rail_deviceid
So many things in the world would have never come into existence if there hadn’t been a problem that needed solving. This truth applies to everything, but boy, is it obvious in the world of computer science.
如果没有需要解决的问题, 那么世界上的许多事情将永远不会存在。 这个真理适用于所有事物,但是对于男孩来说,在计算机科学领域是显而易见的。
So, its a big “YES”, but I do think that it’s unique in one way: computer science’s innovations rely and build upon its own abstractions. But what leads to the need of Ciphering & Deciphering algorithms ??
因此,它是一个很大的“是”,但我确实认为它在某种程度上是独一无二的: 计算机科学的创新依赖并建立在其自身的抽象之上。 但是是什么导致需要加密和解密算法呢?
Have you ever wondered how companies securely store your passwords? Or how your credit card information is kept private when making online purchases?The answer is cryptography. The vast majority of internet sites now use some form of cryptography to ensure the privacy of its users. Even information such as emails from your Gmail account are encrypted as they float around in Google’s data centers.
您是否想过公司如何安全存储密码? 或在网上购物时如何将您的信用卡信息保密?答案是密码术 。 现在,绝大多数互联网站点都使用某种形式的加密技术来确保其用户的隐私。 甚至来自您Gmail帐户的电子邮件之类的信息也会在Google数据中心中浮动时被加密。
什么是密码学? (What is Cryptography ?)
Cryptography is a method of protecting information and communications through the use of codes, so that only those for whom the information is intended can read and process it.
密码术是一种通过使用代码来保护信息和通信的方法,因此,只有那些打算获取信息的人员才能阅读和处理信息。

In cryptography, Encryption is the process of translating plain text data, usually called plain text into something that appears to be random and meaningless, usually called cipher text. Decryption is the process of converting cipher text back to plain text.So, to decrypt the ciphered text, you need to have the same key that was used during encryption.
在密码术中, 加密是将纯文本数据(通常称为纯文本)转换为看似随机且毫无意义的东西(通常称为密文)的过程。 解密是将密文转换回纯文本的过程,因此,要解密密文,您需要使用与加密期间相同的密钥。
Here, we will be discussing about two such algorithms1) Hill Cipher Algorithm2) Rail Fence AlgorithmTo make our message strongly encrypted, we will encode our message twice, first encode it using Hill Cipher, and then pass it through rail fence cipher algorithm.
在这里,我们将讨论两个这样的算法:1)Hill Cipher算法2)Rail Fence算法为了使我们的消息得到高度加密,我们将对消息进行两次编码,首先使用Hill Cipher对其进行编码,然后将其通过Rail fence密码算法。
If this is your very first foray into cyber security, fear not — it’s mine, too!Let’s tackle it together — and try not to lose our sanity in the process.
如果这是您首次涉足网络安全,请不要担心-也是我的!让我们一起解决它-并在此过程中尽量不要失去理智。
挂载Hill密码算法 (Mounting the Hill Cipher Algorithm)
Hill Cipher is a polygraphic substitution cipher based on linear algebra. Each letter is represented by a number modulo 26. Often the simple scheme A = 0, B = 1, …, Z = 25 is used. Let’s see it step-wise:
Hill Cipher是基于线性代数的测谎替代密码。 每个字母都由一个以26为模的数字表示。通常使用简单的方案A = 0,B = 1,...,Z = 25。 让我们逐步来看一下:
Step 1: Convert your message or “plain text” into a column vector & your key into a n*n matrix.
步骤1:将您的消息或“纯文本”转换为列向量,并将密钥转换为* n矩阵。
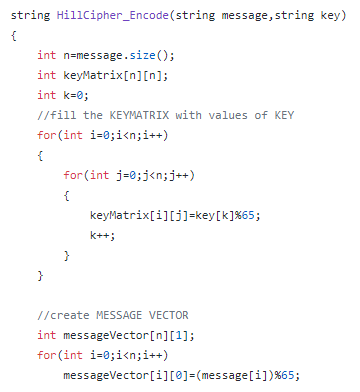
Step 2: Perform matrix multiplication of (Key Matrix * Message Vector) modulo 26 and store it in a string.
步骤2:对(Key Matrix * Message Vector)模26进行矩阵乘法,并将其存储在字符串中。
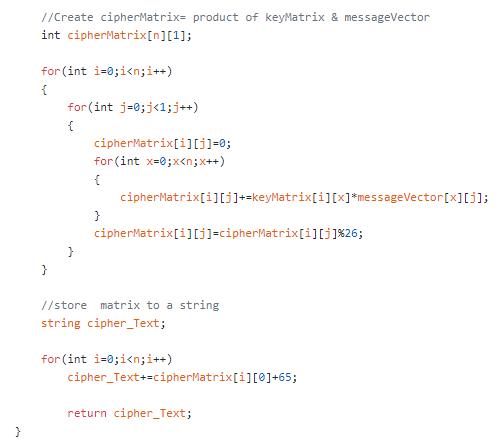
now we will pass this ciphered text as an input to the rail fence cipher algorithm.
现在,我们将把这些密文作为铁路围栏密文算法的输入。
越过围栏密码算法 (Trailing over the Rail Fence Cipher Algorithm)
The rail fence cipher (also called a zigzag cipher) is a form of transposition cipher. It derives its name from the way in which it is encoded.
铁路围网密码(也称为之字形密码)是一种换位密码。 它的名称来自其编码方式。
- In the rail fence cipher, the plain-text is written downwards and diagonally on successive rails of an imaginary fence. 在围栏密码中,纯文本向下且对角地写在假想围栏的连续轨道上。
- When we reach the bottom rail, we traverse upwards moving diagonally, after reaching the top rail, the direction is changed again. Thus the alphabets of the message are written in a zig-zag manner. 当我们到达底部导轨时,我们沿对角线向上移动,到达顶部导轨后,方向再次改变。 因此,消息的字母以之字形方式书写。
- After each alphabet has been written, the individual rows are combined to obtain the cipher-text. 在写完每个字母之后,将各个行合并以获得密文。
Step 1: Take an integer key as an input and create a matrix with:number of rows = keynumber of columns = size of message (text that is to be encrypted)Store the message in this matrix in a zig-zag manner.
步骤1:以整数键作为输入并创建一个矩阵,其中:行数=键数列数=消息大小(要加密的文本)以Z字形方式将消息存储在此矩阵中。
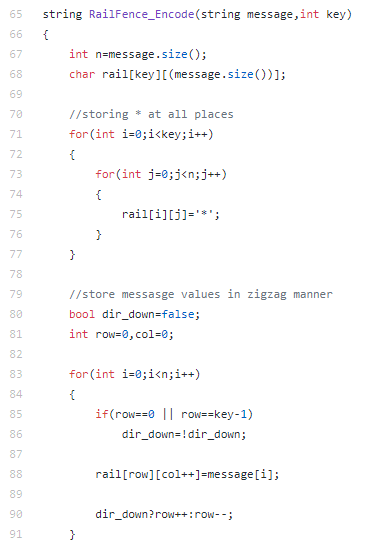
An important note: keep in mind to take the value of key less than the size of message, otherwise the encoded string will be same as input string.
重要说明:请记住,键的值应小于消息的大小,否则编码后的字符串将与输入字符串相同。
Step 2 : Traverse the matrix in row wise manner and if the element is not equal to “ * “, then store it in a string.
步骤2:以行方式遍历矩阵,如果元素不等于“ *”,则将其存储在字符串中。
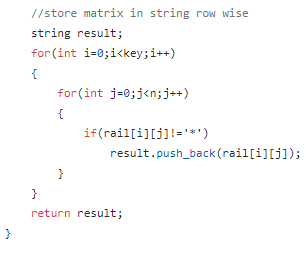
This string is the encoded string after rail fence encoding. Now it is send to the receiver, and he has to decode it.First decrypt using Rail Fence Decipher algorithm, then Hill Decipher algorithm.
该字符串是围栏编码后的编码字符串。 现在将其发送给接收者,他必须对其进行解码。首先使用Rail Fence Decipher算法解密,然后使用Hill Decipher算法解密。
通过围栏解密算法追溯 (Tracing back through Rail Fence Decipher Algorithm)
As we’ve seen earlier, the number of columns in rail fence cipher remains equal to the length of plain-text message. And the key corresponds to the number of rails.
正如我们之前所看到的,围栏密码中的列数保持等于纯文本消息的长度。 并且键对应于滑轨的数量。
- Hence, rail matrix can be constructed accordingly. Once we’ve got the matrix we can figure-out the spots where texts should be placed (using the same way of moving diagonally up and down alternatively ). 因此,可以相应地构造轨道矩阵。 一旦有了矩阵,我们就可以找出应该放置文本的位置(使用相同的方法,即沿对角线上下交替移动)。
- Then, we fill the cipher-text row wise. After filling it, we traverse the matrix in zig-zag manner to obtain the original text. 然后,我们按行填充密文行。 填充后,我们以之字形方式遍历矩阵以获得原始文本。
Step 1 : First create a character array, similar to, that we have created in its ciphering algorithm. Then store “ * ” in zig-zag manner in this matrix.
步骤1:首先创建一个字符数组,类似于我们在其加密算法中创建的字符数组。 然后以锯齿形的方式在该矩阵中存储“ *”。
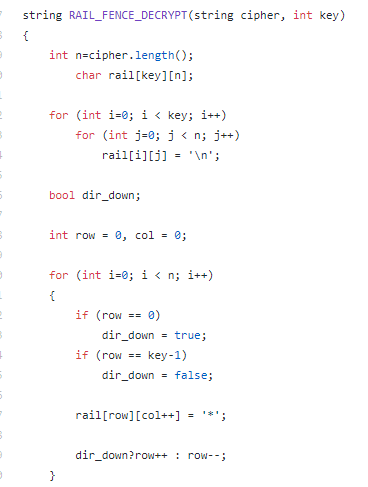
Step 2 : Now traverse this matrix row wise, and if element == “ * “ replace it with input string [index++]. After this process, again traverse this matrix in zig-zag manner and store the elements in a string.
第2步:现在逐行遍历此矩阵,如果element ==“ *”替换为输入字符串[index ++]。 在此过程之后,再次以之字形方式遍历此矩阵并将元素存储在字符串中。
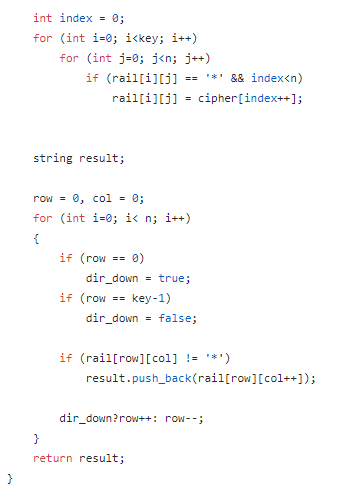
This string is the decoded string after Rail Decipher algorithm, now pass it to Hill Decipher algorithm to get our original message.
该字符串是Rail Decipher算法之后的解码字符串,现在将其传递给Hill Decipher算法以获取原始消息。
通过希尔解密算法下山 (Moving downhill through Hill Decipher Algorithm)
The process of decrypting it is almost similar to its encryption process. Difference being, we turn the cipher text back into a vector, then simply multiply by the inverse matrix of the key matrix.
解密过程几乎与加密过程相似。 区别在于,我们将密文重新转换为向量,然后简单地乘以密钥矩阵的逆矩阵。
Step 1 : We will have to use the same key, that we used in the Hill Ciphering algorithm (actually that’s the main security advantage, that prevent it from going under the wrong hands). Create a key matrix, and calculate its inverse.
第1步:我们将必须使用与Hill Ciphering算法中使用的密钥相同的方法(实际上,这是主要的安全优势,可以防止密钥被错误使用)。 创建一个密钥矩阵,然后计算其逆矩阵。
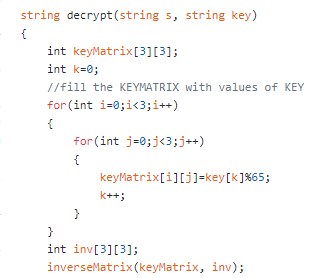
InverseMatrix( ) can be accessed from the GitHub link, I have mentioned at the end of this blog.
我已经在本博客结尾提到了GitHub链接,可以访问InverseMatrix()。
Step 2 : Perform matrix multiplication of (Inverse of key Matrix * Input string) modulo 26 and store the final vector in a string.
步骤2:对(键矩阵的逆*输入字符串)取模26的矩阵乘法,并将最终向量存储在字符串中。
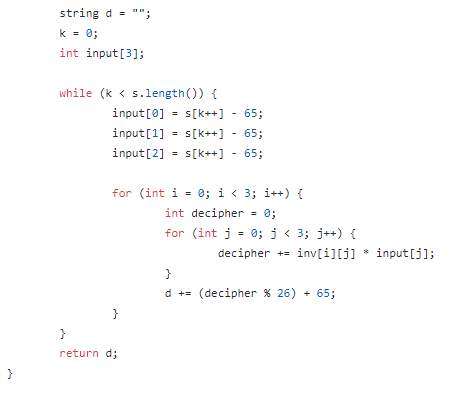
An important note: Since, inverse of every matrix is not possible, so keep in mind to choose the key such that its matrix do not have the determinant as zero. Otherwise its decryption won’t be possible.
重要说明:由于不可能对每个矩阵求逆,因此请记住选择键,以使其矩阵的行列式不为零。 否则将无法解密。
This string is the final decoded string after Hill Decipher algorithm and it should be same as our original string.
该字符串是Hill Decipher算法之后的最终解码字符串,应与我们的原始字符串相同。
输出窗口 (Output window)
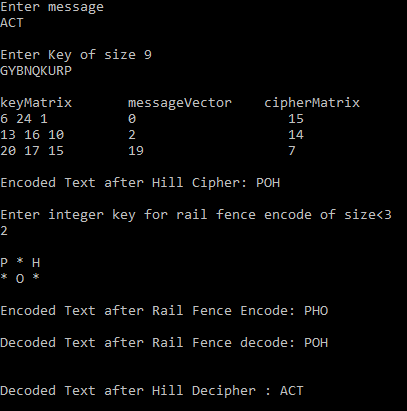
Ciphering process :Here our original message is “ ACT ” and its key is “ GYBNQKURP ” , It is passed through Hill Cipher Algorithm and we get encoded output as “ POH “.Now “POH” is passed as an input to Rail Fence Cipher algorithm with key = 2, and we get the encoded output as “ PHO “.
加密过程:这里的原始消息是“ ACT”,其密钥是“ GYBNQKURP”,它通过Hill密码算法传递,并得到编码后的输出为“ POH”。现在将“ POH”作为输入传递给Rail Fence密码算法键= 2,我们得到的编码输出为“ PHO”。
Deciphering process :Pass “ PHO “ as an input to Rail Fence Decipher algorithm with same key = 2 and the output we get is “ POH “. Now it is used as an input in Hill Decipher algorithm with key = “ GYBNQKURP “ and the final decrypted output we get is “ ACT “, which is same as the input message.
解密过程:将 “ PHO”作为输入输入给具有相同密钥= 2的Rail Fence Decipher算法,得到的输出为“ POH”。 现在,它被用作Hill Decipher算法的输入,其密钥=“ GYBNQKURP”,而最终得到的解密输出为“ ACT”,与输入消息相同。
资源资源 (Resources)
You can access the whole working code of both Encryption and Decryption using Hill Cipher algorithm & Rail Fence Cipher algorithm from this GitHub Repository : Link
您可以从此GitHub存储库中使用Hill Cipher算法和Rail Fence Cipher算法访问加密和解密的整个工作代码: 链接
翻译自: https://medium.com/swlh/encryption-decryption-using-hill-rail-fence-algorithm-96f285309cb5
rail_deviceid




















 479
479











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








