected anywhere in India, in the area of his choice. I can know if my neighboor is sick for example. Sounds like a privacy issue for me…
后果是什么?借助此端点,攻击者可以在自己选择的区域中知道谁感染了印度的任何地方 。 例如,我可以知道邻居是否生病。 听起来对我来说是个隐私问题...
So I decided to play with it a little bit and checked who was infected in some specific places with a radius of 500 meters:- PMO office: {“infected”:0,”unwell”:5,”bluetoothPositive”:4,”success”:true,”selfAsses”:215,”usersNearBy”:1936}- Ministry of Defense: {“infected”:0,”unwell”:5,”bluetoothPositive”:11,”success”:true,”selfAsses”:123,”usersNearBy”:1375}- Indian Parliament: {“infected”:1,”unwell”:2,”bluetoothPositive”:17,”success”:true,”selfAsses”:225,”usersNearBy”:2338}- Indian Army Headquarters: {“infected”:0,”unwell”:2,”bluetoothPositive”:4,”success”:true,”selfAsses”:91,”usersNearBy”:1302}
因此,我决定稍微玩一下它,并检查谁在半径500米的某些特定位置感染了谁:-PMO办公室:{“感染”:0,“不适”:5,“蓝牙阳性”:4,”成功”:true,“ selfAsses”:215,“ usersNearBy”:1936}-国防部:{“感染”:0,“不适”:5,“蓝牙阳性”:11,“成功”:true,“ selfAsses” :123,“ usersNearBy”:1375}-印度议会:{“受感染”:1,“不适”:2,“ bluetoothPositive”:17,“成功”:true,“ selfAsses”:225,“ usersNearBy”:2338} -印度陆军总部:{“受感染”:0,“不适”:2,“蓝牙阳性”:4,“成功”:true,“自我评估”:91,“用户近乎”:1302}
揭露 (Disclosure)
49 minutes after my initial tweet, NIC and the Indian Cert contacted me. I sent them a small technical report.
在我的第一条鸣叫后49分钟,NIC和印度证书(Indian Cert)与我联系。 我给他们发送了一份小型技术报告。
Few hours after that they released an official statement.
此后几个小时,他们发表了官方声明。
To sum up they said “Nothing to see here, move on”.
总结起来,他们说:“没什么可看的,继续前进”。
My answer to them is:- As you saw in the article, it was totally possible to use a different radius than the 5 hardcoded values, so clearly they are lying on this point and they know that. They even admit that the default value is now 1km, so they did a change in production after my report- The funny thing is they also admit an user can get the data for multiple locations. Thanks to triangulation, an attacker can get with a meter precision the health status of someone.- Bulk calls are possible my man. I spent my day calling this endpoint and you know it too.
我对它们的回答是:正如您在文章中所看到的,完全有可能使用与5个硬编码值不同的半径,因此很明显,它们位于这一点上并且他们知道这一点。 他们甚至承认默认值现在为1公里,所以他们在我报告后进行了生产更改-有趣的是,他们还承认用户可以获取多个位置的数据。 多亏了三角剖分,攻击者才能以米的精度获得某人的健康状况。 我整天都在呼叫此端点,您也知道这一点。
I’m happy they quickly answered to my report and fixed some of the issues but seriously: stop lying, stop denying.
我很高兴他们Swift回答了我的报告,并修复了一些问题,但是很认真:停止说谎,停止否认。
And don’t forget folks: Hack the planet! 🤘
别忘了人们:砍死这个星球! 🤘
翻译自: https://medium.com/@fs0c131y/aarogya-setu-the-story-of-a-failure-3a190a18e34
setu






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








