web应用程序和web网站
环境变量变得疯狂:数据泄露结果 (Environment Variables Gone Wild: Data Breach Results)
Information disclosure is a type of vulnerability in which a system inadvertently exposes confidential information. This post walks through an example of this flaw by looking at how environment variables can be misunderstood and misused in web applications. This post will revisit the best practices and conclude with actionable advice for developers.
我载文信息公开是一种类型的漏洞,其中一个系统无意中公开机密信息的。 这篇文章通过研究如何在Web应用程序中误解和滥用环境变量来介绍该漏洞的示例。 这篇文章将回顾最佳实践,并为开发人员提供可行的建议。
Leaking Secrets describes an information disclosure flaw in which an application exposes sensitive credentials or API keys to an adversary. The OWASP Top Ten 2017 categorizes this flaw as “Sensitive Data Exposure”. This post will discuss how this can be exploited with a case study of a vulnerable and misconfigured middleware gem running on a rails application. These types of issues can lead to a data breach for an enterprise, resulting in significant financial and reputation harm. These issues are observed frequently, as Infrastructure as Code (IaC) and Cloud speed enable DevOps personnel to quickly spin up new web applications and environments unchecked. If you are a developer working with Rails, you need to be aware of these issues. If you’re a pentester working with web applications, you’ll find this information useful and (my hope) be better able to protect your clients.
大号 eaking秘密描述了一种信息披露的缺陷,其中一个应用程序暴露敏感凭证或API键对手。 OWASP 2017十佳分类将该漏洞归类为“ 敏感数据暴露 ”。 这篇文章将讨论如何通过在Rails应用程序上运行的易受攻击且配置错误的中间件gem进行案例研究。 这些类型的问题可能导致企业数据泄露,从而严重损害财务和声誉。 经常观察到这些问题,因为基础架构即代码(IaC)和云计算速度使DevOps人员能够快速启动不受限制的新Web应用程序和环境。 如果您是使用Rails的开发人员,则需要注意这些问题。 如果您是使用Web应用程序的上风,您会发现此信息很有用,并且(我希望)可以更好地保护您的客户。
Exposing secrets over the public Internet in your web application is exactly what you never want to do. To the Rails developers reading this, a tip of the hat to the Rack-mini-profiler.
在Web应用程序中通过公用Internet公开秘密正是您永远都不想做的。 对于阅读此内容的Rails开发人员来说,Rack-mini-profiler只是一顶帽子。
机架微型分析器:好,坏,丑 (Rack-Mini-Profiler: The Good, Bad, Ugly)
Rack-mini-profiler is a middleware gem used by Rack developers as a performance tool to improve visibility and speed in Rack-based web applications. The tool has value to the developer community and is highly regarded, as shown from this enthusiast:
[R ACK-迷你分析器是使用机架开发商作为性能工具,以提高基于Rack的Web应用程序的可见性和速度的中间件宝石。 如该发烧友所示,该工具对开发人员社区具有价值并受到高度评价:
rack-mini-profileris a a performance tool for Rack applications, maintained by the talented @samsaffron. rack-mini-profiler provides an entire suite of tools for measuring the performance of Rack-enabled web applications, including detailed drill downs on SQL queries, server response times (with a breakdown for each template and partial), incredibly detailed millisecond-by-millisecond breakdowns of execution times with the incredibleflamegraphfeature, and will even help you track down memory leaks with its excellent garbage collection features. I wouldn’t hesitate to say thatrack-mini-profileris my favorite and most important tool for developing fast Ruby webapps.
rack-mini-profiler是用于Rack应用程序的性能工具,由才华横溢的@samsaffron维护。 rack-mini-profiler提供了一整套工具,用于评估启用了Rack的Web应用程序的性能,包括对SQL查询的详细钻取,服务器响应时间(每个模板和部分数据都有细分),难以置信的详尽的毫秒级-令人难以置信的flamegraph功能可实现毫秒级的执行时间故障,甚至还可以凭借其出色的垃圾收集功能帮助您跟踪内存泄漏。 我会毫不犹豫地说,rack-mini-profiler是我最喜欢的也是最重要的用于开发快速Ruby Webapp的工具。
I recently discovered a deployment of a Rails application using Rack-mini-profiler in the wild, and it was eye-opening to see the security issues. I want to be clear that I’m not saying the gem has an inherent vulnerability; rather, it is a problem with how the middleware gem can be used or configured without proper security protections. So I set out to better understand how this could happen and the actual vulnerabilities observed. The culmination of this effort is an open-source project, “Hammer.” Hammer is an example of a vulnerable Rails application deployment that uses Rack-mini-profiler to leak API keys and sensitive information. It is vulnerable in the exact same way as a real-world application observed in the wild. It’s also a skeleton app that can be used to fork and experiment with sensitive variables in a safe way. In the process of building this tool I’ve learned a few things and want to share the lessons learned with the developer and InfoSec communities.
我最近发现了在野外使用Rack-mini-profiler部署Rails应用程序的过程,看到安全问题令人大开眼界。 我要明确一点,我并不是说该宝石具有固有的漏洞; 相反,在没有适当的安全保护的情况下如何使用或配置中间件gem是一个问题。 因此,我着手更好地了解这是如何发生的以及观察到的实际漏洞。 这项工作的高潮是一个开源项目“ Hammer”。 Hammer是一个易受攻击的Rails应用程序部署的示例,该应用程序使用Rack-mini-profiler泄漏API密钥和敏感信息。 它与在野外观察到的实际应用程序完全相同,容易受到攻击。 它也是一个骨架应用程序,可用于安全地对敏感变量进行分叉和实验。 在构建此工具的过程中,我学到了一些东西,并希望与开发人员和InfoSec社区分享所学到的教训。

The Hammer Github site is here.
Hammer Github网站在这里 。
A light Hammer introduction is here.
这里有一个简短的Hammer介绍。
Let’s do a quick tour of the capabilities of the Middleware that offers so many benefits to a developer but at the same time makes it an attractive attack target. You can follow along at the demo application for Hammer: https://preprod.rtcfingroup.com.
L' s快速浏览了中间件的功能,该功能为开发人员带来了很多好处,但同时又使其成为有吸引力的攻击目标。 您可以按照Hammer的演示应用程序进行操作: https : //preprod.rtcfingroup.com 。
In the top left-hand corner, an “HTML Speed Badge” is rendered by installing this performance middleware gem. When the tool is installed the HTML speed badge can be used to profile any given page served by the Rails application.
在左上角的角落,一个“HTML速度徽章”是通过安装这样的表现中间件宝石呈现。 安装该工具后,可以使用HTML速度标志来描述Rails应用程序提供的任何给定页面。

Let’s navigate over the URL where the sensitive users are publicly accessible — https://preprod.rtcfingroup.com/users/. Note that these aren’t real users. They are randomly generated from a script included with the tool that simulates users. Take a look at the HTML speed badge in the top left corner and see how it has rendered the amount of time for the page to render.
请浏览可公开访问敏感用户的URL — https://preprod.rtcfingroup.com/users/。 请注意,这些不是真正的用户。 它们是从模拟用户的工具附带的脚本中随机生成的。 看一下左上角HTML速度标志,看看它如何呈现页面呈现时间。

Expanding the speed badge at /users/ shows the time in milliseconds spent rendering each page. Note the interesting SQL query for rendering users/index. Rack-mini-profiler creates a link that you can click on to get more information. Let’s take a look.
Ëxpanding速度徽章在/用户/节目中度过呈现每个页面毫秒的时间。 请注意用于呈现用户/索引的有趣SQL查询。 Rack-mini-profiler创建一个链接,您可以单击该链接以获取更多信息。 让我们来看看。

Below, you can see that Rack-mini-profiler displays detailed call stack query information. You can see the SQL query, file, and precise line that is rendering the users. This is great information for a developer who is trying to improve performance and identify bottlenecks in the application. But from an attacker perspective, this gleans valuable information such as SQL queries that could enable other vulnerabilities to be exploited. It is considered a standard security practice to never expose SQL queries client side. When I first saw this in the wild, I couldn’t believe what I was seeing. Rack-mini-profiler’s website states that the tool can be used to profile applications in development and production. That is why it is so important to ensure that exposing the SQL call stack query aligns with your organizational security policy for application development. When I first saw this, I didn’t know that there would be something far more interesting. Read below.
乙 elow,你可以看到,机架迷你探查显示详细的调用堆栈查询信息。 您可以看到正在呈现用户SQL查询,文件和精确行。 对于试图改善性能并确定应用程序瓶颈的开发人员来说,这是非常有用的信息。 但是从攻击者的角度来看,这可以收集有价值的信息,例如可以使其他漏洞得以利用SQL查询。 从不公开SQL查询客户端被视为一种标准的安全措施。 当我第一次在野外看到它时,我简直不敢相信自己所看到的。 Rack-mini-profiler的网站指出,该工具可用于在开发和生产中对应用程序进行概要分析。 这就是为什么确保公开SQL调用堆栈查询与组织安全性策略以进行应用程序开发非常重要的原因。 当我第一次看到这个时,我不知道会有什么更有趣的事情。 参见下文。

Rack-mini-profiler gem uses the “Pretty Print” Ruby class (pp) that can be found at the default URL by appending ?pp=help. It has a lot of nice features for developers such as memory profiling and garbage collection. The most interesting from a security perspective is pretty printing env.
[R ACK-迷你探查宝石使用“漂亮打印”可以在默认的网址通过追加?PP =帮助找到Ruby类(PP)。 它为开发人员提供了许多不错的功能,例如内存分析和垃圾回收。 从安全角度来看,最有趣的是漂亮的env打印。

№1:倾销“ env” (№1: Dumping “env”)
This env pretty print feature dumps all environment variables that are being passed to the Rails application. This includes the Rack Environment as shown below.
Ť他的ENV漂亮的打印功能转储正在传递到Rails应用程序的所有环境变量。 这包括如下所示的机架环境 。
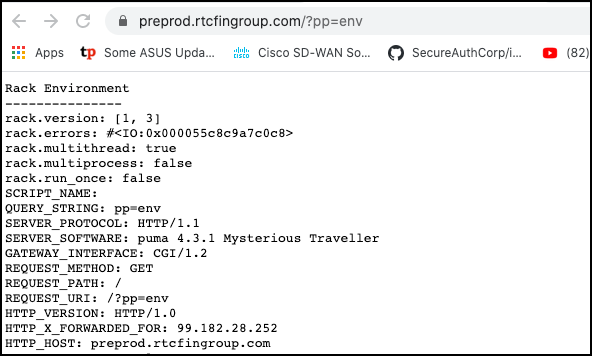
Taking a look at the Rack-mini-profiler source code for the profiler.rb, the code shows that it first dumps env by iterating through and printing the local variables stored in env. This correlates with the output shown above starting with “Rack Environment.”
Ť亚庆一看为所述机架微型分析器源代码profiler.rb ,代码显示,它首先通过迭代和打印存储在ENV局部变量转储ENV。 这与上面显示的以“ Rack Environment ”开始的输出相关。
№2:倾销“ ENV” (№2: Dumping “ENV”)
Second, it dumps the ENV constant by iterating through and printing the contents of this hash.
其次,它通过遍历并打印此哈希的内容来转储ENV常数。

The screenshot below shows the start of dumping ENV constant hash from the sample vulnerable application, correlating with the second part of code starting with ENV.each do.
吨他下面的截图示出了从样品中易受攻击的应用程序倾倒ENV恒定散列,用代码的第二部分相关联以开始的开始ENV.each do 。

In this example, the Amazon S3 API keys have been stored in ENV, leaking them out to the public. This shows how dangerous it can be storing API secrets and other sensitive credentials within environment variables stored in the ENV constant hash. We’ll talk a little more about how this happens below.
在此示例中,Amazon S3 API密钥已存储在ENV中,将其泄露给公众。 这表明将API机密和其他敏感凭据存储在ENV常量哈希中存储的环境变量中是多么危险。 我们将在下面详细讨论这种情况。
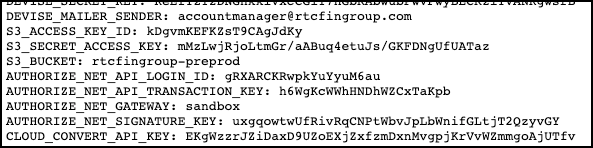
Taking this a step further, the sample application leaks a variety of different cloud API and secrets, including Facebook, Twitter, LinkedIn, and Google.
Ť亚庆这一步,将样品应用程序泄漏的各种不同的云API和秘密,包括Facebook,Twitter,LinkedIn,和谷歌。

Ruby中的ENV和ENV是什么? (What are ENV and env in Ruby?)
ENV is a hash-like class that Ruby uses to expose environment variables to our application. For example, PATH or HOME can be made available to our rails application. Rack-mini-profiler doesn’t have to do much to dump ENV because the constant is exposed upon the application launch. It is up to the developer to properly store, load, and secure ENV. ENV traditionally correlates with an environment variable and is more global than env. Each of these variables is listed as key/value pairs and they are usually used to share configuration.
E NV是类似于哈希的类,Ruby使用它来将环境变量公开给我们的应用程序。 例如,可以使PATH或HOME对我们的rails应用程序可用。 Rack-mini-profiler不需要做太多的工作来转储ENV,因为在应用程序启动时会公开该常量。 开发人员需要适当地存储,加载和保护ENV。 传统上,ENV与环境变量相关,并且比env更具全局性。 这些变量中的每一个都列为键/值对,它们通常用于共享配置。
All Rack applications such as Rails take a single argument which is a hash called env. The env is passed to the Rails application and stores information such as HTTP header, request, and server configuration. In comparison to ENV, env is more local to Rails.
作为导轨采取单一参数,它是一个被称为包膜散列一 ll机架等应用。 该环境被传递到Rails应用程序并存储诸如HTTP标头,请求和服务器配置之类的信息。 与ENV相比, env在Rails中更本地。
漏洞 (The Vulnerability)
Environment variables should never be used to store sensitive configuration information such as credentials and API keys. If they must be used, your security program should accept this risk, document it within your risk register, and provide appropriate security controls to mitigate the risk.
Ënvironment变量不应该被用于敏感的配置信息存储诸如证书和API密钥。 如果必须使用它们,您的安全程序应接受此风险,将其记录在风险登记册中,并提供适当的安全控制措施以减轻风险。
Much has been said about environment variables and their proper usage. The Twelve-Factor App manifesto states that environment variables should be used to store configuration elements such as credentials to external services such as Amazon S3 or Twitter.
中号 UCH已经说过环境变量及其正确使用。 十二要素应用程序声明声明应使用环境变量来存储配置元素(例如,凭证)到外部服务(例如Amazon S3或Twitter)。

I do not agree with this. Following this practice will increase the business risk to your company.
我不同意这一点。 遵循这种做法会增加您公司的业务风险。
The example application shows how easy it can be for developers to make a mistake and inadvertently expose sensitive API keys such as AWS that allow data breach. This application was created to mimic a production environment found in the wild that was secured after enumerating the issues described above. It is the case that Rails developers can use different environments such as production, QA, or development. The Rack-mini-profiler is designed to be used in any of these environments. The exposed environment variables, if containing sensitive secrets running in development environments, can give attackers credentials that allow unauthorized data access, information leakage, and privilege escalation into production. There is a good place for environment variables to store configuration elements. They should just never be used for sensitive secrets.
吨他示例应用程序显示它可以多么容易为开发者犯了一个错误,并在无意中暴露敏感API密钥,如AWS,使数据泄露。 创建该应用程序的目的是为了模仿在枚举上述问题后得到保证的野外生产环境。 Rails开发人员可以使用不同的环境,例如生产,QA或开发。 Rack-mini-profiler设计用于这些环境中的任何一种。 暴露的环境变量(如果包含在开发环境中运行的敏感机密)可以为攻击者提供凭据,允许未经授权的数据访问,信息泄漏以及特权升级到生产环境 。 环境变量是存储配置元素的好地方。 绝对不要将它们用作敏感机密。
This example application uses the Dotenv rails gem to load environment variables from .env This example app uses .env.local to load all of the populated environment variables contained in the file into the ENV constant that is dumped by Rack-mini-profiler. Take a look at the configuration that can also be seen in the Github repo for Hammer:
Ť他的示例应用程序使用的Dotenv轨宝石负载环境变量从.env此示例应用程序使用.env.local加载所有的人口环境变量中包含的文件到由机架迷你探查甩ENV不断英寸 看一下在Hamth的Github存储库中也可以看到的配置:

Beyond the risk of exposing sensitive environment variables through Middleware, there are a few other solid reasons why a developer should be aware of the risks inherent in this practice. This list below summarizes some of these risks from Diogo Monica :
乙 eyond通过中间件暴露敏感的环境变量的风险,还有其他一些固体原因,开发人员应该意识到风险的这种做法所固有的。 以下列表总结了Diogo Monica的一些风险:
The risk of copying unencrypted environment variables files such as
.env.localinto central Git repositories by not properly using the .gitignore file. The risk of tribal knowledge, when new developers who didn’t set up the system don’t take the proper care in safeguarding these files containing environmental variables. Secrets are copied to a different system and exposed.如果未正确使用.gitignore文件,则可能
.env.local未加密的环境变量文件(例如.env.local到中央Git存储库中。 如果没有设置系统的新开发人员在保护包含环境变量的这些文件时未采取适当的措施,则存在部落知识的风险。 机密将复制到其他系统并公开。- An application can grab the whole environment and print it out for debugging or error-reporting. Secrets can get leaked if they are not properly sanitized before leaving your environment. 应用程序可以获取整个环境并将其打印出来以进行调试或错误报告。 如果机密信息在离开您的环境之前没有经过适当的清理,则可能会泄露。
- Environment variables are passed to child processes, which can lead to unintended access (i.e., a 3rd-party tool has access to your environment). 环境变量将传递给子进程,这可能导致意外访问(即,第三方工具可以访问您的环境)。
- When applications crash, it is common to store the environment variables in log files for debugging. This increases the risk of plain text secrets on disk. 当应用程序崩溃时,通常将环境变量存储在日志文件中以进行调试。 这增加了磁盘上纯文本秘密的风险。
在ENV和Bash环境中进行实验 (Experimenting with ENV and Bash Environment)
Before we jump into playing with some examples of ENV and environment variables, let’s review some laws of Ruby Environment variables. Honeybadger.io gives a fantastic tutorial on this and I’ll summarize:
在开始研究ENV和环境变量的一些示例之前,让我们回顾一下Ruby环境变量的一些定律。 Honeybadger.io为此提供了一个很棒的教程,我将总结一下:
- Every process has its own set of environment variables. 每个进程都有自己的一组环境变量。
- Environment variables die with their process. 环境变量随其过程而消失。
- A process inherits its environment variables from its parent. 进程从其父级继承其环境变量。
- Changes to the environment don’t synch between processes. 对环境的更改不会在进程之间同步。
- Your shell is just a UI for the environment variable system. 您的外壳程序只是环境变量系统的UI。
This example walks through the Hammer environment, inside the home directory of the Rails application.
该示例遍历了Rails应用程序主目录中的Hammer环境。
Change into the working home directory of the Rails Hammer application:
进入Rails Hammer应用程序的工作主目录:
$ cd /home/<username>/hammerGrep for SECRET in the .env.local to see some of the environment variables we want to play with.
.env.local中的 SECRET的 Grep,以查看我们要使用的一些环境变量。
$ grep SECRET .env.localYou’ll see several of the crown jewel API keys. Now print your Bash shell environment variables with env. You’ll see all of the standard environment variables such as $HOME and $PATH. Verify with env | grep SECRET that those sensitive variables are not currently loaded in your Bash environment.
您将看到几个王冠珠宝API密钥。 现在,使用env打印您的Bash shell环境变量。 您将看到所有标准环境变量,例如$ HOME和$ PATH。 与env | grep SECRET验证env | grep SECRET env | grep SECRET说,那些敏感变量当前未在您的Bash环境中加载。

Run the Interactive Ruby Tool (irb) and we’ll see what happens. By default, irb will not see any of the sensitive environment variables exposed by ENV. This is because we need to use the Rails ‘dotenv’ gem to load the variables from an .env file. This shows that by default a Rails application inherits the environment variables of its parent process (the Bash shell) into ENV constant when a Ruby application is instantiated. But we need to specifically load extra environment variables into ENV hash constant in a special way, as those variables are not available by default. You’ll be able to see $PATH and $HOME but not any of the others.
运行Interactive Ruby Tool( irb ),我们将看到发生了什么。 默认情况下, irb将看不到ENV暴露的任何敏感环境变量。 这是因为我们需要使用Rails的“ dotenv ” gem从.env文件中加载变量。 这表明在默认情况下,实例化Ruby应用程序时,Rails应用程序会将其父进程(Bash shell)的环境变量继承为ENV常量。 但是我们需要以特殊方式将额外的环境变量专门加载到ENV哈希常量中,因为默认情况下这些变量不可用。 您将看到$ PATH和$ HOME,但看不到其他任何一个。
$ irb
> ENV
> ENV['PATH']
> ENV['S3_SECRET_ACCESS_KEY']

Instruct irb to use the dotenv gem to load the environment variables from the .env.local file. This command will load the environment variables into ENV, making them available to our irb ruby environment.
指示irb使用dotenv gem从.env.local文件中加载环境变量。 此命令会将环境变量加载到ENV中,使它们可用于我们的irb ruby环境。
> require 'dotenv';Dotenv.load('.env.local')
> require 'dotenv';Dotenv.load('.env.local')
Notice that all of the beautiful things are now available, the sensitive crown jewel API keys!
请注意,现在所有美丽的东西都可用了,灵敏的皇冠珠宝API密钥!

Verify that you have access to a couple of these beautiful, sensitive ENV things in your irb terminal!
验证您是否可以在irb终端中访问其中的一些美观,敏感的ENV设备!
> ENV['S3_ACCESS_KEY_ID']
> ENV['S3_SECRET_ACCESS_KEY']
Next, open up a new shell. Launch irb and try to list the sensitive environment variables stored in ENV.
接下来,打开一个新的外壳。 启动irb并尝试列出存储在ENV中的敏感环境变量。

Note that in the second shell’s irb session, no sensitive environment variables are listed. This is because of the way environment variables work. Every process has its own set of environment variables that are not automatically synced between processes.
请注意,在第二个外壳程序的irb会话中,没有列出敏感的环境变量。 这是因为环境变量的工作方式。 每个进程都有自己的环境变量集,这些变量不会在进程之间自动同步。
Now to experiment with exporting these variables. If you put export in front of the syntax of the variables named in .env.local, and source the file, magic happens. This converts the local shell variables into environment variables available to ENV. Which is then available to any child Rails process instantiated from that bash shell. The hammer app includes a sample exported variable file for the purpose of playing with sensitive variables in a safe way - .env.local.exported . Let’s give this a try.
现在尝试导出这些变量。 如果将export放在.env.local命名的变量的语法前面,并提供文件源, .env.local 发生魔术 。 这会将本地Shell变量转换为ENV可用的环境变量。 然后从该bash shell实例化的任何子Rails进程都可以使用它。 .env.local.exported应用程序包括一个示例导出的变量文件,目的是以安全的方式播放敏感变量.env.local.exported 。 让我们尝试一下。
In the second shell, exit the irb session and type the source command. Then run env to list the environment variables in the bash shell:
在第二个Shell中,退出irb会话并键入source命令。 然后运行env在bash shell中列出环境变量:
$ source .env.local.exported
$ env | grep SECRET
Now in the second shell, re-launch irb and fetch the sensitive ENV variables.
现在,在第二个shell中,重新启动irb并获取敏感的ENV变量。
$ irb
> ENV['S3_ACCESS_KEY_ID']
> ENV['S3_SECRET_ACCESS_KEY']
Amazing! You didn’t have to call Dotenv gem to automatically load into ENV. This shows you what Dotenv gem is doing — essentially sourcing the variables from the .env file when the environment is bootstrapped and loading them into ENV. ENV is then dumped via the Rack-mini-profiler Pretty Printer (pp) ruby class.
惊人! 您不必调用Dotenv gem即可自动加载到ENV中。 这向您展示了Dotenv gem在做什么—从本质上讲,当引导环境时,从.env文件中获取变量并将其加载到ENV中。 然后,ENV通过Rack-mini-profiler Pretty Printer(pp)Ruby类倾倒。
In this example, we ended up sourcing the exported variables to our bash shell. Once we exit the shell, the environment variables are not available to the next launched bash shell. If a developer were to add the commands to a shell init script such as .bashrc, this would persist these secrets to all users of the system in cleartext. This is another reason why this practice should be avoided.
在此示例中,我们最终将导出的变量采购到我们的bash shell中。 一旦退出shell,环境变量将无法用于下一个启动的bash shell。 如果开发人员将命令添加到Shell初始化脚本(如.bashrc)中 ,则这些秘密将以明文形式保留给系统的所有用户。 这是应避免这种做法的另一个原因。
存储秘密的方法摘要 (Summary of Methods to Store Secrets)
Storing Secrets in Plaintext: Use Rails gem methods such as Dotenv or Figaro to store secrets in the environment, and access them through loading ENV. Other methods include rbenv-vars plugin and direnv. These are popular methods but developers should consider better security.
以纯 文本格式 存储秘密:使用Dotenv或Figaro等Rails gem方法将秘密存储在环境中,并通过加载ENV来访问它们。 其他方法包括rbenv-vars插件和direnv 。 这些是流行的方法,但是开发人员应考虑更好的安全性。
SaaS Secrets Management Service: Use a service such as Vault, AWS Secrets Manager, and many others to synchronize and manage secrets within your app. This is a better approach than storing the secrets in plaintext, but keep in mind that you have to protect a super-secret SaaS API key that guards all of your secrets.
SaaS秘密管理服务 :使用Vault , AWS Secrets Manager等服务在您的应用程序中同步和管理秘密。 与以纯文本形式存储密钥相比,这是一种更好的方法,但是请记住,您必须保护保护所有密钥的超级秘密SaaS API密钥。
Rails Encrypted Secrets: Starting with Rails 5.1, you can use encrypted secrets to provide better protection to your app credentials. They can be accessed with a special variable other than ENV key/value hash. Here is a good overview, and starting with Rails 6, you can do multi-environment credentials management. This is a more secure way than the first method and similar to the second one. This should keep the master encryption key on your Rails system instead of synchronizing it with a cloud SaaS.
Rails的加密机密:从Rails 5.1开始,您可以使用加密的机密为您的应用程序凭据提供更好的保护。 可以使用除ENV键/值哈希以外的特殊变量来访问它们。 这是一个很好的概述 ,从Rails 6开始,您可以进行多环境凭据管理。 这是比第一种方法更安全的方法,与第二种方法类似。 这应将主加密密钥保留在Rails系统上,而不是与云SaaS同步。
推荐建议 (Recommendations)
Here are some recommendations for risk mitigation. These are meant to provide ideas and should be aligned with your DevOps processes.
以下是一些缓解风险的建议。 这些旨在提供想法,并应与您的DevOps流程保持一致。
- Remove the rack-mini-profiler gem on all systems connected to the public Internet. 删除连接到公共Internet的所有系统上的rack-mini-profiler gem。
- On systems requiring Rack-mini-profiler with public Internet access: Implement strong access control by whitelisting/firewalling IP addresses to only allow developer workstations to access the web application. 在需要具有公共Internet访问的Rack-mini-profiler的系统上:通过将IP地址列入白名单/防火墙来实施强大的访问控制,以仅允许开发人员工作站访问Web应用程序。
Use the RackMiniProfiler access control to authorize and whitelist requests. RackMiniProfiler has an authorization_mode to whitelist in production. Reference the Access control in non-development environments section of the Readme.
使用RackMiniProfiler访问控制来授权和白名单请求。 RackMiniProfiler具有一个authorization_mode可以在生产中将其列入白名单。 请参阅自述文件的“ 非开发环境中的访问控制”部分。
- Use Encrypted Secrets and avoid using the environment variables with ENV to store sensitive credentials. The best method to perform this locally is Rails Encrypted Secrets. This will avoid loading sensitive variables into ENV where the risk increases that they can be inadvertently exposed. 使用“加密的机密”,并避免将环境变量与ENV一起使用来存储敏感凭据。 在本地执行此操作的最佳方法是Rails Encrypted Secrets。 这样可以避免将敏感变量加载到ENV中,否则可能会无意中暴露出这些风险,从而增加风险。
结论 (Conclusion)
Middleware such as Rack-mini-profiler provides excellent features to developers for improving the speed of Rails applications; however, security controls must be applied to ensure that secrets are properly protected in your application and not leaked to adversaries.
诸如Rack-mini-profiler之类的中间件为开发人员提供了出色的功能,以提高Rails应用程序的速度。 但是,必须应用安全控制措施以确保机密已在您的应用程序中得到适当保护,并且不会泄露给对手。
A wise Cyber Security professional made this simple yet powerful statement:
明智的网络安全专家发表了以下简单而有效的声明:
We all need to work together. Any weakness is a weakness that needs to be fixed, let’s work together to fix things.
我们都需要共同努力。 任何弱点都是需要修复的弱点,让我们共同努力解决问题。
翻译自: https://towardsdatascience.com/leaking-secrets-in-web-applications-46357831b8ed
web应用程序和web网站





















 1247
1247

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








