ctf安全
In this article, I will be walking through the InjuredAndroid CTF. This is a vulnerable Android application with CTF examples based on bug bounty findings, exploitation concepts, and pure creativity. I have left a link to the creators Github and the GitHub I used to download the APK in the references below for anyone interested in trying out the CTF themselves.
在本文中,我将逐步介绍InjuredAndroid CTF。 这是一个易受攻击的Android应用程序,带有基于漏洞赏金发现,利用概念和纯粹创造力的CTF示例。 我留下了指向创建者Github和我用来下载APK的GitHub的链接,这些链接在下面的参考资料中供有兴趣尝试CTF本身的任何人使用。
免责声明 (Disclaimer)
This writeup will obviously contain spoilers and I encourage readers to attempt this CTF before looking at this article. You will learn more by attempting it yourself first and will gain more satisfaction from solving the challenges yourself.
该文章显然将包含破坏者,我鼓励读者在阅读本文之前尝试使用CTF。 您将可以先尝试一下,从中学到更多,并从解决挑战中获得更多的满足感。
The author of this CTF has also mentioned that:
该CTF的作者还提到:
Looking at the source code of the applications in the InjuredAndroid directory, InjuredAndroid FlagWalkthroughs.md file, or binary source code in the Binaries directory will spoil some if not all of the ctf challenges.
在InjuredAndroid目录中查看应用程序的源代码,InjuredAndroid FlagWalkthroughs.md文件或Binaries目录中的二进制源代码将破坏一些(甚至不是全部)ctf挑战。
I must also point out that challenge seven and eight for the release of the APK I used do not function properly and do not have flags. I discovered this after starting the writeup and decided to continue on anyways. With all that said, it’s time to move onto to the writeup!
我还必须指出,针对我使用的APK的发布,挑战7和8不能正常运行且没有标志。 我在开始撰写文章后就发现了这一点,并决定继续进行下去。 综上所述,现在该进行写作了!
最初设定 (Initial Setup)
For this CTF, I will be using a Kali Linux virtual machine as my host device and a Samsung Galaxy S8 emulator created with Genymotion with the following specs:
对于此CTF,我将使用Kali Linux虚拟机作为主机设备,并使用由Genymotion创建的Samsung Galaxy S8模拟器,其规格如下:
To begin the CTF, i connected to my emulator using Android Debug Bridge (ADB) and installed the “injuredandroid.apk” file.
为了开始CTF,我使用Android调试桥(ADB)连接到仿真器并安装了“ injuredandroid.apk”文件。
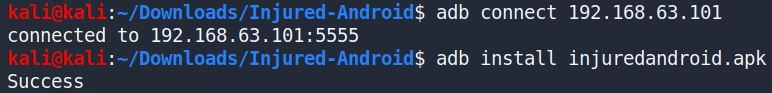
Looking at my emulator, I can see that the application has been installed successfully.
查看我的模拟器,可以看到该应用程序已成功安装。

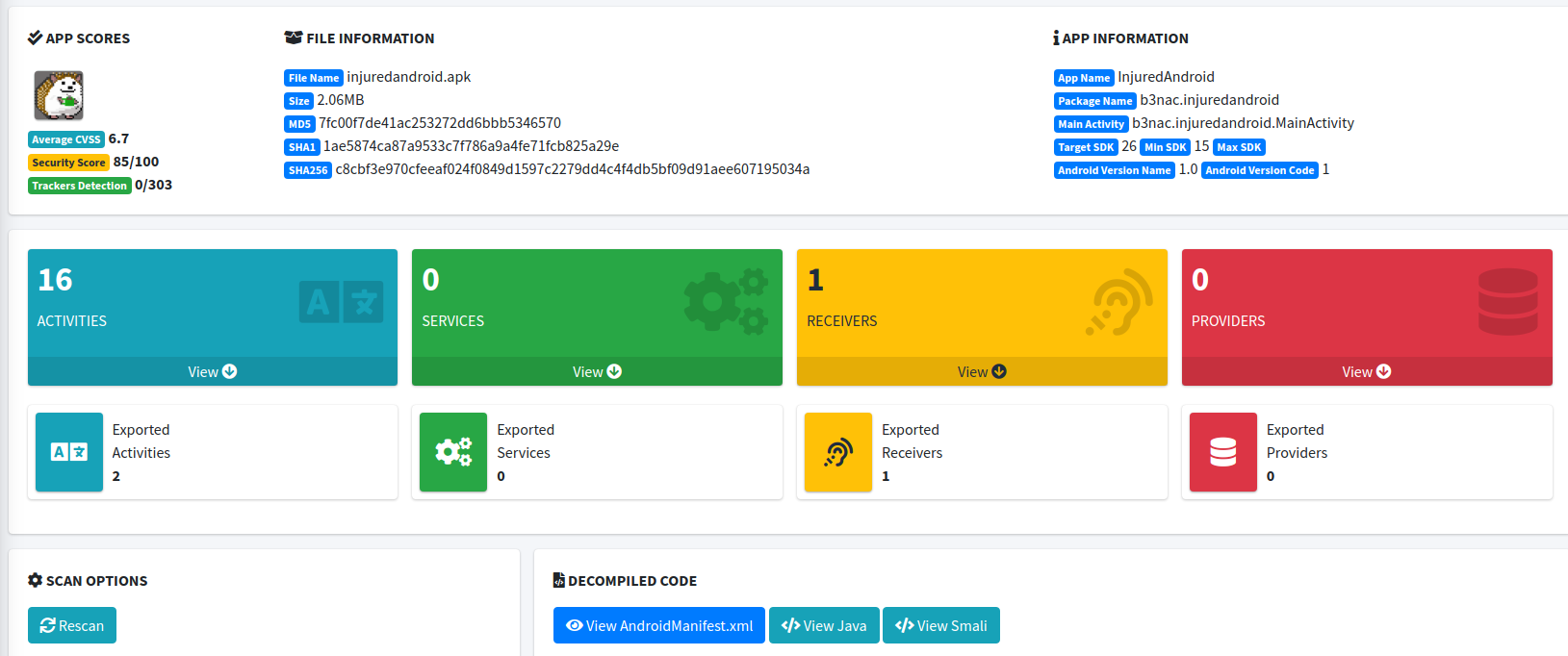
The CTF author also highly recommends decompiling the “injuredandroid.apk”. To accomplish this, I will be using a tool called Mobile Security Framework (MobSF). MobSF automates the process of decompiling the APK, reading the manifest file, identifying issues in the source code and in the Manifest file, extracting the certificate of the application etc. and saves me from having to do this manually. The image below shows the application has been successfully decompiled by MobSF.
CTF作者还强烈建议反编译“ injuredandroid.apk”。 为此,我将使用一个称为“移动安全框架”(MobSF)的工具。 MobSF可以自动执行以下过程:反编译APK,读取清单文件,识别源代码和清单文件中的问题,提取应用程序的证书等,从而使我不必手动执行此操作。 下图显示了该应用程序已被MobSF成功反编译。
With the initial setup out of the way, I can now move on to the challenges.
通过最初的设置,我现在可以继续挑战。
XSS测试 (XSS Test)
Opening the application, I am greeted with the following main activity.
打开该应用程序,我将看到以下主要活动。
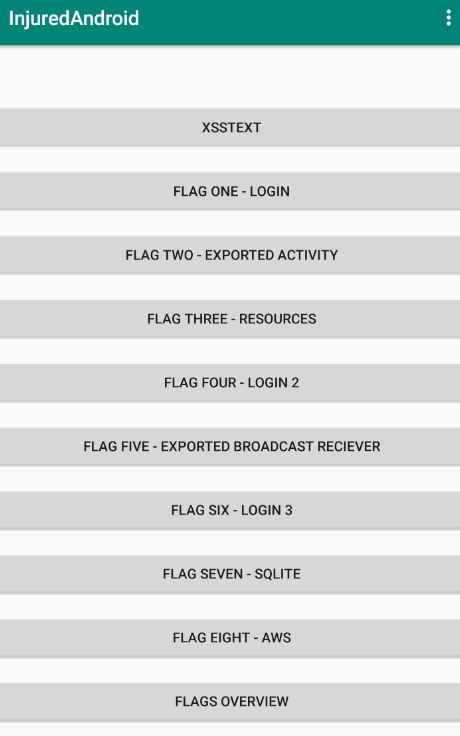
There appears to be eight flags in total. According to the author:
似乎总共有八个标志。 根据作者:
XSSTEST is just for fun and to raise awareness on how WebViews can be made vulnerable to XSS.
XSSTEST只是为了娱乐,并提高了人们对如何使WebView容易受到XSS攻击的认识。
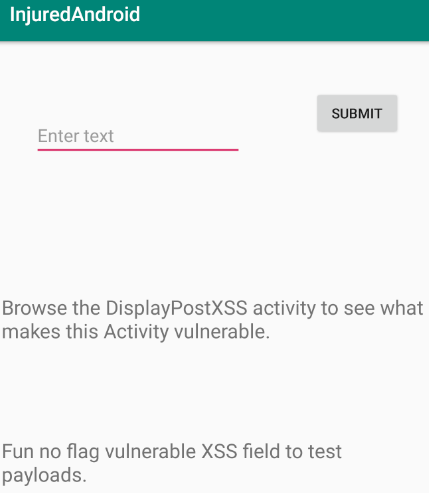
Looking at the XSSTEST activity, I am presented with a simple input field where I can submit text.
在XSSTEST活动中,我看到一个简单的输入字段,可以在其中提交文本。
I can enter some simple JavaScript that will create and alert box to demonstrate if the vulnerability exists.
我可以输入一些简单JavaScript,它们将创建并在警告框中显示该漏洞是否存在。
<script>alert('XSS!!')</script>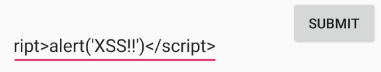
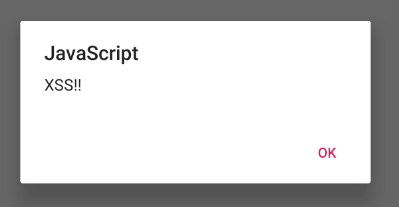
Entering this input causes an alert box to be generated when the activity used to display our input is loaded.
输入此输入将导致在加载用于显示输入的活动时生成警报框。
The challenge recommends looking at the “DisplayPostXSS” activity to determine what makes this activity vulnerable. The source code for the “DisplayPostXSS” activity can be seen in the image below.
挑战建议查看“ DisplayPostXSS”活动,以确定导致该活动易受攻击的原因。 下图显示了“ DisplayPostXSS”活动的源代码。








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章














 499
499











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








